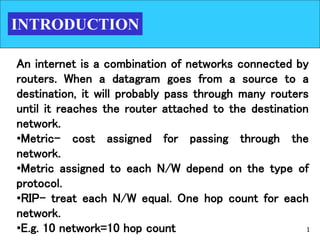
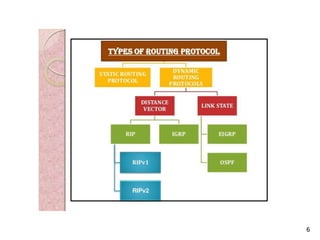
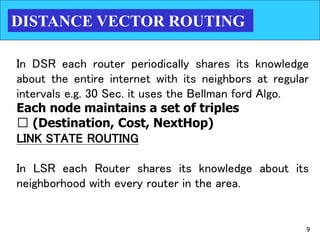
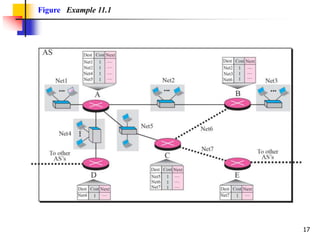
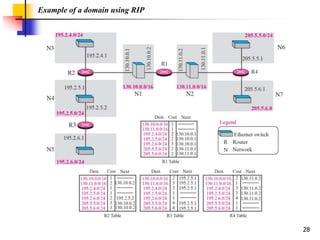
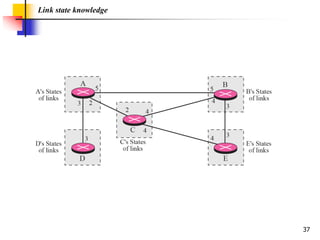
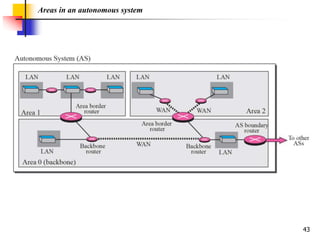
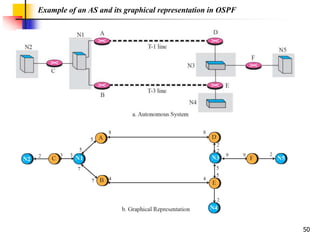
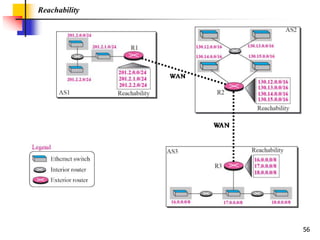
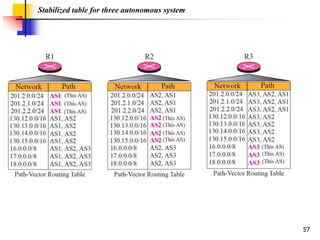
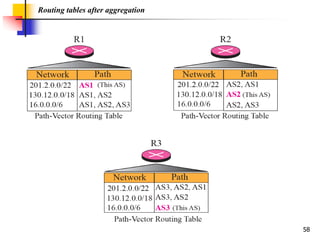
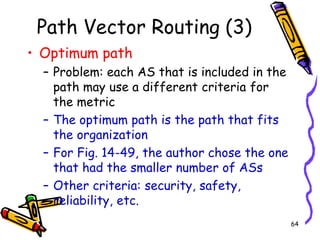
The document discusses routing protocols used in internets and autonomous systems. It describes how distance vector routing protocols like RIP work by sharing routing tables between neighbors. It also explains link state routing protocols like OSPF, where each router shares information about connected links and all routers can independently calculate optimal routes. Finally, it outlines path vector routing and BGP, which is used for inter-domain routing between autonomous systems and considers routing policies.