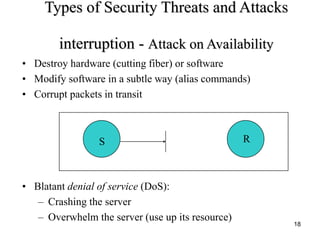
This document provides an overview of cryptography and network security. It defines key terms like computer security, network security, and internet security. It describes common security attacks like eavesdropping, tampering, fabrication, and denial of service. It also outlines security services, security mechanisms, and the OSI security architecture. The document models network security and network access security.