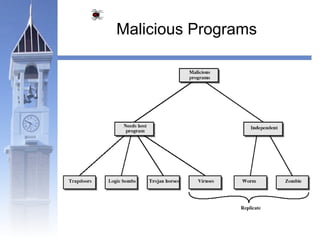
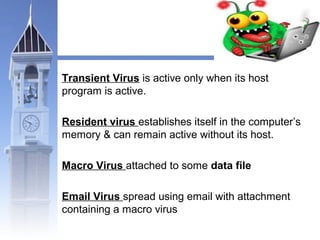
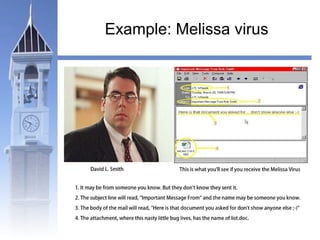
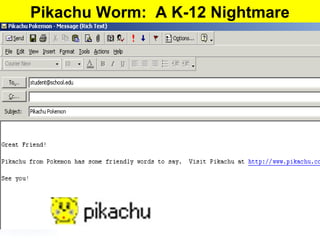
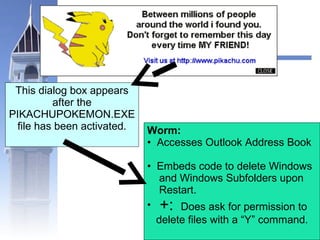
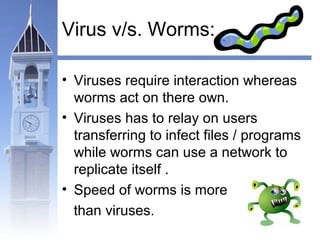
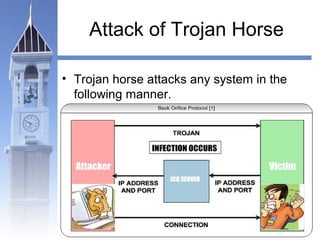
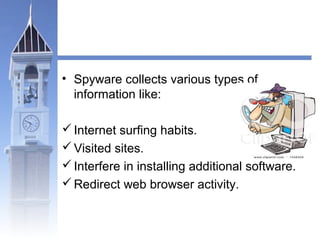
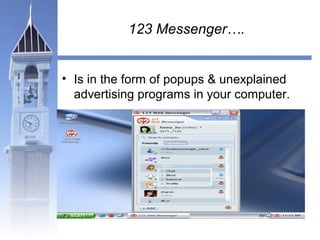
This document discusses different types of malicious programs including viruses, worms, Trojan horses, logic bombs, spyware, and adware. Viruses replicate by inserting copies of themselves into other programs or files. Worms replicate across network connections without needing host programs. Trojan horses appear useful but contain hidden malicious code. Logic bombs trigger when specific conditions occur. Spyware collects user information without consent. Adware automatically displays advertisements. The document provides examples of different malware types and advises users to only install trusted software and keep anti-virus software updated.