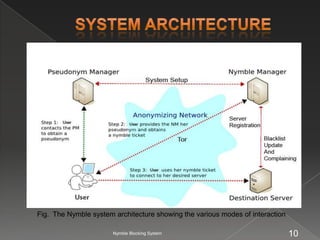
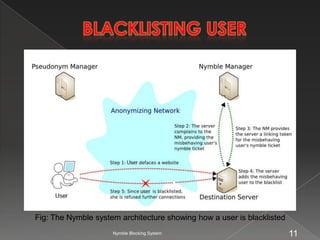
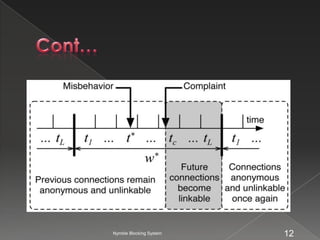
The document describes the Nymble blocking system, which allows websites to selectively blacklist users of anonymizing networks without seeing their IP addresses. It maintains users' anonymity while blocking blacklisted users from future connections. The system architecture includes users, a pseudonym manager, Nymble manager, and servers. It aims to achieve blacklistability, rate-limiting, nonframeability, and anonymity.