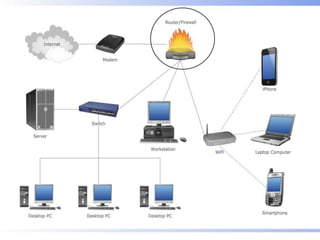
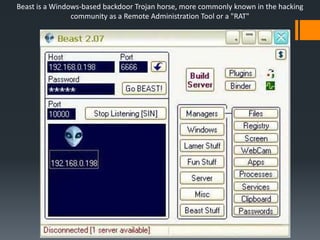
Malware comes in various forms and can infect computers through many sources such as malicious websites, pirated software/media, and emails. There are three main types of malware: viruses, trojans, and worms, which operate differently to disrupt computers. Users can protect themselves by only visiting trusted sites, avoiding suspicious ads and emails, and using antivirus and firewall software to block unauthorized access and programs. Malware aims to access personal information and systems without permission.