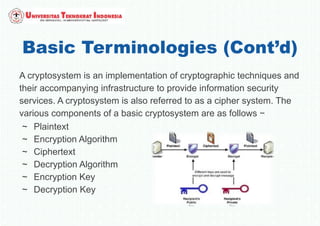
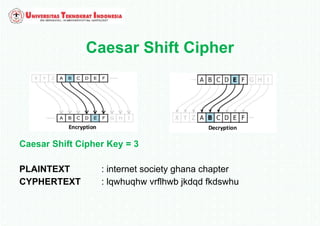
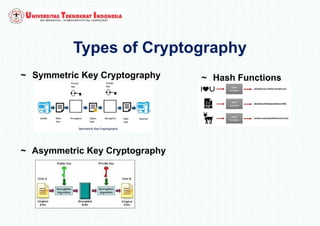
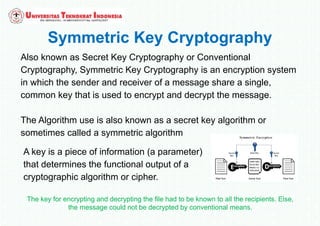
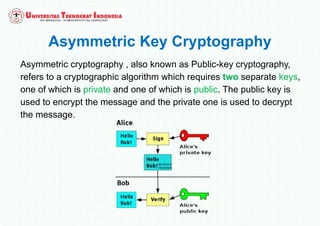
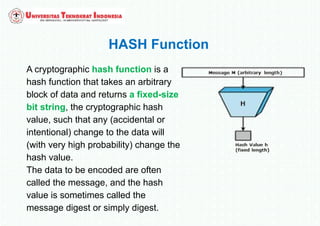
The document discusses various topics in network security and cryptography. It begins by defining cryptography as the study of secure communication techniques. It then discusses symmetric key cryptography, where the sender and receiver share a single key, and asymmetric key cryptography using public/private key pairs. The document also covers hash functions, which take an input and produce a fixed-size output to verify data integrity. Examples of cryptographic algorithms for each type are also provided.