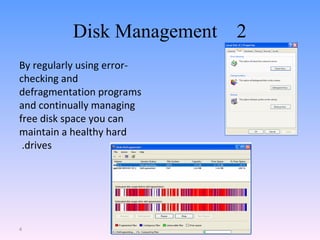
This document provides an overview of how to protect computers from various threats through preventative maintenance, disk management, and security practices. It discusses cleaning internal components and the computer case, using error-checking and defragmentation programs, and managing disk space to prevent issues. The document also covers securing physical equipment from theft, protecting against viruses, worms, trojans, phishing, and using anti-virus software, popup blockers, and spam filters to enhance online security.