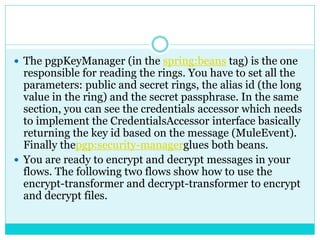
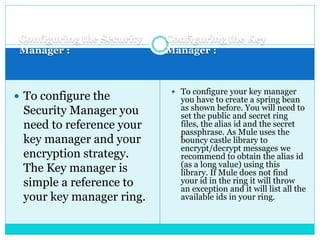
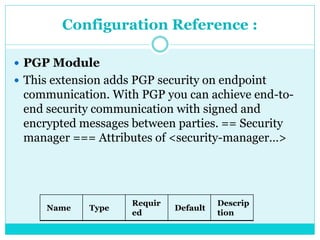
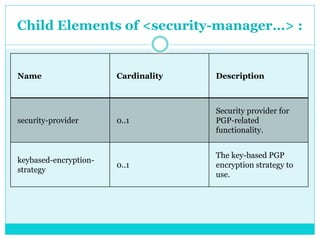
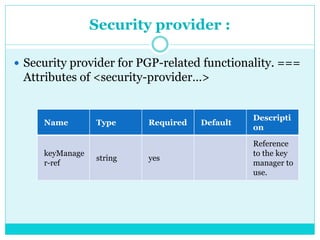
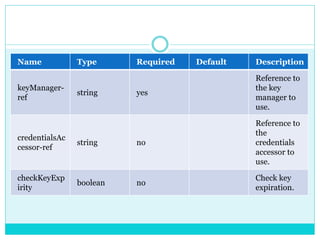
This document discusses how to configure Pretty Good Privacy (PGP) security on Mule connectors. PGP provides encryption and authentication for data communication. Key elements needed for PGP include a security manager, key manager, and credential accessor. The security manager holds encryption strategy and key rings. The key manager reads the key rings and requires configuration of public/secret rings, alias ID, and passphrase. The credential accessor determines the key ID to use for encryption/decryption based on message contents. Examples show configuring these elements and using encrypt/decrypt transformers.