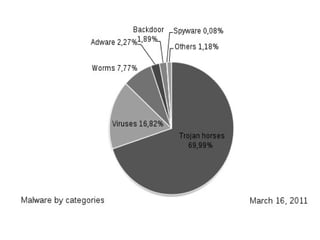
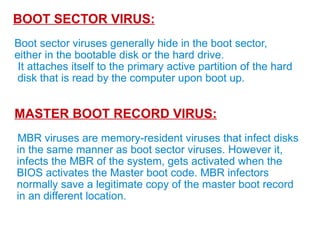
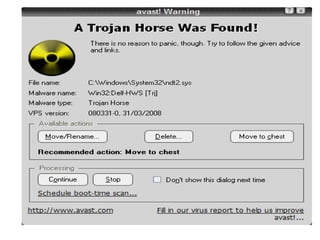
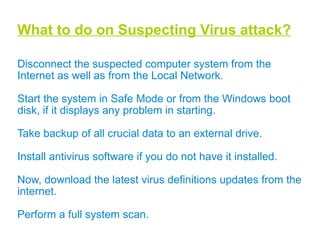
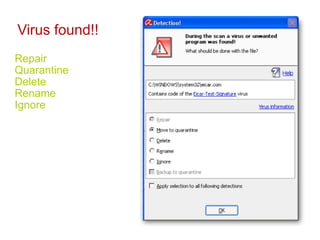
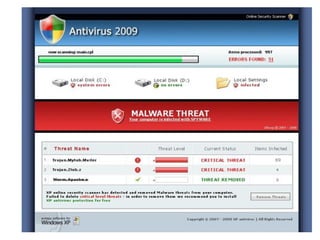
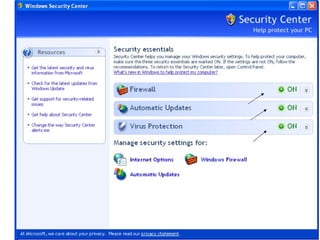
This document discusses malware and provides information about common types of malware like viruses, trojans, worms, spyware, and adware. It then discusses antivirus and anti-spyware software that can be used to protect systems from malware by identifying, removing, and preventing malware infections. Regularly updating antivirus software and scanning systems is recommended to keep systems secure from evolving malware threats.