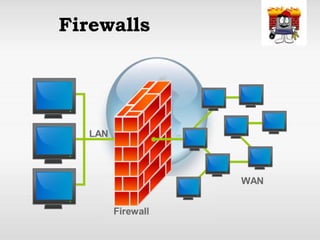
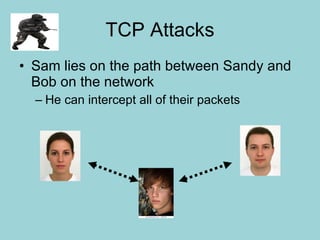
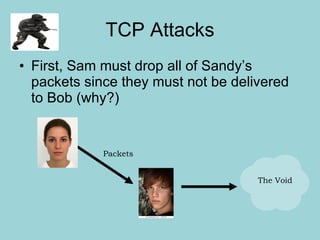
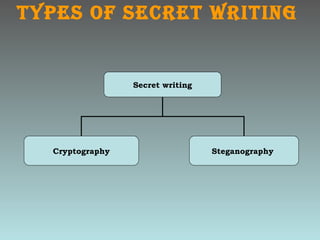
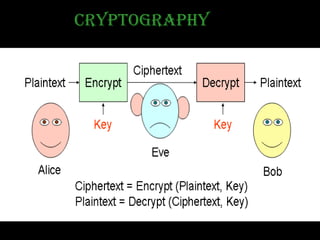
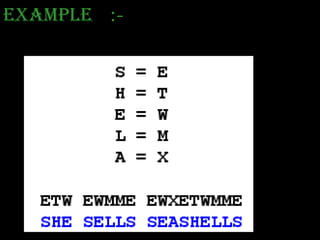
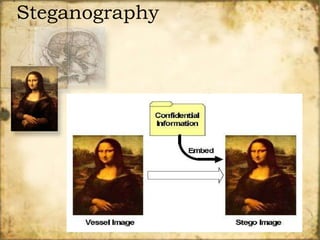
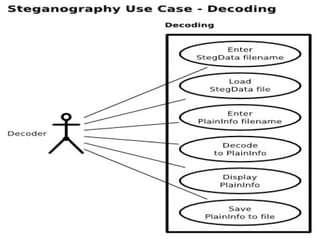
Network security involves protecting computer networks through tools like firewalls, encryption, and digital signatures. Common security threats include TCP hijacking, packet sniffing, and unauthorized access to networks. Cryptography and steganography are methods used to secure communications and information. Cryptography involves encrypting data using techniques like public key infrastructure, while steganography hides secret messages within ordinary files like images or audio files. Both have benefits but also limitations, as strong encryption does not guarantee security if other vulnerabilities exist.