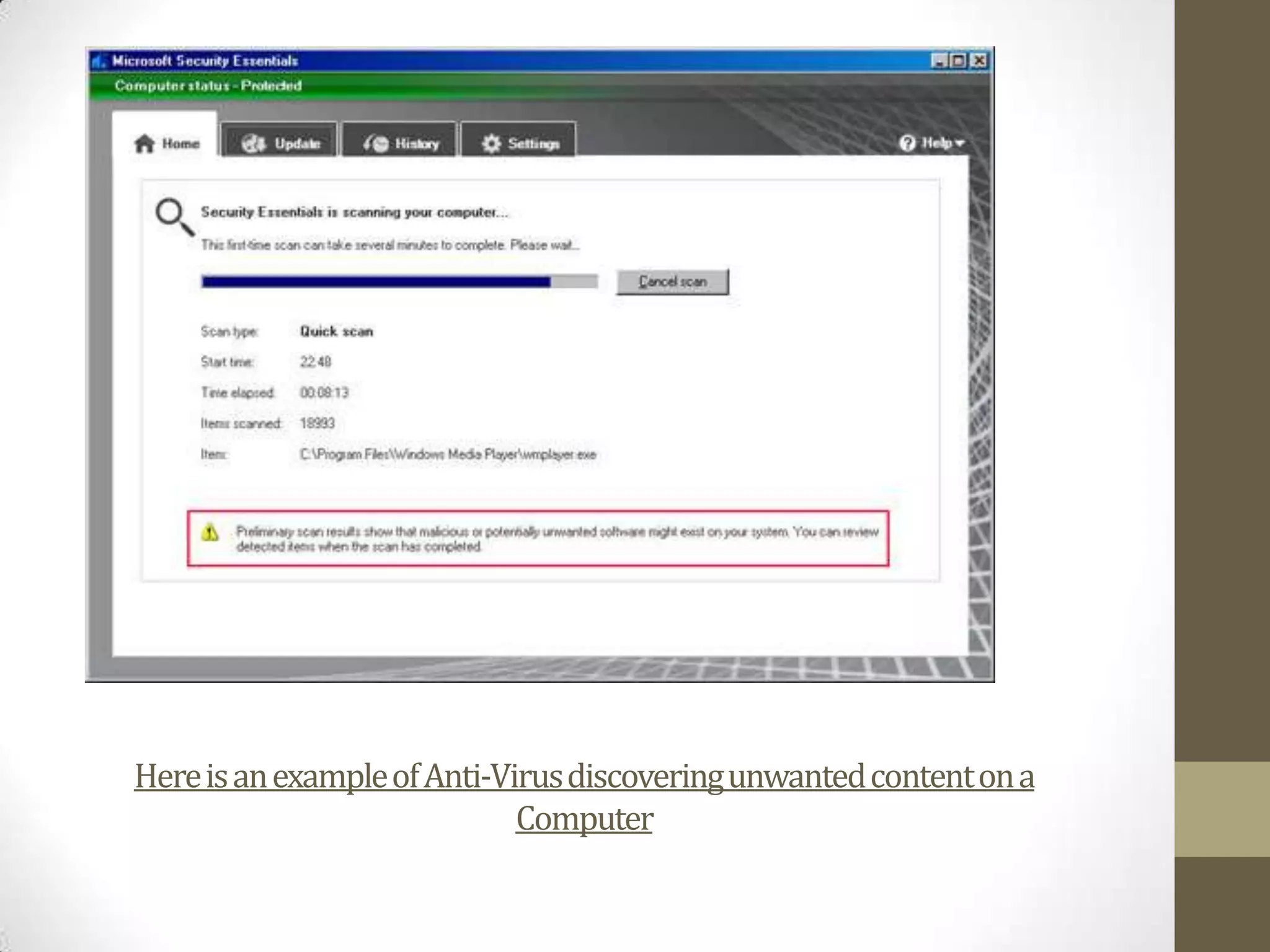
The document discusses potential security risks like viruses, Trojans, and worms, and how an anti-virus program helps protect against these threats. It explains that the anti-virus was installed to protect the computer from being infected through hourly updates and daily scans. Trojans disguise as legitimate programs but give hackers access, while viruses replicate and spread between computers corrupting files. Worms also duplicate themselves to spread through networks. Anti-virus software can detect and delete viruses and uncover unwanted content.