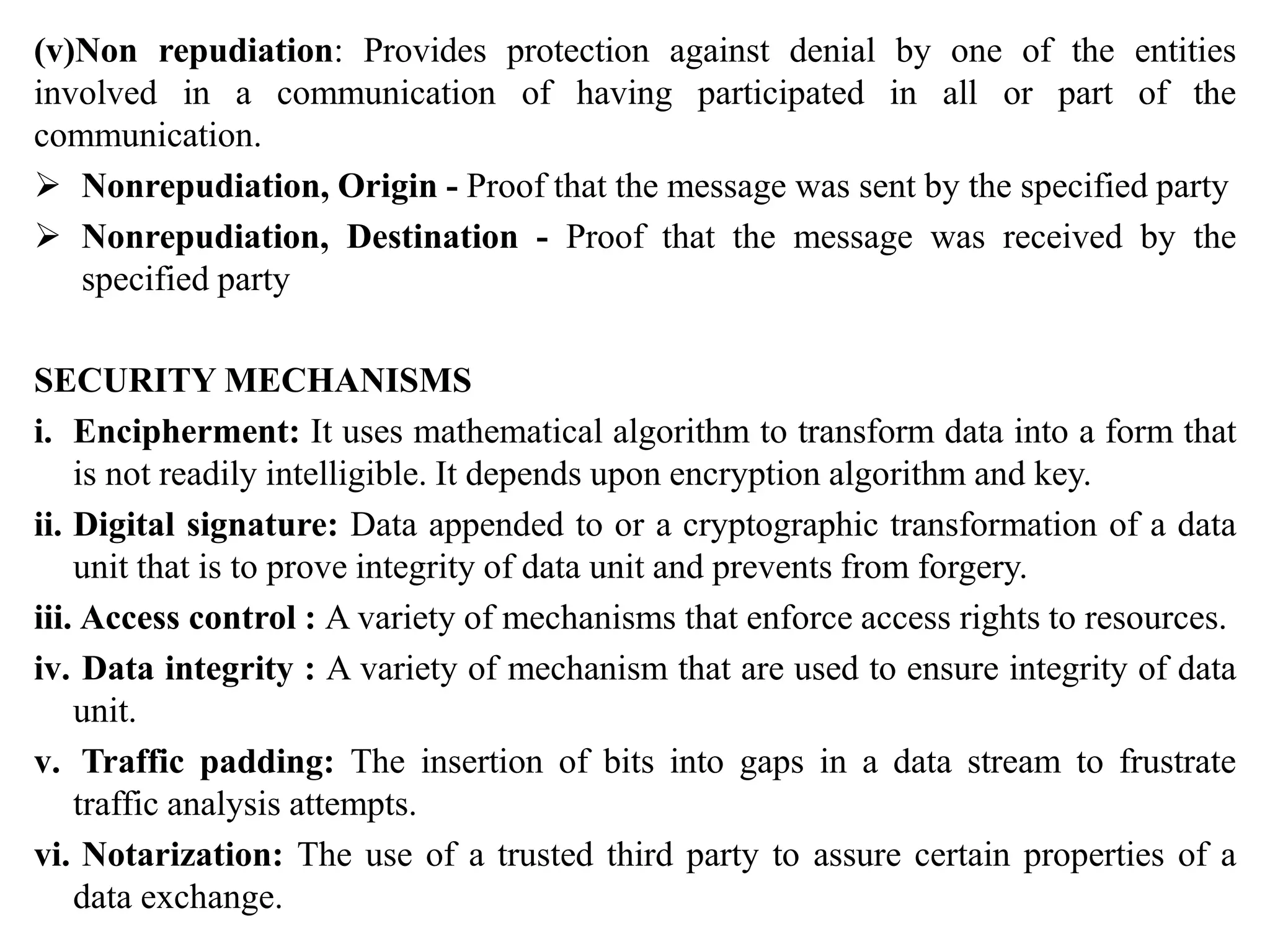
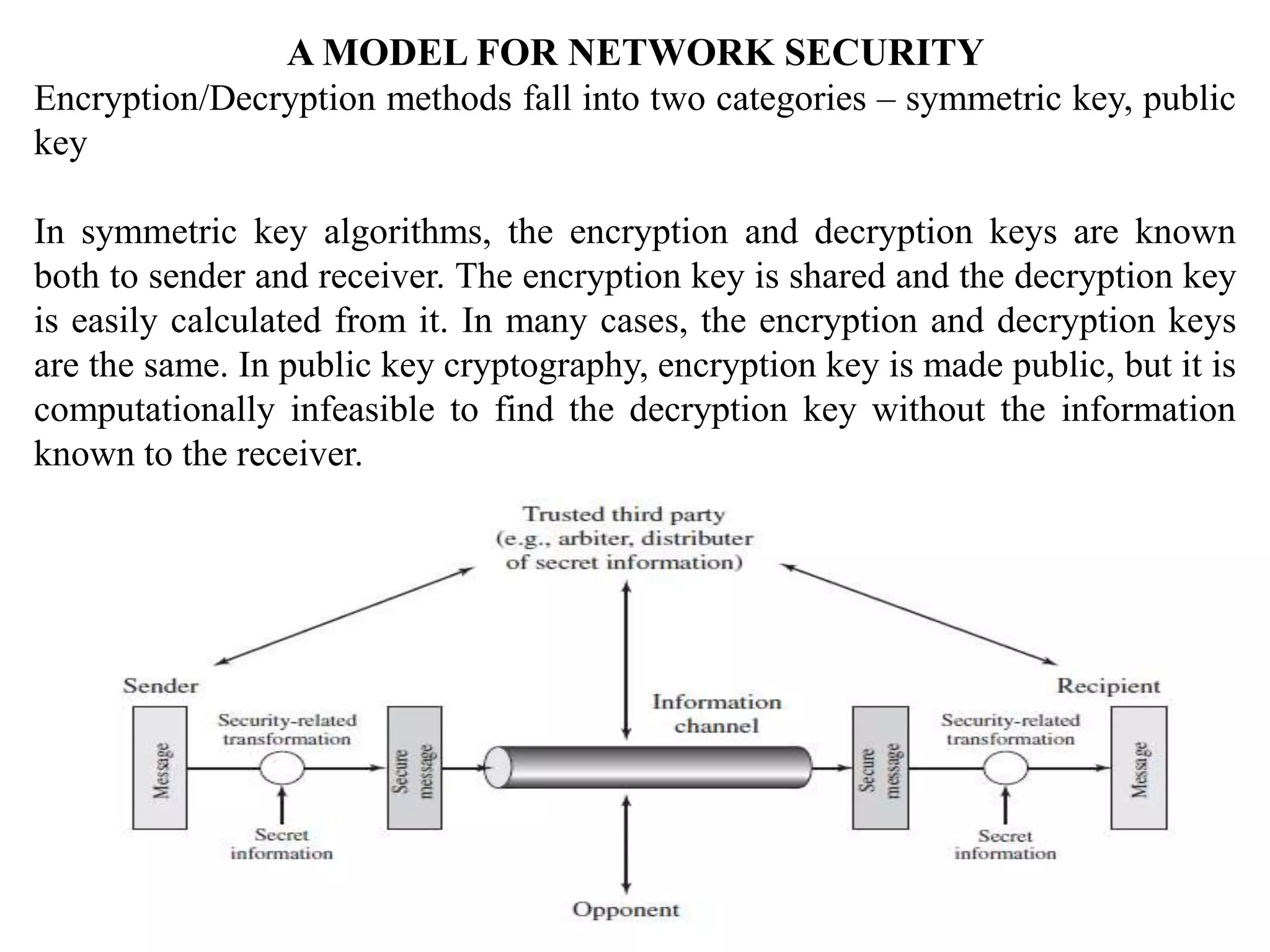
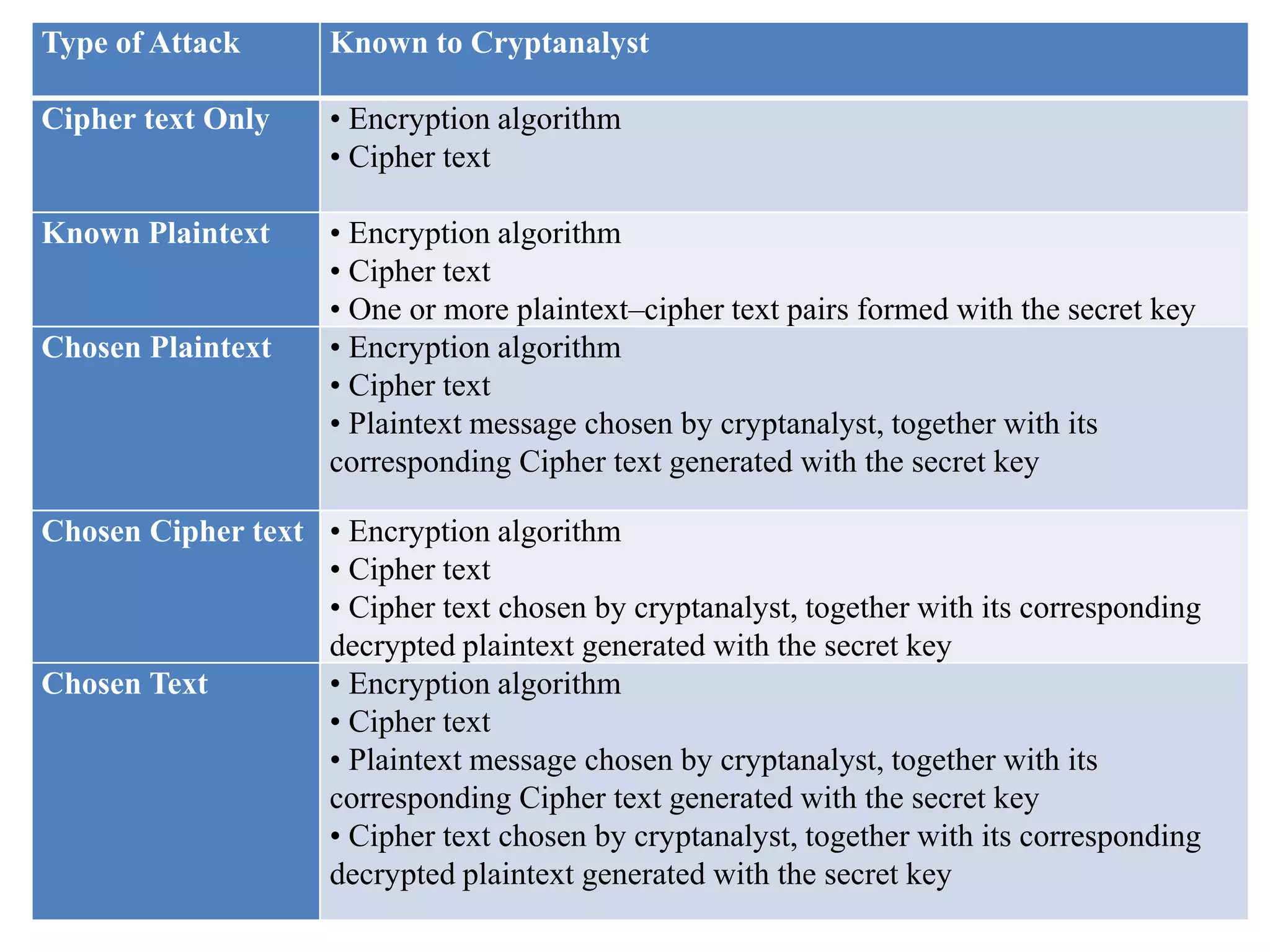
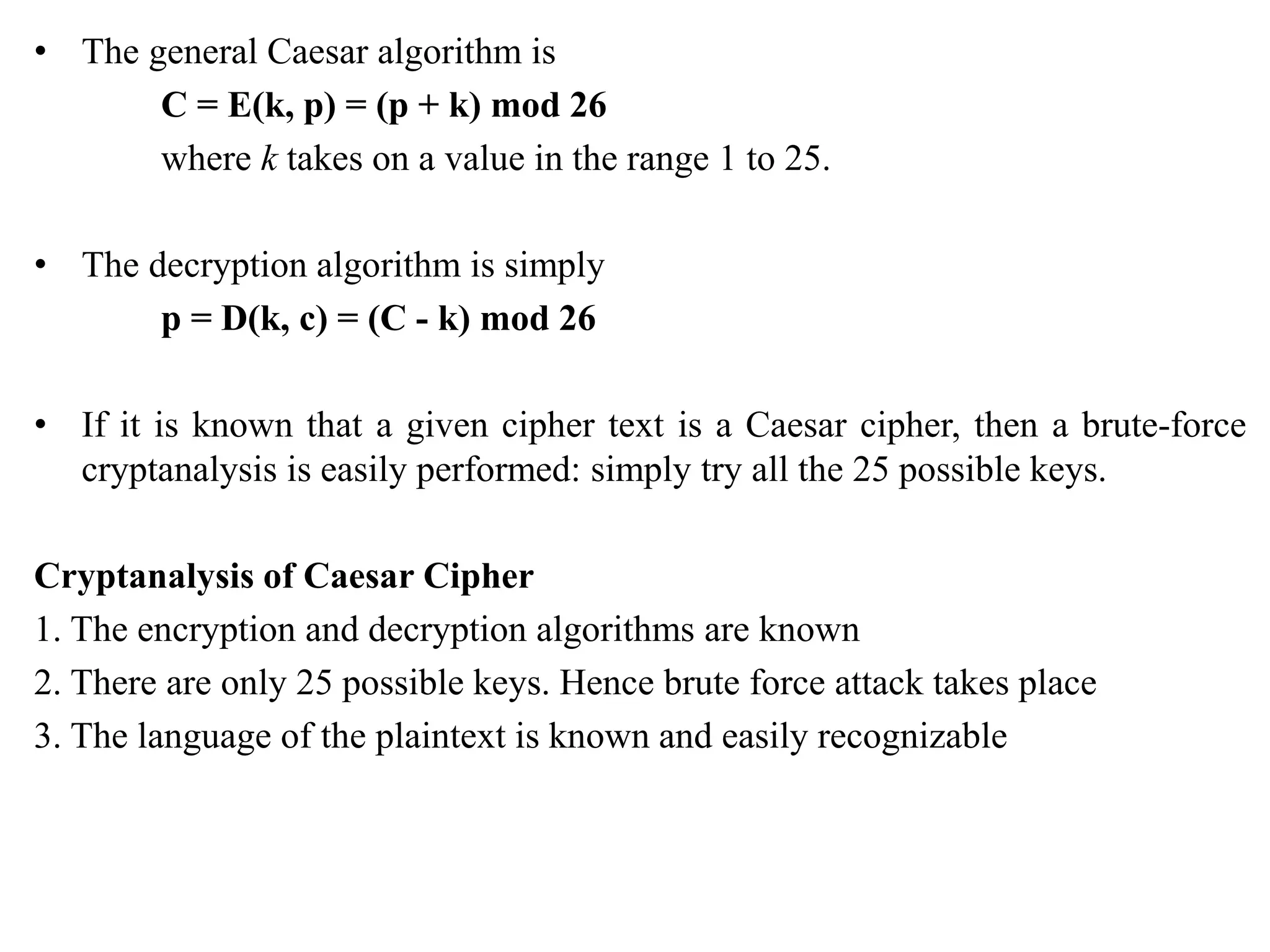
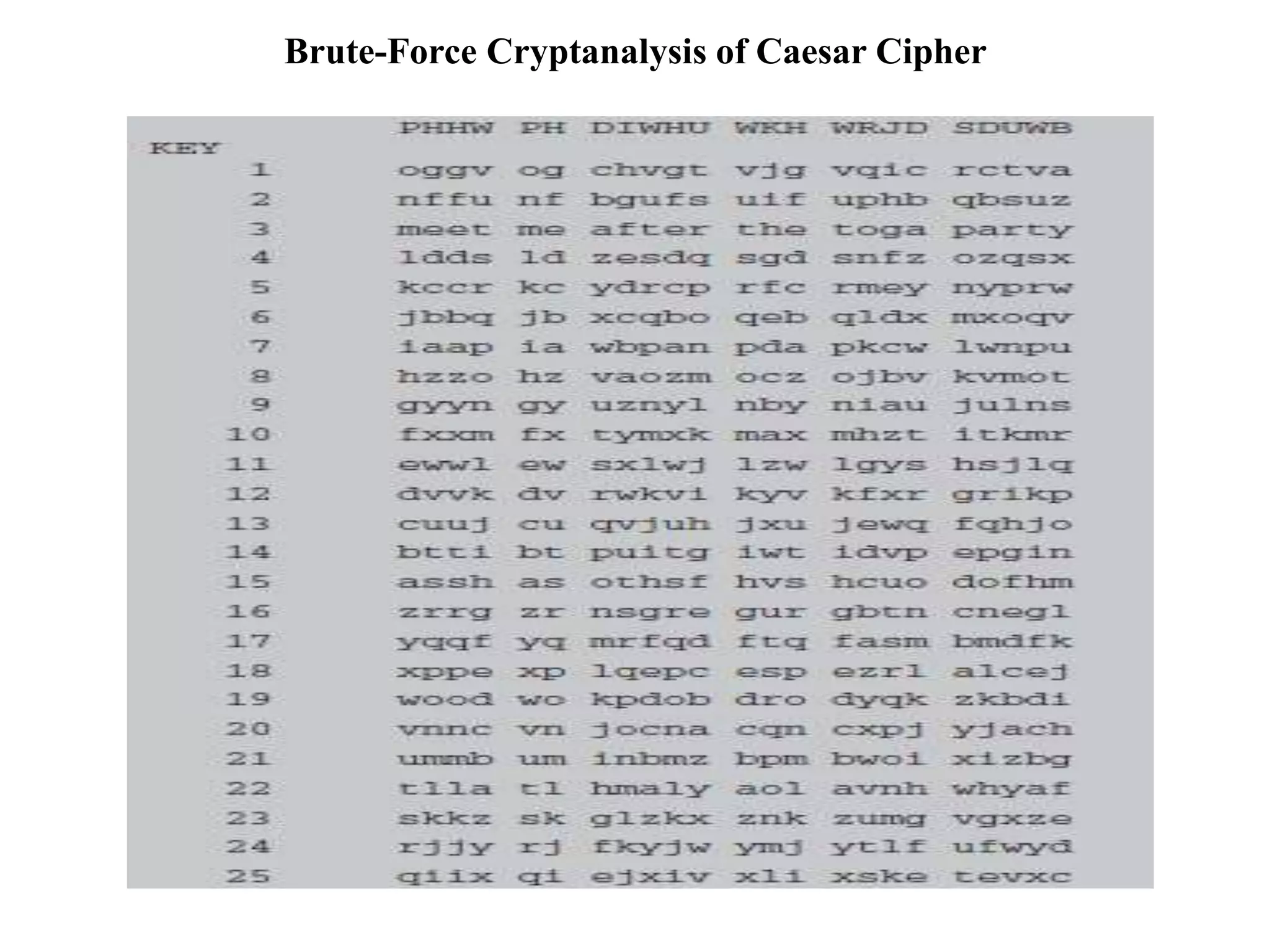
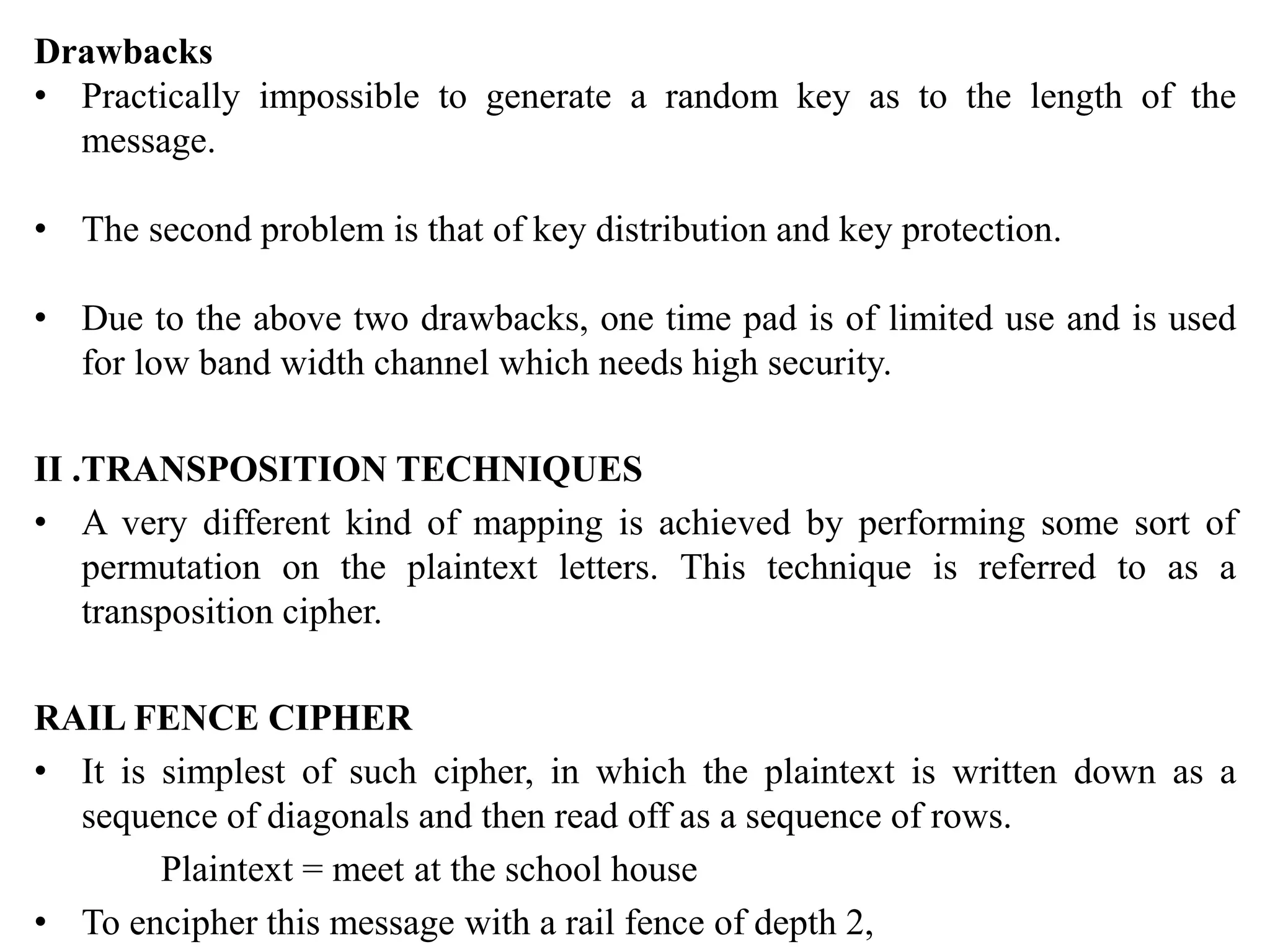
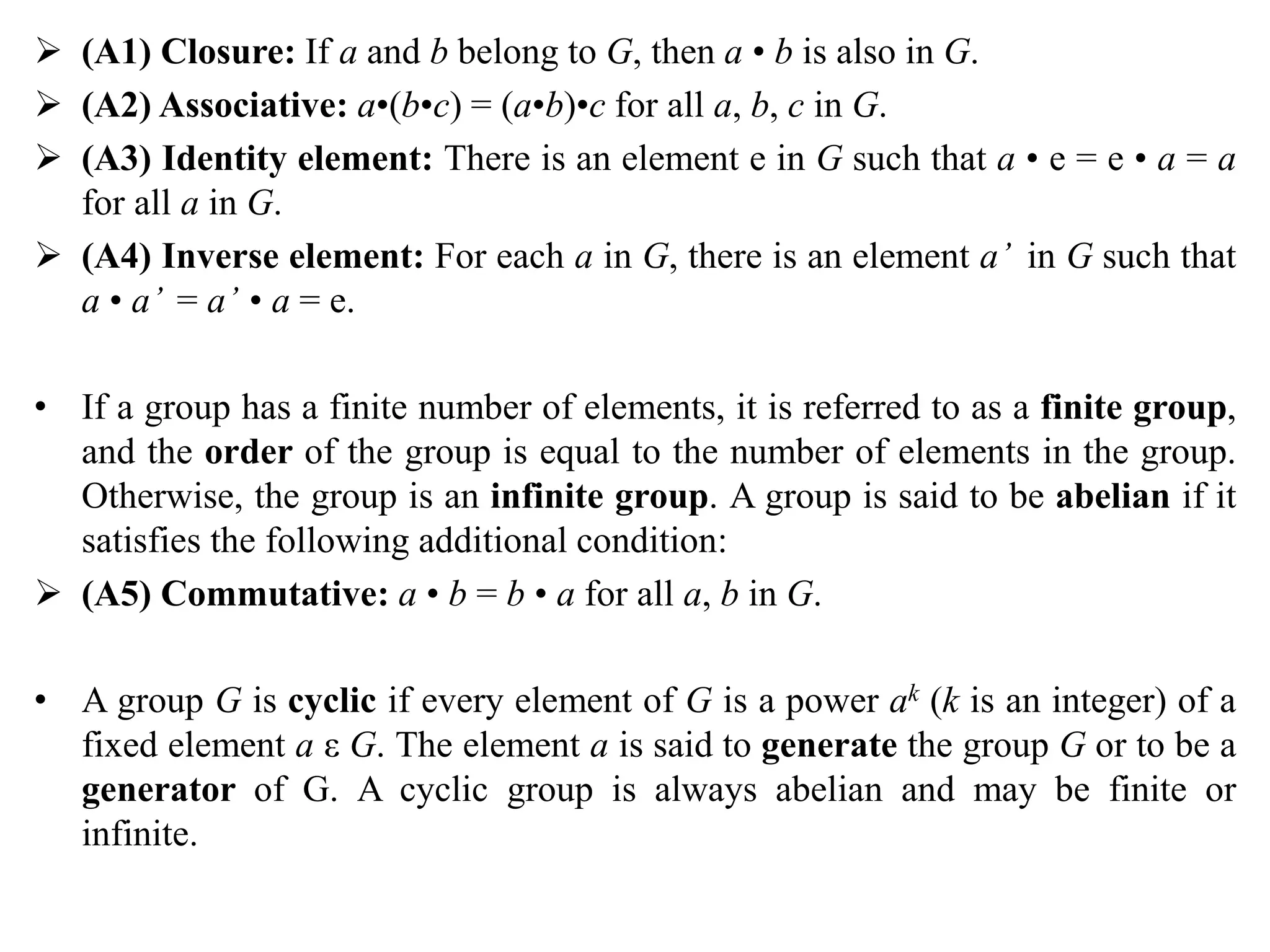
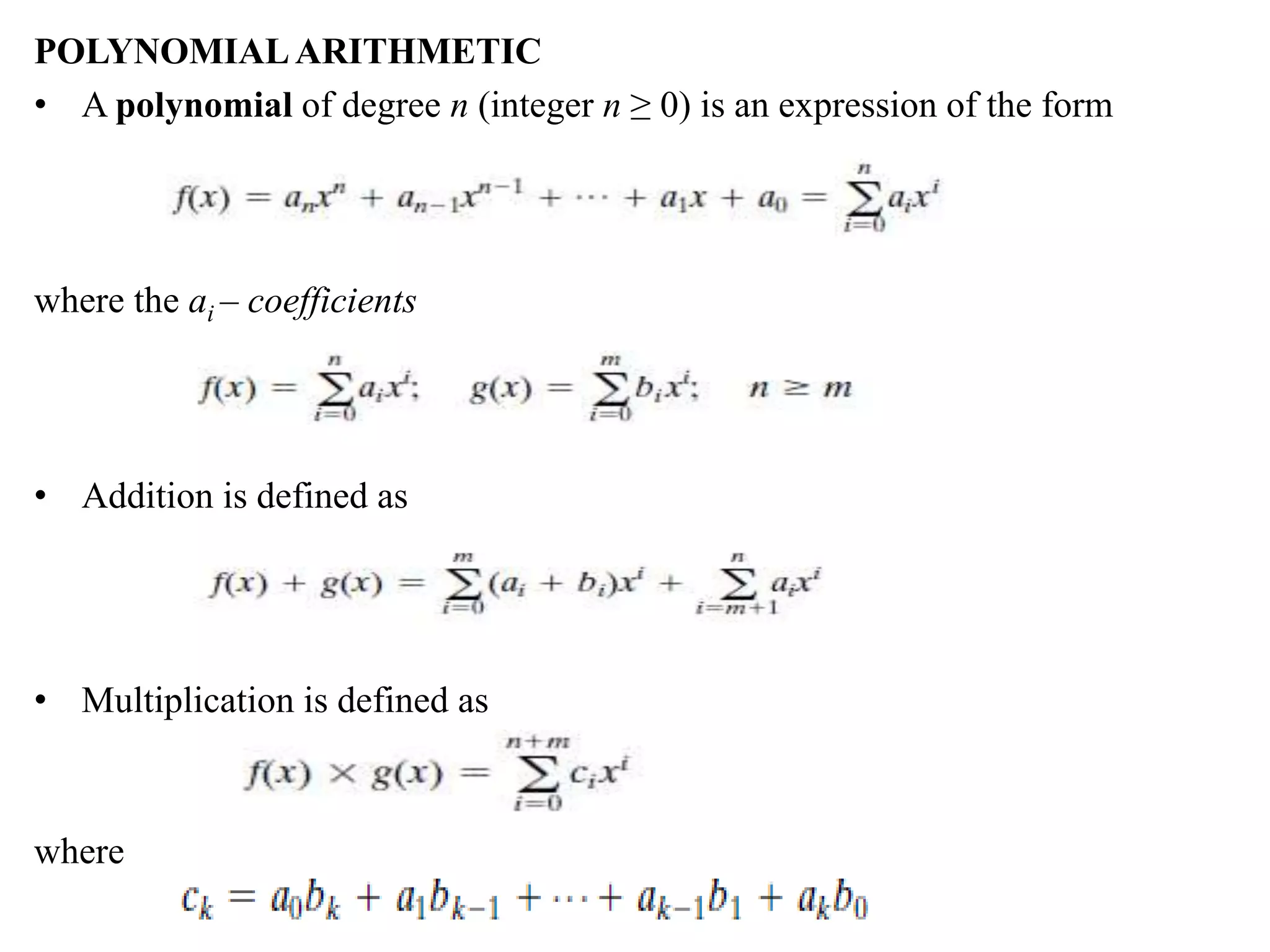
The document discusses various topics in network security including:
1. It describes the OSI security architecture and defines security attacks, mechanisms, and services.
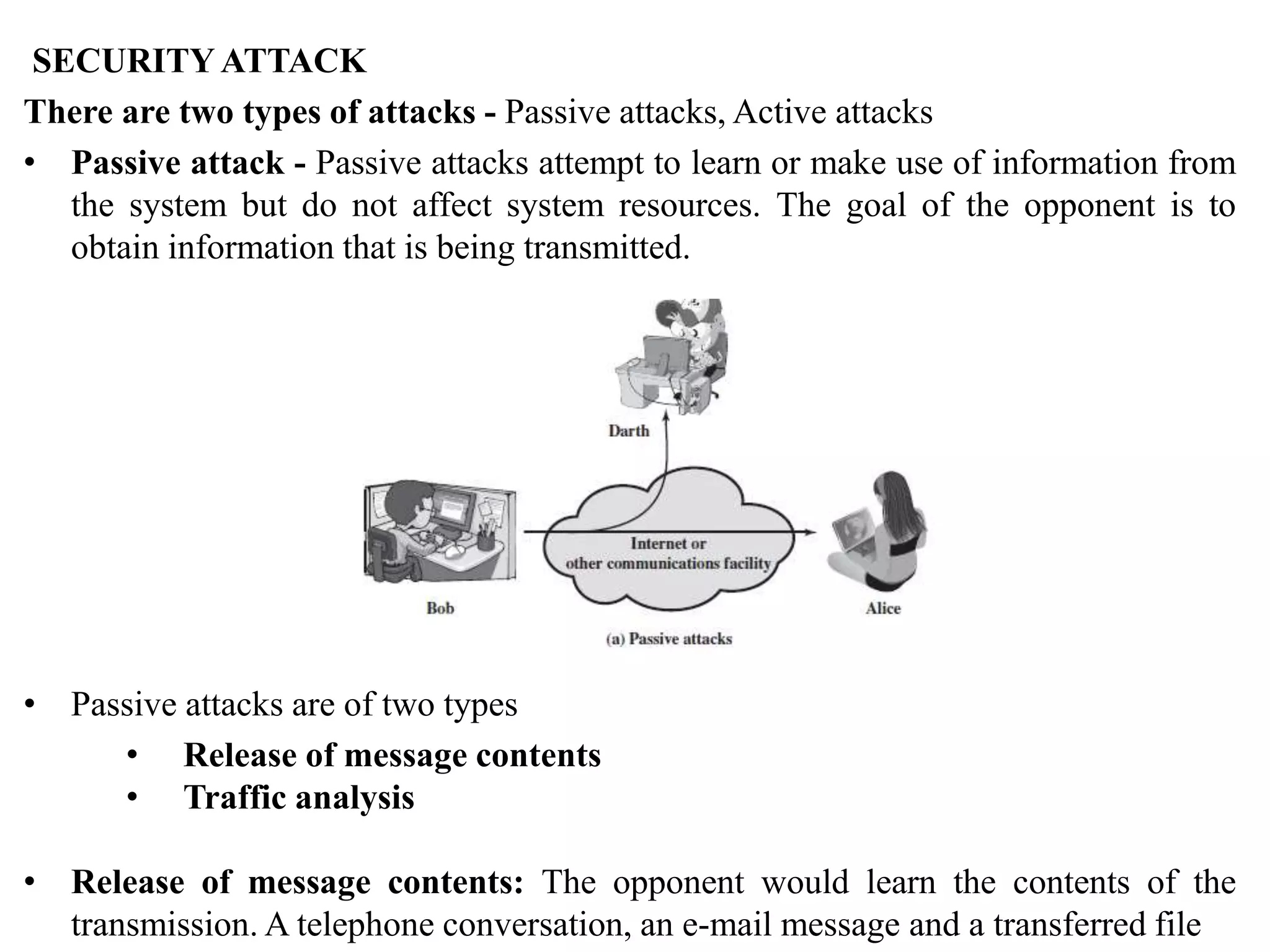
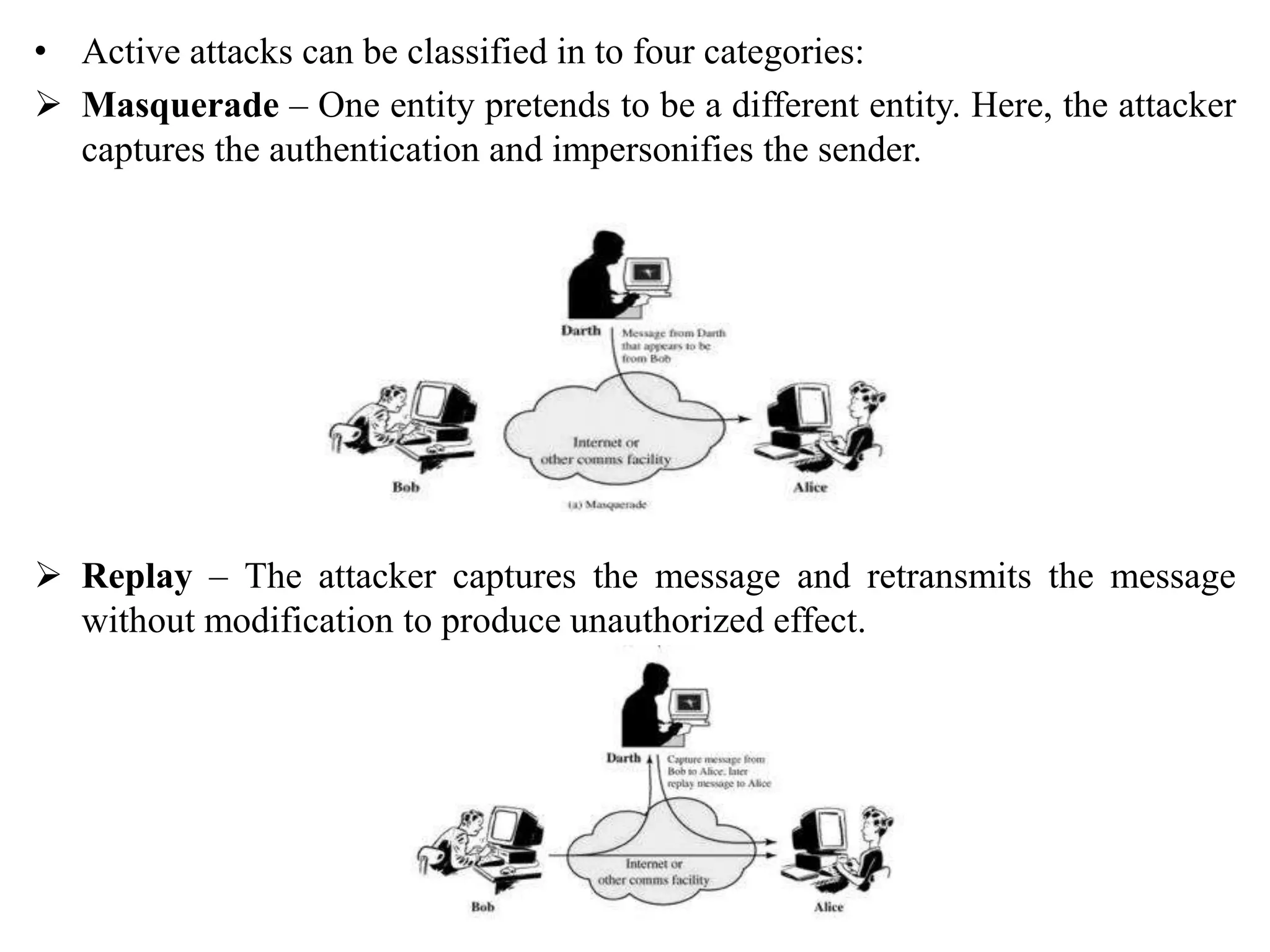
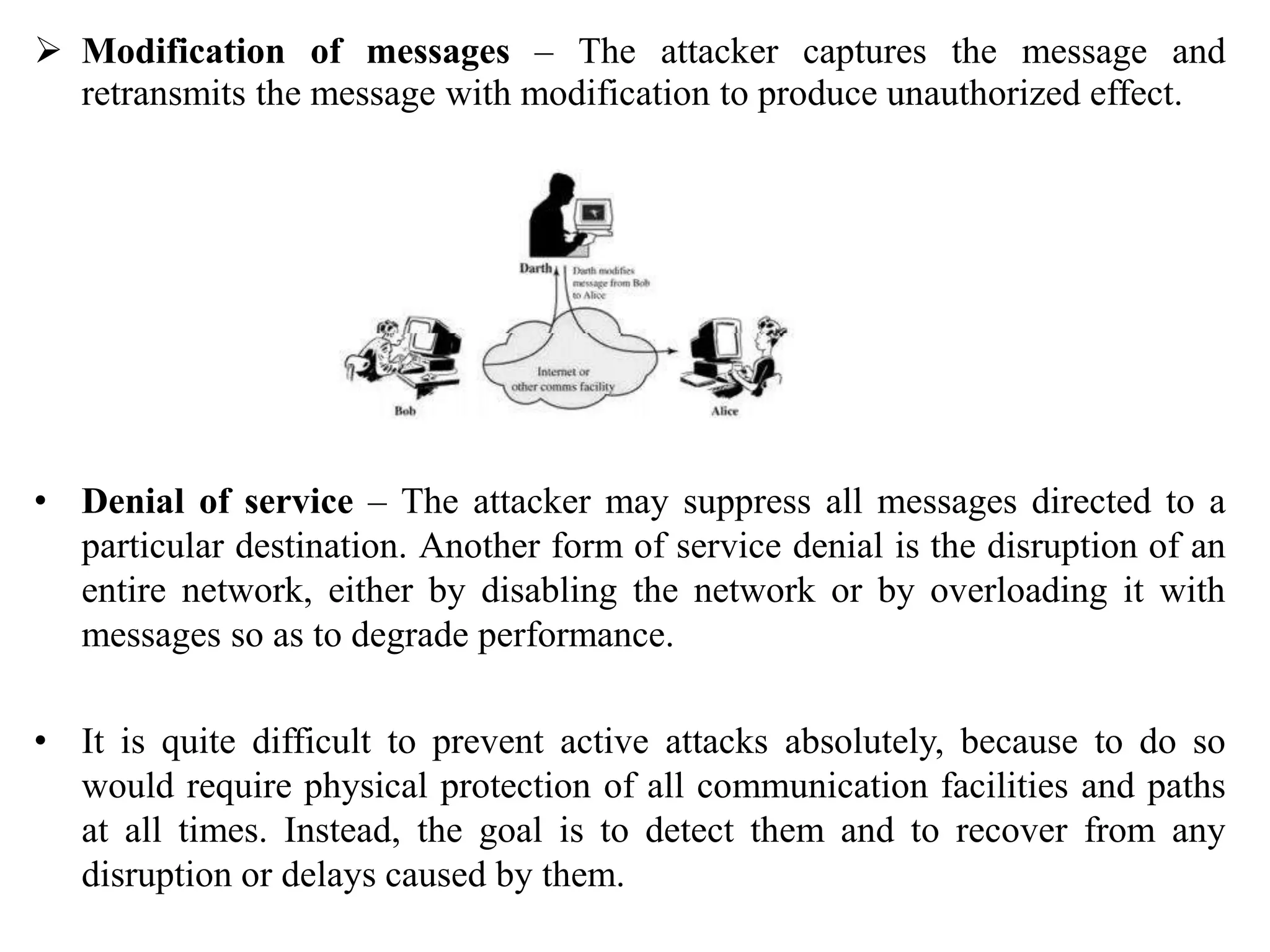
2. It covers different types of security attacks like passive attacks and active attacks.
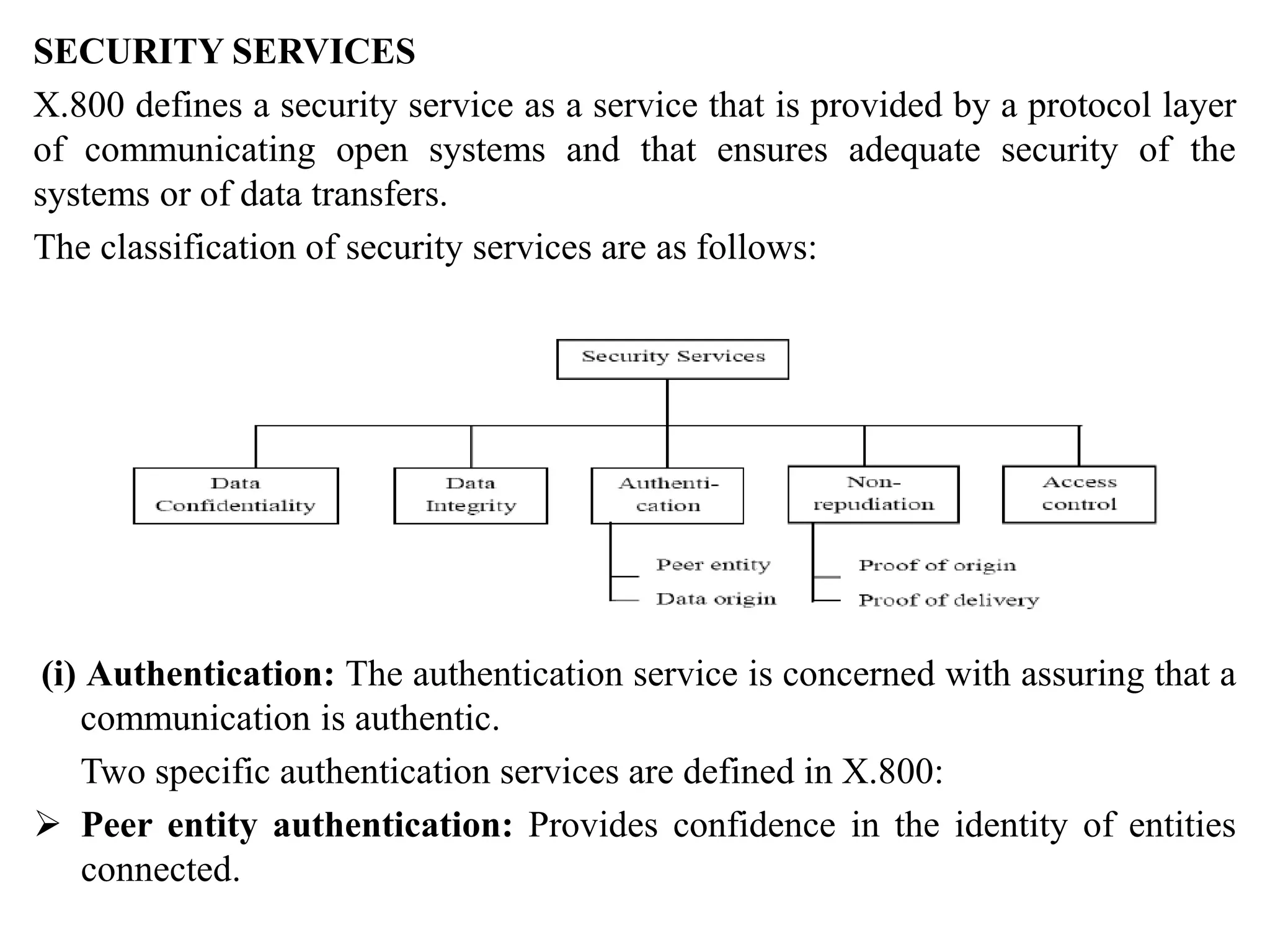
3. It discusses security services like authentication, access control, data confidentiality, and data integrity.
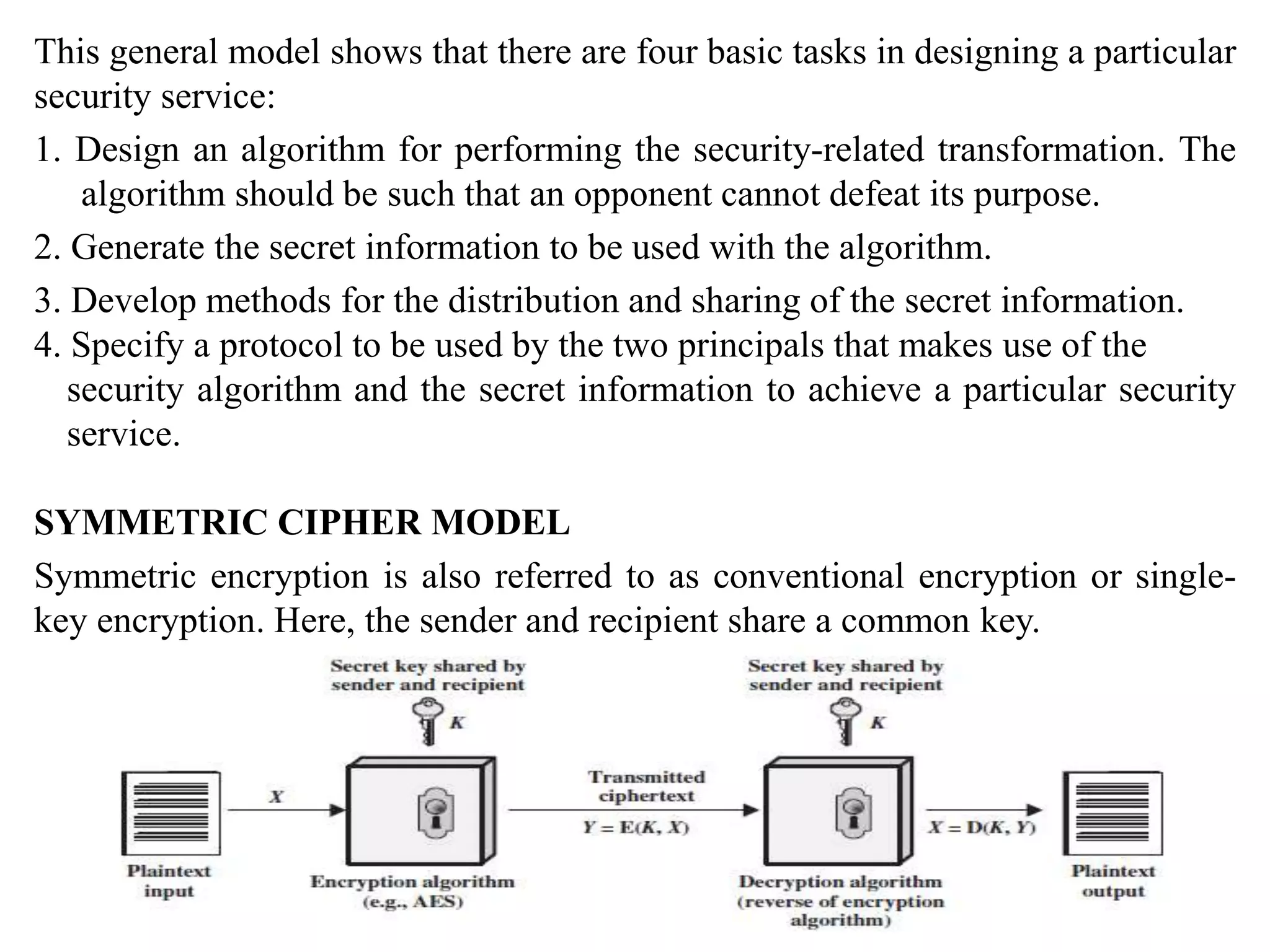
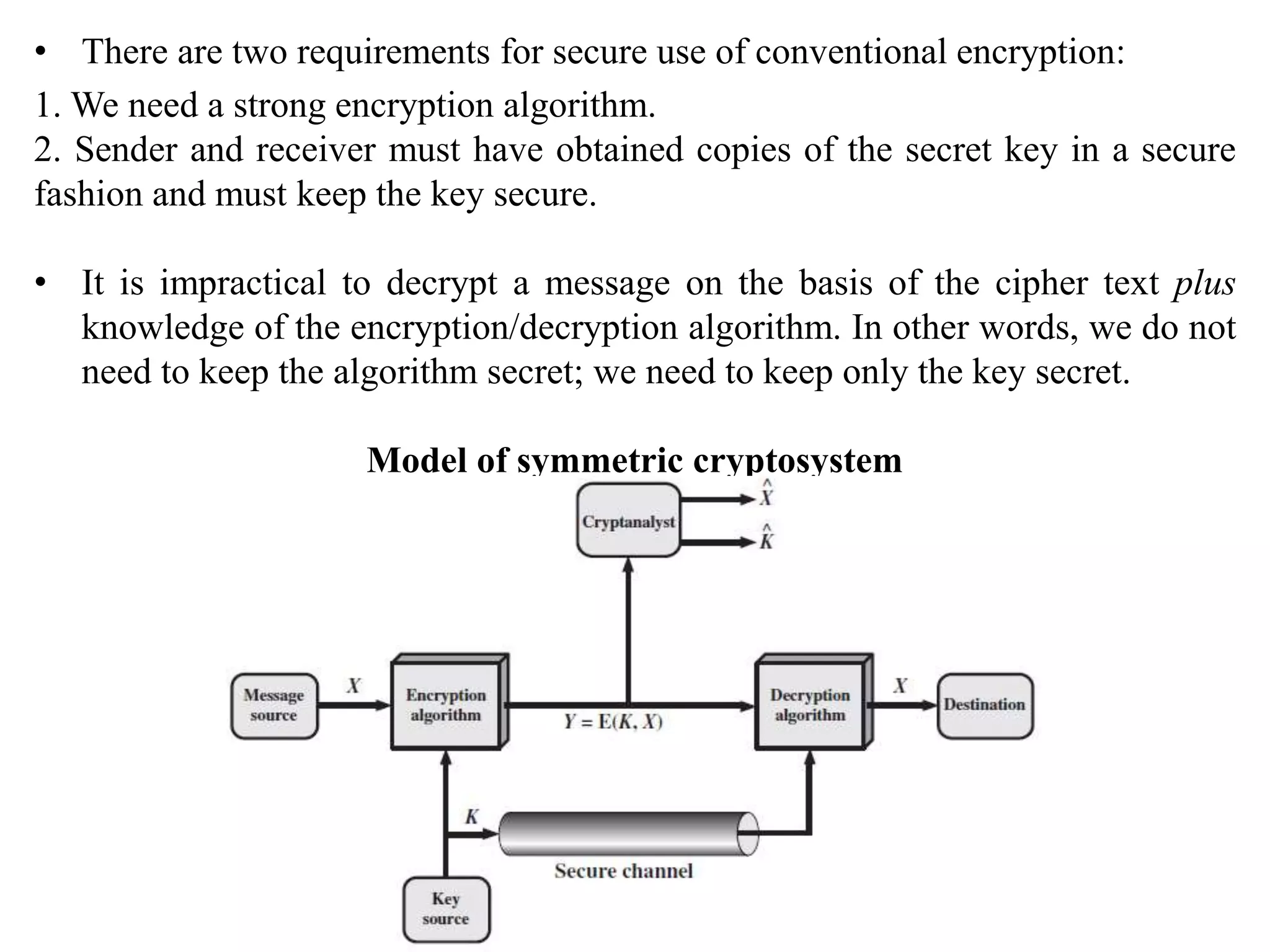
4. It provides an overview of classical encryption techniques like symmetric ciphers, substitution ciphers, transposition ciphers, and steganography.







![• A source produces a message in plaintext
X = [X1, X2,..., XM].
M- elements of X are letters.
• For encryption, a key of the form
K = [K1, K2, …, KJ] is generated.
• If the key is generated at the message source, then it must also be provided to
the destination by means of some secure channel. Alternatively, a third party
could generate the key and securely deliver it to both source and destination.
• With the message X and the encryption key K as input, the encryption
algorithm forms the cipher text
Y = [Y1, Y2,…, YN].
Y = E(K, X)
where Y- cipher text, E- Encryption algorithm, K- Key, X-Plain text
• At the receiver side the transformation is:
X = D(K, Y)
where Y- cipher text, D-Decryption algorithm, K- Key, X-Plain text](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-16-2048.jpg)



















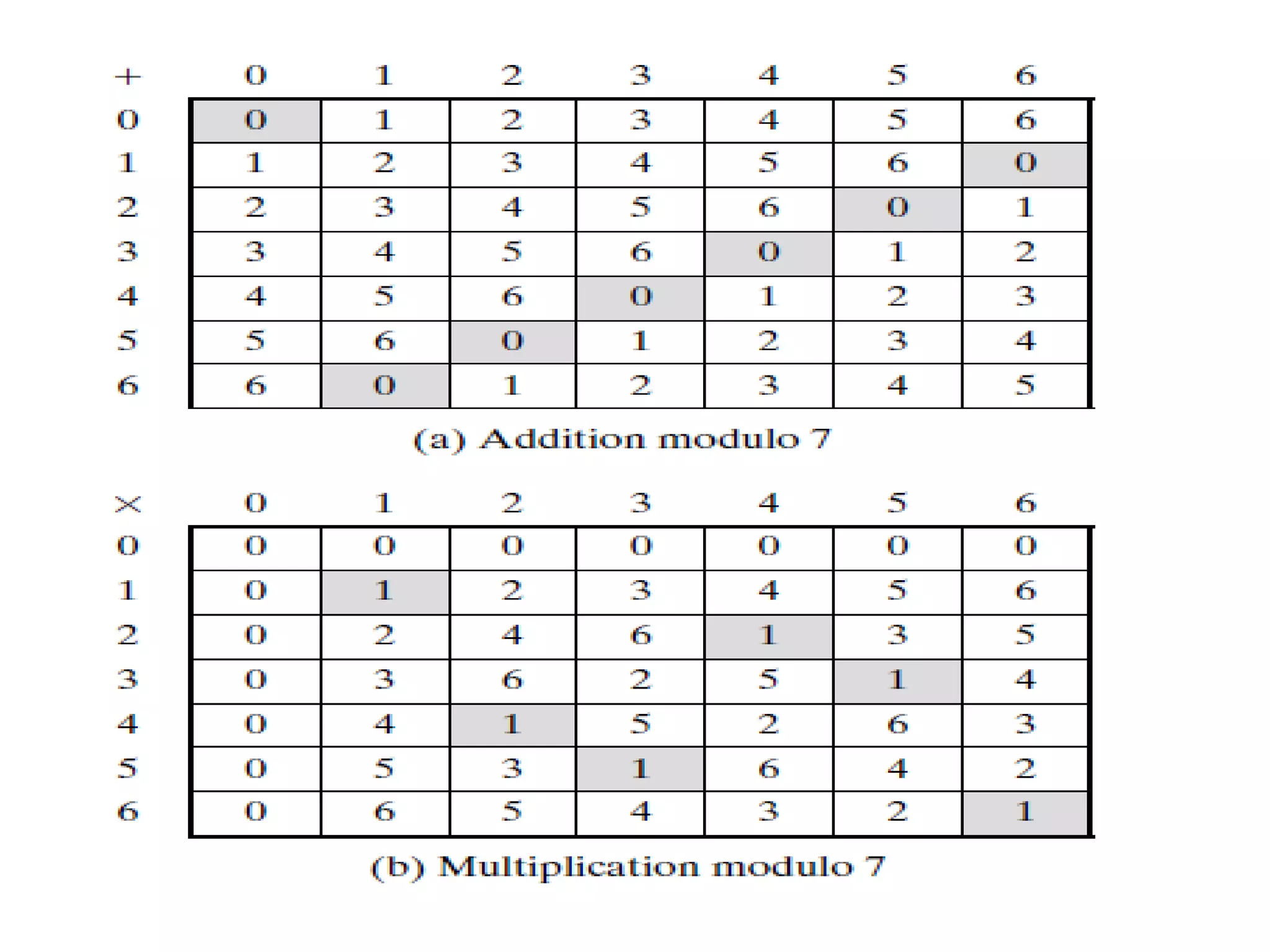
![Modular Arithmetic Operations
• Modular arithmetic exhibits the following properties:
1. [(a mod n) + (b mod n)] mod n = (a + b) mod n
2. [(a mod n) - (b mod n)] mod n = (a - b) mod n
3. [(a mod n) * (b mod n)] mod n = (a * b) mod n
• The proof for the above 3 properties can be explained with an example. For
example consider 11 mod 8 = 3 and 15 mod 8 = 7
1. [(11 mod 8) + (15 mod 8)] mod 8 = 10 mod 8 = 2
(11 + 15) mod 8 = 26 mod 8 = 2.
2. [(11 mod 8) - (15 mod 8)] mod 8 = -4 mod 8 = 4
(11 - 15) mod 8 = -4 mod 8 = 4.
3. [(11 mod 8) * (15 mod 8)] mod 8 = 21 mod 8 = 5
(11 * 15) mod 8 = 165 mod 8 = 5.](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-47-2048.jpg)



![• Let f(x) = x3 + x2 + 2 and g(x) = x2 - x + 1, where S is the set of integers. Then
Addition : f(x) + g(x) = x3 + 2x2 - x + 3
Subtraction: f(x) - g(x) = x3 + x + 1
Multiplication: f(x) * g(x) = x5 + 3x2 - 2x + 2
Finding the Greatest Common Divisor
• The polynomial c(x) is said to be the greatest common divisor of a(x) and
b(x) if:
1. c(x) divides both a(x) and b(x).
2. Any divisor of a(x) and b(x) is a divisor of c(x).
• An equivalent definition is the following:
• gcd [a(x), b(x)] is the polynomial of maximum degree that divides both a(x)
and b(x). Euclid’s algorithm can be adapted in the following form:
gcd[a(x), b(x)] = gcd[b(x), a(x) mod b(x)]](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-52-2048.jpg)
![• Euclid’s algorithm for polynomials assumes that the degree of a(x) is greater
than the degree of b(x). Then to find gcd[a(x), b(x)],
EUCLID[a(x), b(x)]
1. A(x) = a(x); B(x) = b(x)
2. if B(x) = 0 return A(x) = gcd[a(x), b(x)]
3. R(x) = A(x) mod B(x)
4. A(x) B(x)
5. B(x) R(x)
6. goto 2
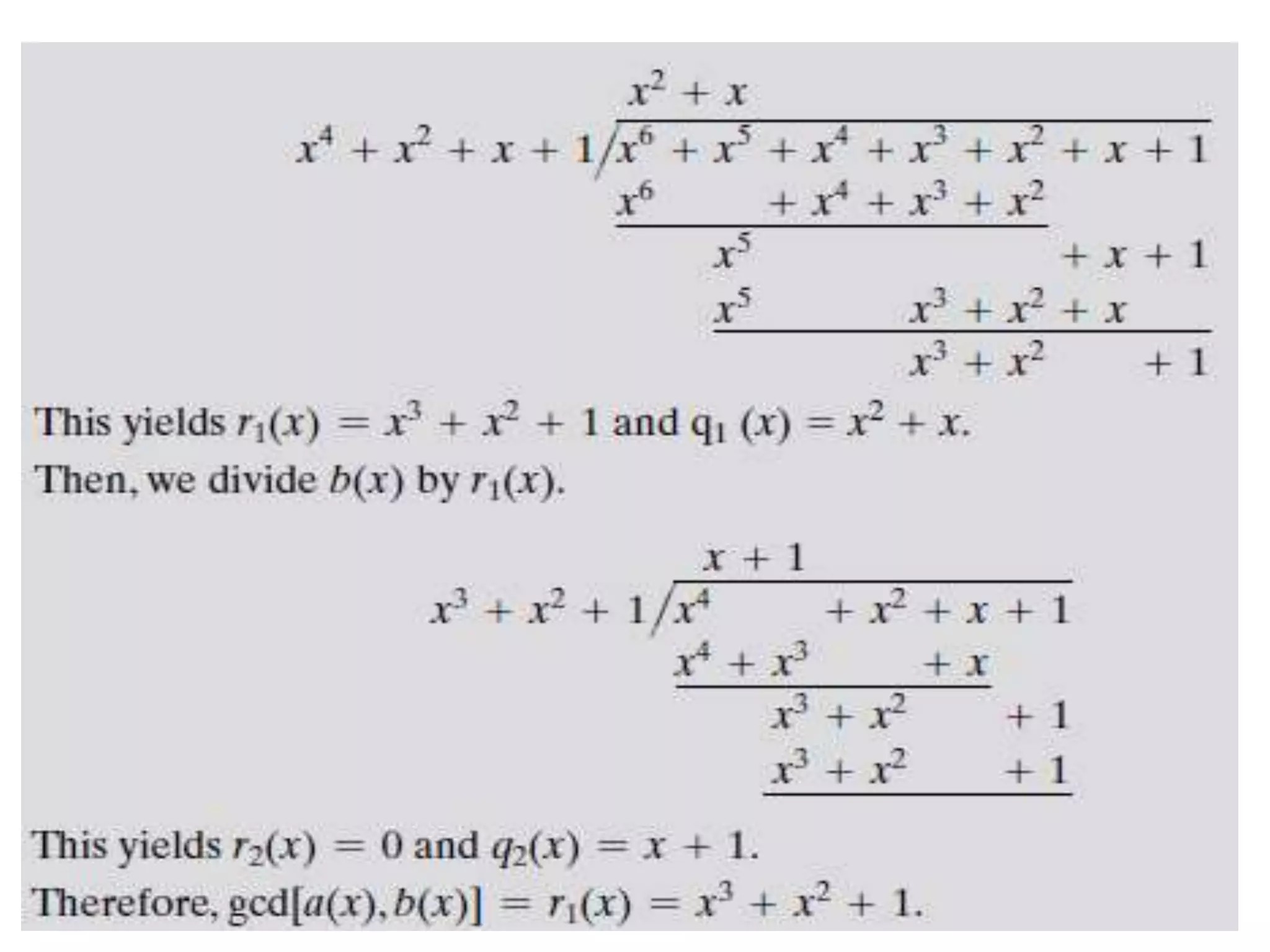
• Find gcd[a(x), b(x)] for a(x) = x6 + x5 + x4 + x3 + x2 + x + 1 and b(x) = x4 + x2
+ x + 1.
• Euclidean algorithm to compute the greatest common divisor of two
polynomials
gcd[a(x), b(x)] = gcd[b(x), a(x) mod b(x)]
= gcd(b(x),r1(x))
= gcd[r1(x),b(x) mod r1(x)]](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-53-2048.jpg)




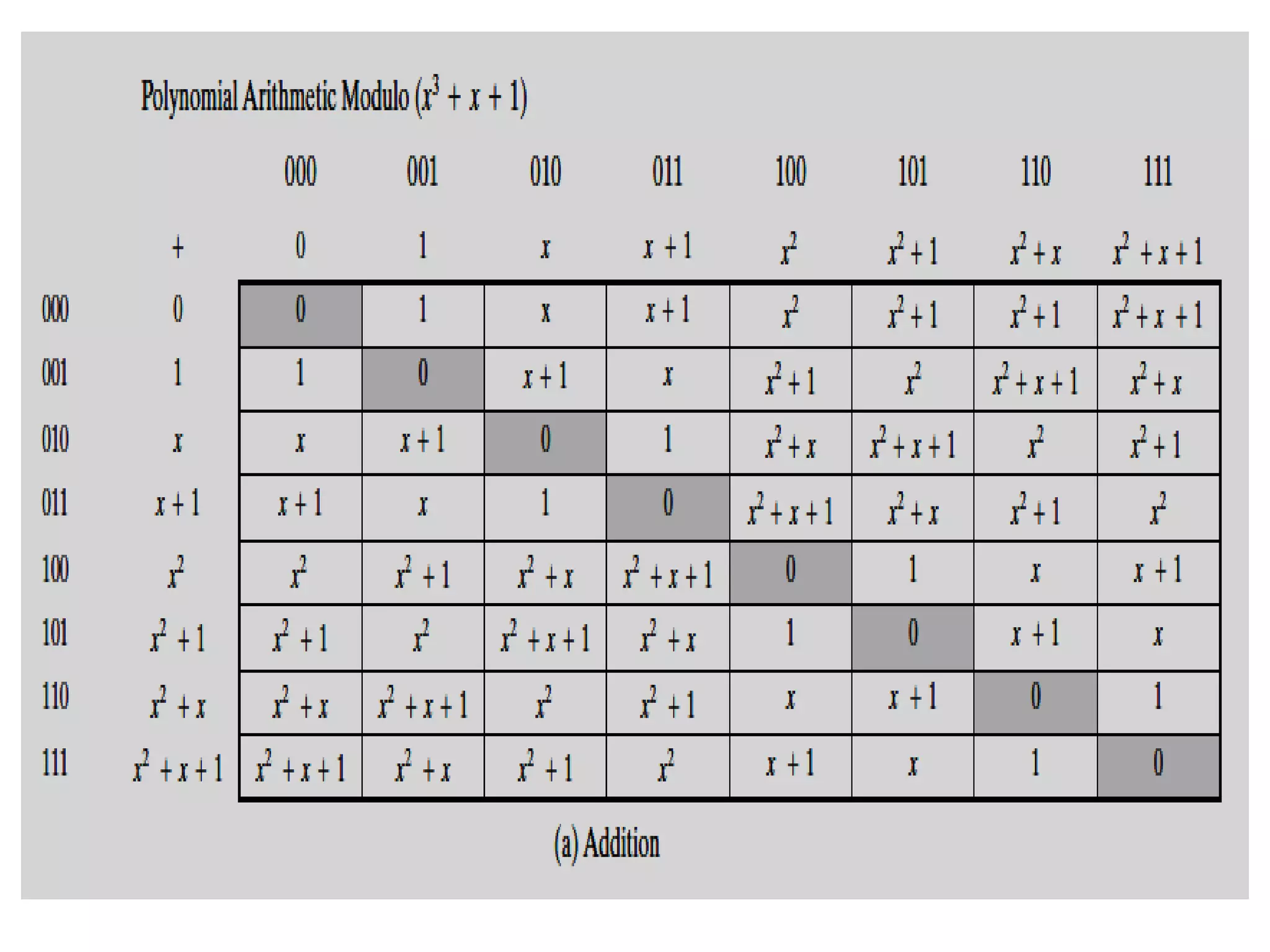
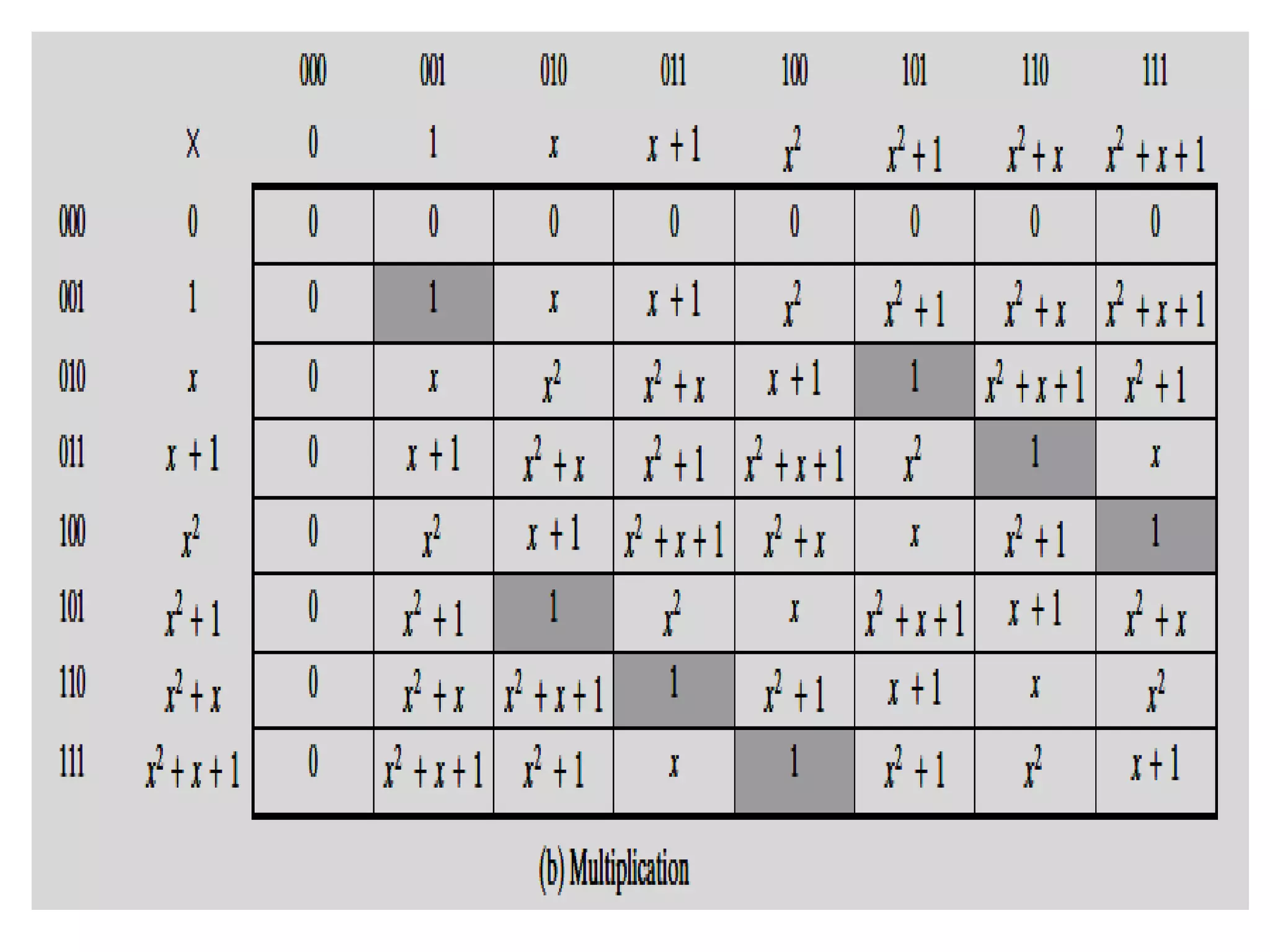
![Finding the Multiplicative Inverse of a polynomial
• The extended Euclidean algorithm can be adapted to find the multiplicative
inverse of a polynomial. Specifically, the algorithm will find the
multiplicative inverse of b(x) modulo m(x) if the degree of b(x) is less than
the degree of m(x) and gcd[m(x), b(x)] = 1.
• If m(x) is an irreducible polynomial, then it has no factor other than itself or
1, so that gcd[m(x), b(x)] = 1. The algorithm is as follows:
EXTENDED EUCLID [m(x), b(x)]
1. [A1(x), A2(x), A3(x)][1, 0, m(x)]; [B1(x), B2(x),B3(x)] [0, 1, b(x)]
2. if B3(x) = 0 return A3(x) = gcd[m(x), b(x)]; no inverse
3. if B3(x) = 1 return B3(x) = gcd[m(x), b(x)]; B2(x) = b(x)-1 mod m(x)
4. Q(x) = quotient of A3(x) / B3(x)
5. [T1(x), T2(x), T3(x)] [A1(x)-Q(x)B1(x),A2(x)-Q(x)B2(x),A3(x)-Q(x)B3(x)]
6. [A1(x), A2(x), A3(x)] [B1(x), B2(x), B3(x)]
7. [B1(x), B2(x), B3(x)] [T1(x), T2(x), T3(x)]
8. goto 2](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-60-2048.jpg)




{1 * 2 *…*(p-1)} ap-1 ≡ [(1*2*…*(p-1)](mod p)
(p-1)! ap-1≡ (p-1)!(mod p)
ap-1 ≡ 1(mod p)
Example
a = 7, p = 19
72 = 49≡ 11 (mod 19)
74 = 121 ≡ 7 (mod 19)
78 ≡ 49 ≡ 11 (mod 19)
716 ≡ 121 ≡ 7 (mod 19)
ap-1 = 718 = 716 * 72 ≡ 7 * 11 ≡ 1 (mod 19).](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-66-2048.jpg)
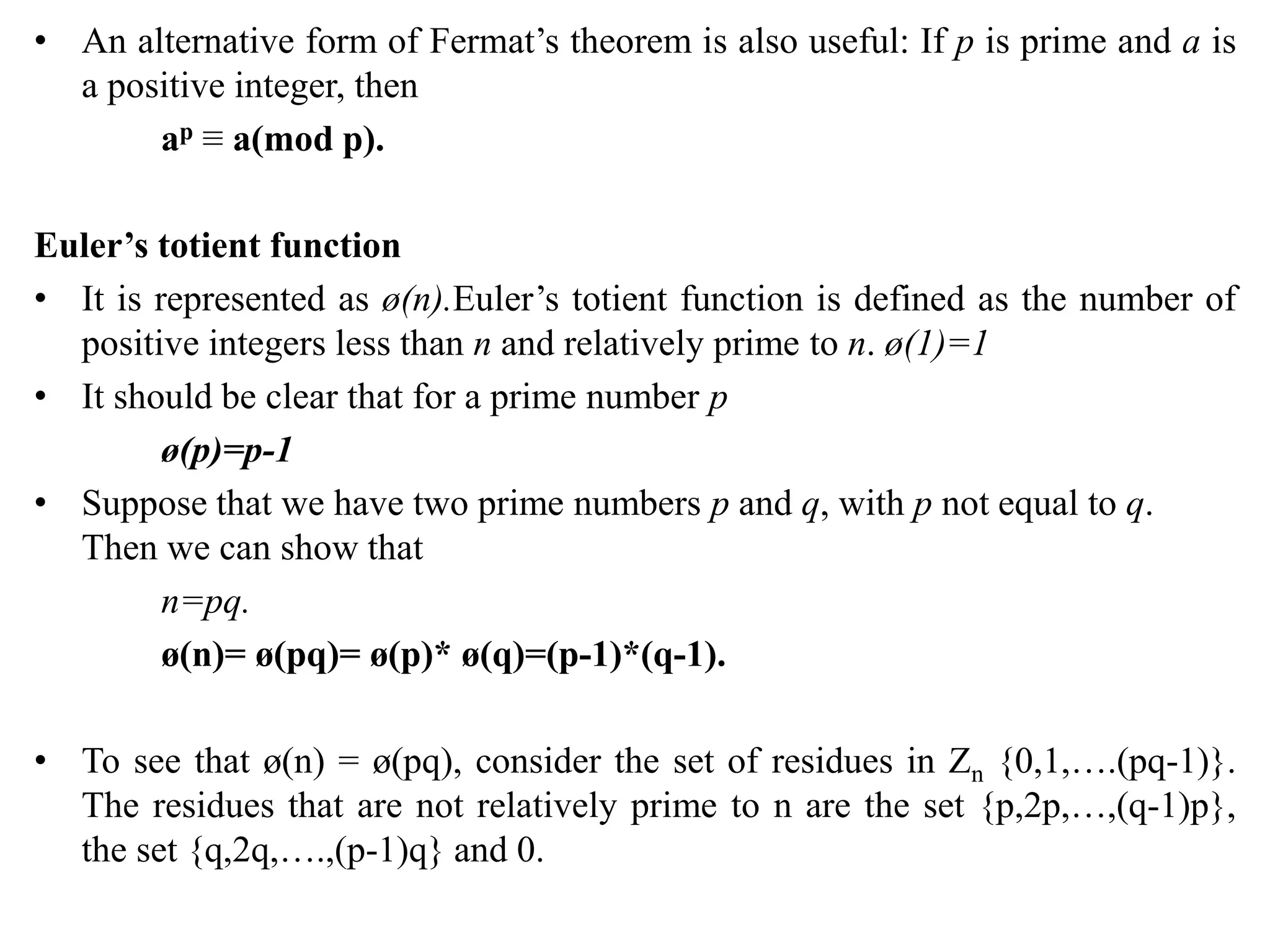
![ø(n) = (pq-1) - [(q-1)+(p-1)]
= pq - (p+q)+1
= (p-1) * (q-1)
= ø(p) * ø(q).
• To determine f(35), we list all of the positive integers less than 35 that are
relatively prime to it:
1, 2, 3, 4, 6, 8, 9, 11, 12, 13, 16, 17, 18, 19, 22, 23, 24, 26, 27, 29, 31, 32,
33, 34
There are 24 numbers on the list, so f(35) = 24.
f(21) = f(3) * f(7) = (3 - 1) * (7 - 1) = 2 * 6 = 12.](https://image.slidesharecdn.com/unit-1-230419141754-43eb54a6/75/Unit-1-pptx-68-2048.jpg)