Embed presentation
Downloaded 17 times




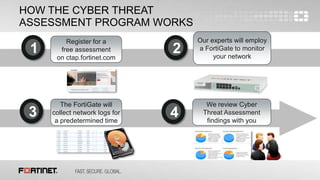
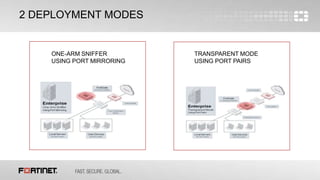



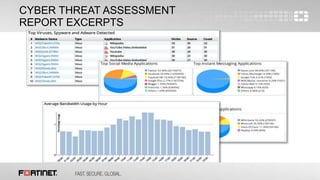



The document describes a free cyber threat assessment program offered by Fortinet that analyzes a network's security, user productivity, and network utilization. The assessment involves deploying a FortiGate appliance on the network to monitor traffic for a set time period. Fortinet experts then analyze the collected logs and provide a report detailing any security threats detected, application vulnerabilities, malware and botnet activity, non-compliant device or application usage, and opportunities to optimize network performance and security solutions.












