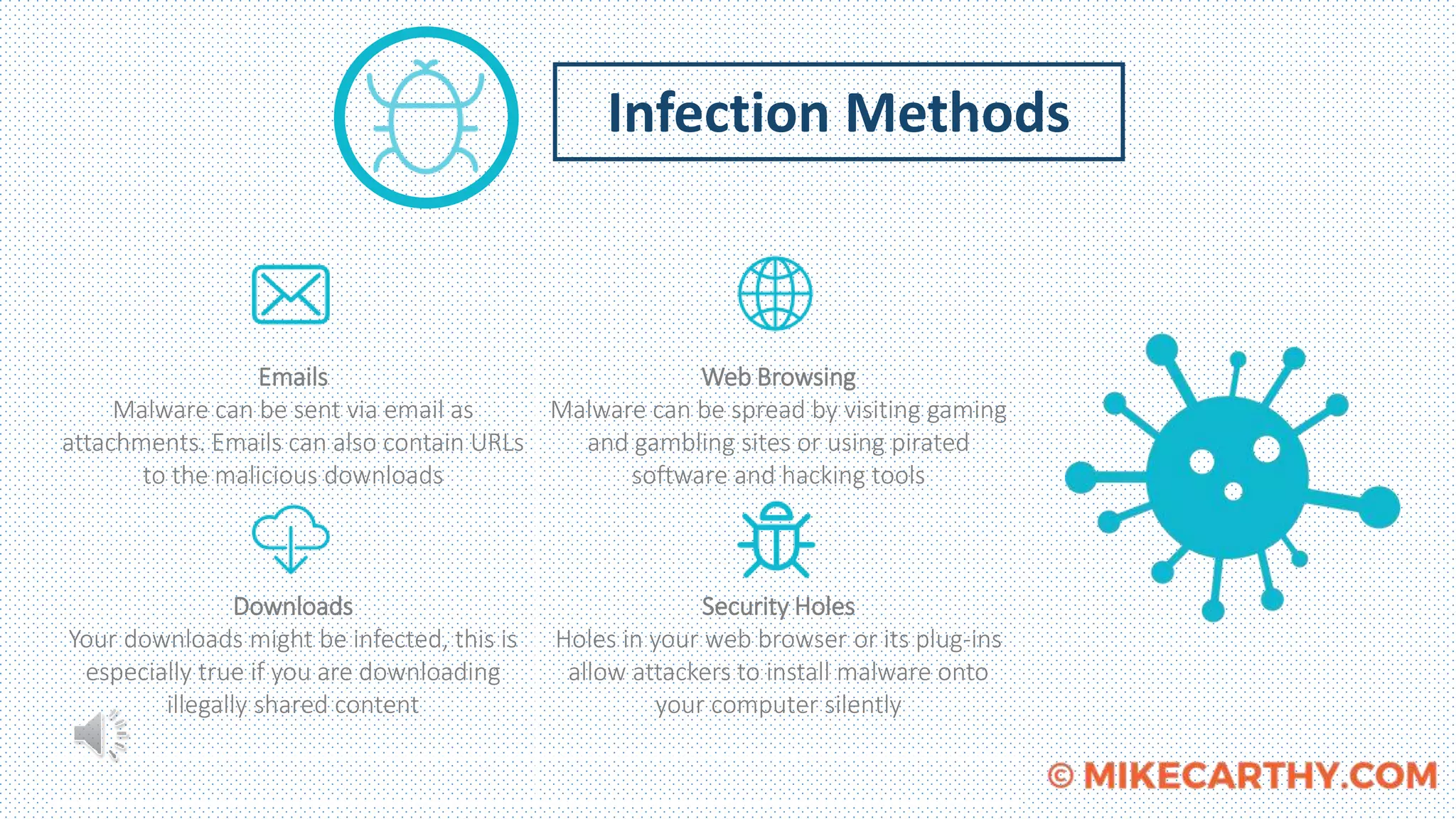
Malware presents a danger to computers and networks by causing unauthorized harm. It includes viruses, worms, Trojan horses, ransomware, and other malicious code. This malware can monitor activity, record keystrokes, and encrypt files. Different types of malware like viruses, worms, and Trojan horses use various techniques to infect systems. A case study of Target Corporation in 2013 showed how malware installed on point-of-sale systems was used to steal personal information of 110 million customers, demonstrating the serious threats malware poses to businesses.