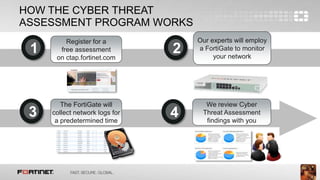
The document describes a Cyber Threat Assessment Program that provides a free network security assessment. The program involves deploying a FortiGate appliance on the network to monitor traffic for a period of time, then generating a report analyzing security, user productivity, and network utilization. The report identifies areas for improvement and is reviewed with the customer by a Fortinet systems engineer.