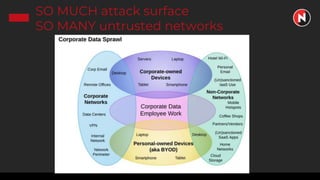
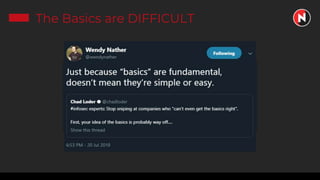
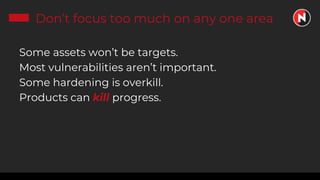
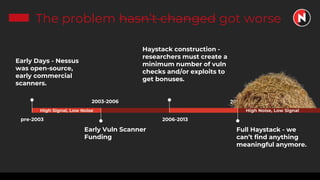
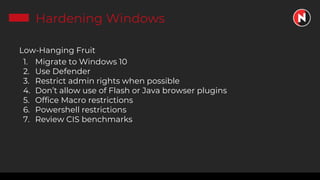
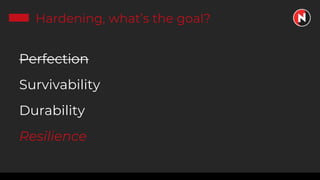
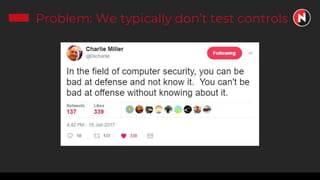
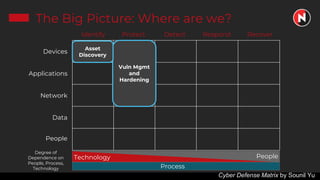
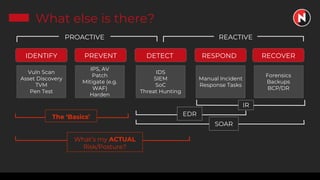
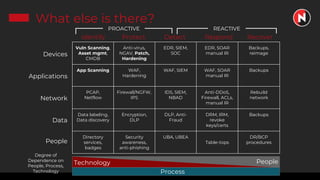
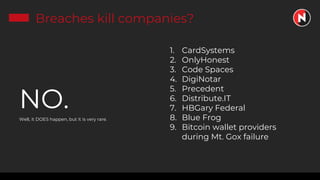
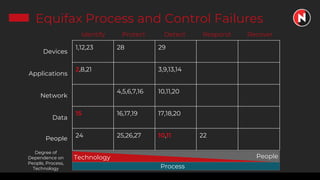
This document discusses the ongoing challenges of securing systems and networks. It notes that while cybersecurity basics like asset discovery, vulnerability management, and hardening are important, they are also very difficult tasks given the complexity of modern IT environments. The constant evolution of threats, emerging technologies, and lack of standardized frameworks add to these challenges. However, taking a perspective focused on resilience over perfection, prioritizing the highest risks, and learning from breaches can help tackle security issues in a pragmatic way. The presentation provides strategies for discovery assets, managing vulnerabilities, and hardening systems effectively.