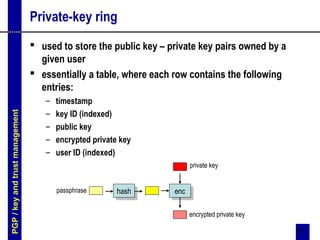
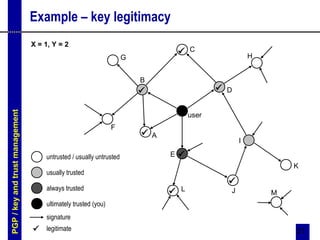
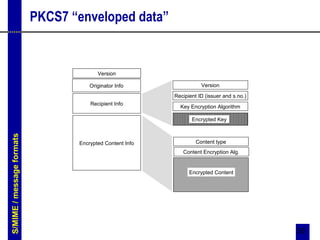
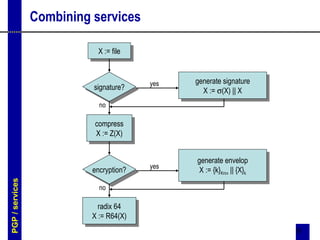
PGP and S/MIME are two standards for securing email. PGP uses asymmetric encryption and digital signatures to provide authentication, confidentiality, and compression of messages. It utilizes public/private key pairs and trust is established through signatures on public keys. S/MIME is an Internet standard that provides similar security services to MIME messages as PGP, using PKI/certificates and industry standard algorithms. Both standards encrypt messages and attach digital signatures to authenticate senders and guarantee message integrity.










![15
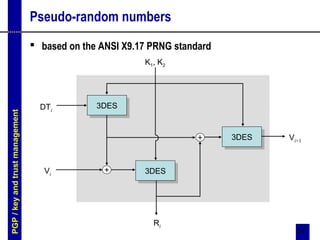
Pseudo-random numbers
EE
EE
EE+
+
EE
EE+
+
EE
EE+
+
+ + +
dtbuf
rseed
rseed’
IV[0..7] K[8..15] K[0..7]
true
random
bits
CAST-128 is used instead of 3DES with key rkey
PGP/keyandtrustmanagement](https://image.slidesharecdn.com/pgpsmime-160113130724/85/Pgp-smime-15-320.jpg)
![16
Pseudo-random numbers
dtbuf[0..3] = current time, dtbuf[4..7] = 0
pre-wash
– take the hash of the message
• this has already been generated if the message is being signed
• otherwise the first 4K of the message is hashed
– use the result as a key, use a null IV, and encrypt (rkey, rseed)previous in
CFB mode
• if (rkey, rseed)previous is empty, it is filled up with true random bits
– set (rkey, rseed)current to the result of the encryption
post-wash
– generate 24 more bytes as before but without XORing in true random
bytes
– encrypt the result in CFB mode using K and IV
– set (rkey, rseed)previous to the result of the encryption
PGP/keyandtrustmanagement](https://image.slidesharecdn.com/pgpsmime-160113130724/85/Pgp-smime-16-320.jpg)