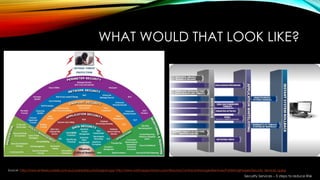
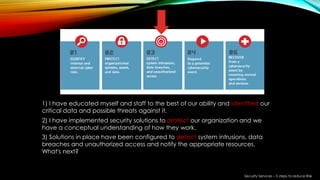
This document provides a summary of a presentation on cybersecurity evolution and awareness. It discusses emerging technology trends like the internet of things, big data, and predictive analytics. It also covers social media risks and security services to reduce risk through a five step approach of identifying, protecting, detecting, responding to, and recovering from cyber attacks. The presentation aims to prepare organizations for future cybersecurity challenges through education and implementing best practices.