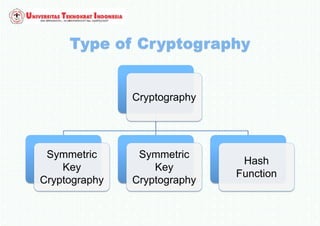
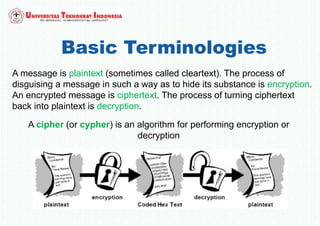
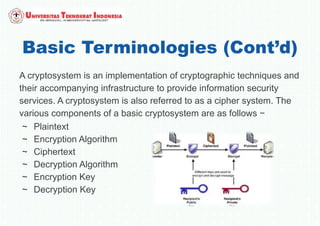
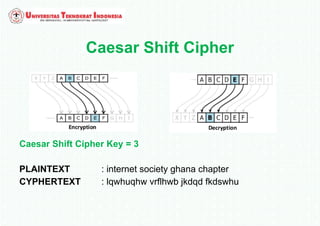
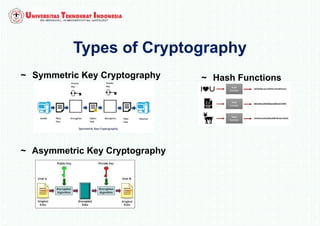
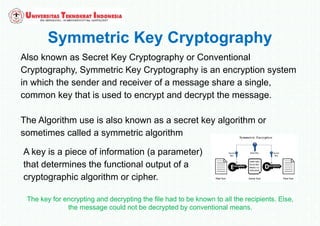
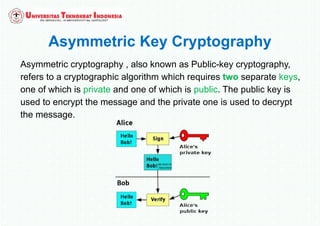
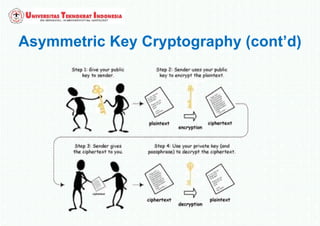
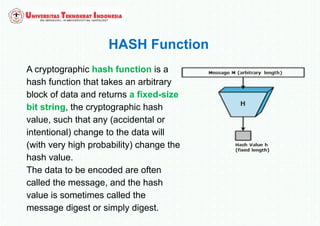
The document discusses various topics in network security and cryptography. It begins by introducing cryptography and its basic concepts, including encryption, decryption, ciphers, and cryptosystems. It then discusses the goals of cryptography in providing confidentiality, integrity, authentication, and non-repudiation. The document outlines the main types of cryptography: symmetric key cryptography using a shared private key, asymmetric key cryptography using public/private key pairs, and hash functions which generate unique fingerprints of data. Examples of algorithms for each type are also provided.