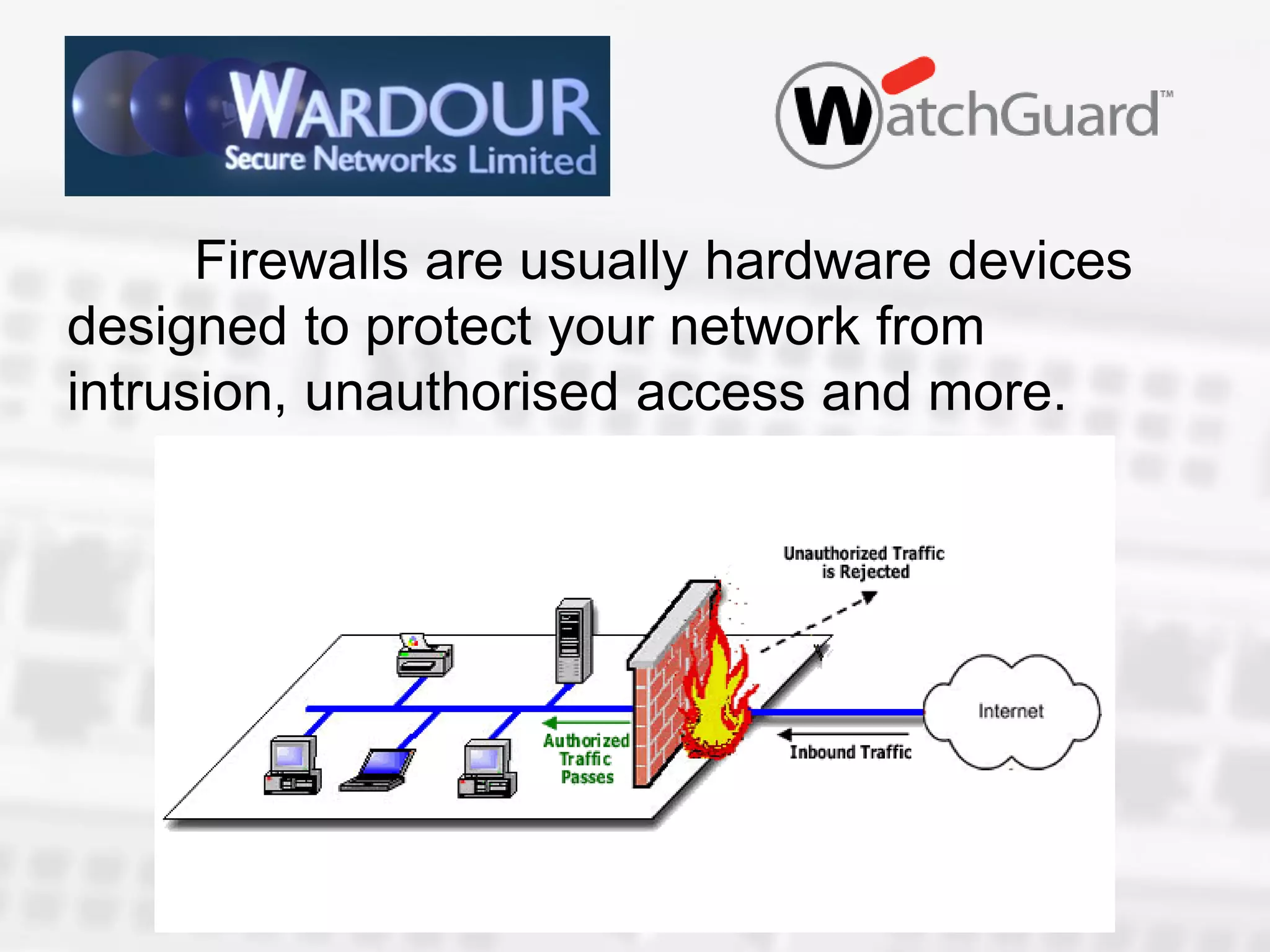
Simon Pell gave a presentation on malware threats facing small businesses. He defined different types of malware like viruses, trojans, worms, and rootkits. Viruses self-replicate and infect files, while trojans and worms do not self-replicate but can still damage files. Rootkits are used to hide other malware. Spyware/adware collects user information without consent. Cookies are small text files that store website preferences. Pell stressed the importance of using updated antivirus software, firewalls, and being cautious of downloads. Firewalls can control network access and applications without slowing performance. Unified threat management provides additional protections like blocking suspicious websites and spam.