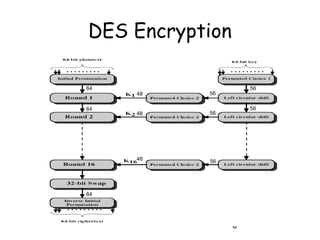
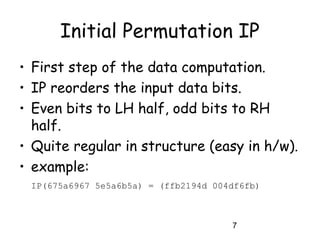
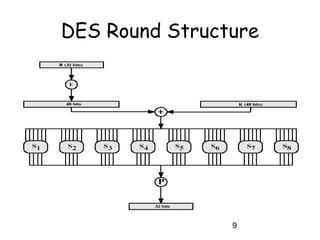
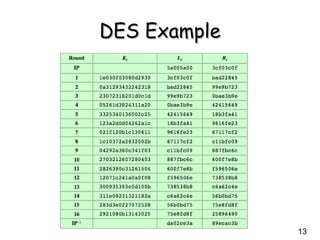
This document provides an overview of the Data Encryption Standard (DES) algorithm. It describes how DES was adopted as a standard in 1977, uses a 64-bit block size and 56-bit key, and has been widely used for encryption. The document outlines the key components of DES, including the initial permutation, round structure using substitution boxes and key schedule, as well as the decryption process. It notes that while DES was controversial due to its 56-bit key size, it exhibits good diffusion properties. However, it has been shown to be vulnerable to brute force and timing attacks in recent years.