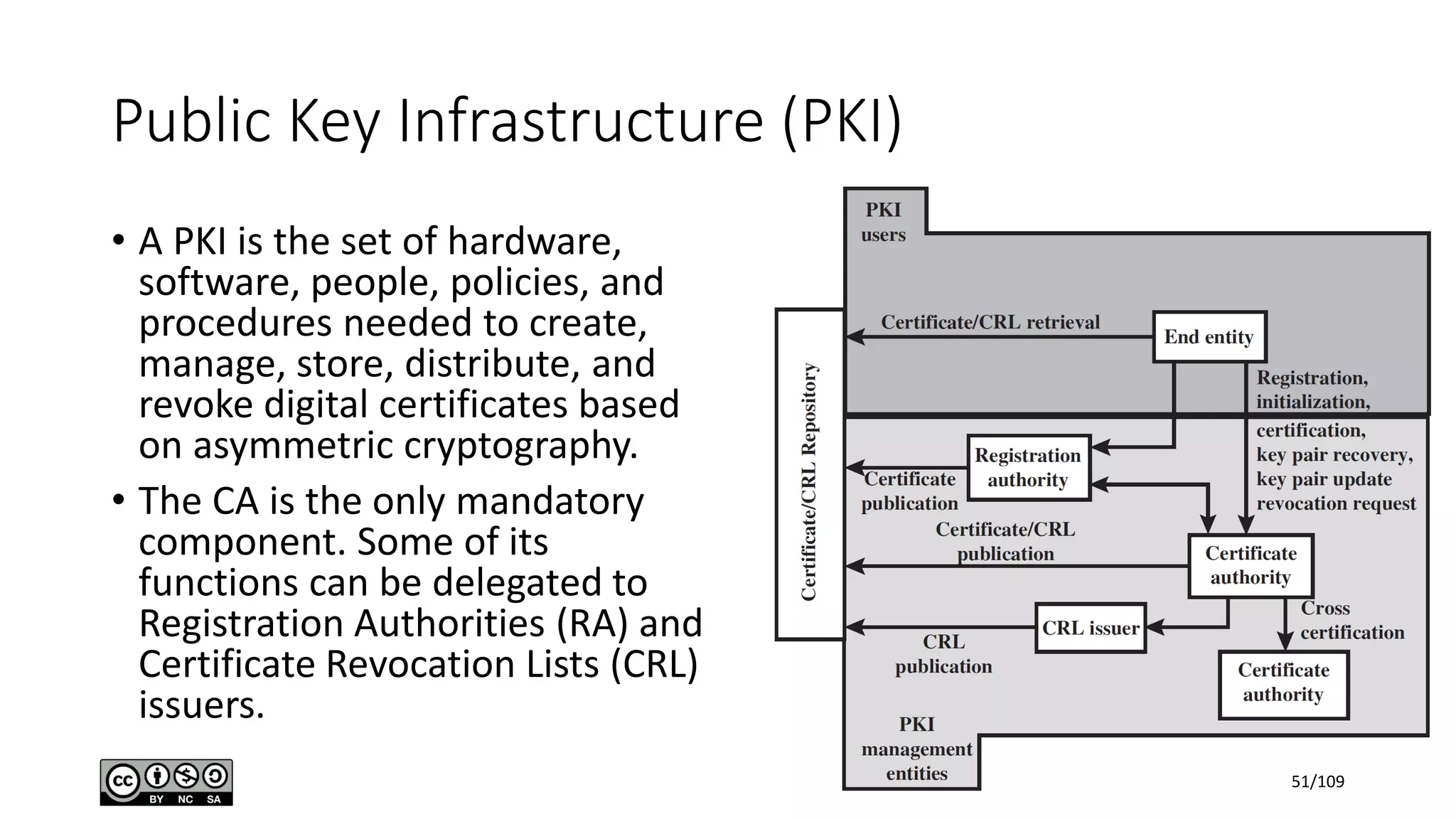
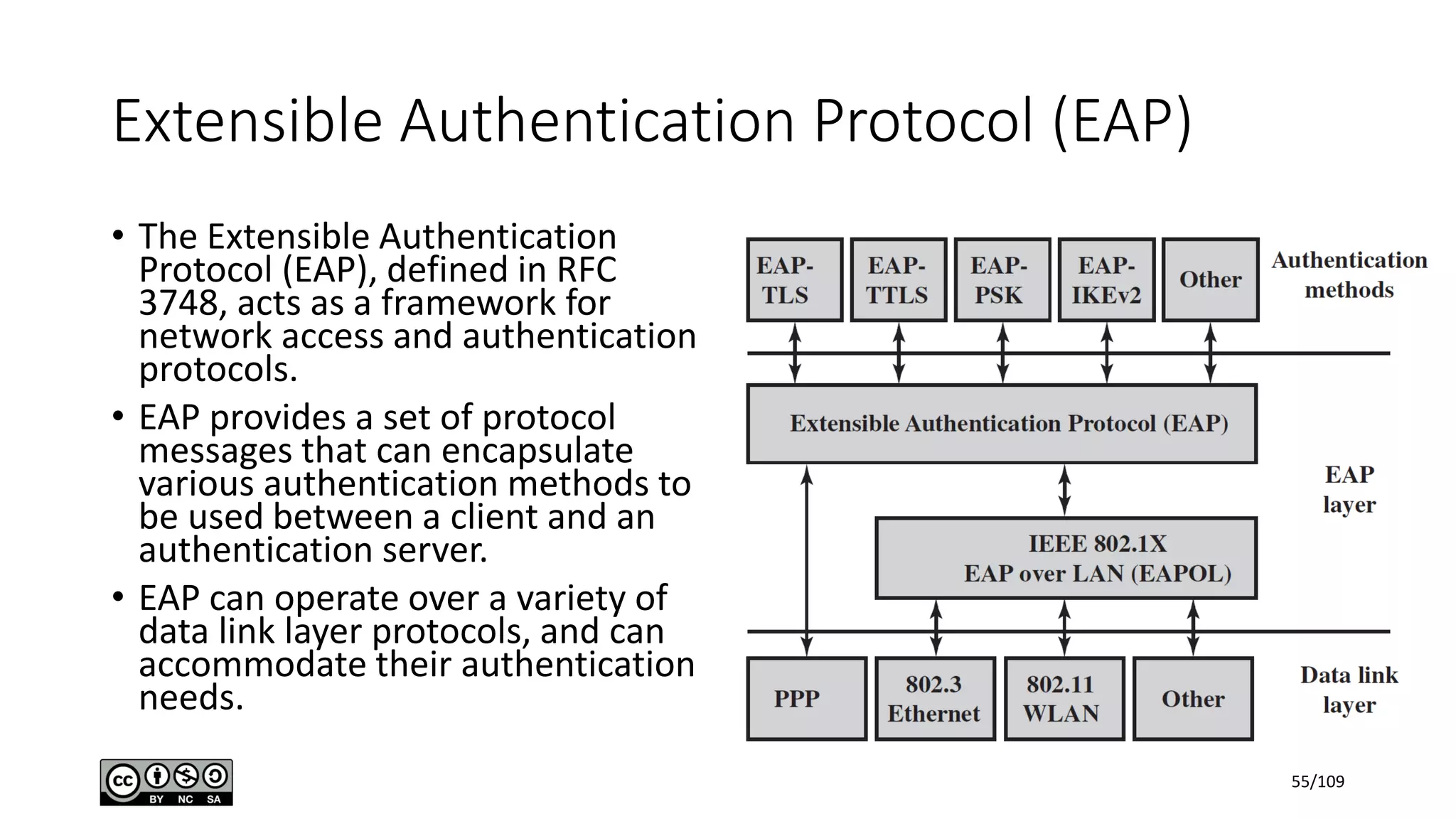
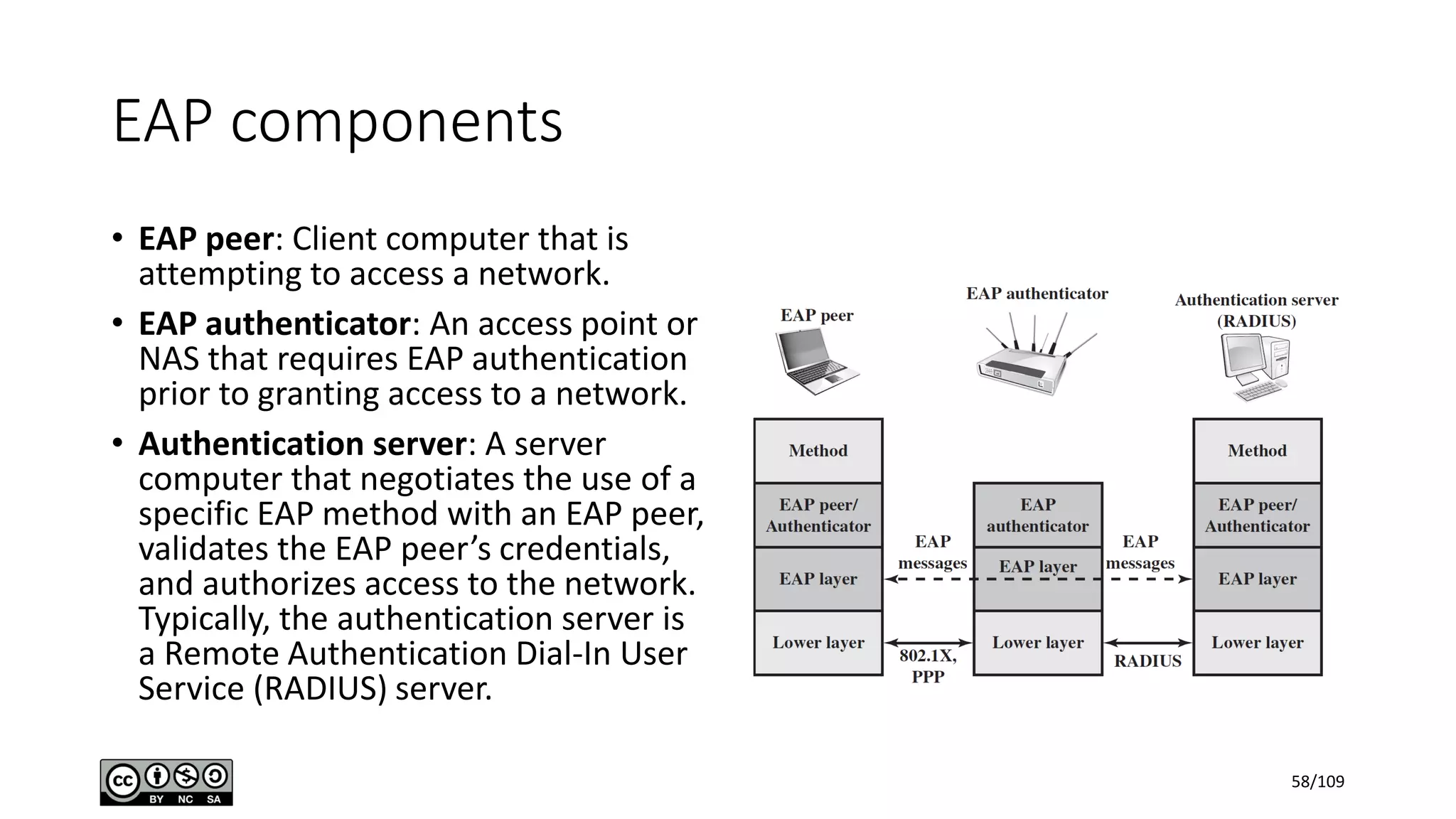
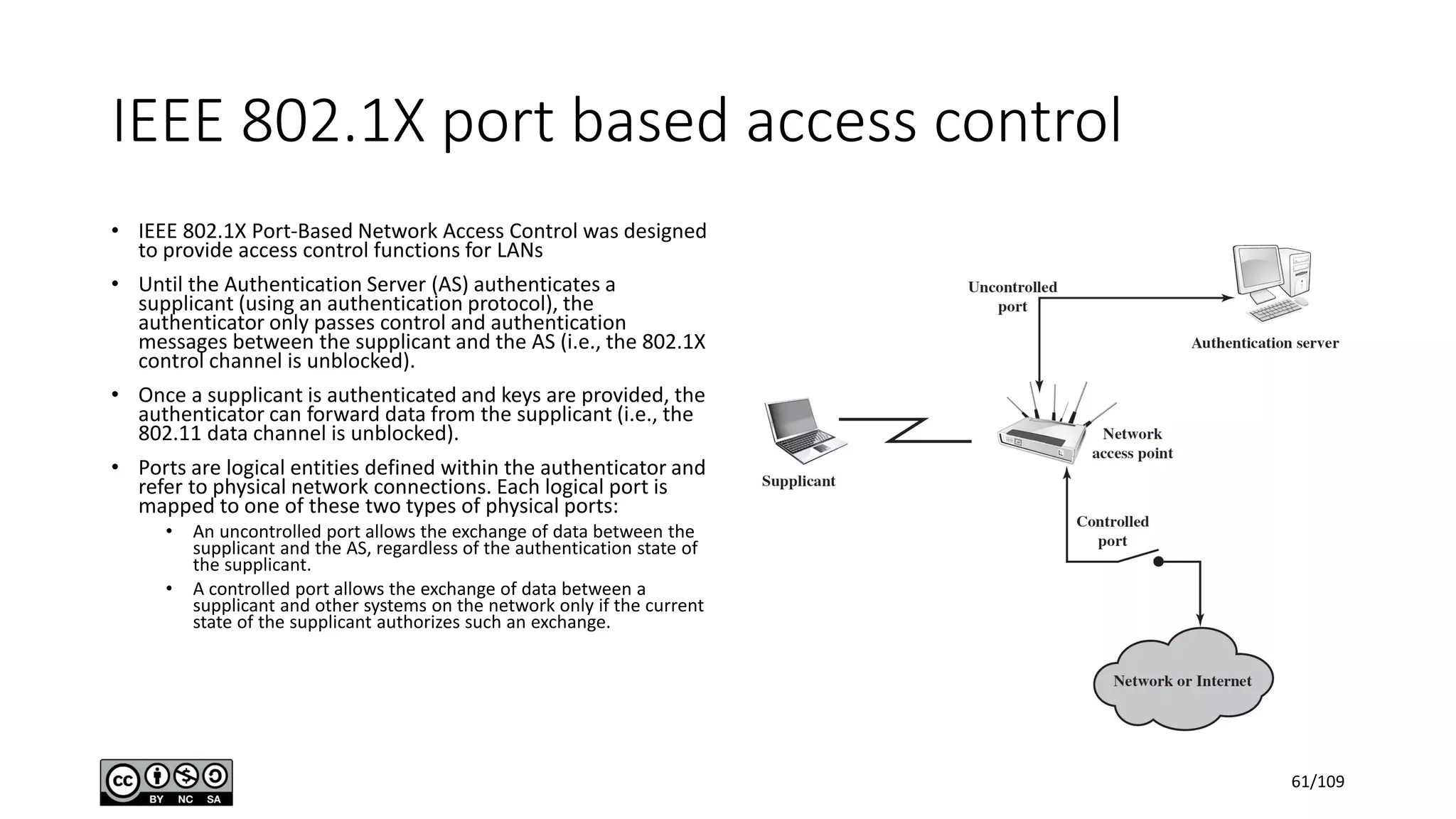
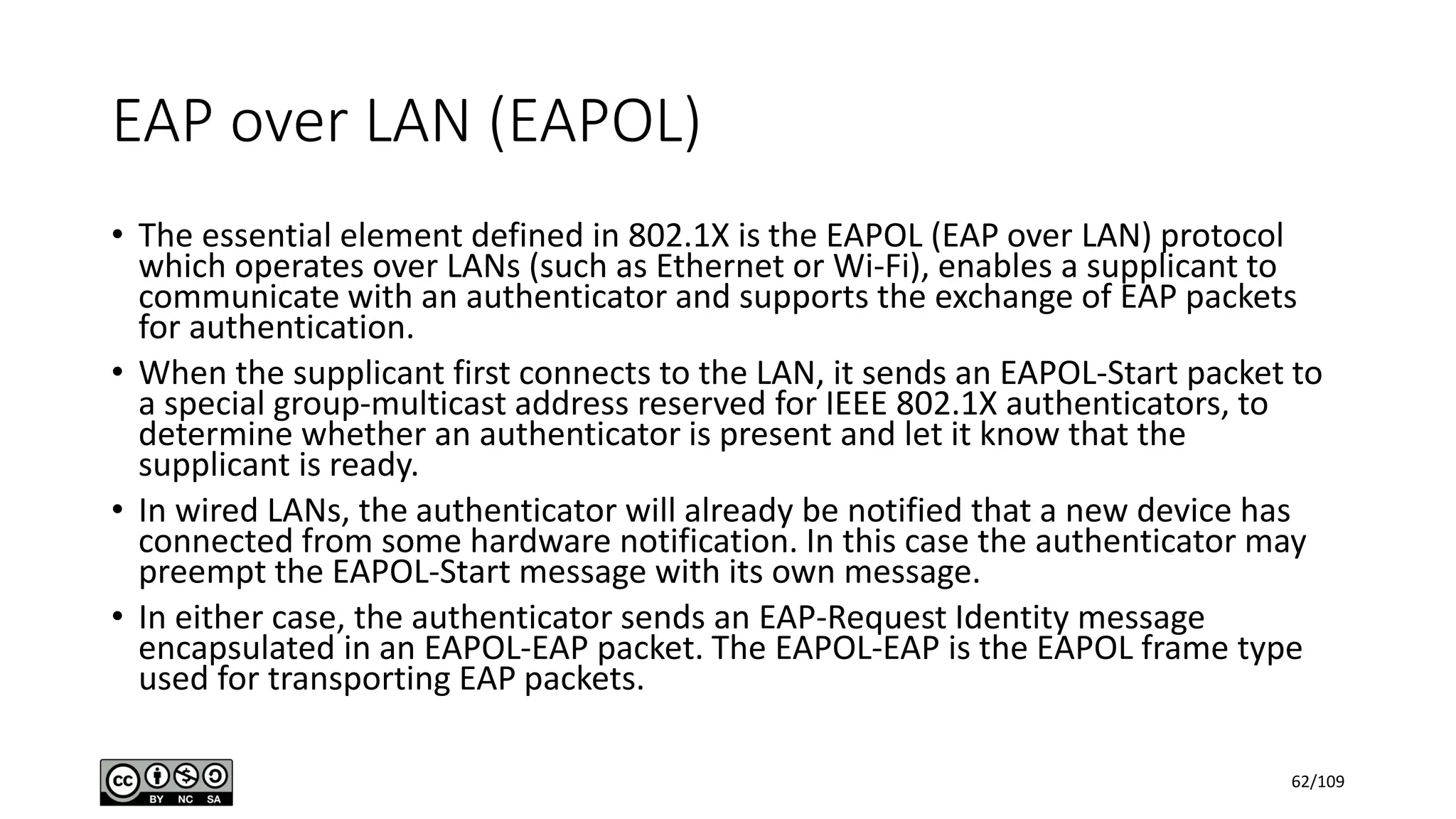
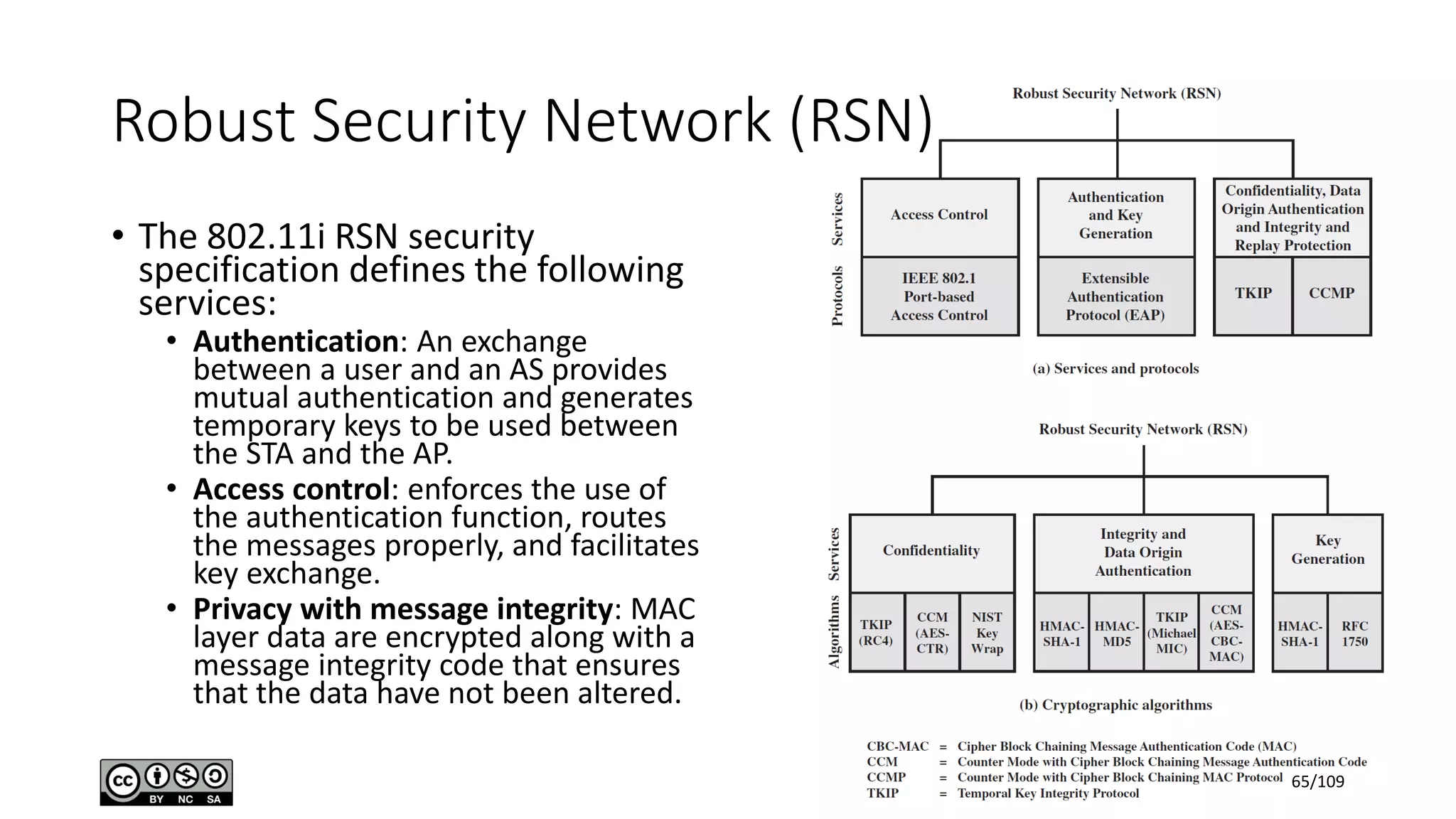
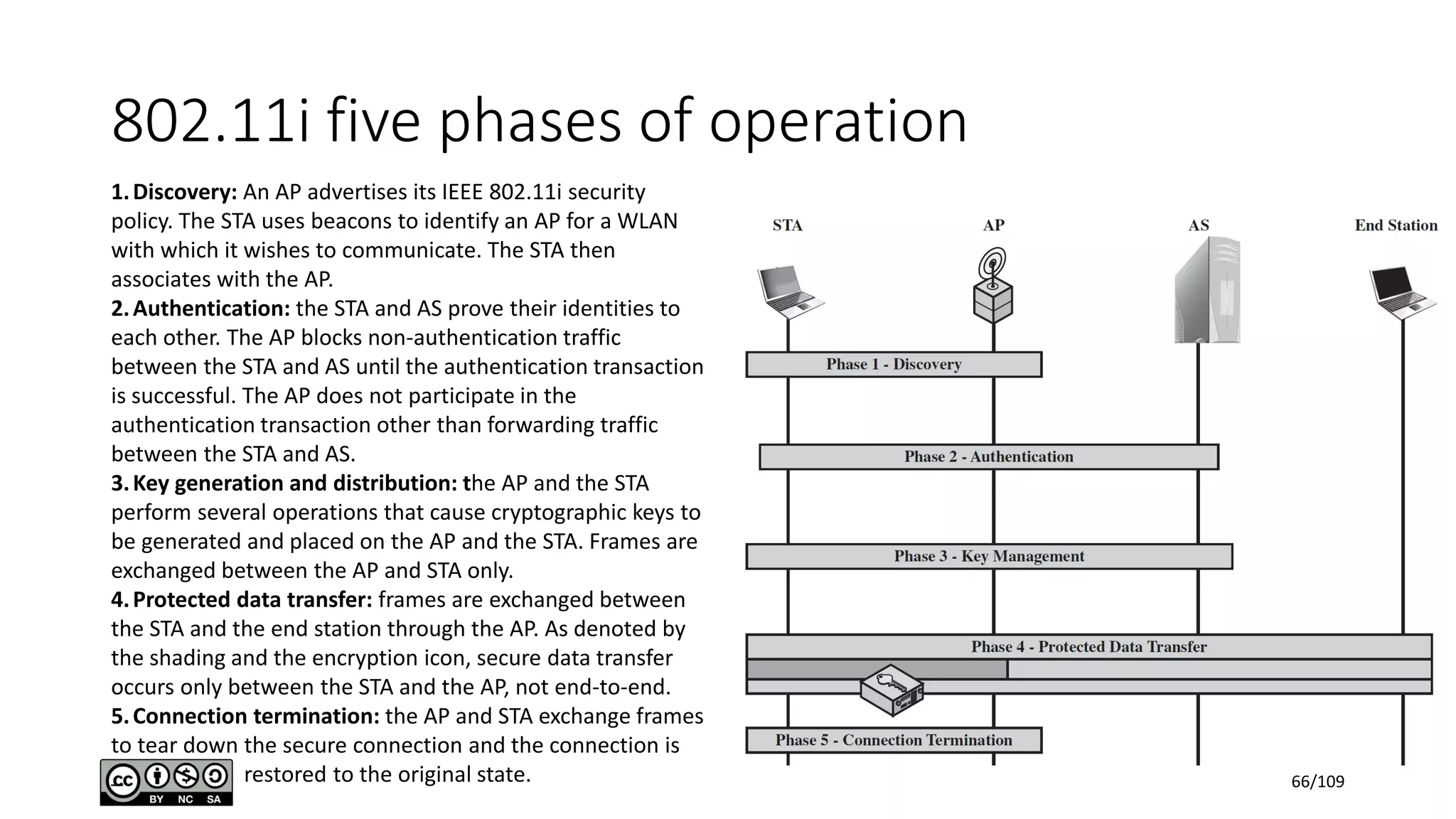
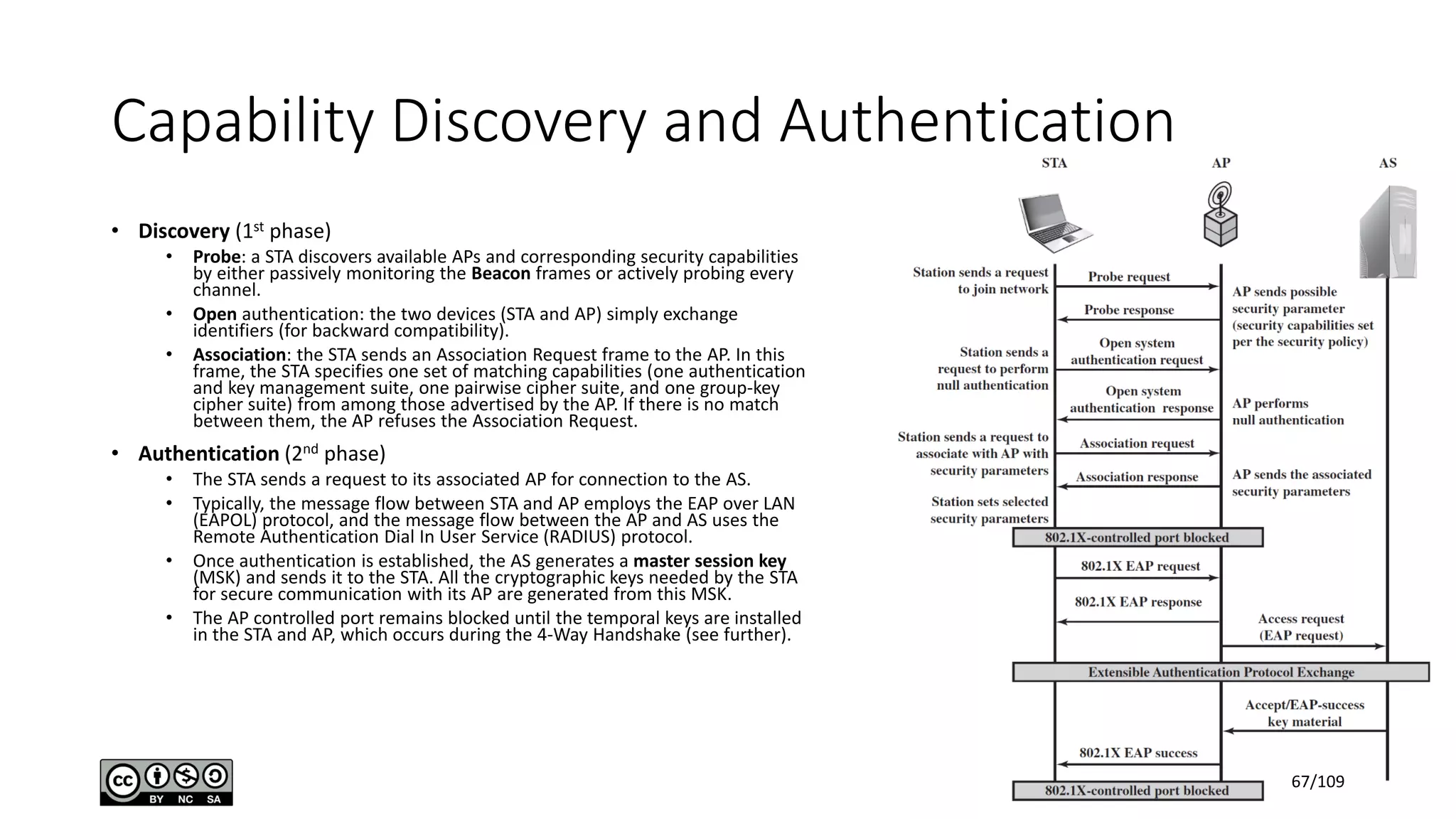
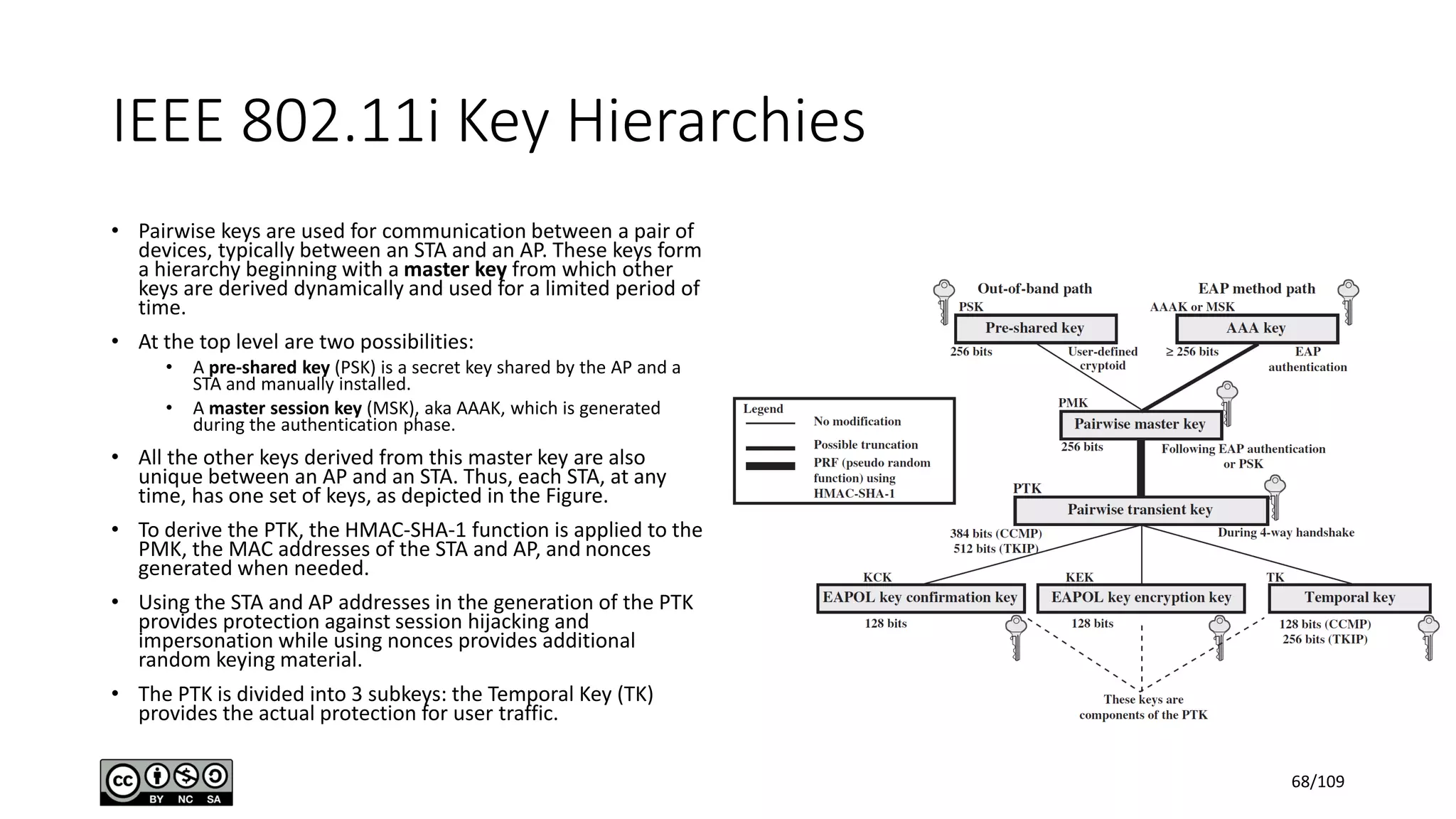
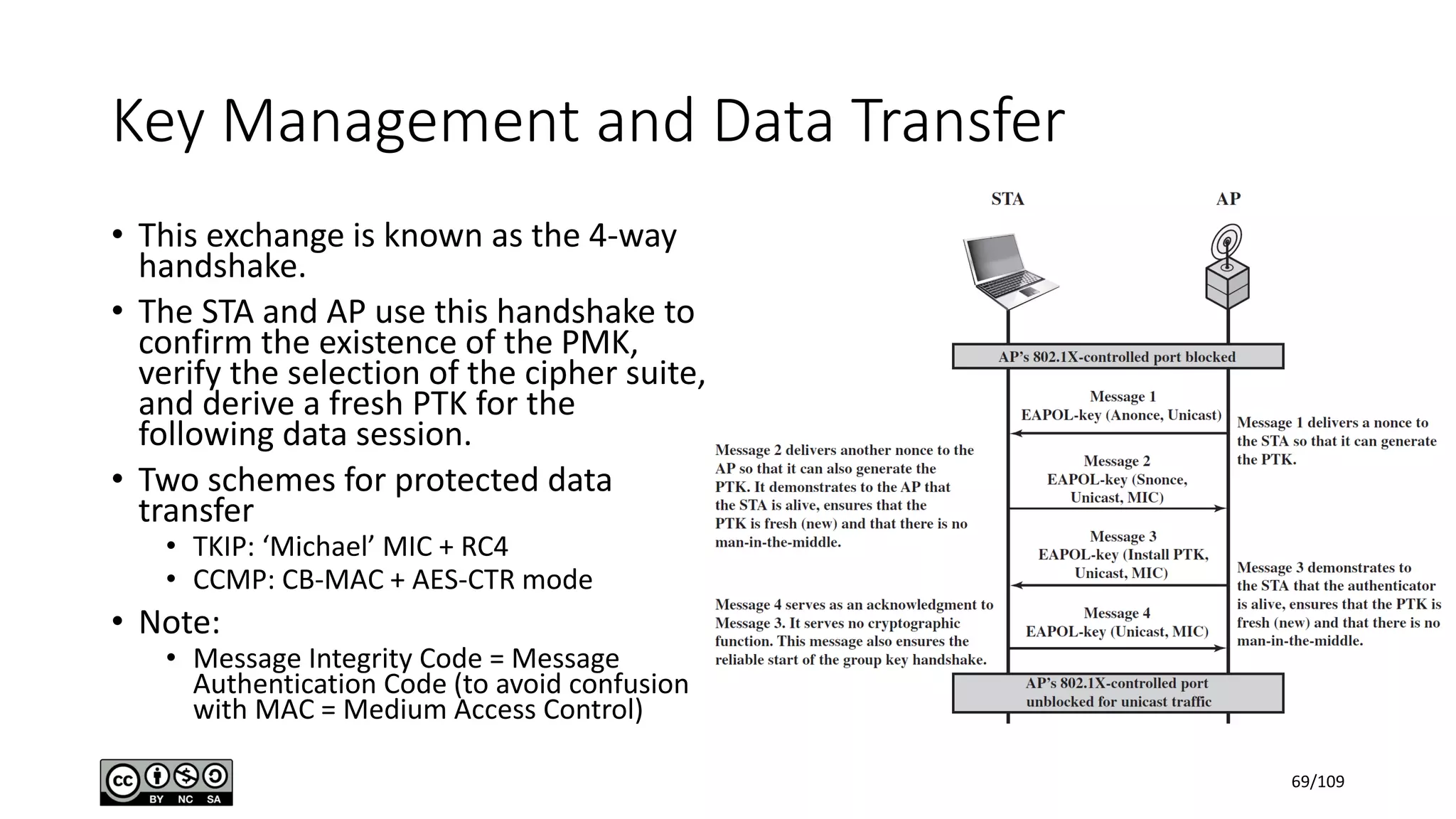
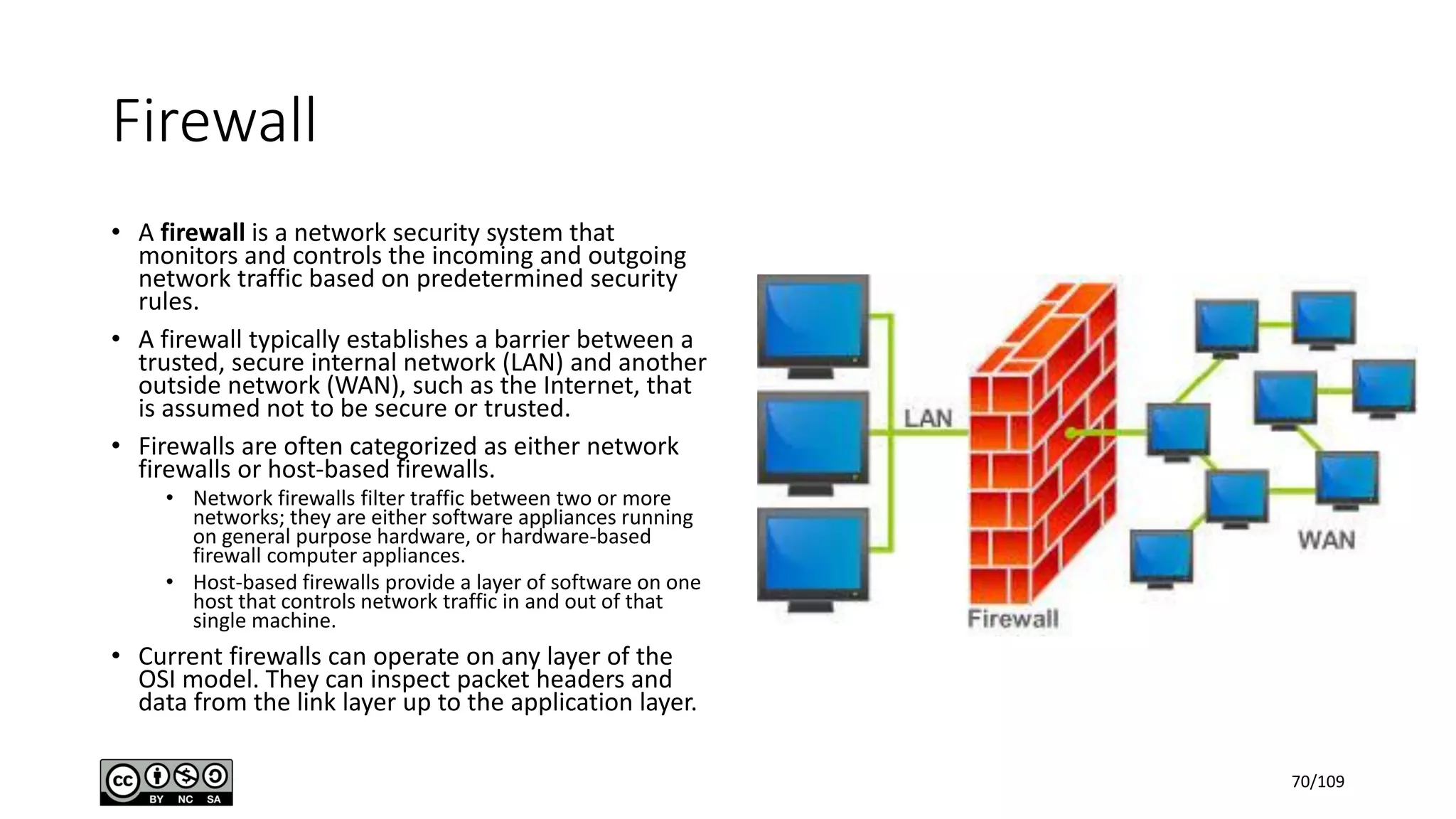
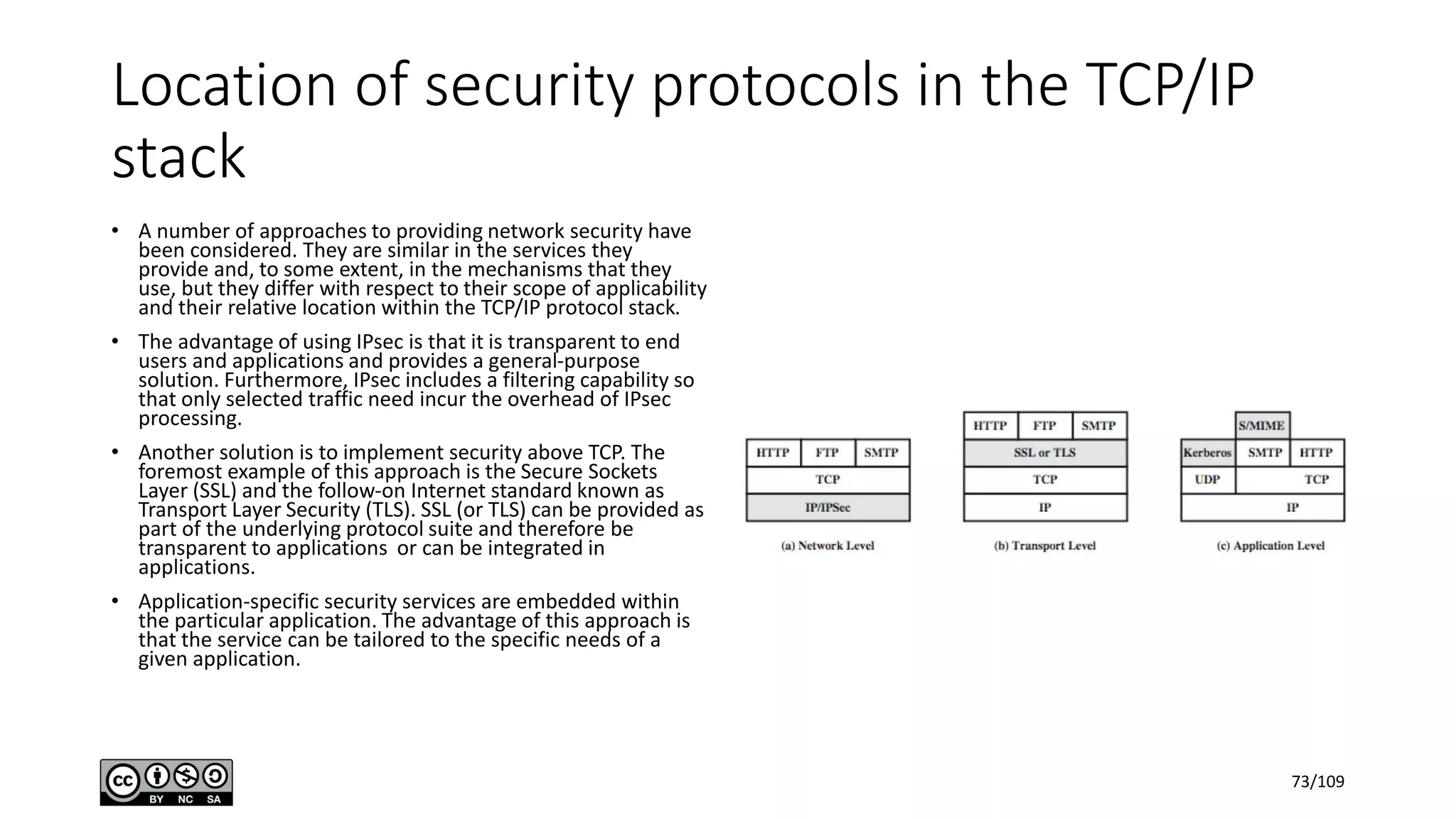
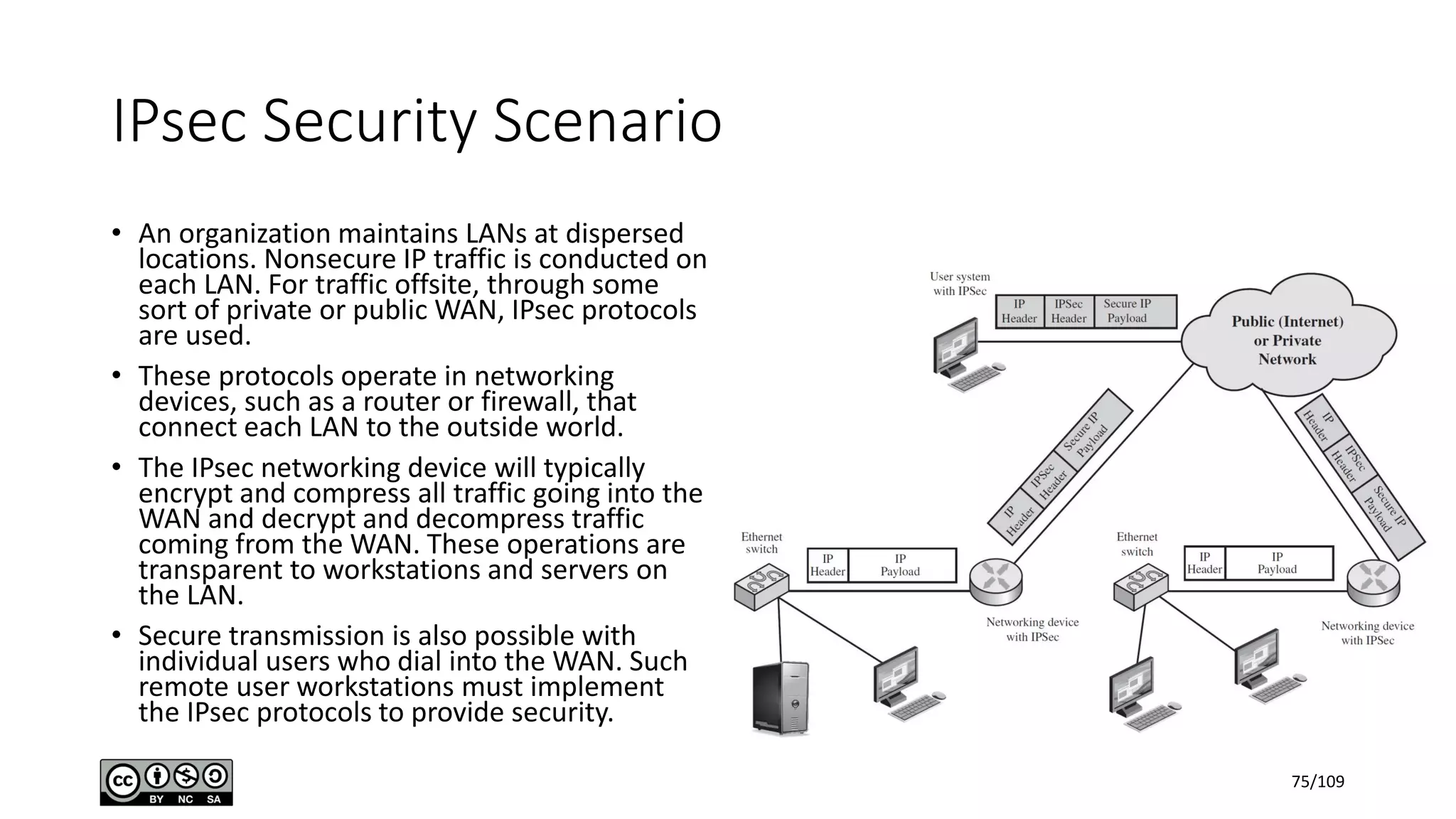
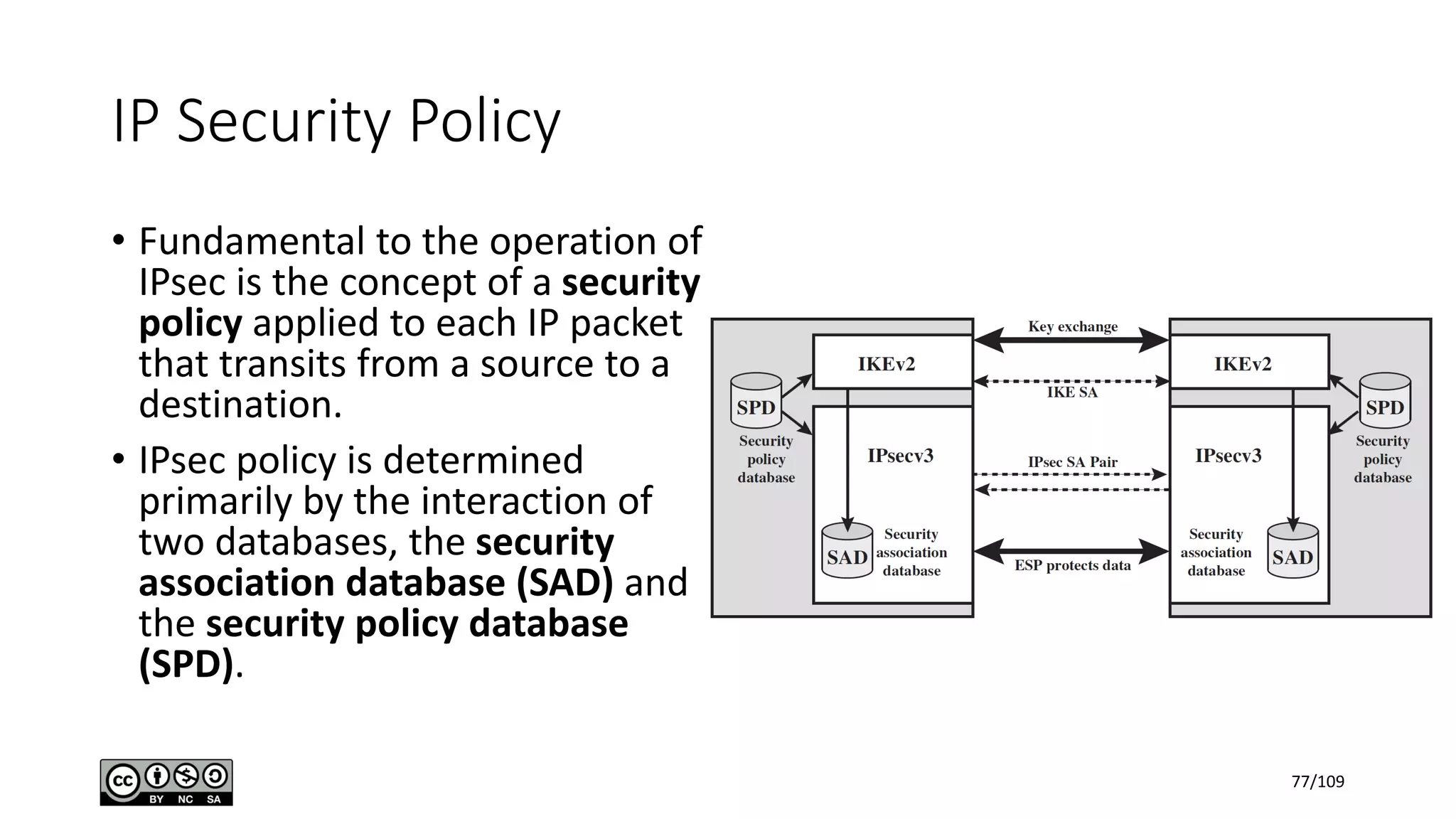
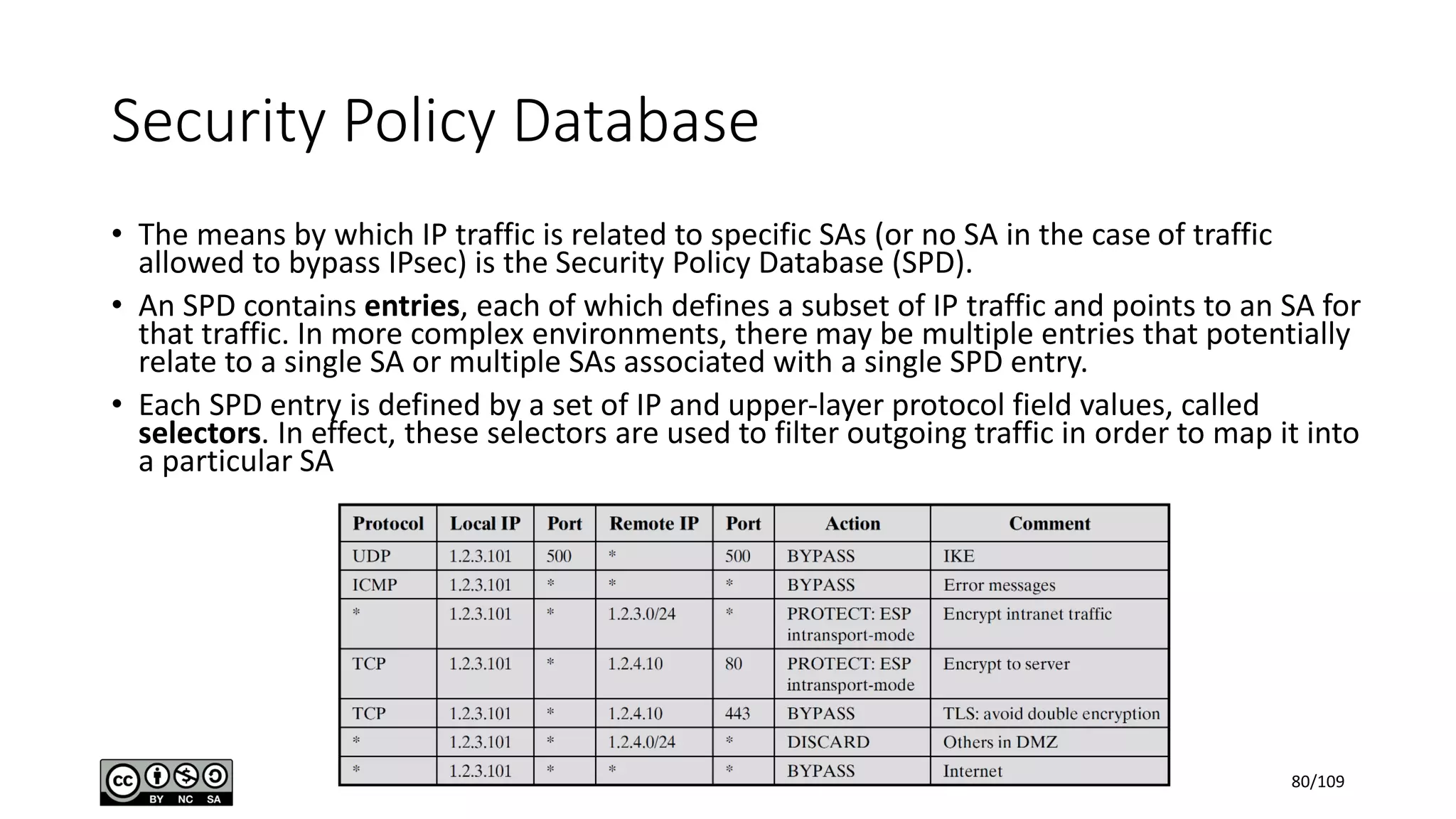
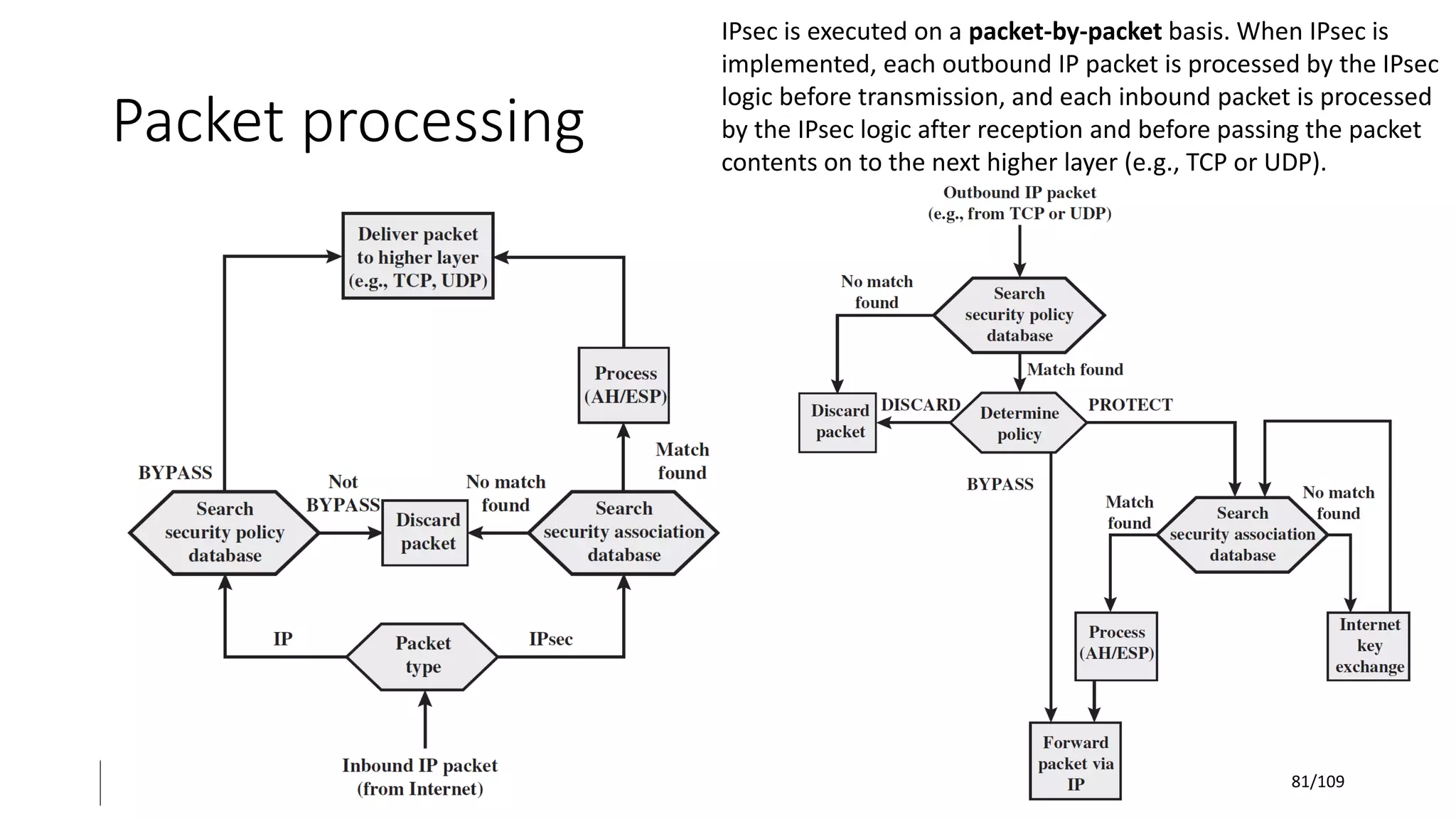
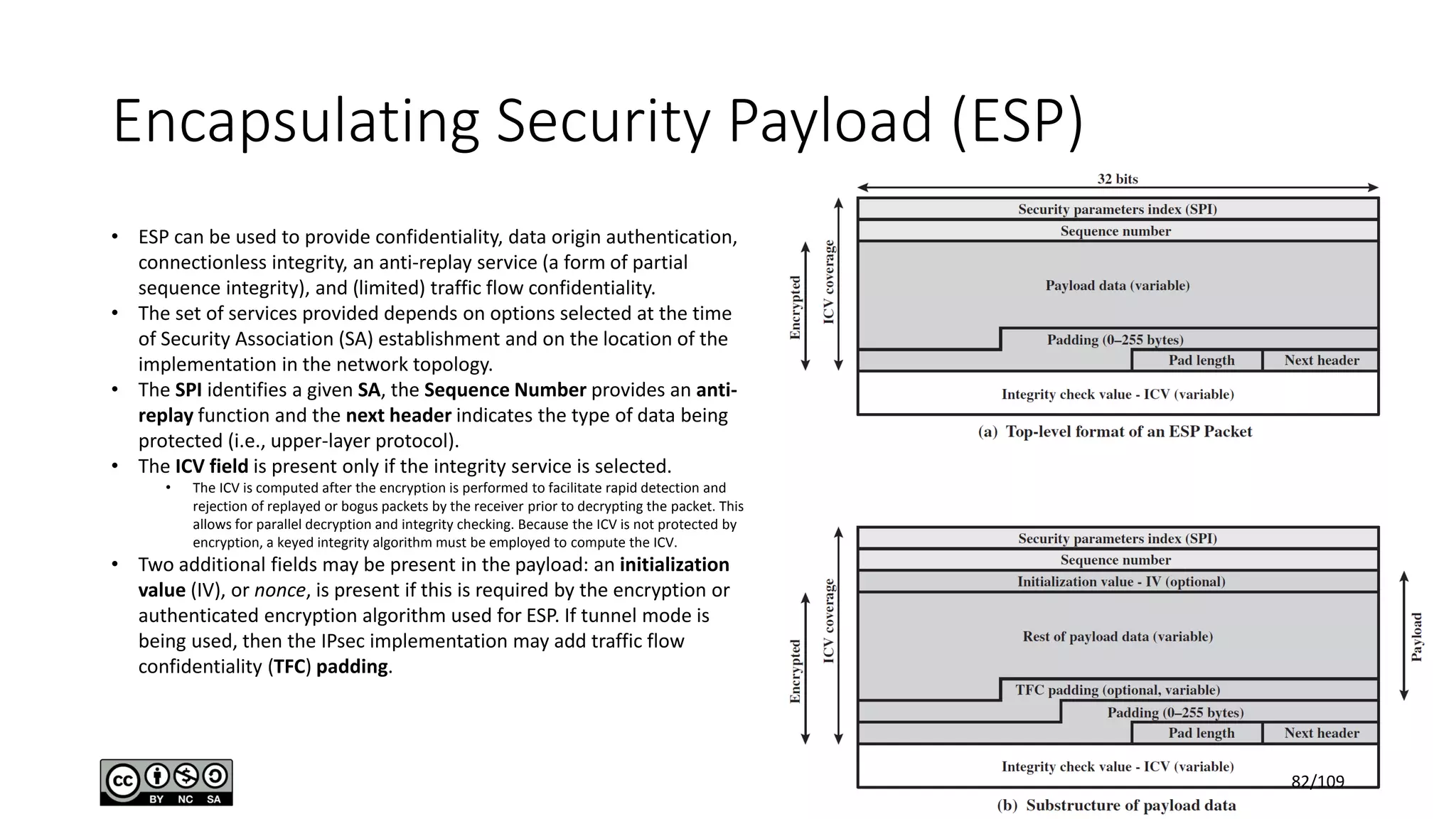
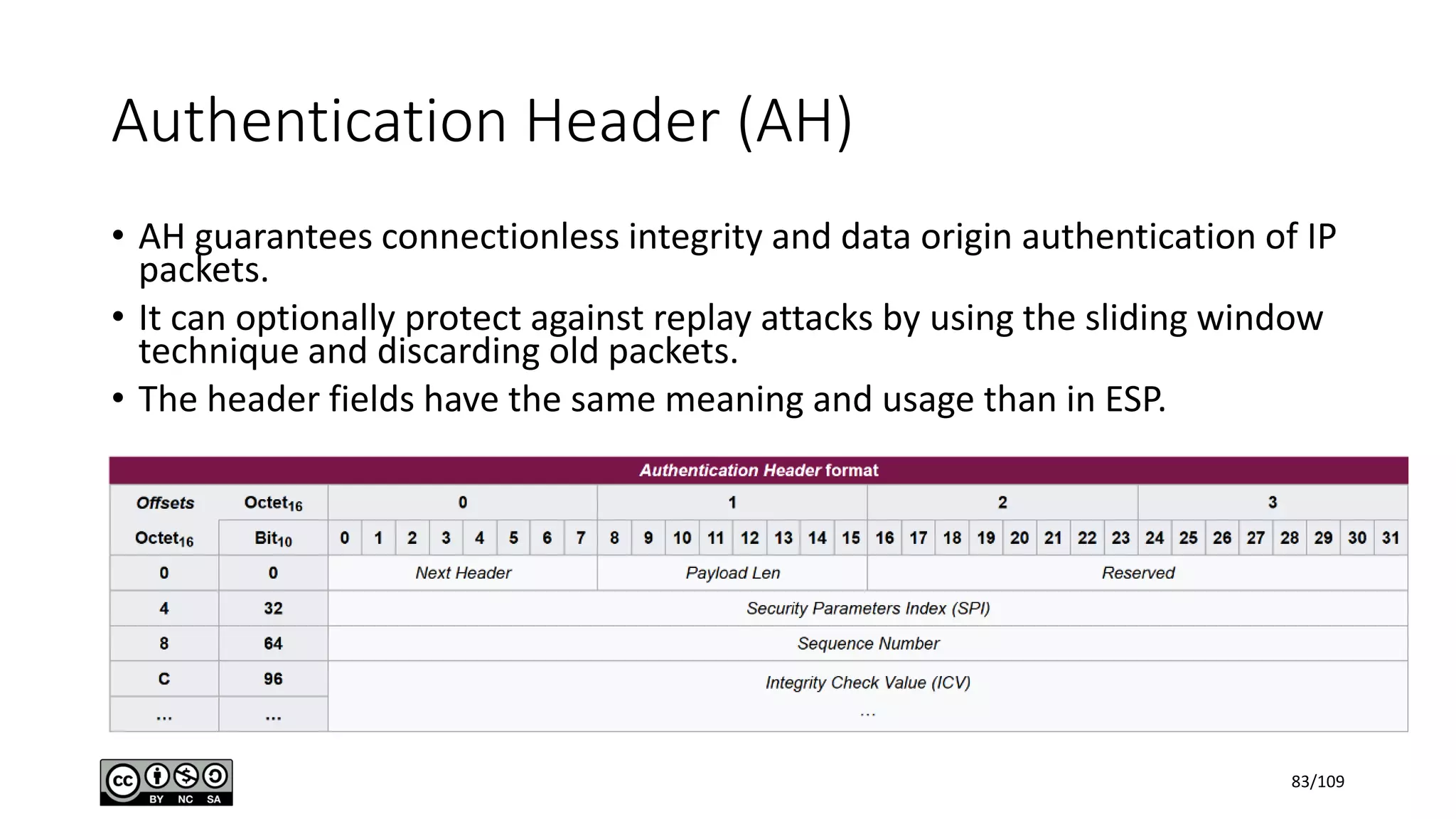
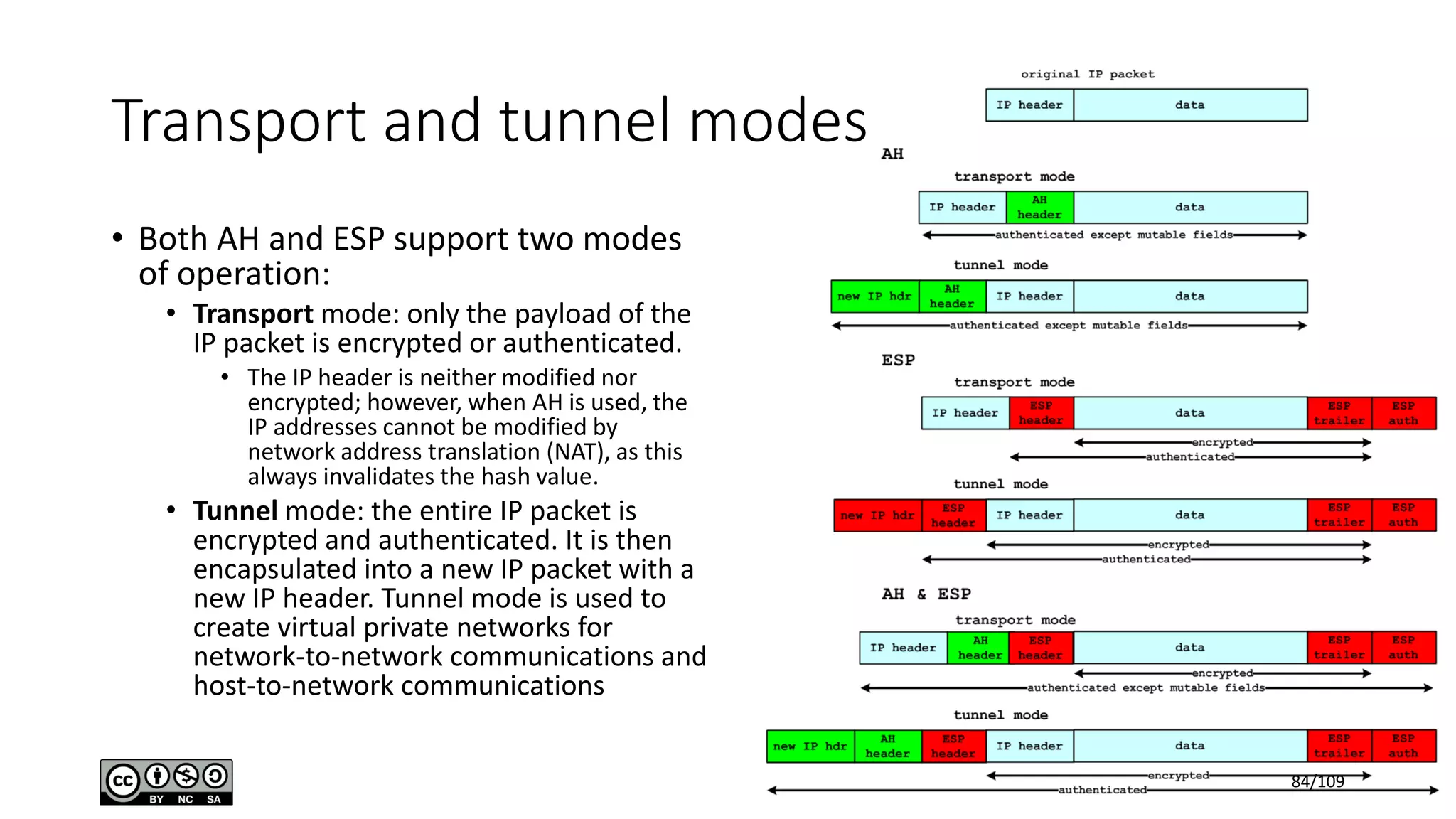
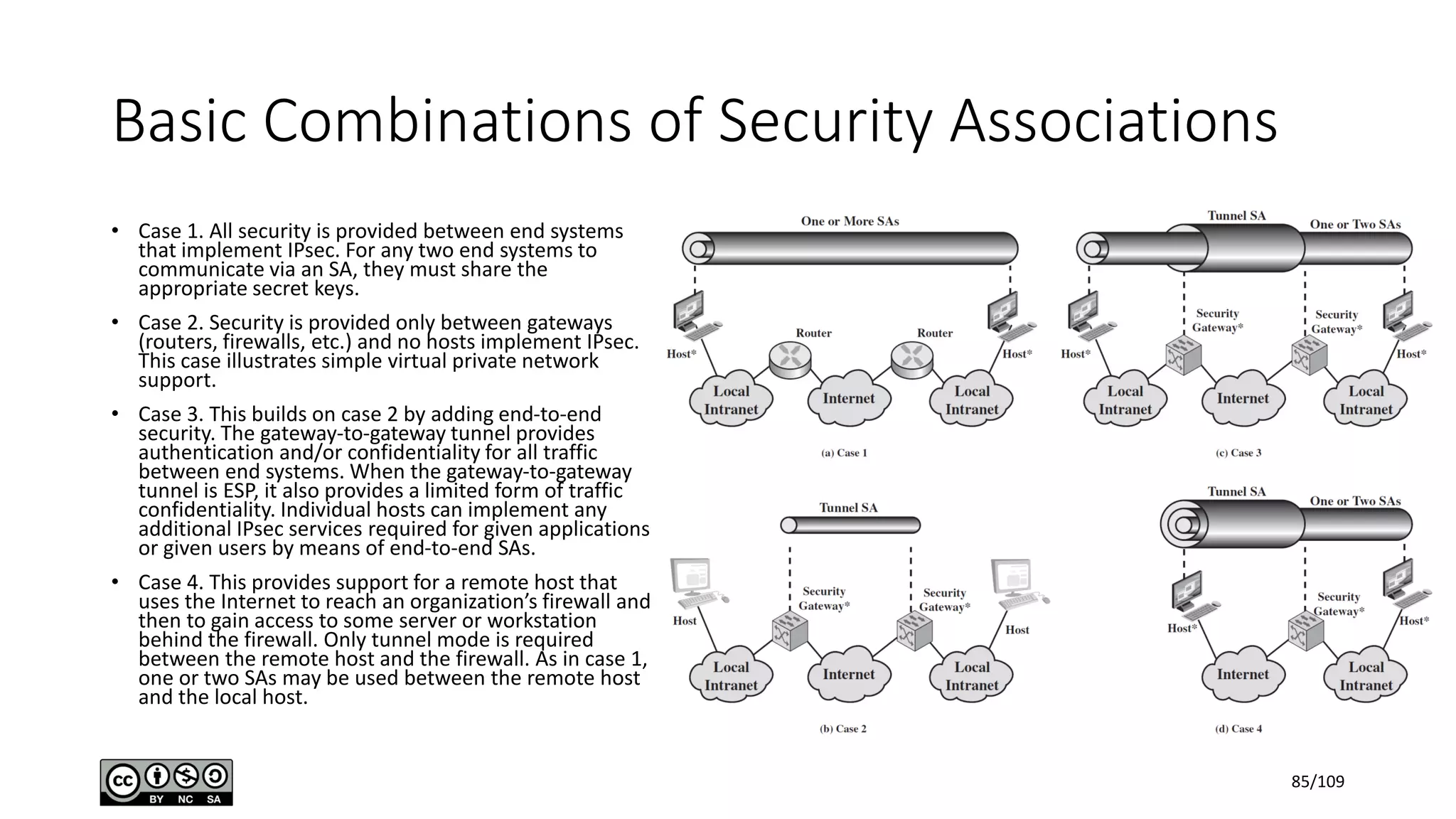
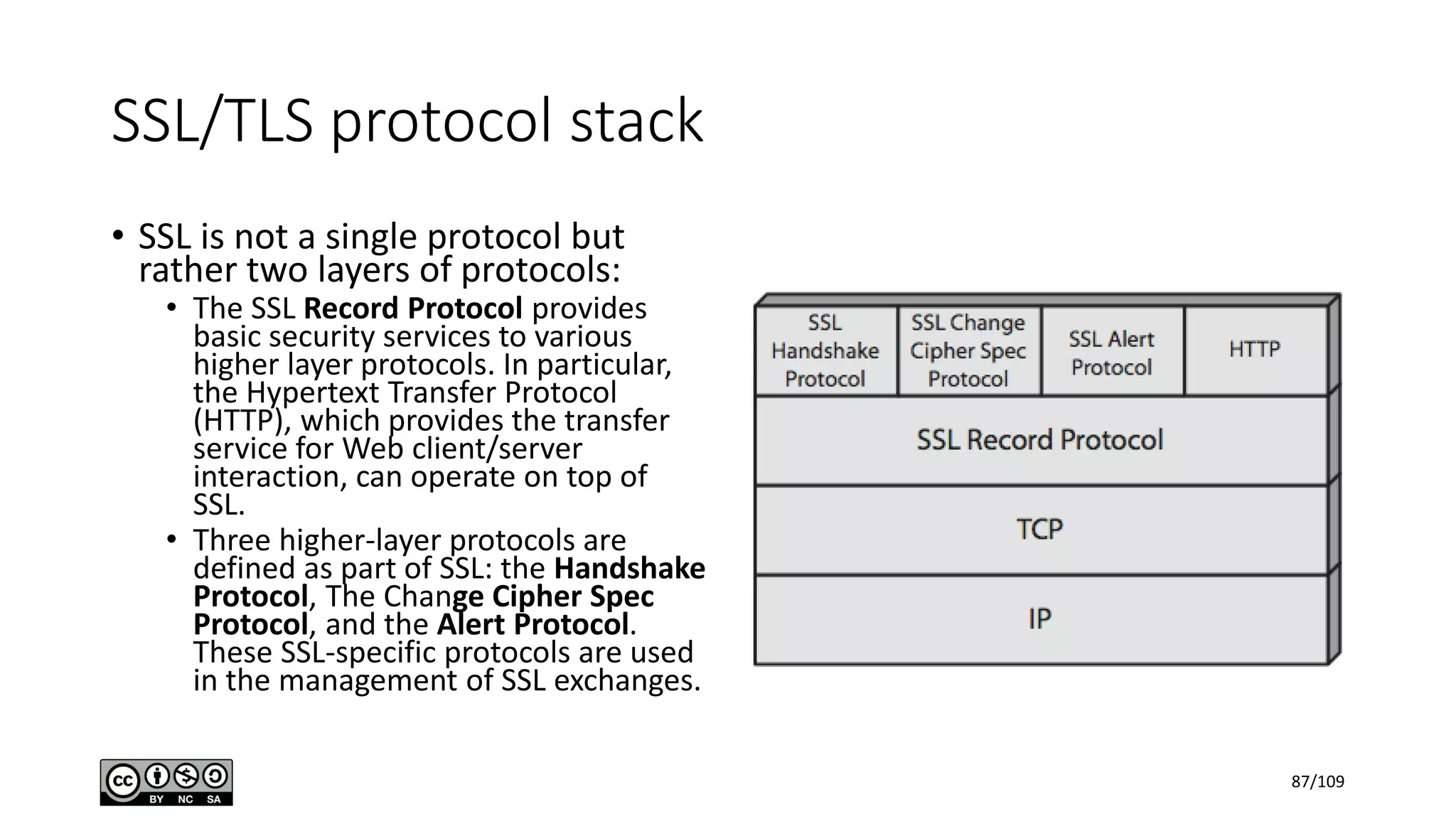
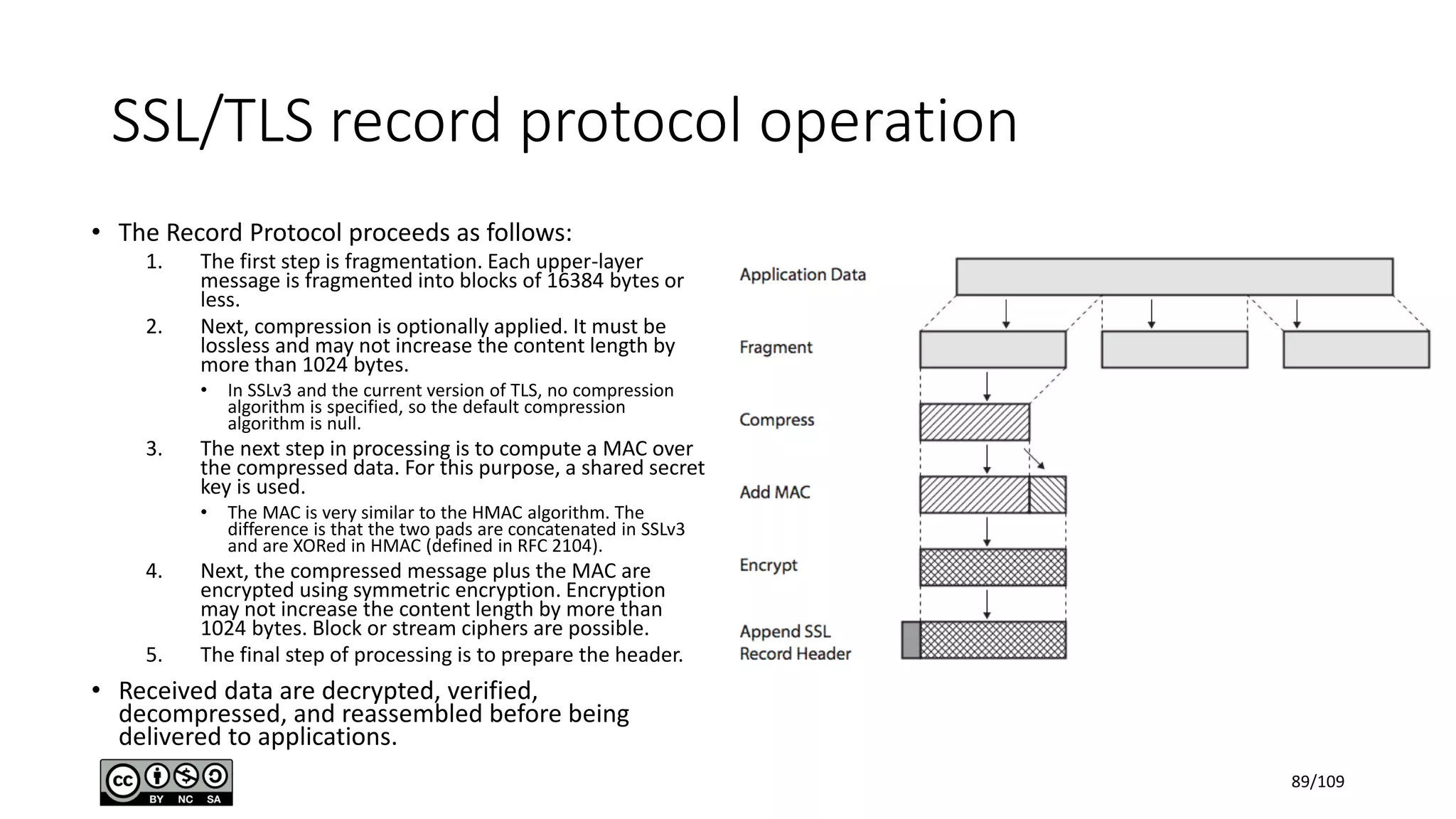
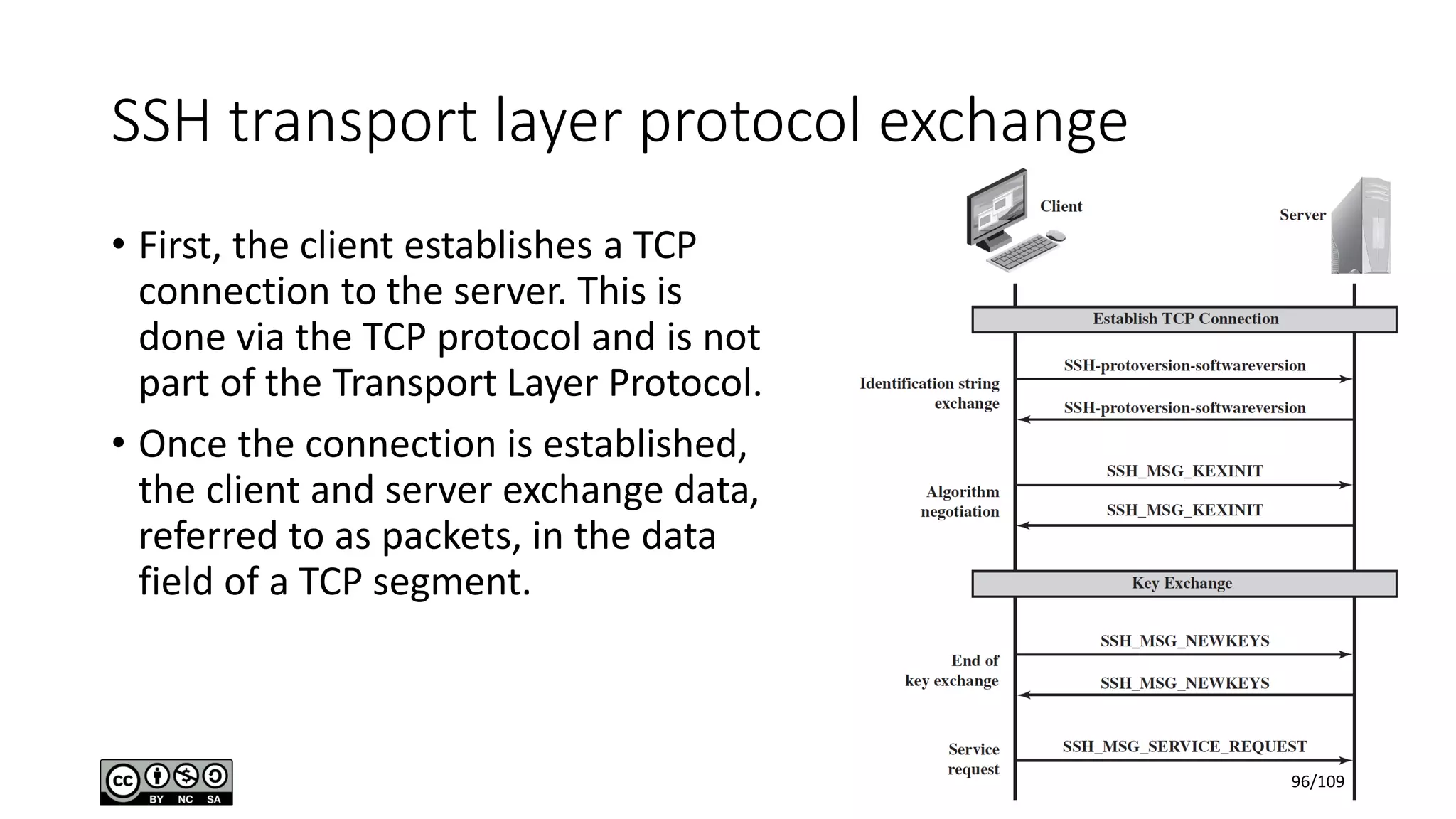
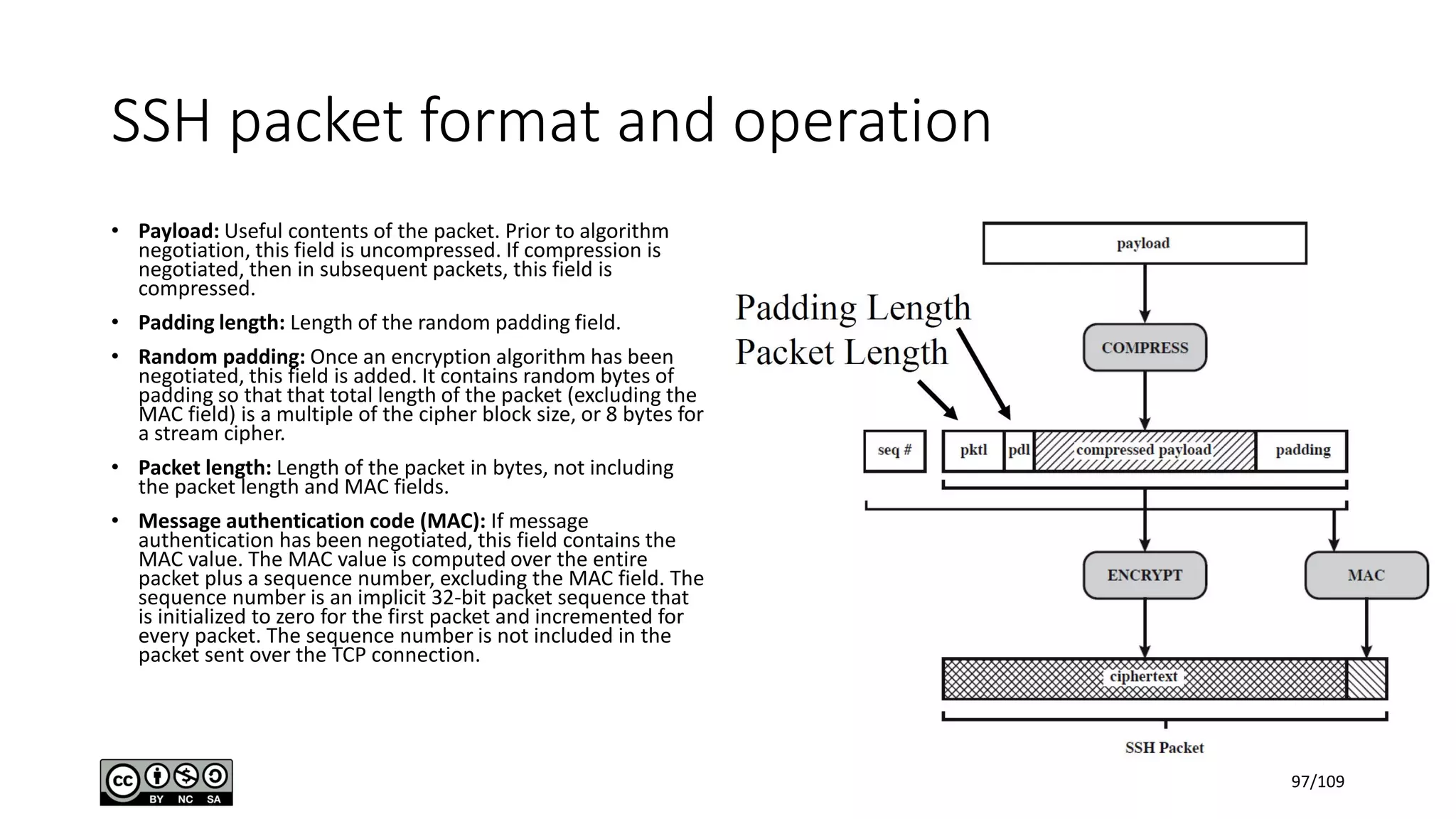
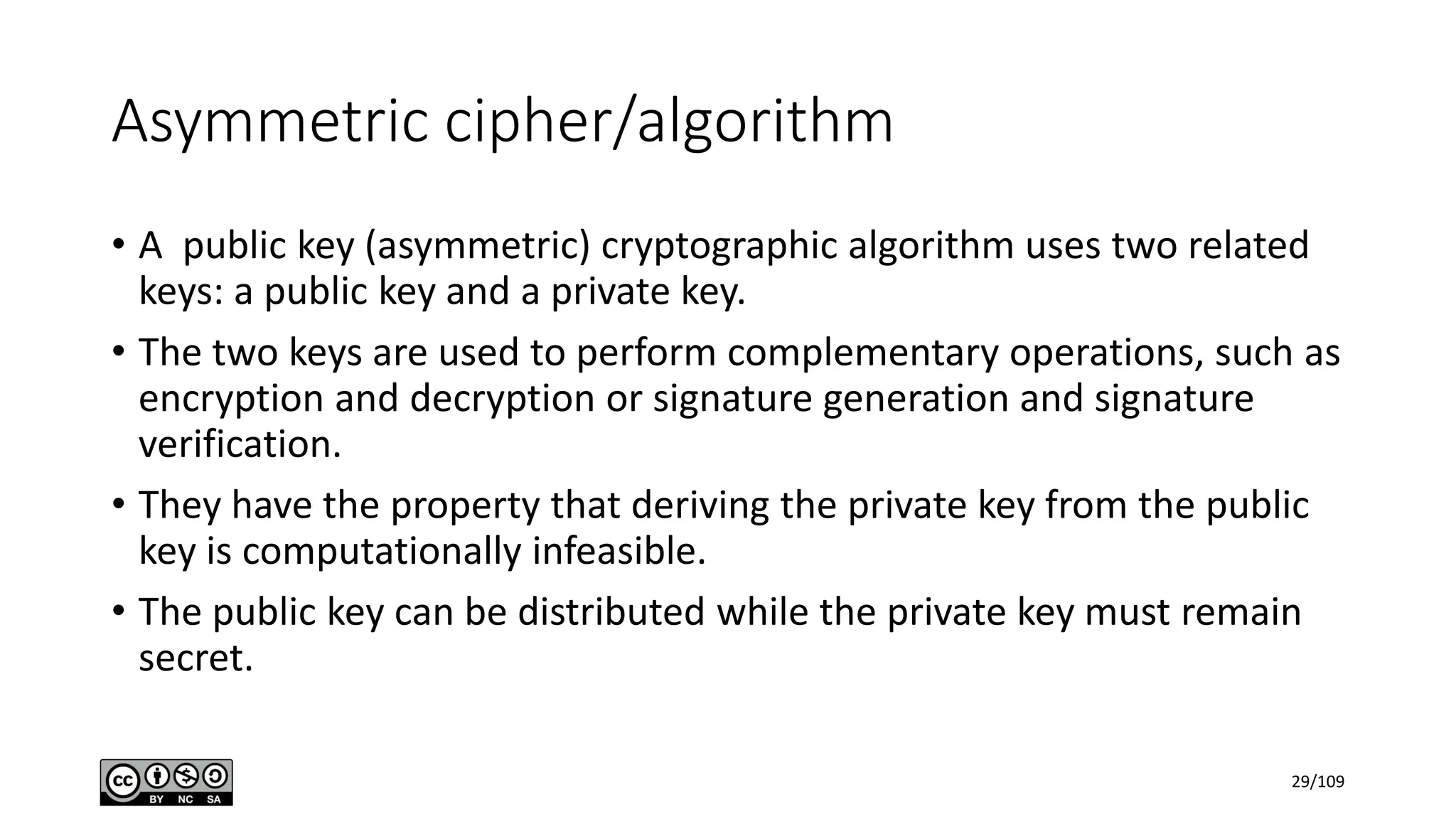
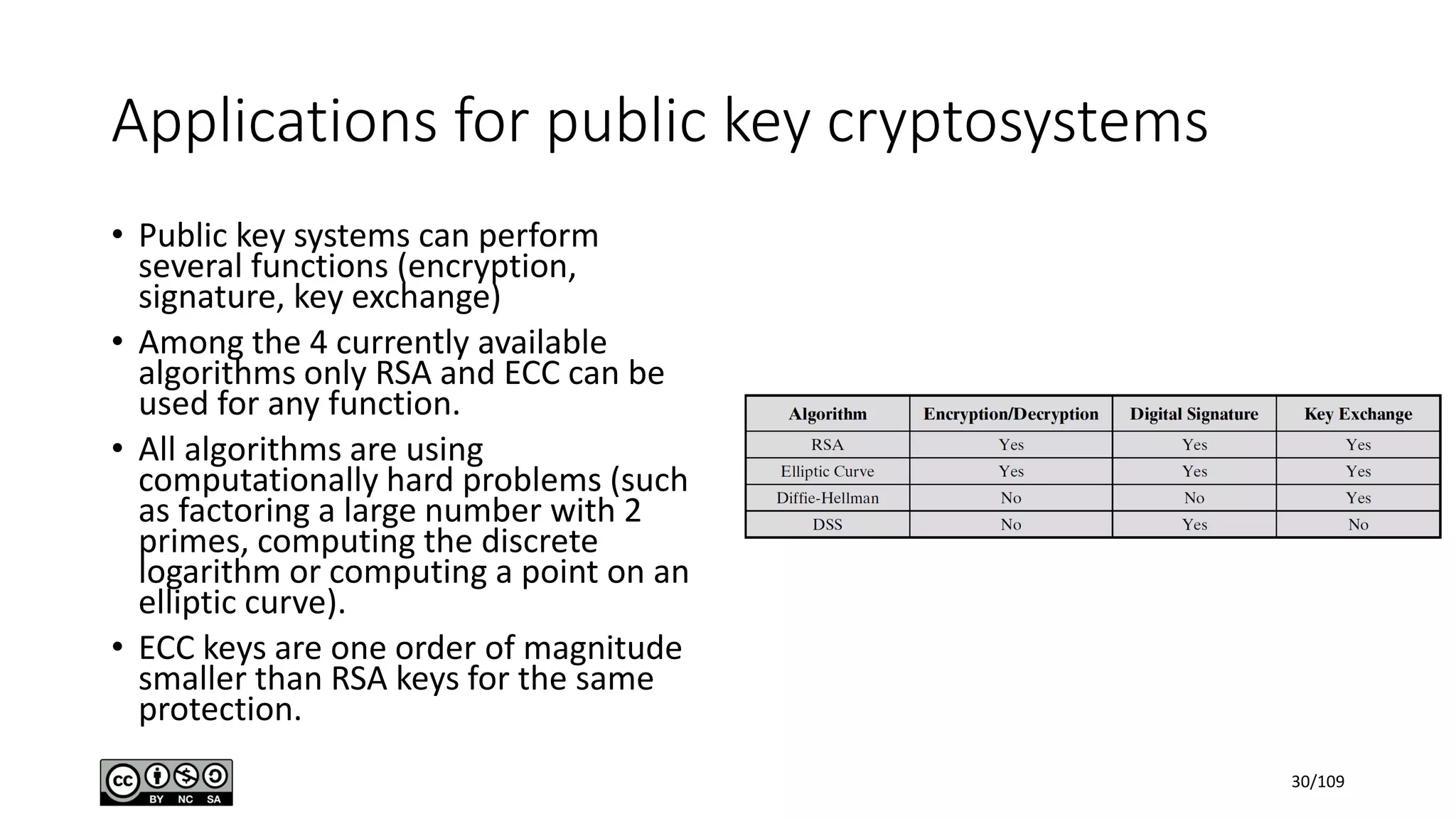
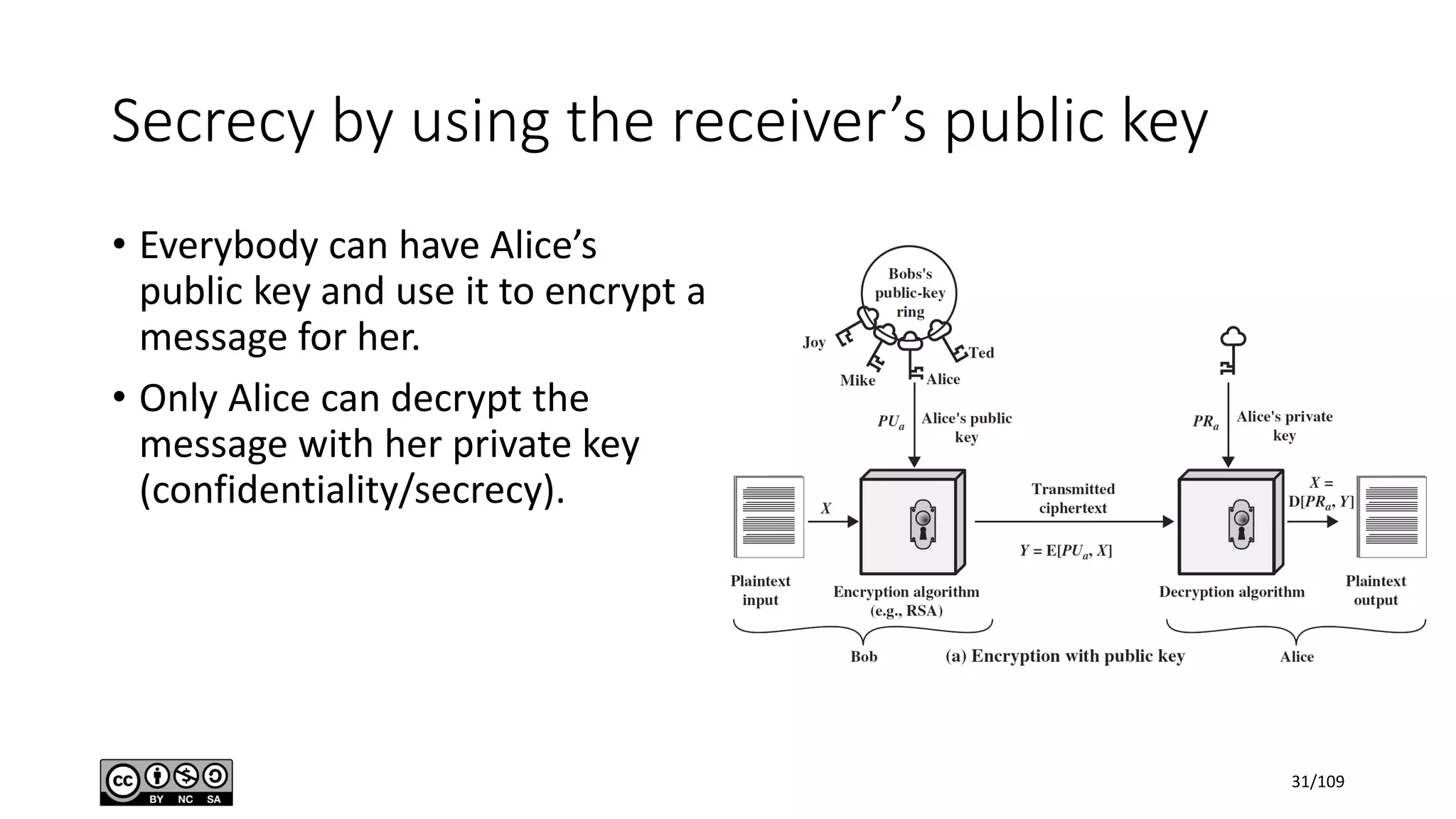
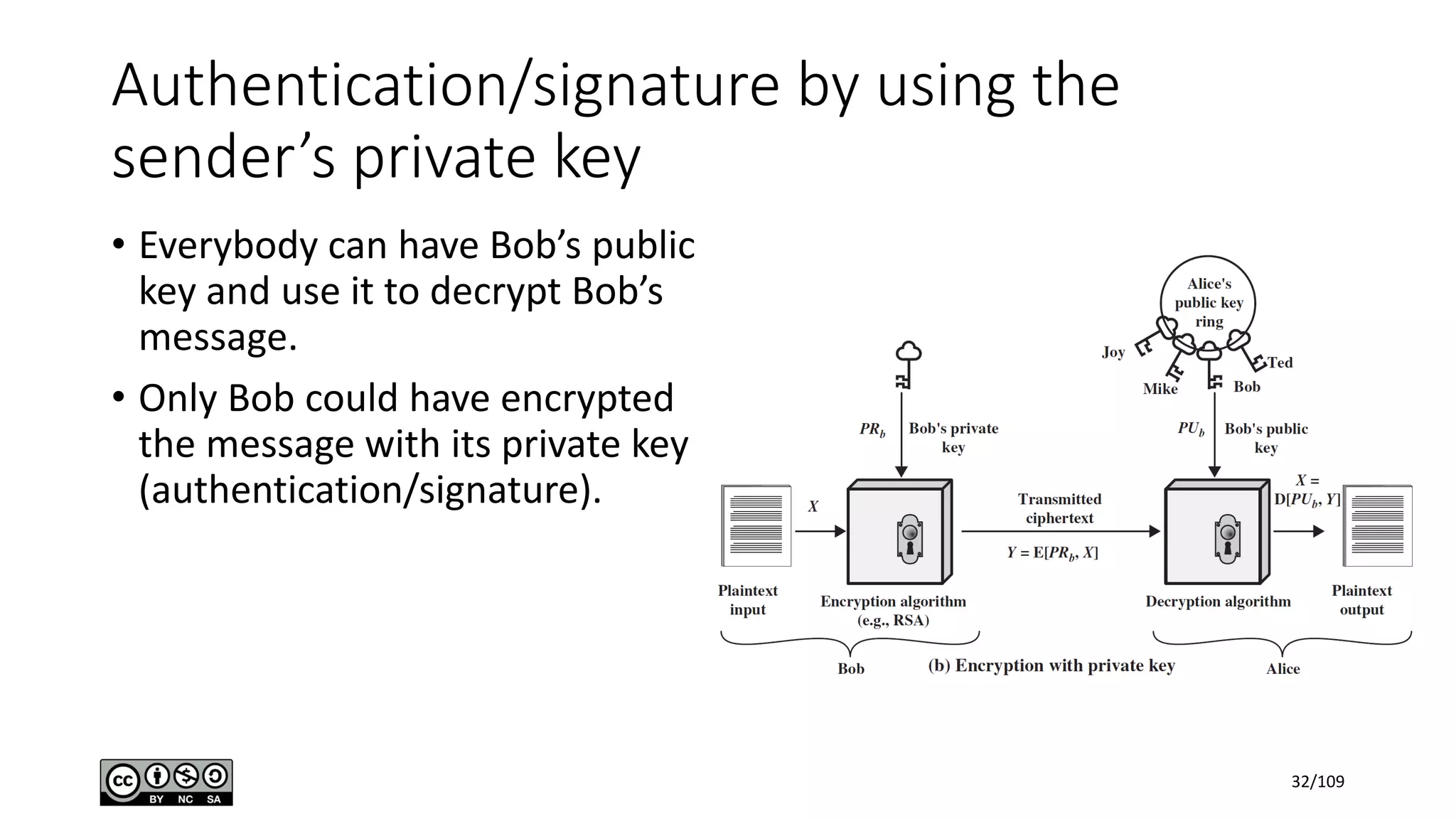
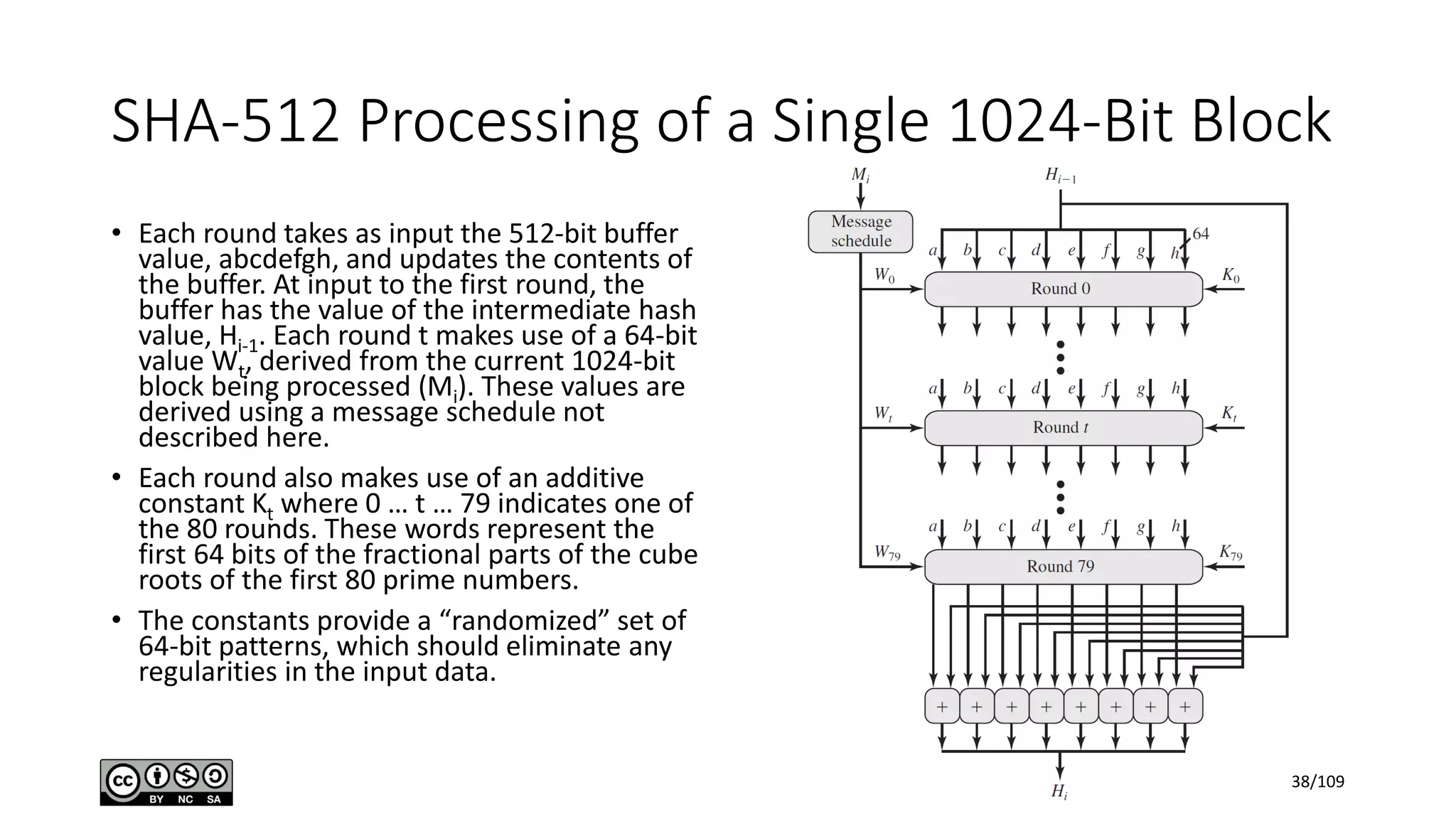
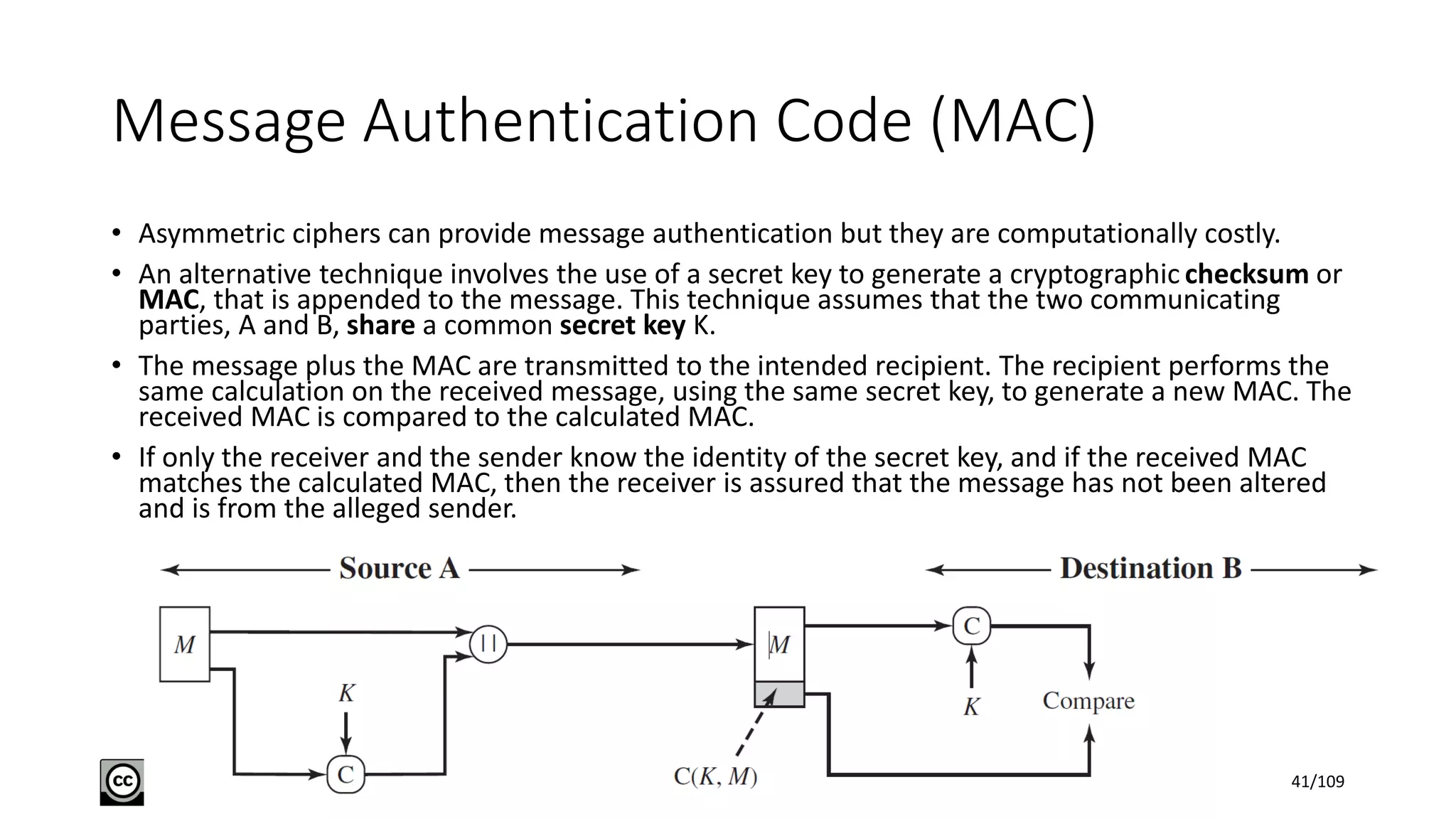
This document outlines the fundamentals of network security, detailing key concepts, types of attacks, and various security mechanisms. It describes essential components like cryptographic algorithms, including symmetric and asymmetric encryption, hash functions, and the CIA triad (confidentiality, integrity, availability). Additionally, it emphasizes the need for secure communication channels and the roles of trusted parties in facilitating secure transmissions.














![Hash-based MAC (HMAC)
• Defined in RFC2104
• Uses hash function on the message:
• HMACK (M) =
H[(K’ ㊉ opad)||H[(K’ ㊉ ipad)||M]]
• Where K’ = key padded to b-bits or
hashed to b-bits if |k|>b (with b = block
size for the hash)
• opad, ipad are constants:
• ipad = 0x36 repeated (b/8) times
• opad = 0x5C repeated (b/8) times
• Any hash function can be used.
• It is proved that the security of HMAC
relates to that of the underlying hash
algorithm.
42/109](https://image.slidesharecdn.com/network-security-fundamentals-v3-200124222421/75/Network-Security-Fundamentals-42-2048.jpg)