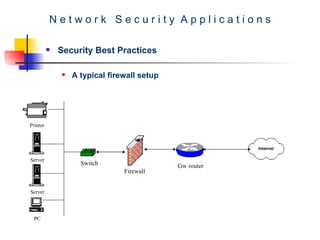
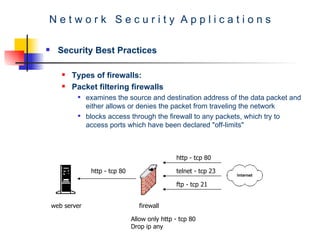
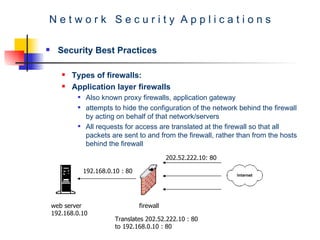
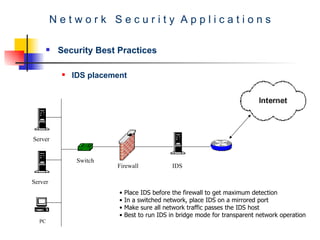
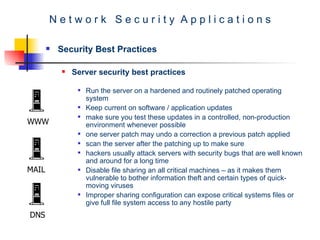
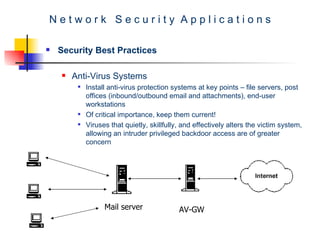
The document discusses network security best practices. It covers common network security risks due to issues with the TCP/IP protocol. It then discusses mistakes that users and IT professionals make that compromise security. The document outlines various security best practices for networks, firewalls, intrusion detection systems, and host-level security. These include recommendations around backups, access control, firewall configurations, personal firewalls, and keeping systems patched.
![N e t w o r k S e c u r i t y A p p l i c a t i o n s CAN IT Conference 2003 Ritesh Raj Joshi Manager (Technical) Mercantile Communications [email_address]](https://image.slidesharecdn.com/network-security-tools-and-applications3549/75/Network-Security-Tools-and-applications-1-2048.jpg)