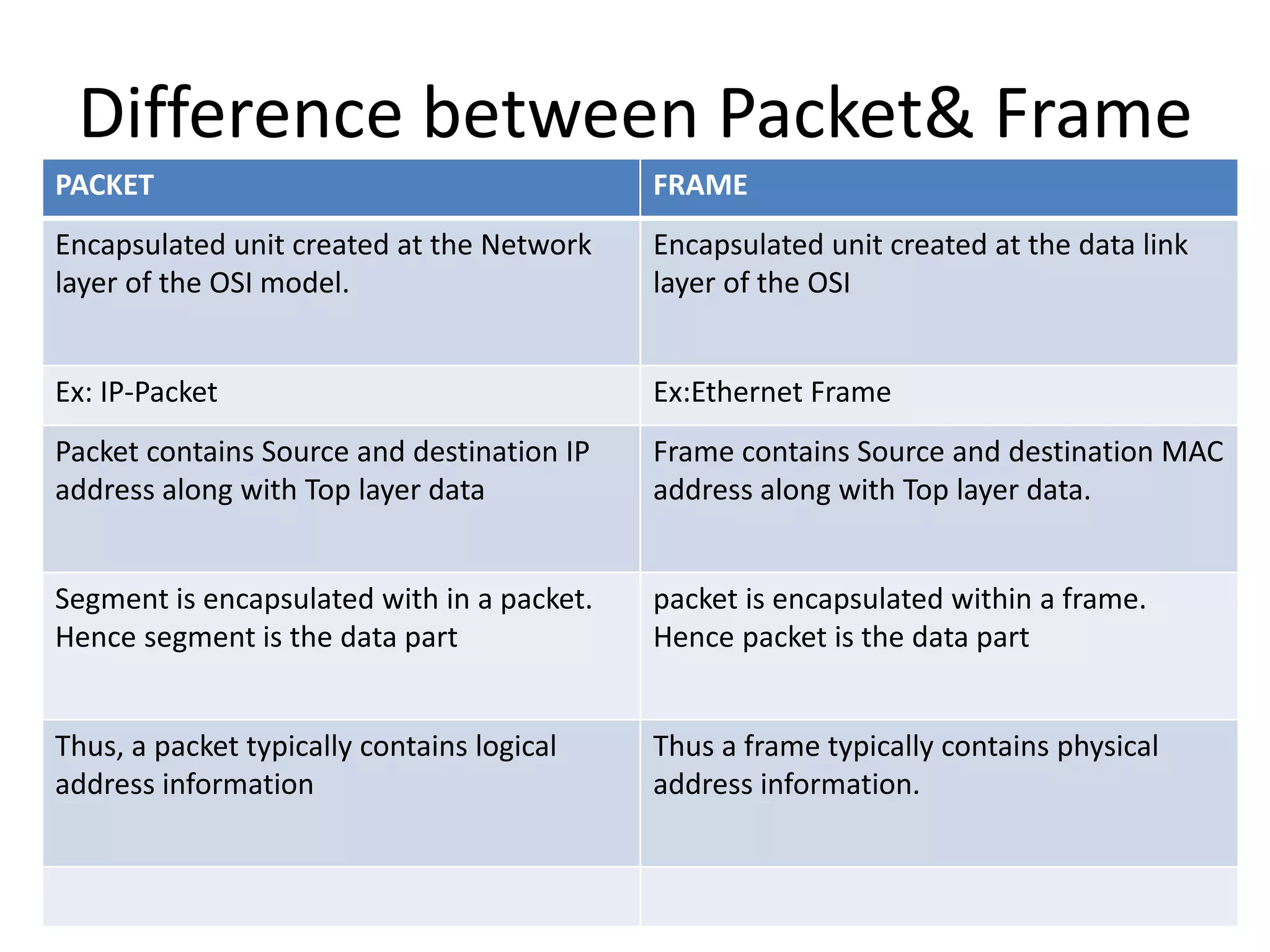
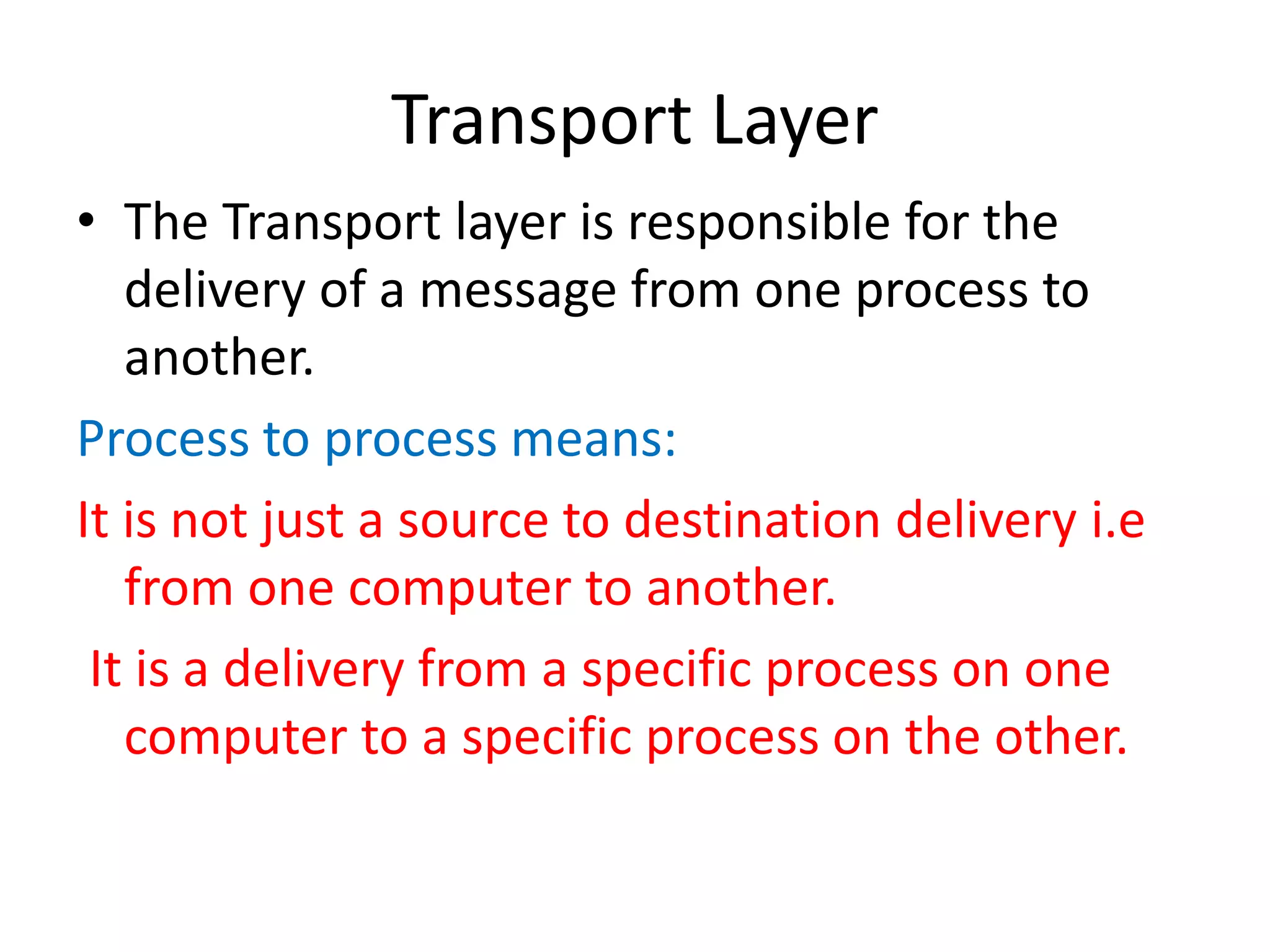
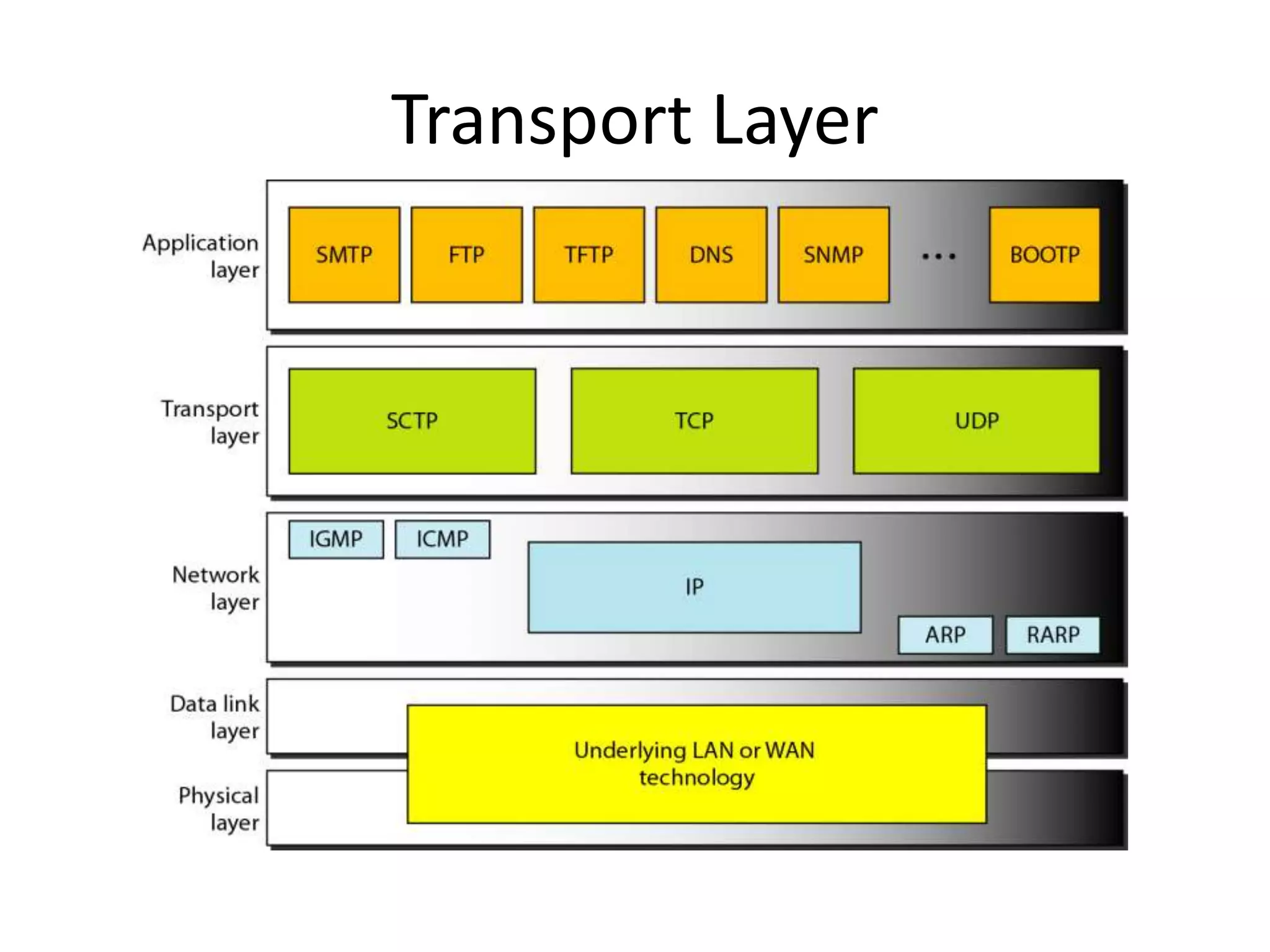
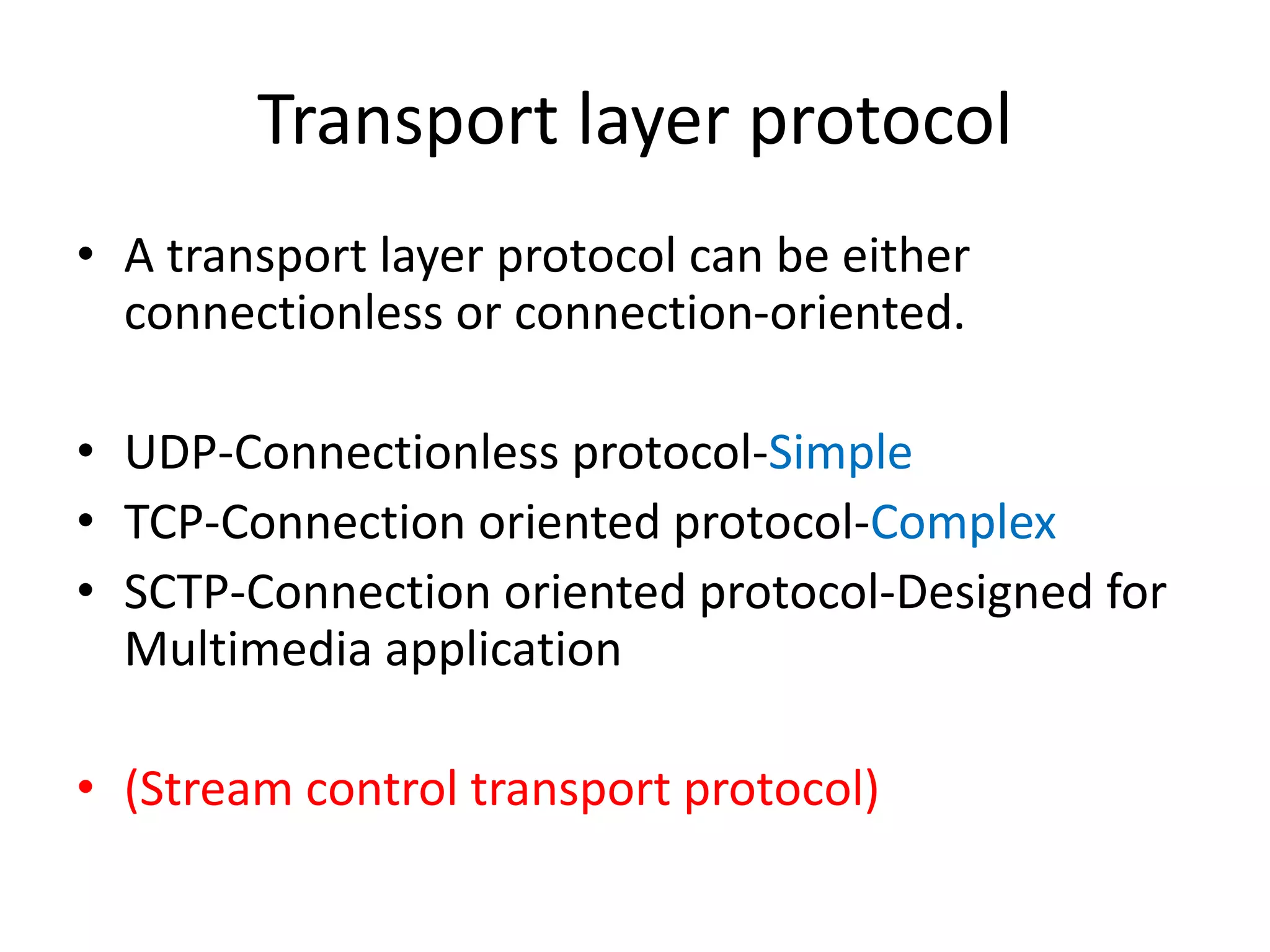
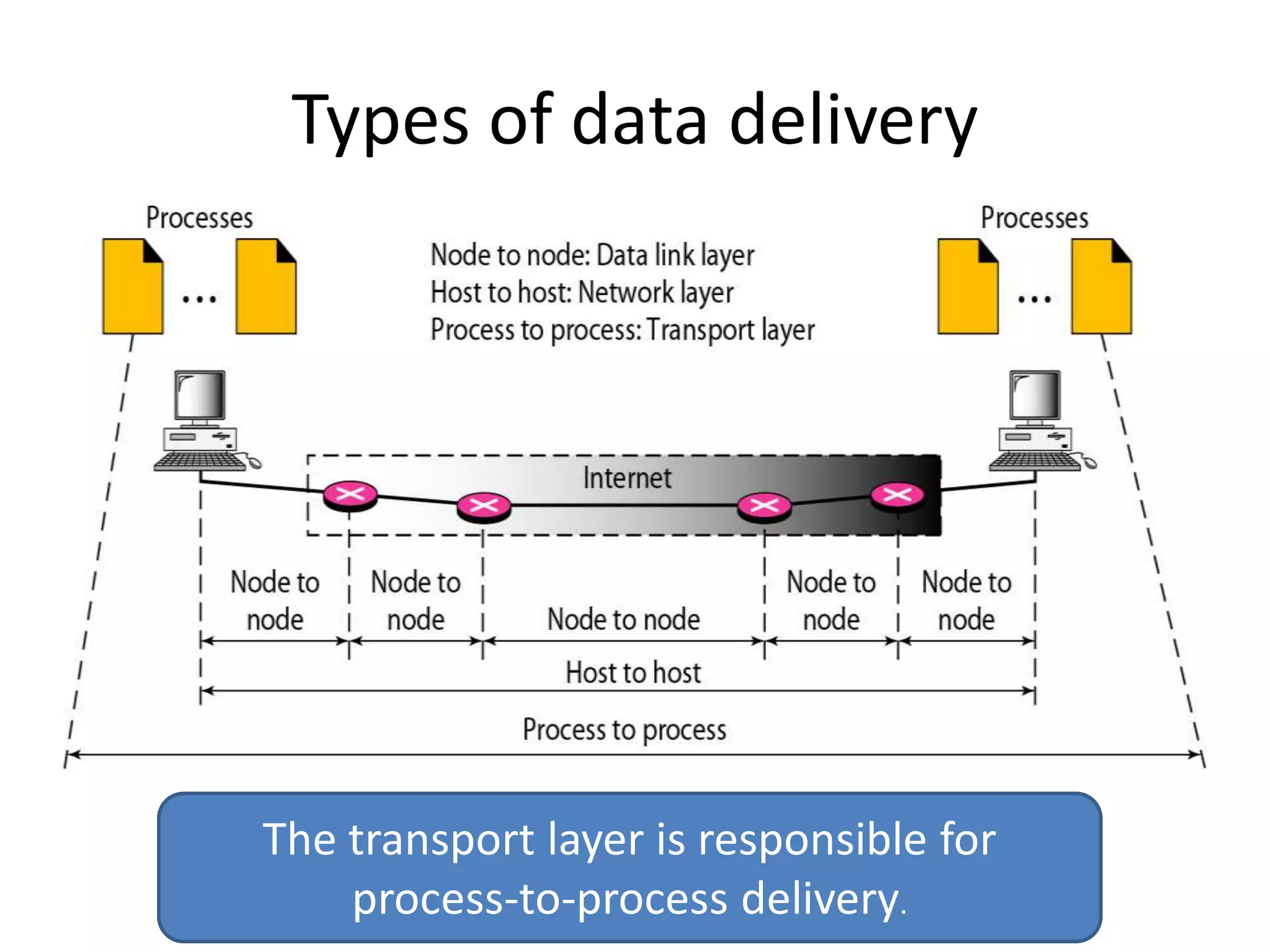
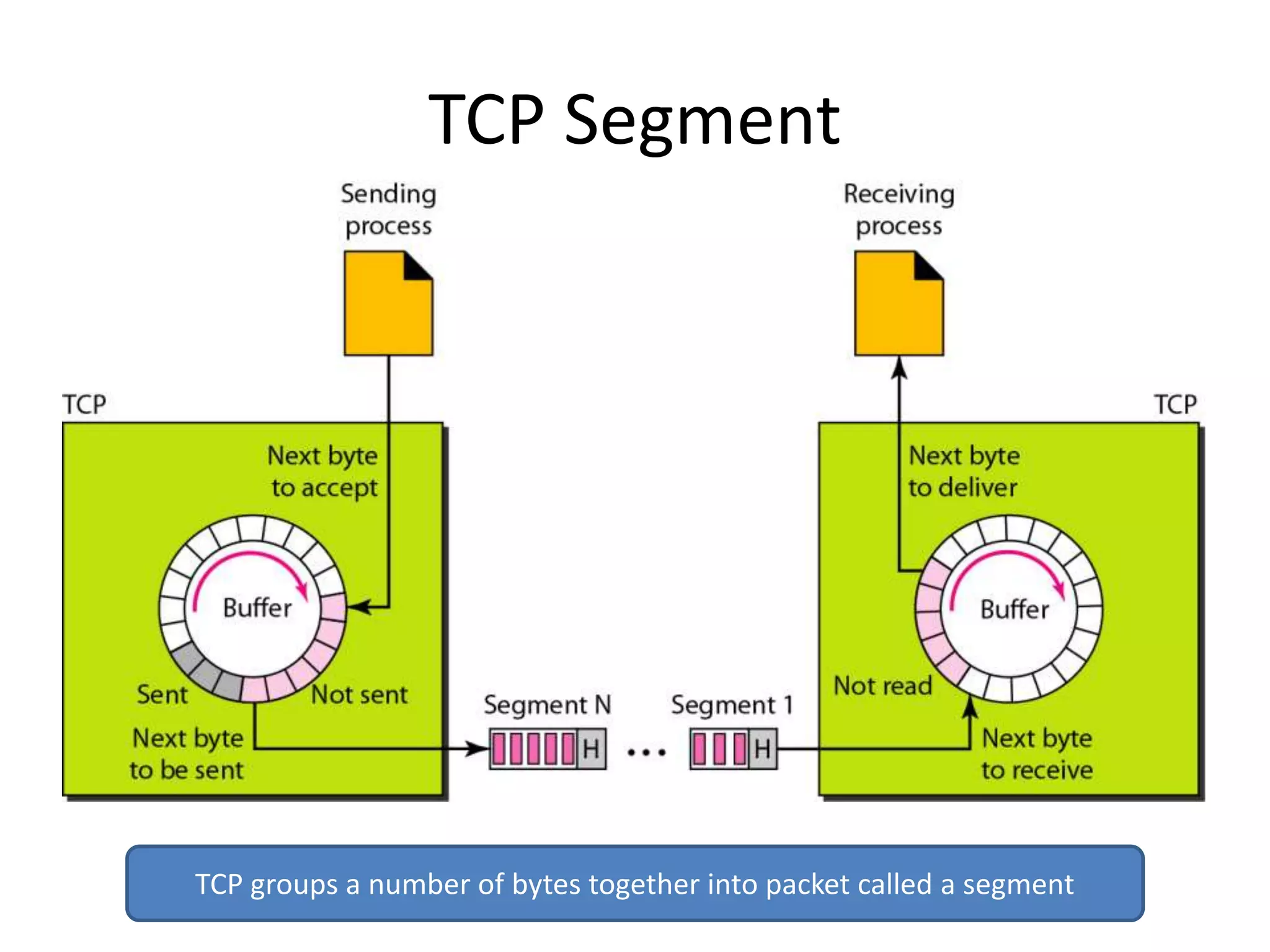
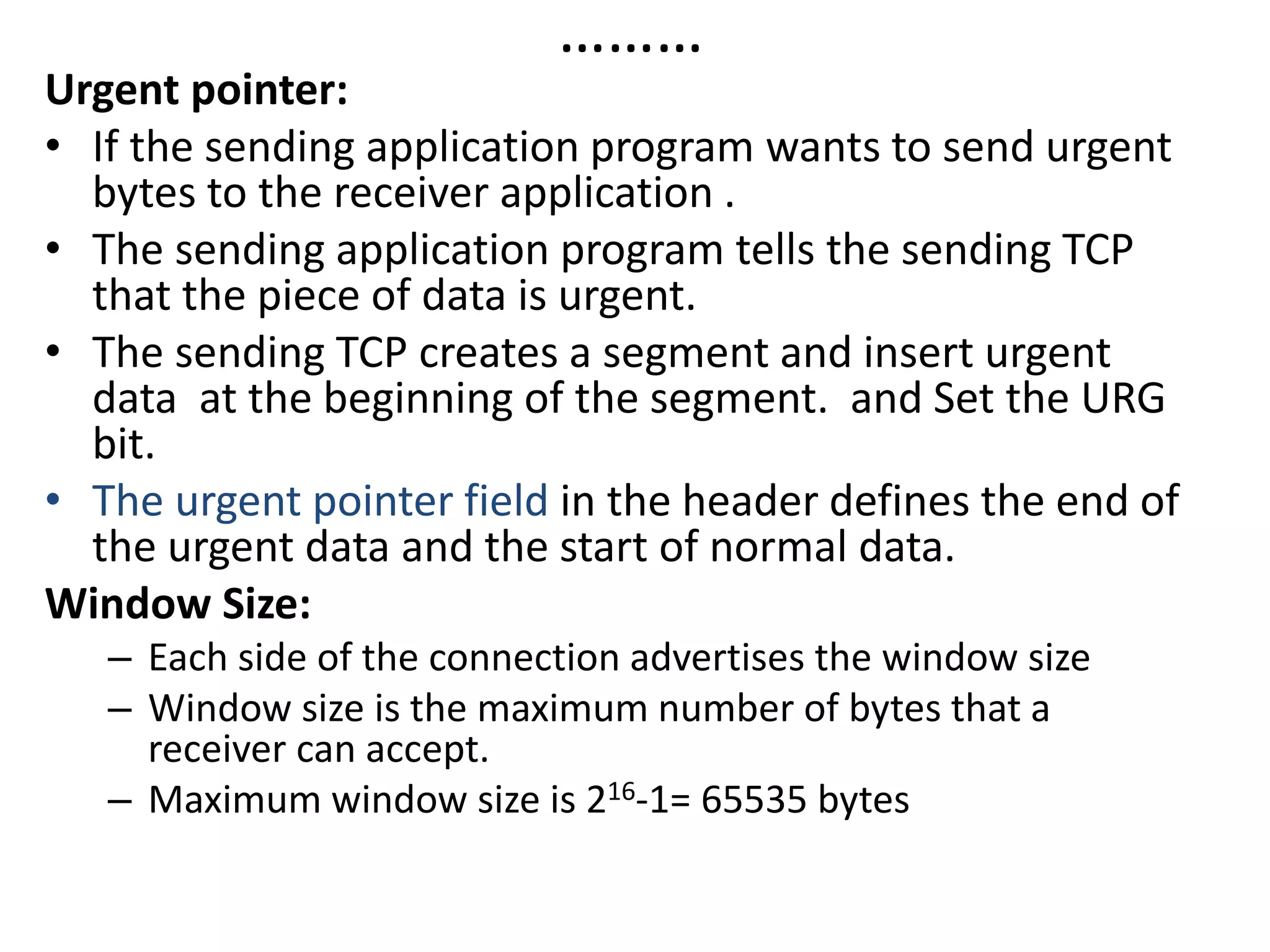
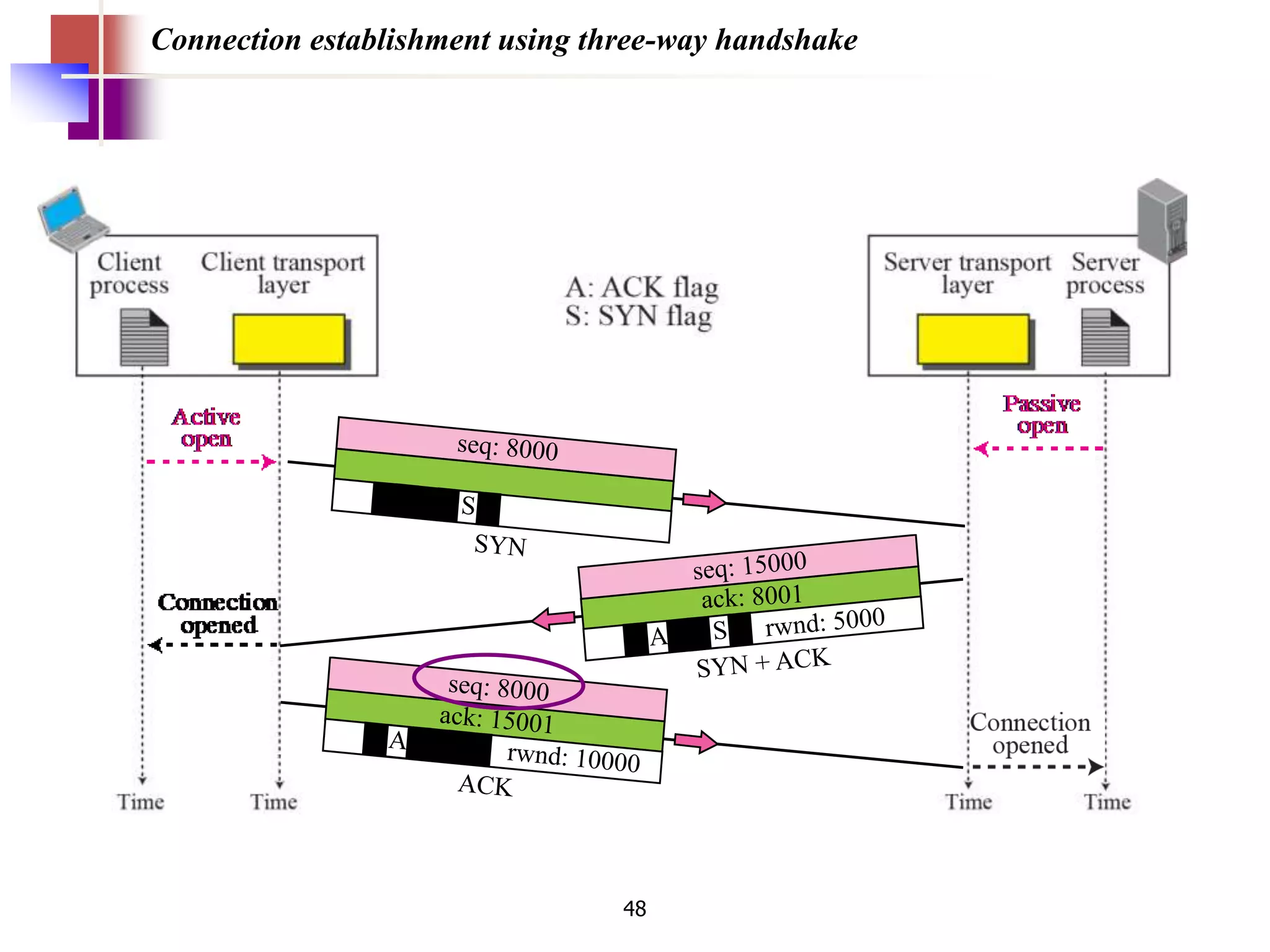
The document discusses the differences between packets and frames, and provides details on the transport layer. It explains that the transport layer is responsible for process-to-process delivery and uses port numbers for addressing. Connection-oriented protocols like TCP use three-way handshaking for connection establishment and termination, and implement flow and error control using mechanisms like sliding windows. Connectionless protocols like UDP are simpler but unreliable, treating each packet independently.