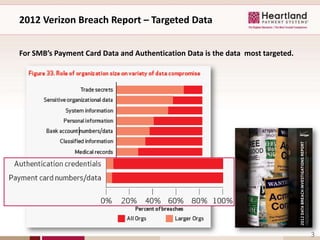
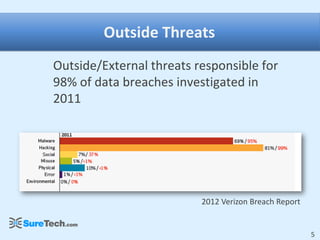
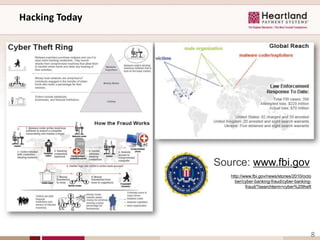
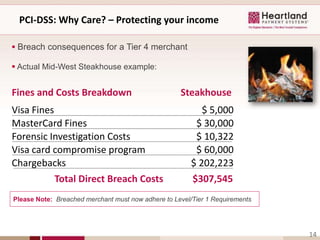
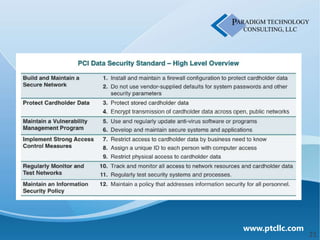
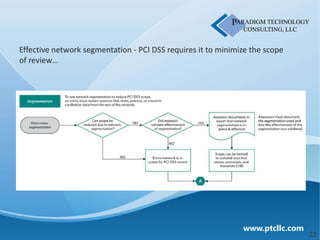
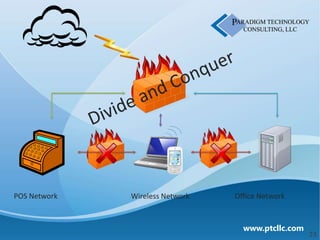
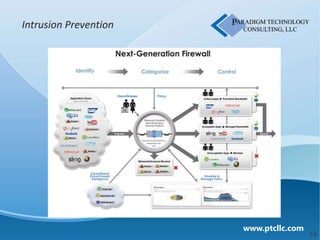
This document discusses business security insights and highlights key points from the 2012 Verizon Breach Report. It summarizes that small and medium businesses are now the preferred targets for payment card and authentication data theft. Over two-thirds of breaches investigated in 2011 were at small and medium businesses. While outside threats were responsible for most breaches, inside threats like data loss, remote access issues, and human error also pose risks. The document outlines different technical, physical, network, endpoint, and operational security layers businesses should implement and maintain to protect themselves, as well as issues like compliance, costs of prevention versus remediation, and the role of insurance.