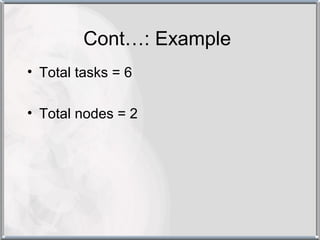
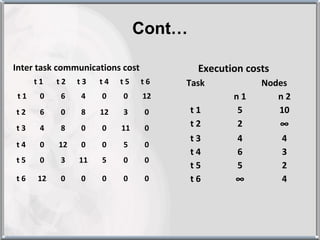
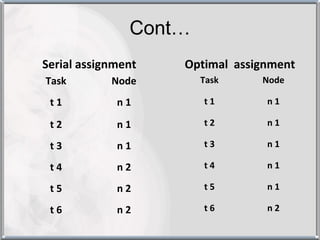
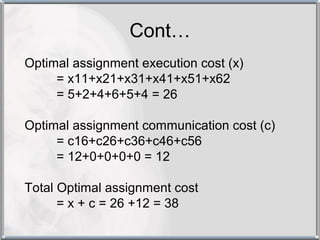
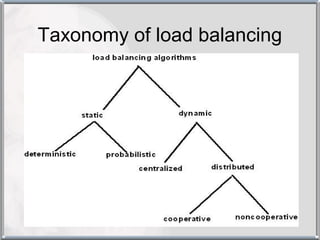
The document discusses various techniques for resource management in distributed systems. It describes approaches like task assignment, load balancing, and load sharing. It also covers desirable features of scheduling algorithms and discusses techniques like task assignment in detail with an example. Furthermore, it discusses concepts like load balancing approaches, task assignment, location policies, state information exchange policies, and priority assignment policies.