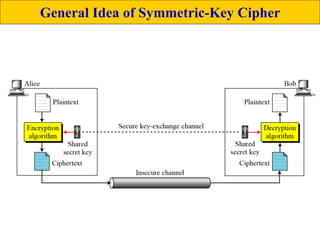
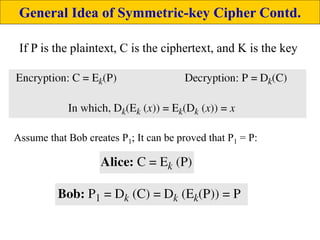
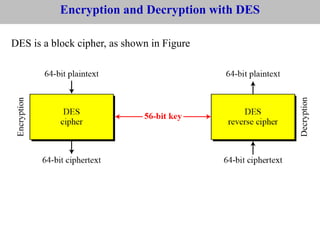
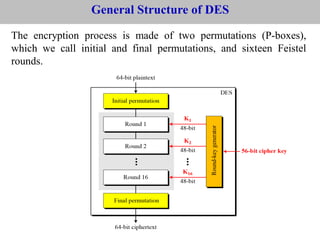
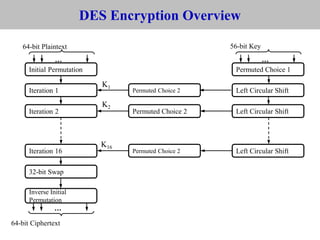
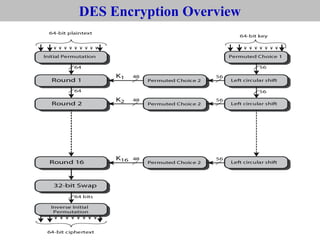
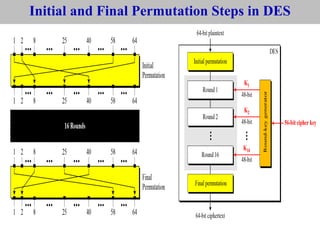
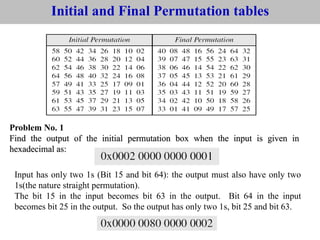
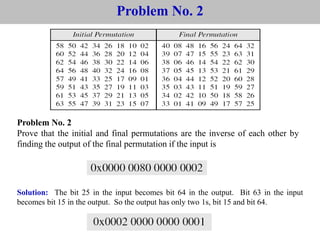
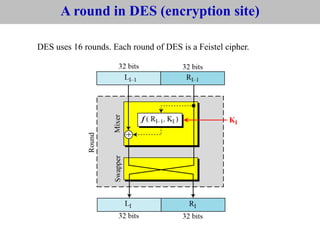
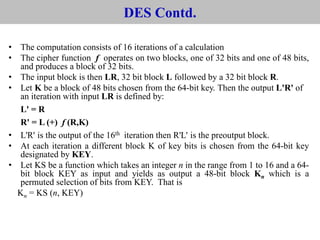
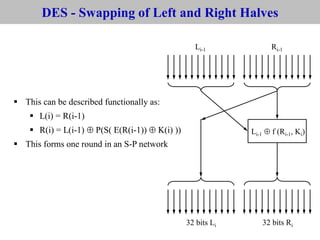
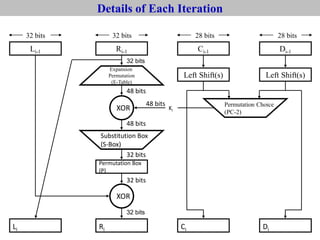
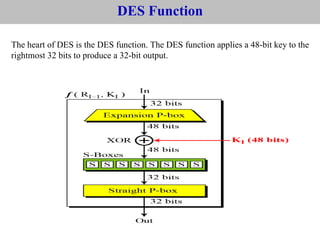
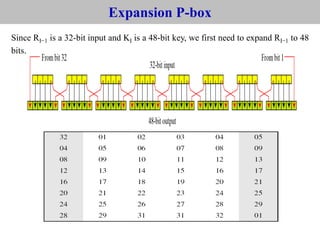
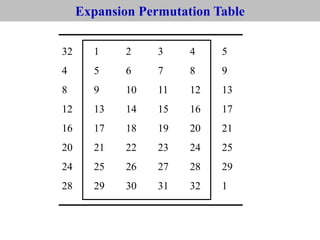
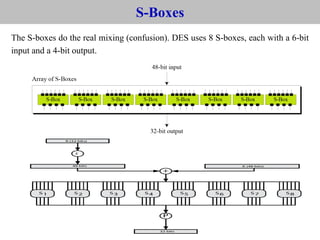
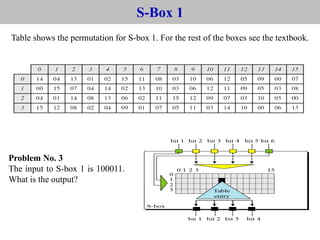
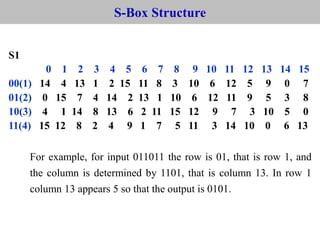
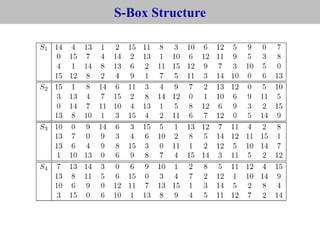
The document provides an overview of cyber security concepts and the Data Encryption Standard (DES) algorithm. It defines key terminology like plaintext, ciphertext, encryption, decryption, and cryptography. It explains that DES is a symmetric block cipher that encrypts data in 64-bit blocks using a 56-bit key. DES operates by performing an initial permutation on the plaintext, then uses 16 rounds of encryption involving substitution boxes and key-dependent permutation/XOR operations to generate the ciphertext.