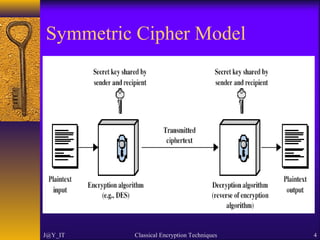
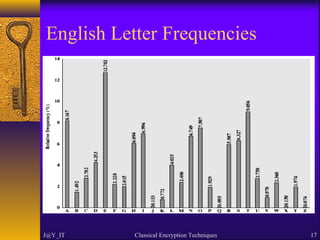
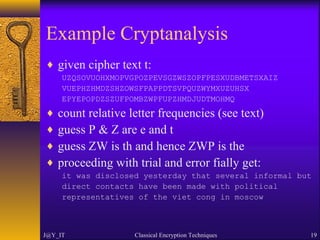
The document discusses classical encryption techniques including symmetric and asymmetric encryption, with a focus on several types of classical ciphers such as substitution and transposition ciphers. It explains the terminology used in cryptography, cryptanalysis methods, and various ciphers like the Caesar cipher, Playfair cipher, and Vigenère cipher. Additionally, the document covers the security aspects, including the effectiveness of different ciphers and the concept of steganography.