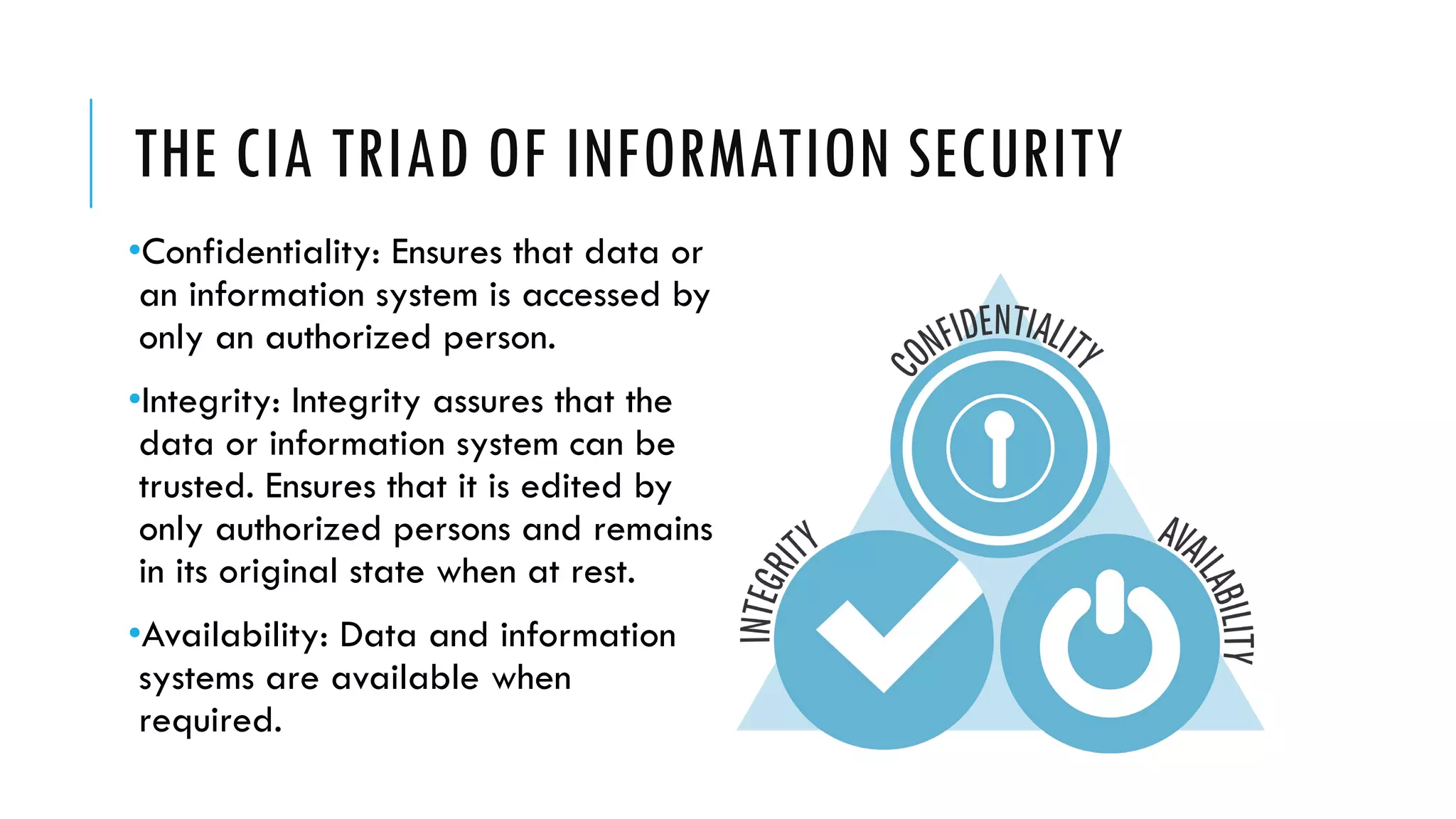
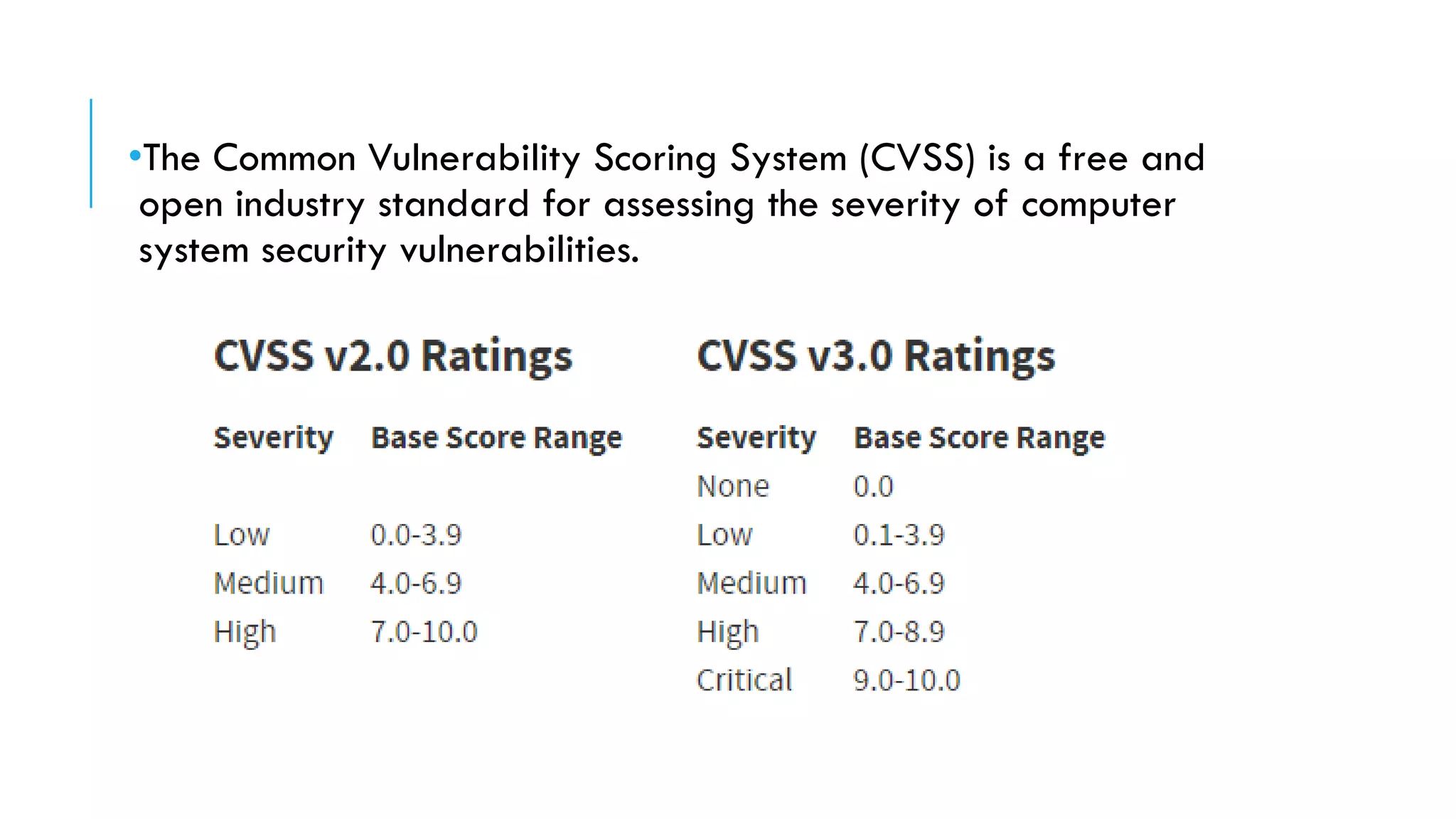
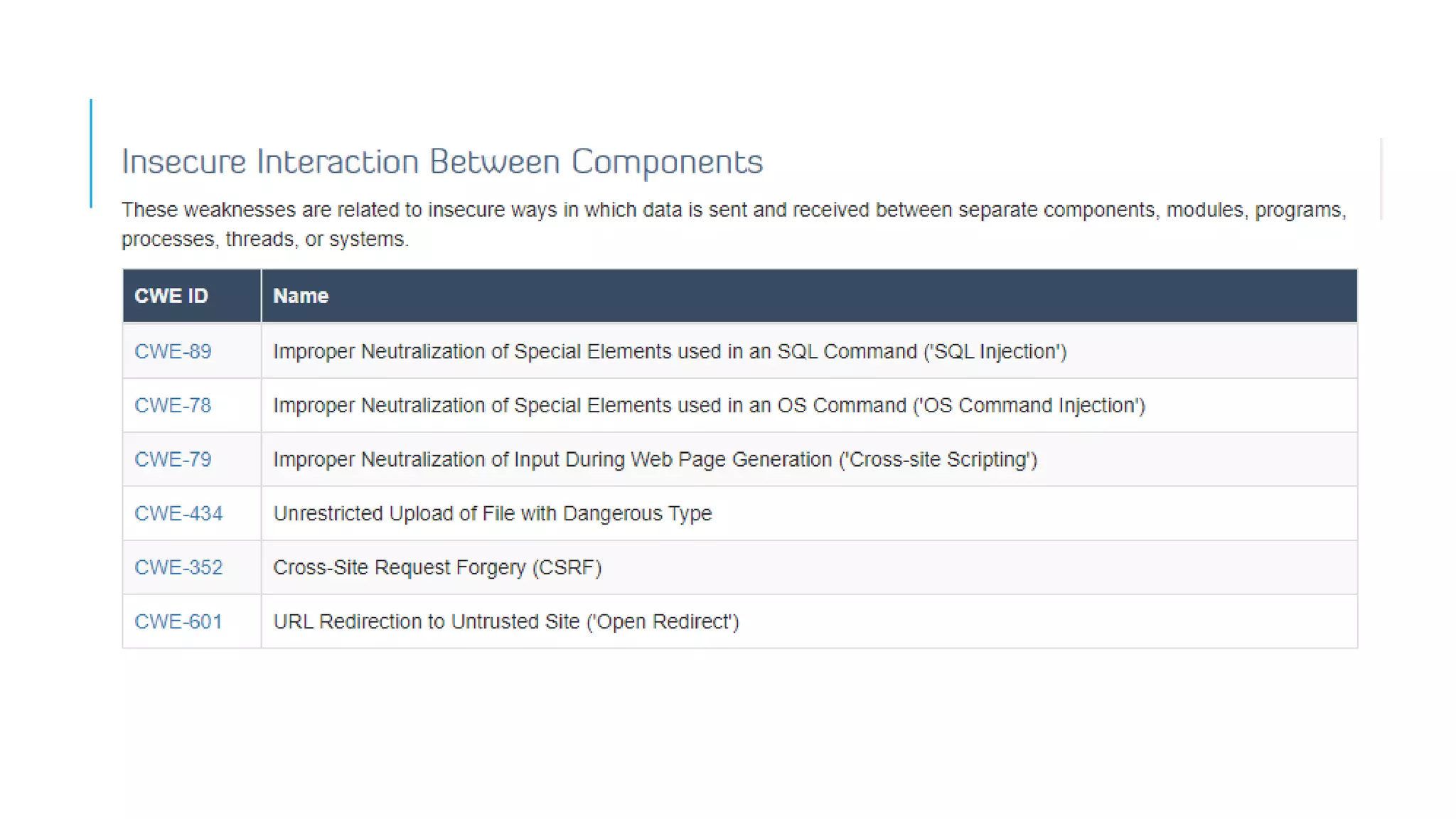
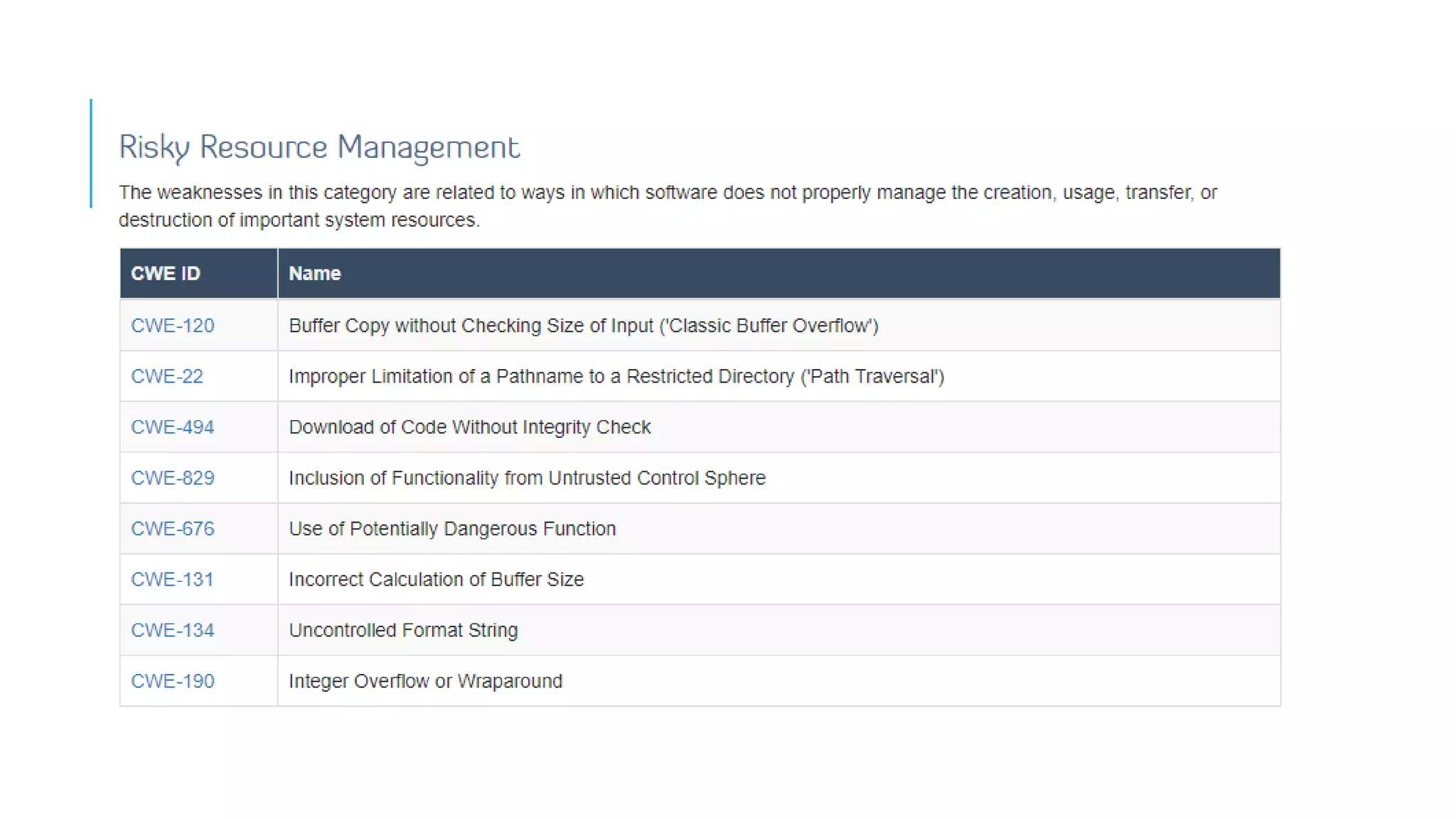
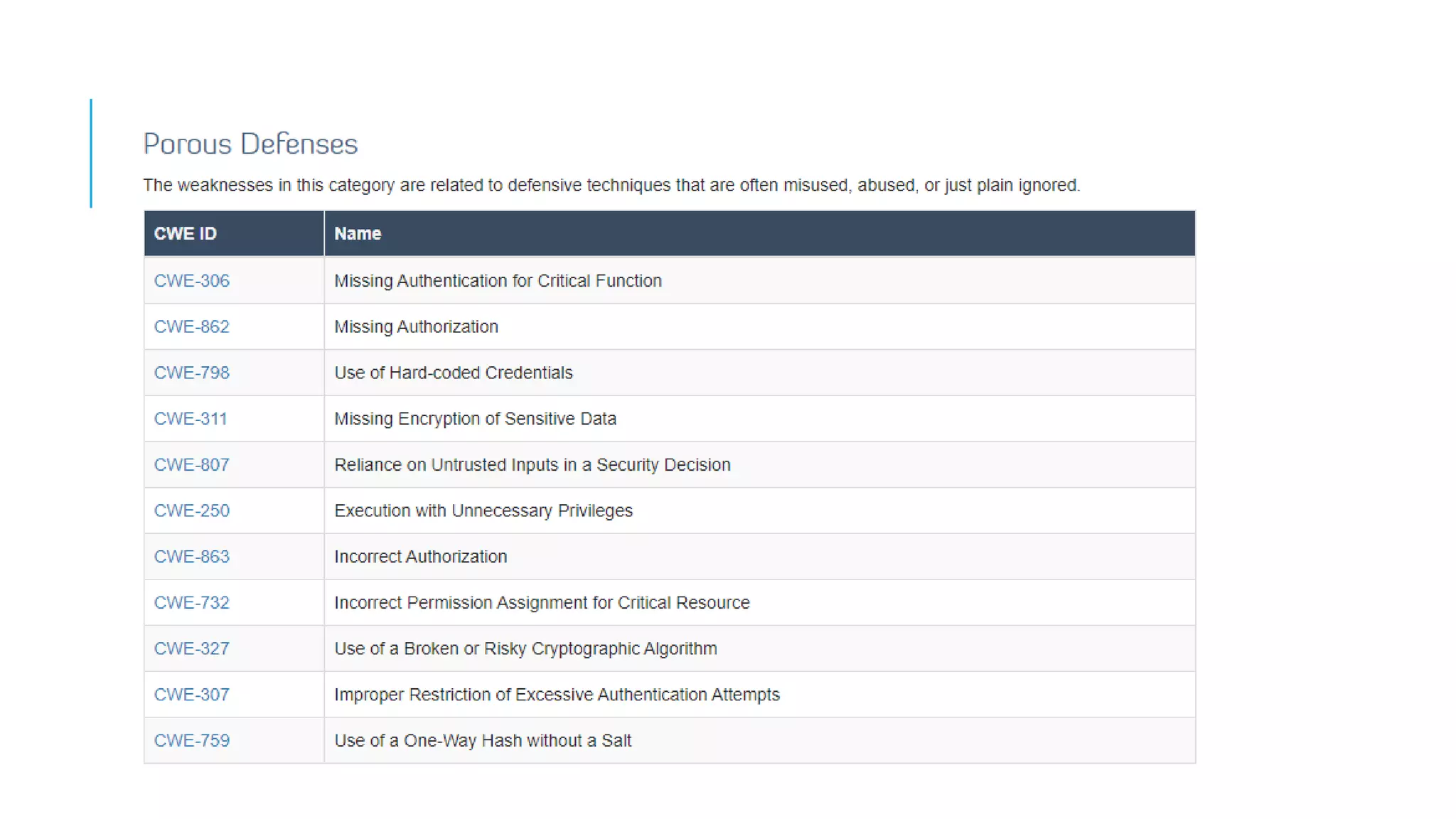
The document provides an overview of cybersecurity, covering its market growth, cyber crime statistics, and career opportunities in the field. It outlines key concepts such as the CIA triad of information security and includes demonstrations of security tools like Wireshark, Nmap, and Nessus. Additionally, it details various cybersecurity roles, their responsibilities, salaries, and necessary certifications.