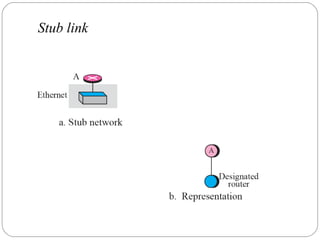
The document discusses various routing protocols used in computer networks, emphasizing the distinction between intra-domain and inter-domain routing. It describes the functionality of distance vector routing protocols like RIP, link state protocols such as OSPF, and path vector routing protocols like BGP, detailing their mechanisms and updates. Additionally, the document covers multicast routing techniques and their applications, including multicast distance vector routing and protocol independent multicast.