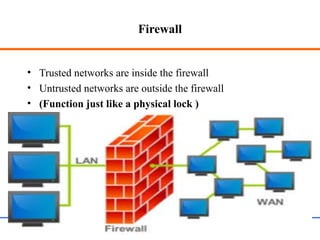
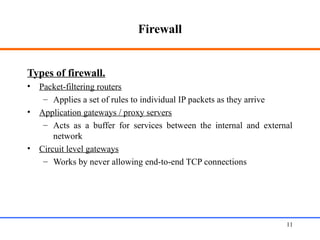
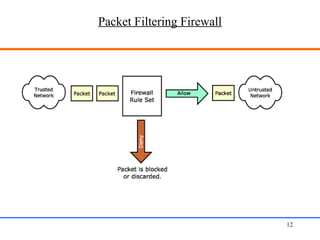
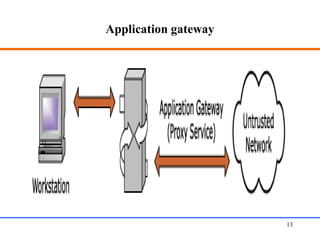
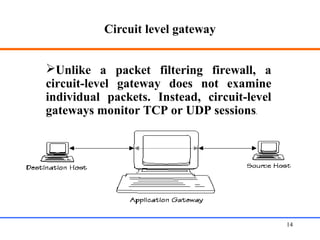
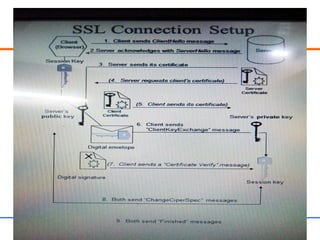
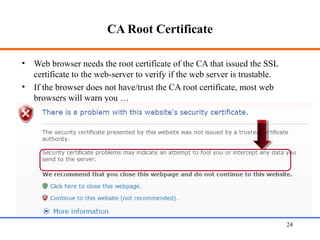
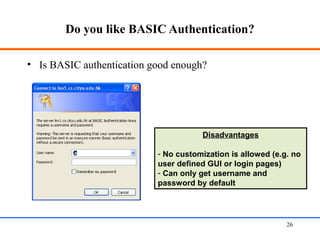
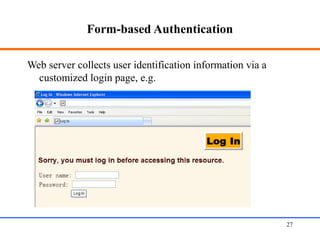
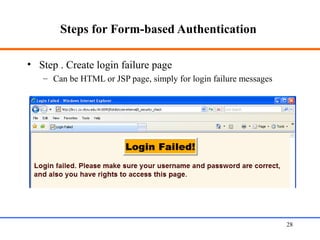
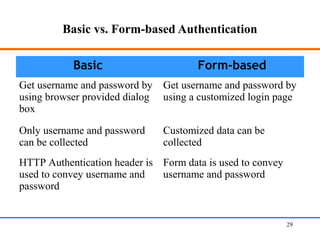
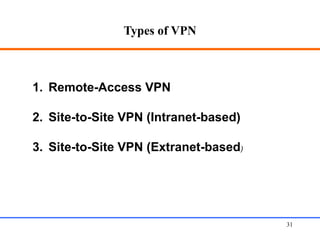
This document discusses various aspects of web security, including the need for security when transmitting data over the internet, common security measures like authentication, authorization, encryption, and accountability. It describes techniques for securing web applications such as SSL, firewalls, VPNs. It provides details on authentication methods like basic authentication and form-based authentication. It also explains concepts like SSL certificates, VPN types, and how firewalls and SSL work.