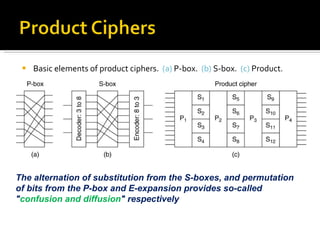
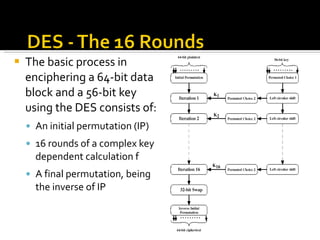
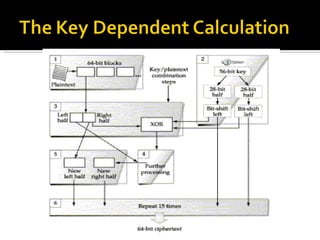
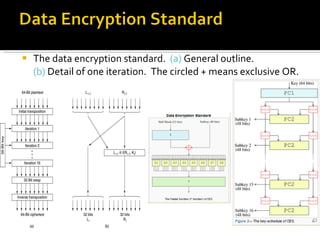
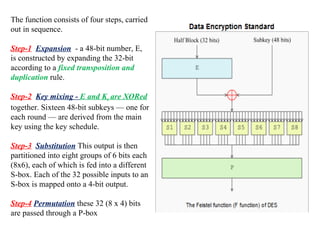
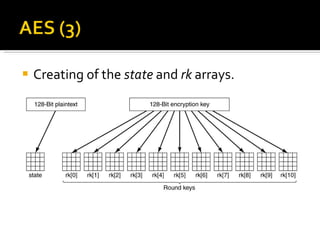
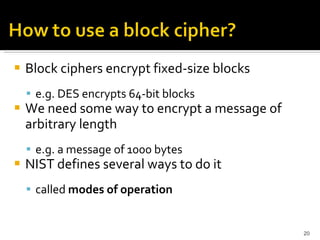
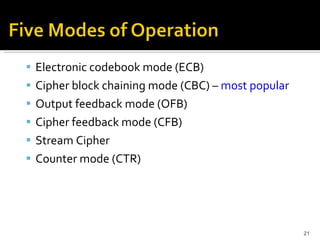
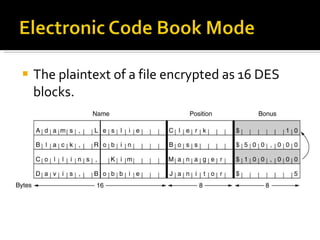
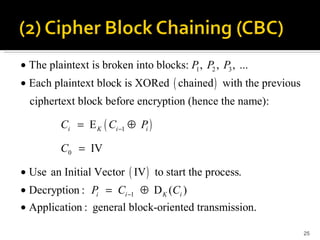
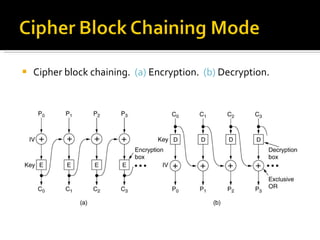
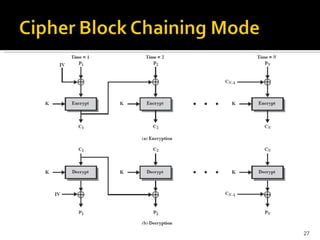
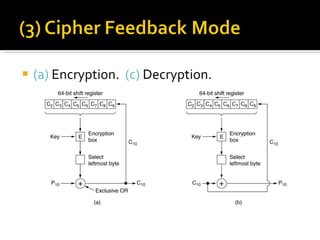
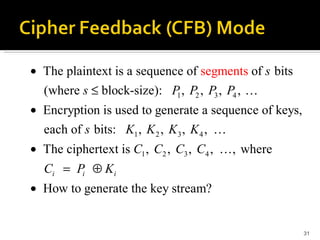
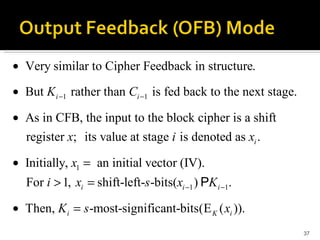
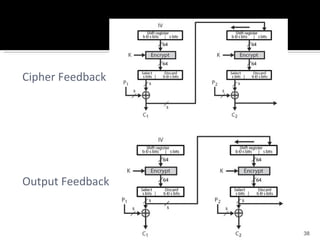
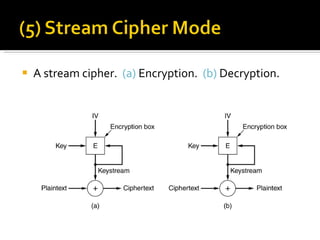
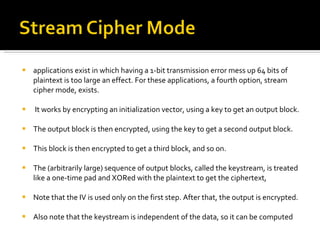
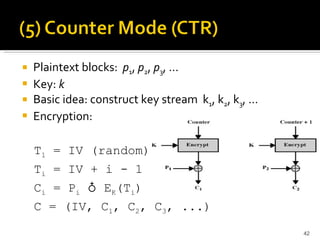
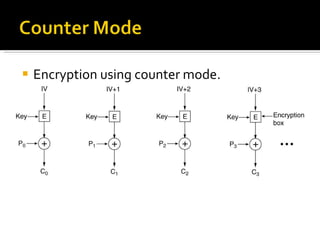
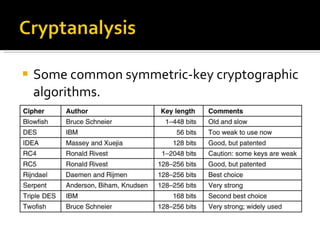
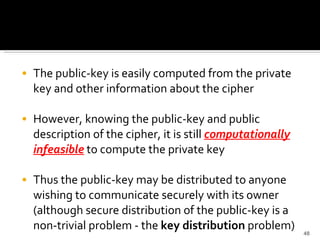
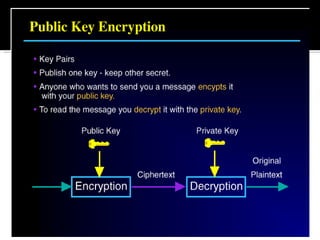
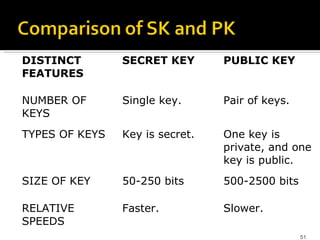
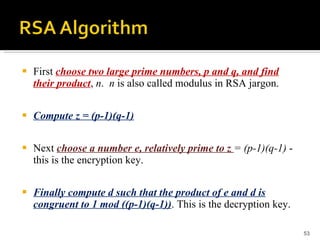
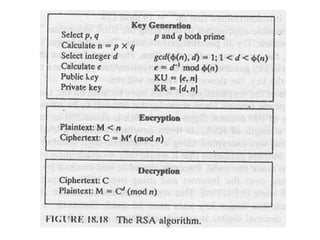
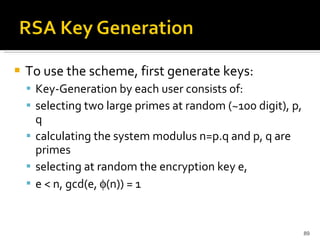
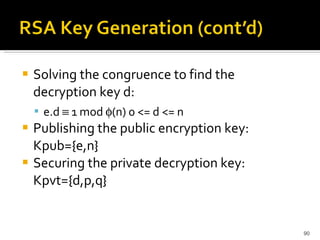
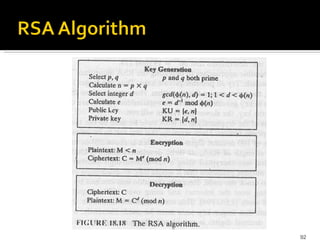
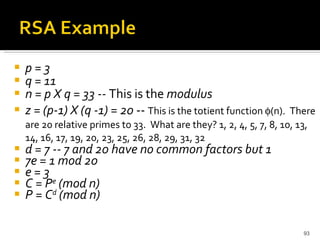
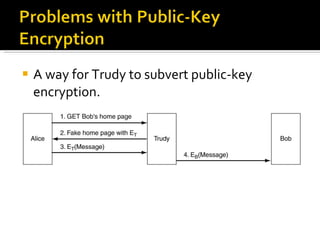
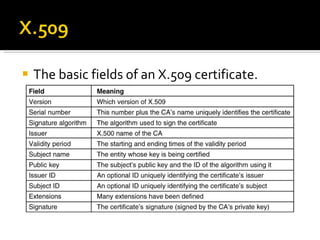
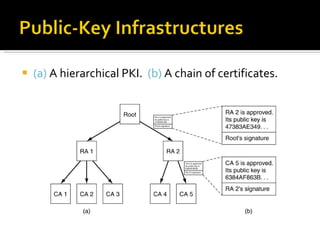
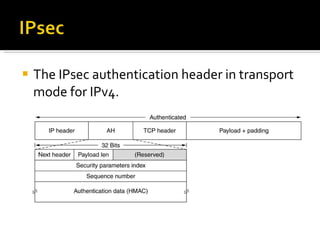
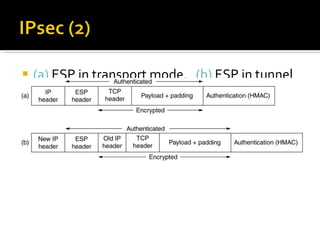
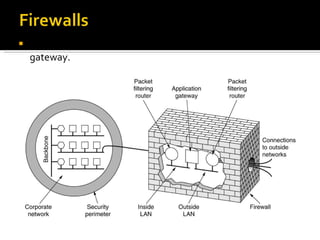
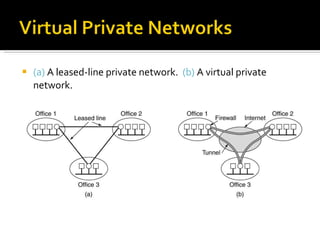
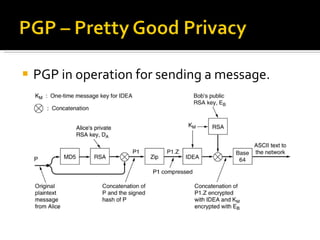
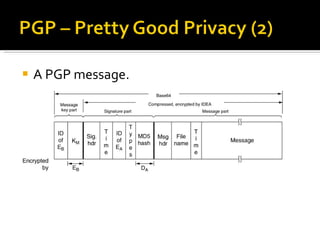
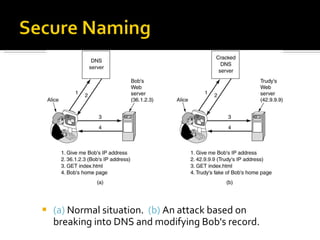
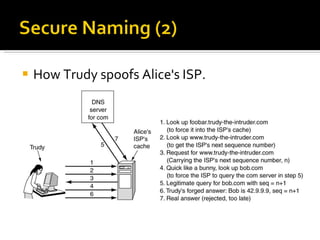
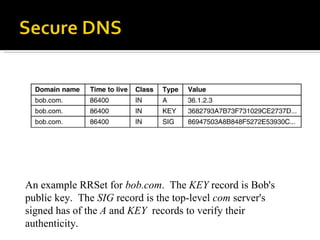
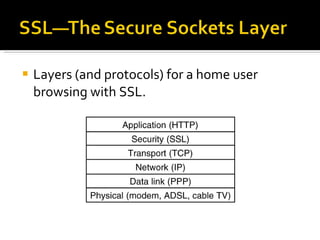
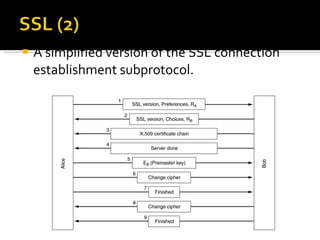
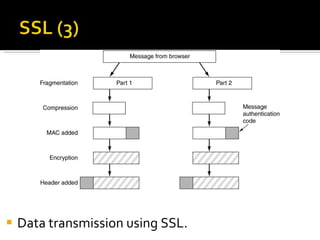
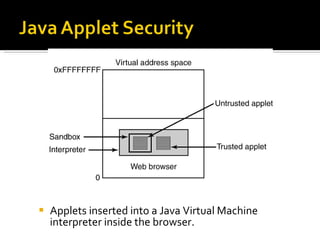
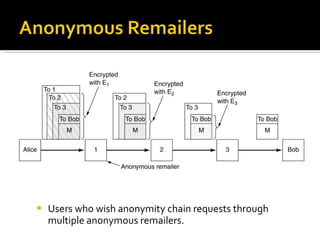
The document discusses cryptography concepts including symmetric and asymmetric encryption algorithms like DES, AES, RSA. It explains the basic working principles of RSA including key generation using large prime numbers, modular arithmetic and the concept of one-way functions that make private key derivation difficult. It also covers cryptographic modes of operation like ECB, CBC that are used to encrypt data blocks of arbitrary length.





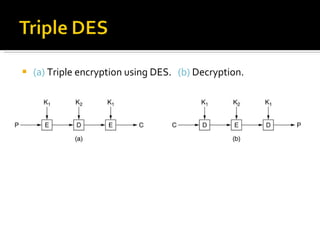
![Triple DES uses a "key bundle" which comprises three DES keys, K1, K2 and K3, each of 56 bits (excluding parity bits). The encryption algorithm is: ciphertext = EK3(DK2(EK1(plaintext))) I.e., DES encrypt with K1, DES decrypt with K2, then DES encrypt with K3. Decryption is the reverse: plaintext = DK1(EK2(DK3(ciphertext))) I.e., decrypt with K3, encrypt with K2, then decrypt with K1. Each triple encryption encrypts one block of 64 bits of data. In each case the middle operation is the reverse of the first and last. This improves the strength of the algorithm when using keying option 2, and provides backward compatibility with DES with keying option 3. [edit] Keying options The standards define three keying options: Keying option 1: All three keys are independent. Keying option 2: K1 and K2 are independent, and K3 = K1. Keying option 3: All three keys are identical, i.e. K1 = K2 = K3. Keying option 1 is the strongest, with 3 × 56 = 168 independent key bits. Keying option 2 provides less security, with 2 × 56 = 112 key bits. This option is stronger than simply DES encrypting twice, e.g. with K1 and K2, because it protects against meet-in-the-middle attacks. Keying option 3 is equivalent to DES, with only 56 key bits. This option provides backward compatibility with DES, because the first and second DES operations cancel out](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-16-320.jpg)







































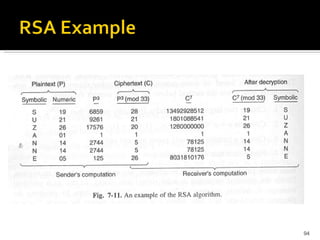










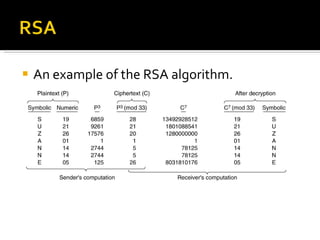
![RSA is part of many official standards worldwide. The ISO (International Standards Organization) 9796 standard lists RSA as a compatible cryptographic algorithm, as does the ITU-T X.509 security standard. RSA is part of the Society for Worldwide Interbank Financial Telecommunications (SWIFT) standard, the French financial industry's ETEBAC 5 standard, the ANSI X9.31 rDSA standard and the X9.44 draft standard for the U.S. banking industry. The Australian key management standard, AS2805.6.5.3, also specifies RSA. RSA is found in Internet standards and proposed protocols including S/MIME IPSec, and TLS, the Internet standards-track successor to SSL, as well as the PKCS standard for the software industry. The OSI Implementers' Workshop (OIW) has issued implementers' agreements referring to PKCS, which includes RSA. A number of other standards are currently being developed and will be announced over the next few years; many are expected to include RSA as either an endorsed or a recommended system for privacy and/or authentication. A comprehensive survey of cryptography standards can be found in publications by Kaliski [ Kal93b ] and Ford [ For94 ].](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-105-320.jpg)



![The speed and efficiency of the many commercially available software and hardware implementations of RSA are increasing rapidly. On a 90 MHz Pentium, has a throughput for private-key operations of 21.6 kbits per second with a 512-bit modulus and 7.4 kbits per second with a 1024-bit modulus. The fastest RSA hardware has a throughput greater than 300 kbits per second with a 512-bit modulus, implying that it performs over 500 RSA private-key operations per second (There is room in that hardware to execute two RSA 512-bit RSA operations in parallel, hence the 600 kbits/s speed reported in [ SV93 ]. For 970-bit keys, the throughput is 185 kbits/s.). It is expected that RSA speeds will reach 1 mbits/second in late 1999.](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-109-320.jpg)








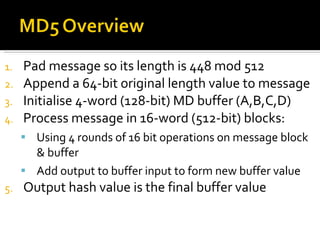

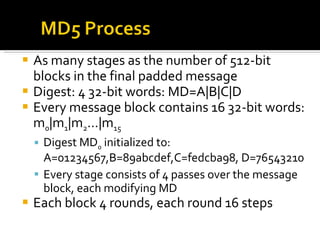
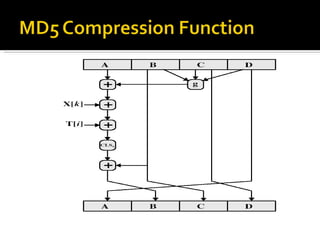
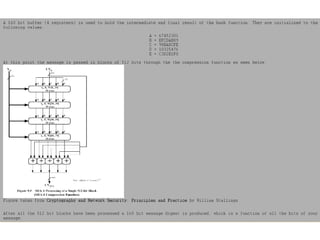
![ABCD=f F (ABCD,m i ,T[1..16]) ABCD=f G (ABCD,m i ,T[17..32]) ABCD=f H (ABCD,m i ,T[33..48]) ABCD=f I (ABCD,m i ,T[49..64]) m i + + + + A B C D MD i MD i+1](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-124-320.jpg)

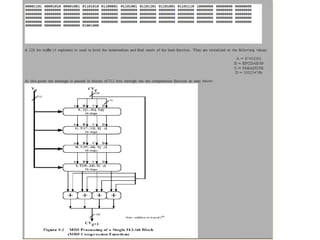
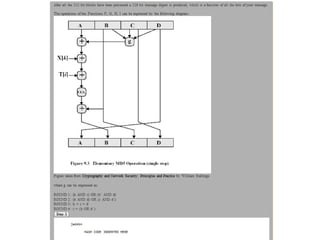

![Each round has 16 steps of the form: a = b+((a+g(b,c,d)+X[k]+T[i])<<<s) a,b,c,d refer to the 4 words of the buffer, but used in varying permutations note this updates 1 word only of the buffer after 16 steps each word is updated 4 times where g(b,c,d) is a different nonlinear function in each round (F,G,H,I)](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-129-320.jpg)

















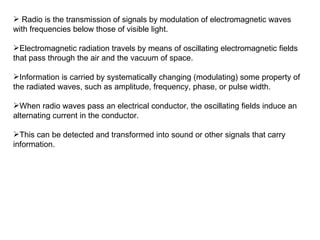

![Processes Radio systems used for communications will have the following elements. With more than 100 years of development, each process is implemented by a wide range of methods, specialized for different communications purposes. Each system contains a transmitter. This consists of a source of electrical energy, producing alternating current of a desired frequency of oscillation. The transmitter contains a system to modulate (change) some property of the energy produced to impress a signal on it. This modulation might be as simple as turning the energy on and off, or altering more subtle properties such as amplitude, frequency, phase, or combinations of these properties. The transmitter sends the modulated electrical energy to a tuned resonant antenna; this structure converts the rapidly-changing alternating current into an electromagnetic wave that can move through free space (sometimes with a particular polarization (waves)). Electromagnetic waves travel through space either directly, or have their path altered by reflection, refraction or diffraction. The intensity of the waves diminishes due to geometric dispersion (the inverse-square law); some energy may also be absorbed by the intervening medium in some cases. Noise will generally alter the desired signal; this electromagnetic interference comes from natural sources, as well as from artificial sources such as other transmitters and accidental radiators. Noise is also produced at every step due to the inherent properties of the devices used. If the magnitude of the noise is large enough, the desired signal will no longer be discernible; this is the fundamental limit to the range of radio communications. The electromagnetic wave is intercepted by a tuned receiving antenna; this structure captures some of the energy of the wave and returns it to the form of oscillating electrical currents. At the receiver, these currents are demodulated, which is conversion to a usable signal form by a detector sub-system. The receiver is "tuned" to respond preferentially to the desired signals, and reject undesired signals. Early radio systems relied entirely on the energy collected by an antenna to produce signals for the operator. Radio became more useful after the invention of electronic devices such as the vacuum tube and later the transistor, which made it possible to amplify weak signals. Today radio systems are used for applications from walkie-talkie children's toys to the control of space vehicles, as well as for broadcasting, and many other applications. Electromagnetic spectrum Main article: Electromagnetic spectrum Radio frequencies occupy the range from a few tens of hertz to three hundred gigahertz, although commercially important uses of radio use only a small part of this spectrum.[2] Other types of electromagnetic radiation, with frequencies above the RF range, are microwave, infrared, visible light, ultraviolet, X-rays and gamma rays. Since the energy of an individual photon of radio frequency is too low to remove an electron from an atom, radio waves are classified as non-ionizing radiation.](https://image.slidesharecdn.com/jaimin-chp-8-networksecurity-new-usethis-2011batch-110406051154-phpapp01/85/Jaimin-chp-8-network-security-new-use-this-2011-batch-191-320.jpg)