Embed presentation
Download to read offline


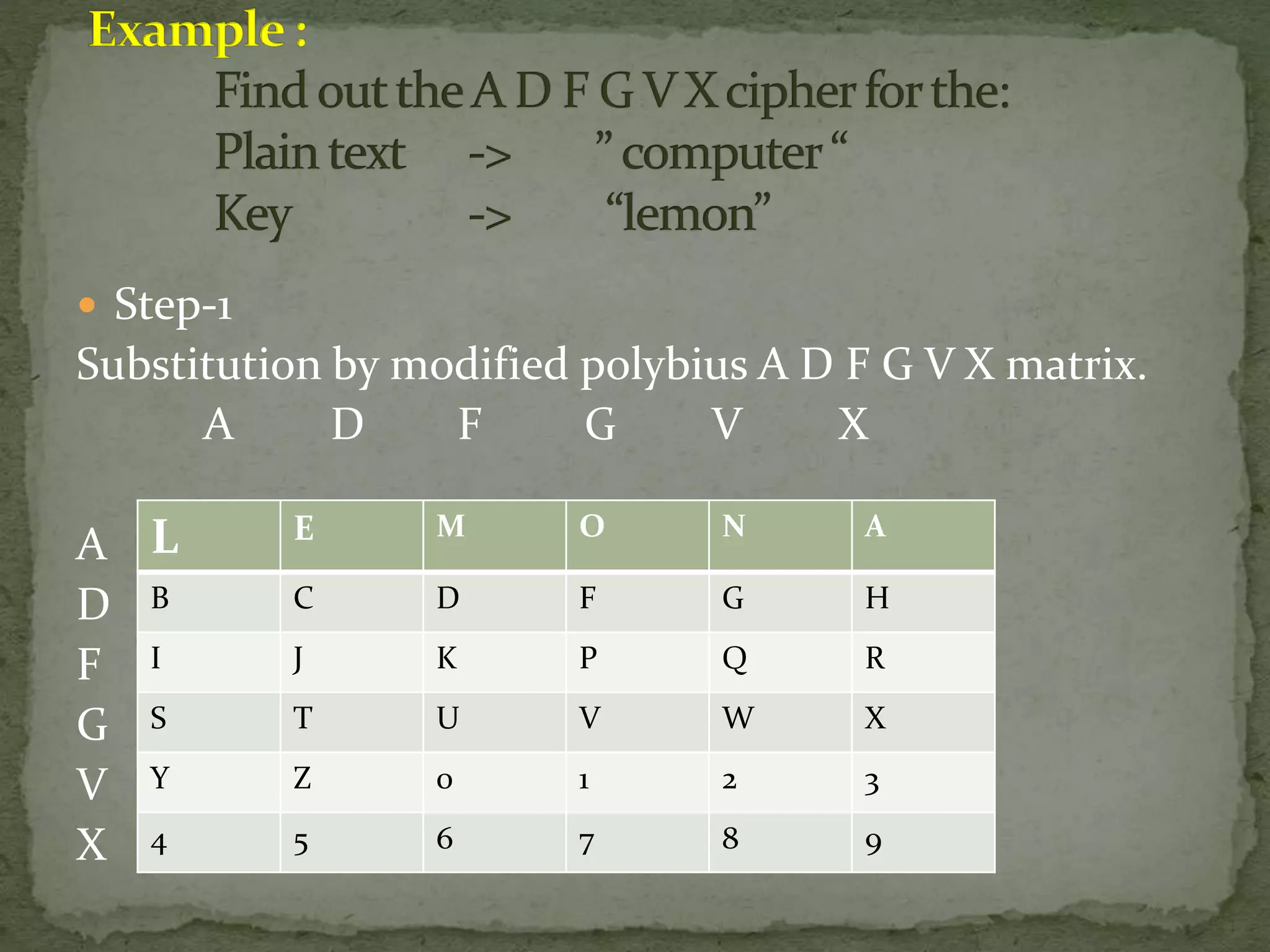




This document discusses product ciphers, which combine substitution and transposition ciphers for stronger encryption. It provides an example of encrypting the plaintext "COMPUTER" using a two-step product cipher. First, substitution encryption is done using a 6x6 matrix. Then, transposition encryption is performed by rearranging the ciphertext columns according to a keyword. The document explains how to encrypt another plaintext "CRYPTOGRAPHY" using the same technique with a different keyword.







