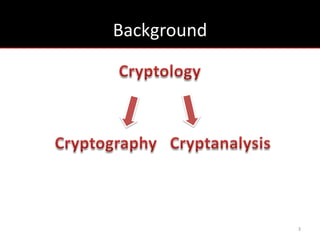
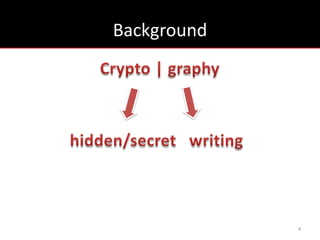
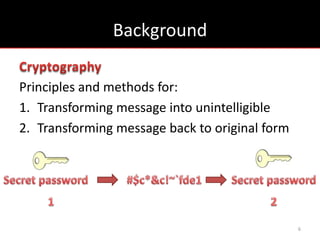
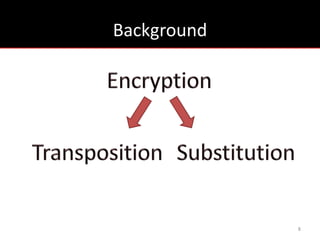
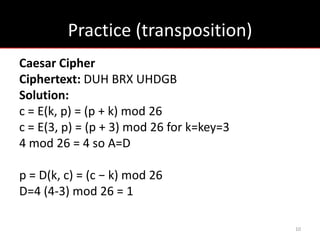
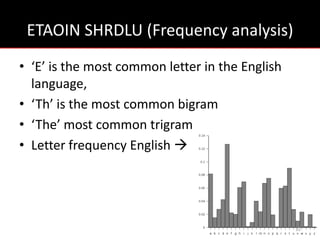
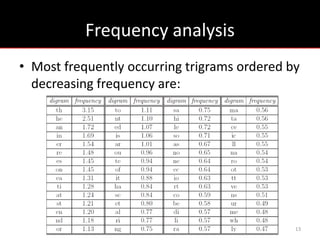
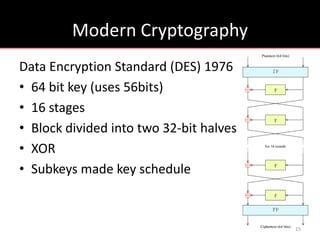
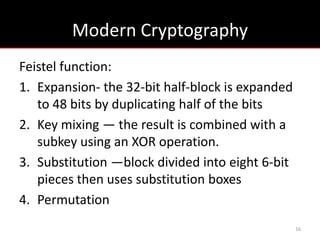
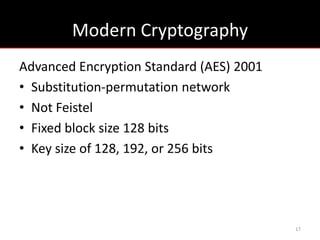
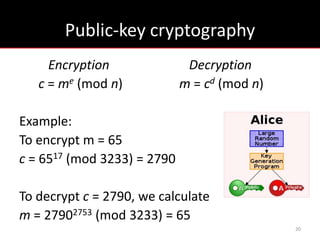
The document provides an overview of cryptology, covering ancient to modern cryptography methods, including encryption techniques such as the Caesar cipher, Vigenère cipher, and public-key cryptography like RSA. It discusses the principles of encryption and decryption, highlighting the significance of frequency analysis and secure communication protocols. Additionally, it outlines some tools used in file encryption and network security.