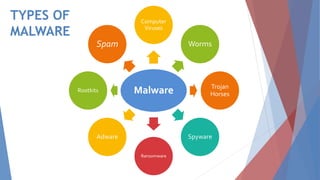
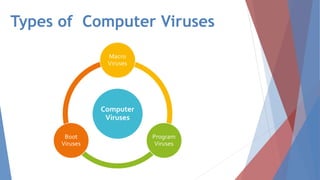
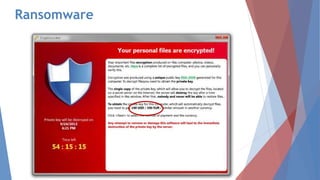
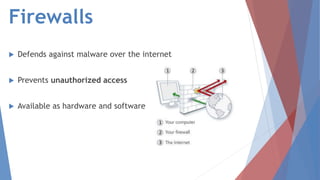
The document discusses malware, defining it as harmful software that steals information and damages computers, detailing various types such as viruses, worms, trojan horses, spyware, ransomware, adware, rootkits, and spam. It also presents methods for detecting, removing, and preventing malware infections, emphasizing the importance of using antivirus software and being cautious with programs and emails. Additionally, the document highlights the significant financial losses caused by malware and urges increased awareness and the development of advanced protective software.