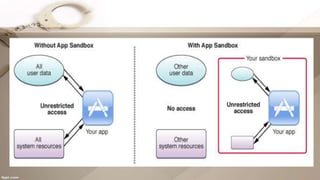
Sandboxing creates confined execution environments for running untrusted programs. It works by restricting programs' access to system files and resources to minimize risks if the program misbehaves. Examples include sandboxing web pages in browsers, PDFs in Adobe Reader, and mobile apps. Sandboxes can detect unknown viruses with low false alarms and allow testing malware safely. Virtual machines and tools like Sandboxie provide sandboxing for any program. Without sandboxing, hostile programs would have unlimited access to users' computers.