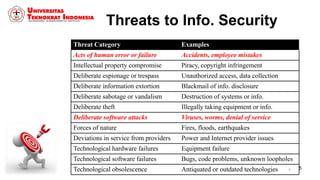
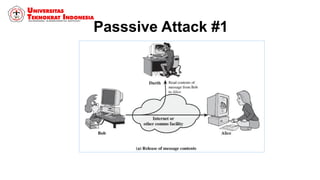
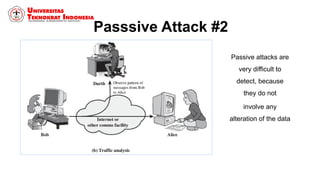
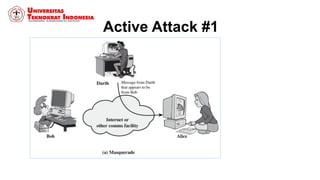
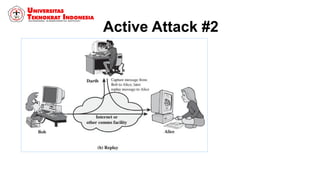
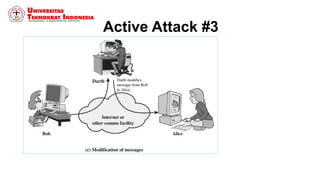
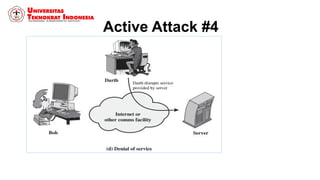
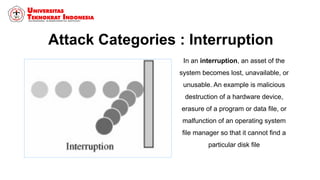
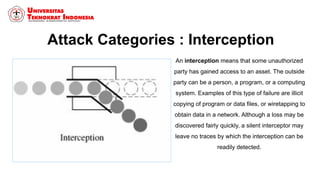
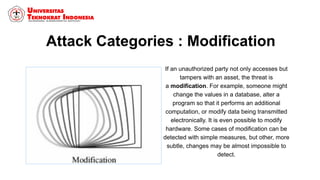
This document discusses threats, vulnerabilities, and attacks related to information security. It defines threats as potential dangers that could breach security, and lists categories of threats like deliberate threats, environmental threats, and accidental threats. Vulnerabilities are weaknesses that can be exploited by threats, like physical vulnerabilities, hardware/software vulnerabilities, and human vulnerabilities. Attacks are exploits of vulnerabilities that damage systems. Common attacks are discussed like passive attacks that obtain information and active attacks that alter systems. The document also categorizes attacks as interruptions, interceptions, modifications, or fabrications of systems and assets. The three biggest common attacks are said to be virus, worm, and Trojan horse attacks.