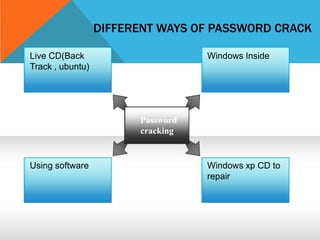
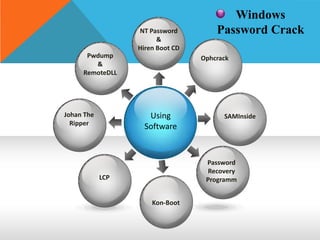
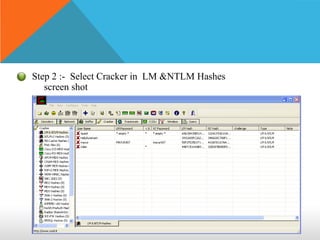
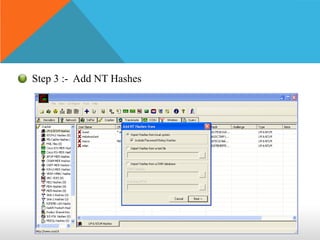
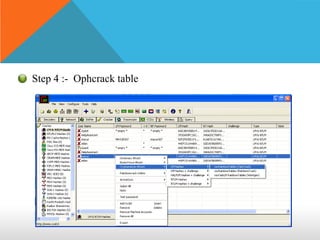
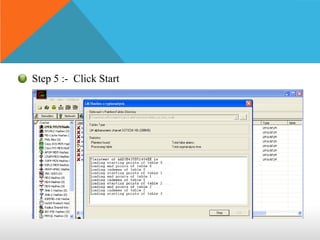
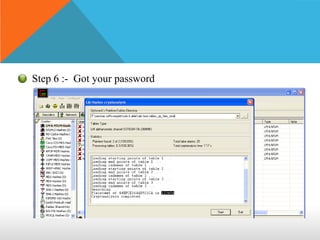
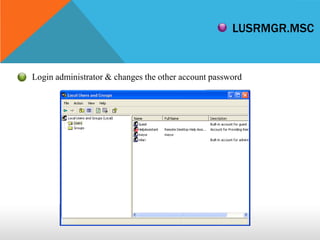
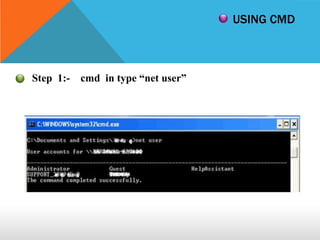
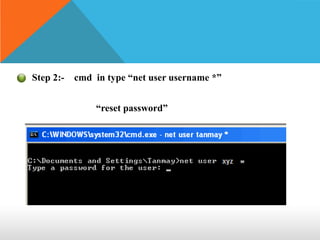
This document discusses different types of hackers and methods of hacking passwords. It defines white hat and black hat hackers, with white hats using their skills constructively and ethically to find security vulnerabilities, while black hats use their skills illegally and destructively. The document also discusses crackers/attackers who hack with malicious intent, phreaks who hack phone networks, and script kiddies who exploit known vulnerabilities without technical skills. It provides examples of password cracking tools and methods like Cain & Abel, LCP, password dumping, and using Windows repair mode. It notes the importance of security awareness and prevention.