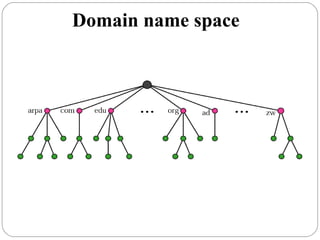
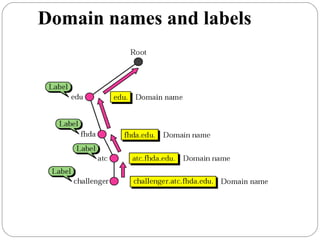
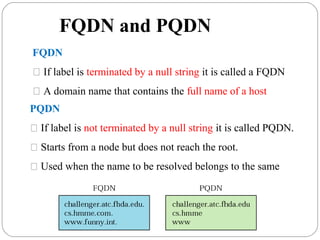
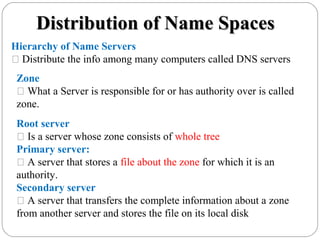
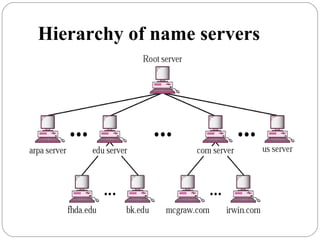
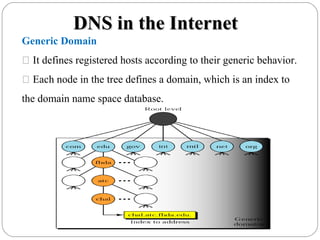
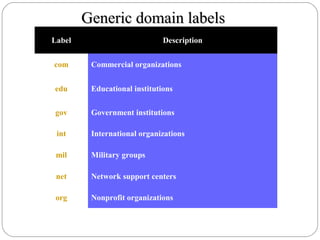
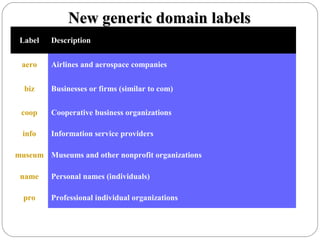
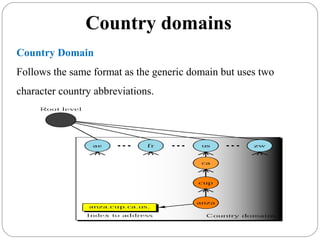
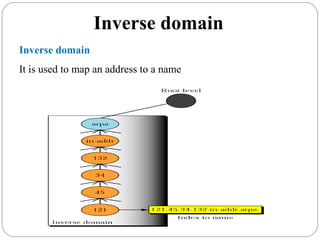
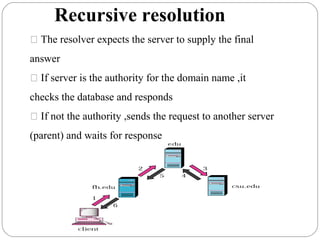
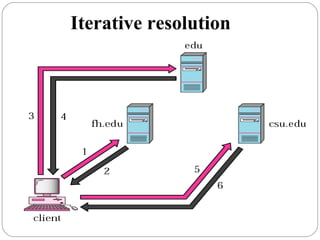
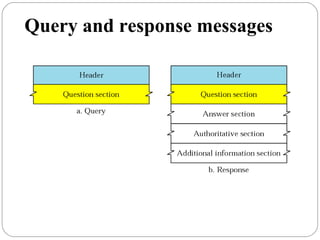
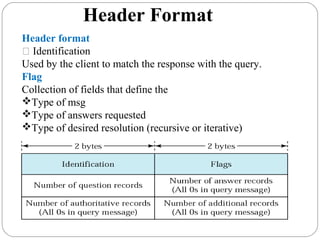
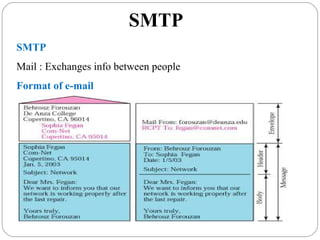
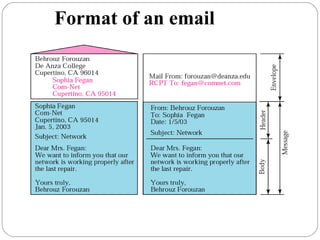
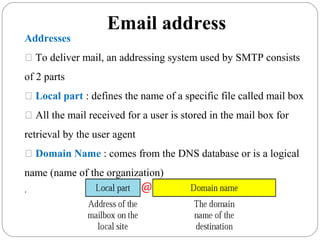
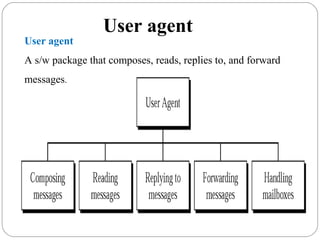
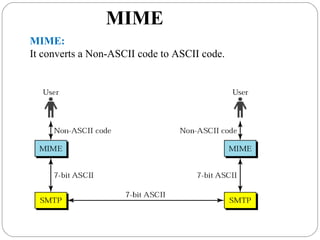
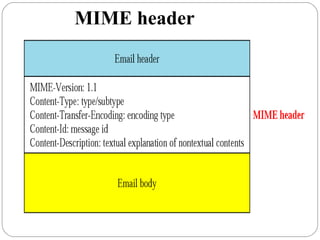
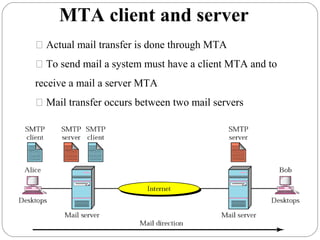
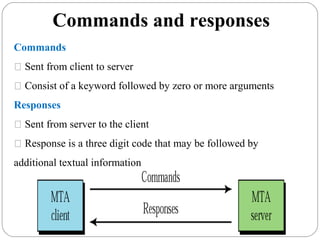
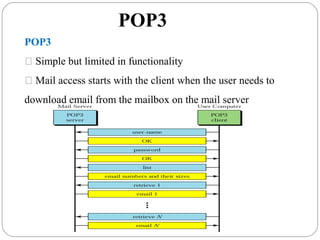
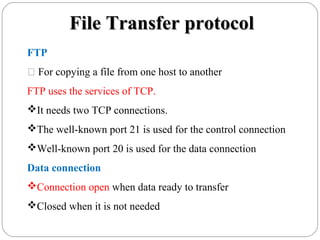
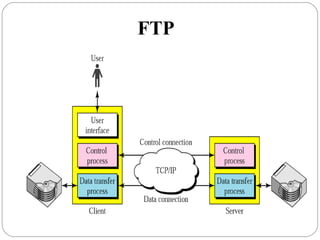
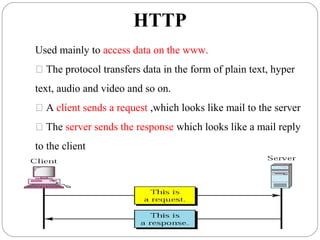
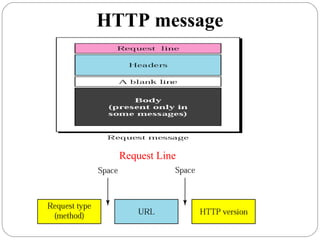
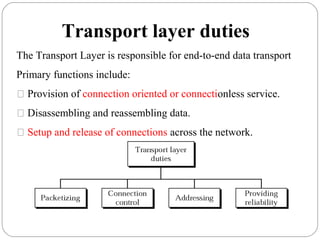
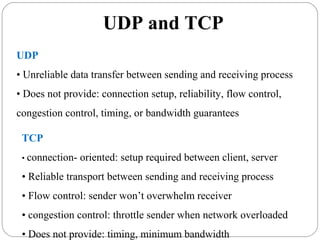
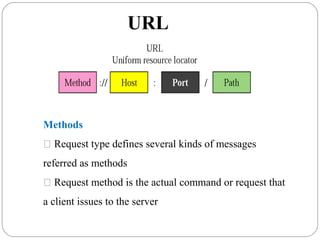
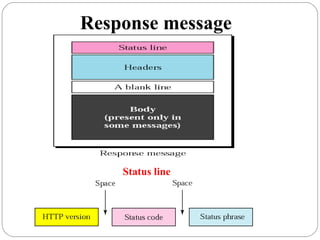
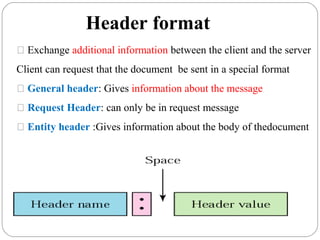
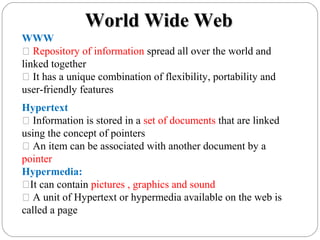
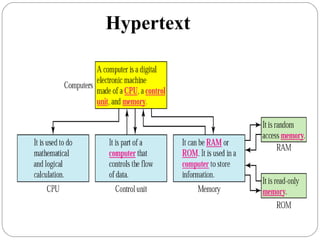
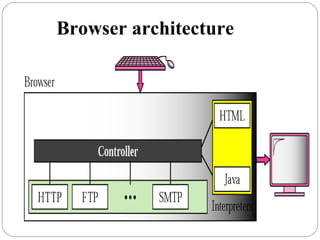
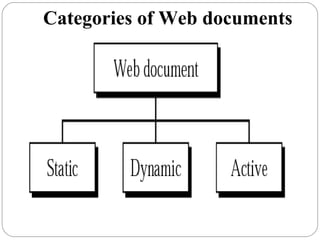
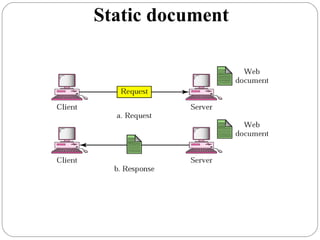
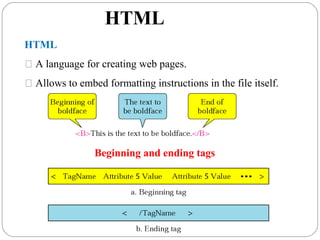
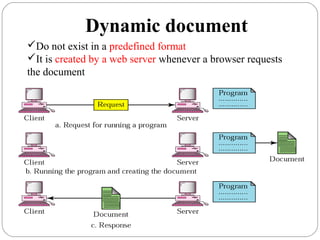
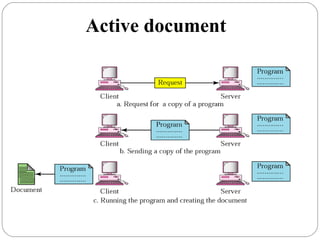
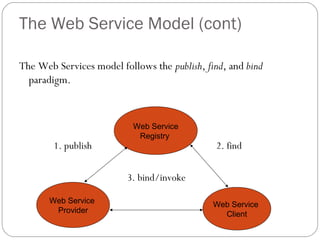
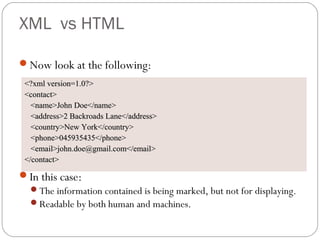
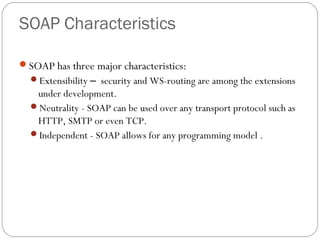
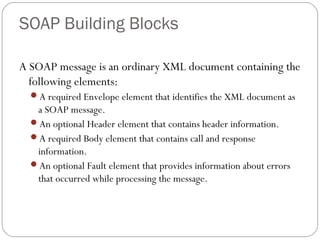
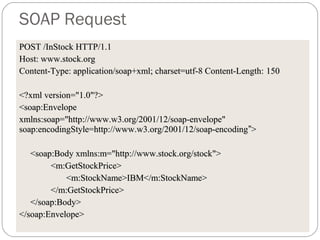
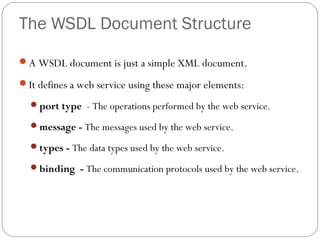
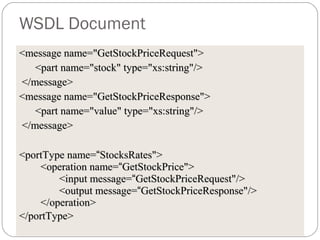
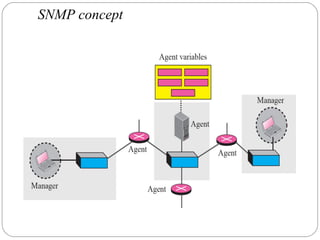
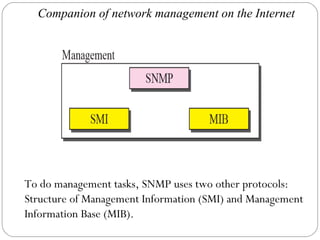
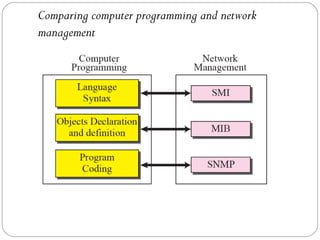
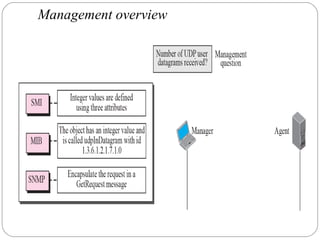
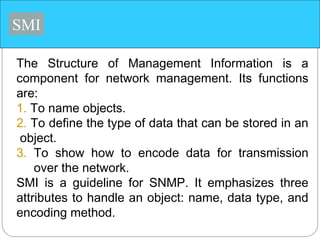
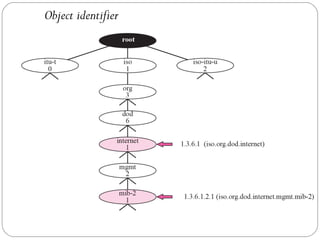
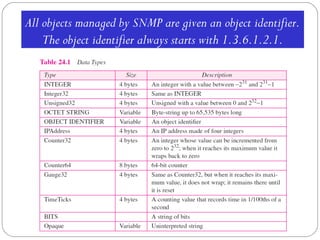
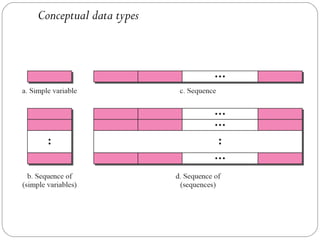
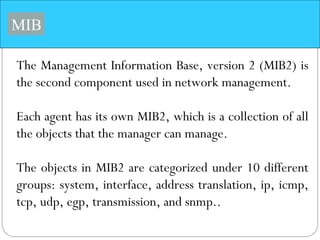
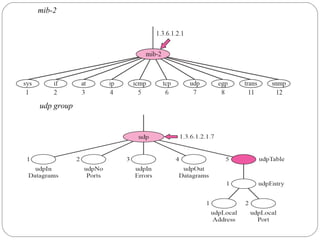
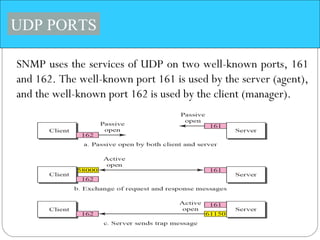
The document provides a comprehensive overview of the application layer focusing on the Domain Name System (DNS), email protocols, and web services. It explains key concepts including domain name structure, email format and protocols like SMTP and POP3, along with file transfer protocols such as FTP and HTTP. Additionally, it details web services, SOAP, XML, and WSDL definitions, highlighting their roles in modern web communication and interoperability.