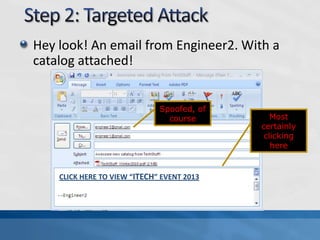
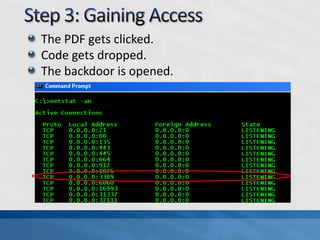
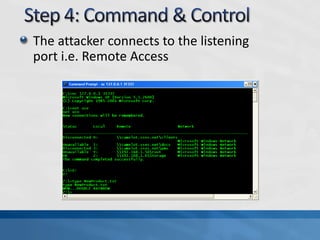
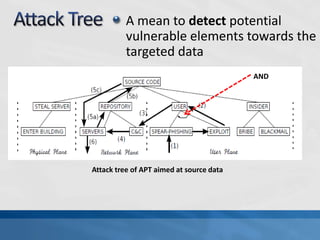
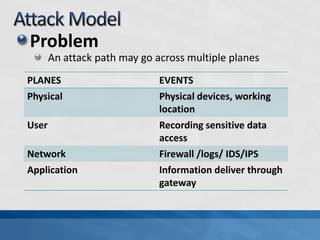
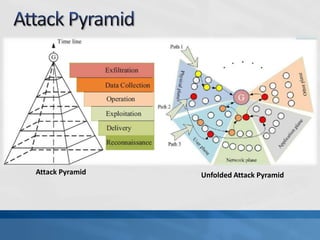
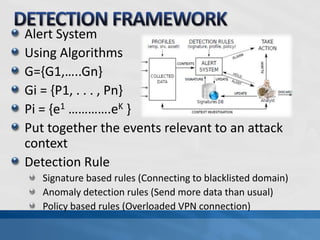
This document discusses advanced persistent threats (APTs). It defines APTs, describes their stages including reconnaissance, delivery, exploitation, operation, data collection, and exfiltration. It then presents an APT detection framework called the Attack Pyramid that models APT attacks across physical, user access, network, and application planes and detects relevant events using algorithms and rules. Research papers are cited that further define APTs and propose the Attack Pyramid model for detecting such threats.