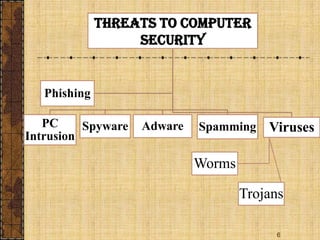
This document discusses computer security threats and solutions. It describes how computers can become insecure if data is not trustworthy or behaves unexpectedly. Common threats include viruses, worms, Trojan horses, spyware, adware, spamming, and PC intrusion. Viruses can damage or delete files, slow computers down, and invade email programs. Spyware and adware track user activities and display unwanted pop-up ads. Spamming disrupts email delivery through bulk messages. Hackers also try to intrude PCs. The document recommends both active protection methods like antivirus software and preventative measures like updating systems and using caution online to secure computers against these threats.