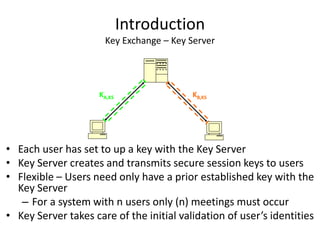
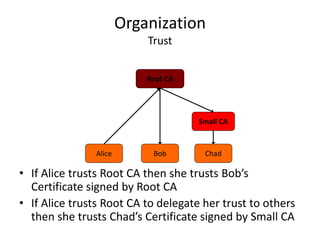
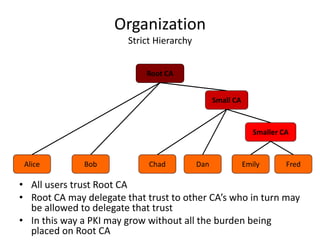
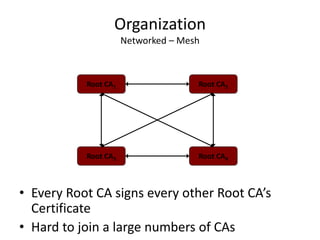
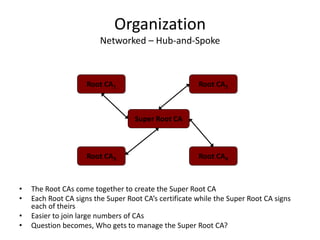
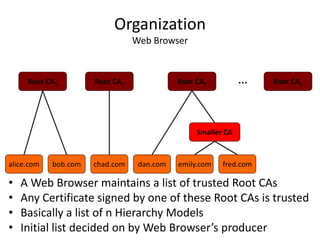
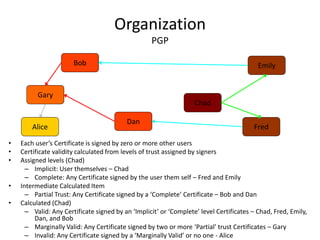
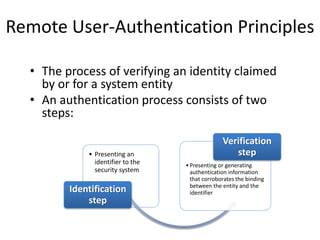
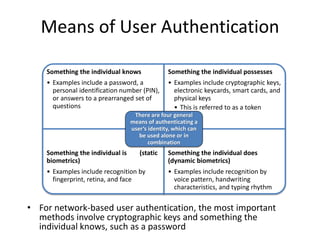
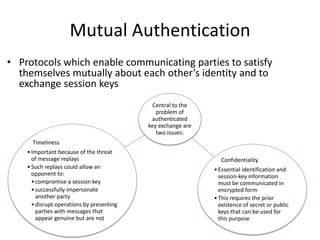
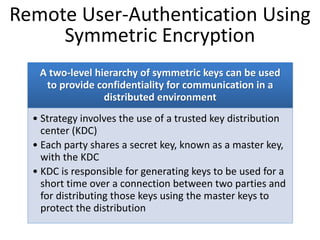
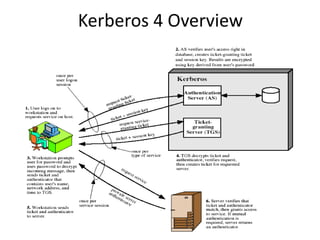
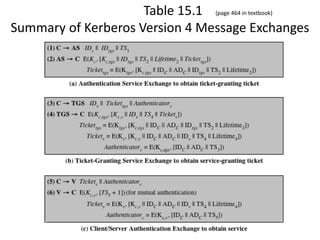
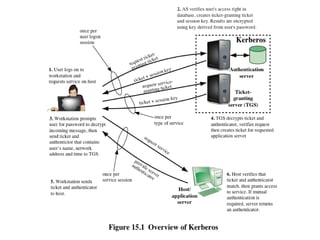
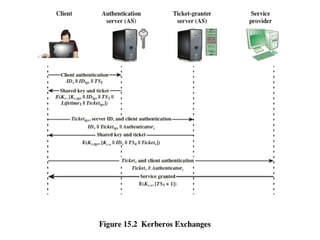
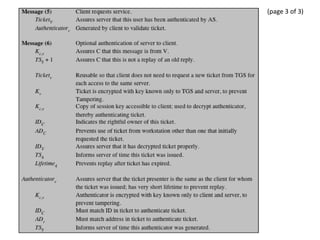
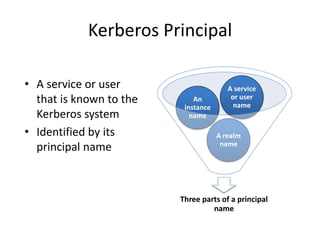
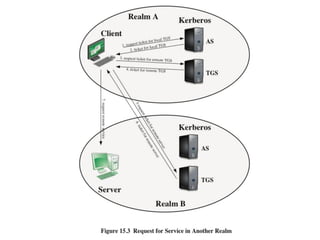
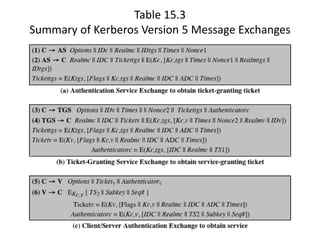
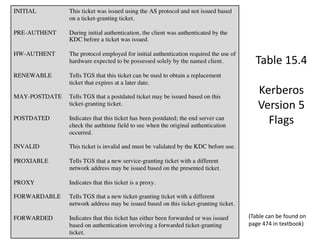
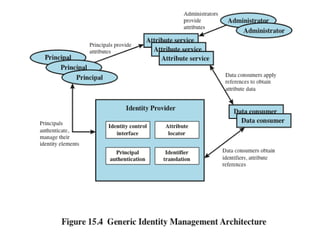
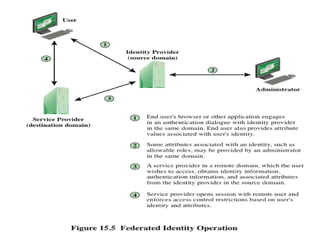
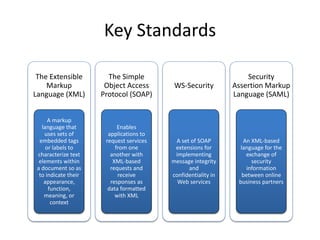
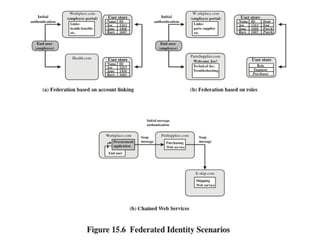
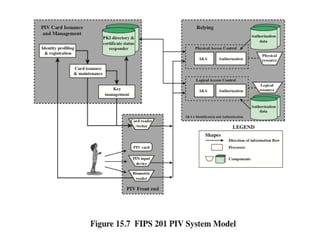
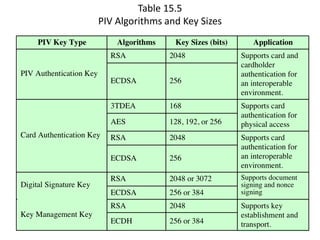
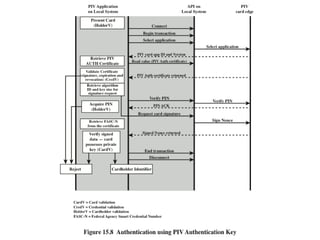
The document discusses key concepts in public key infrastructure (PKI) including X.509 certificates, certification authorities, certificate hierarchies, and certificate extensions.
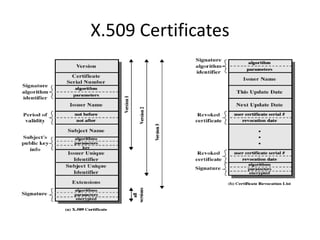
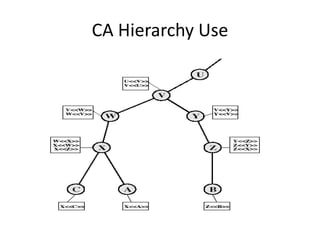
It describes how X.509 certificates contain a user's public key and identification information that is digitally signed by a certification authority. Certification authorities issue and manage certificates according to PKI organization models like strict hierarchies and cross-certification. Certificate revocation lists are used to invalidate compromised certificates. The document outlines authentication protocols using digital signatures and discusses extensions that provide additional certificate information.