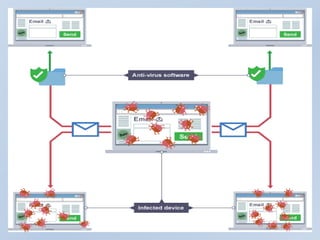
Viruses and malware can damage computers. Viruses spread by copying themselves, while malware is designed to access or harm devices without owner knowledge. Common malware includes adware, bugs, rootkits, Trojans, and ransomware. It is important to use updated antivirus software, strong passwords, firewalls, and be cautious of suspicious links and downloads to protect devices from viruses and malware.