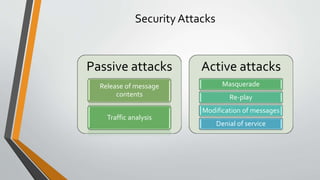
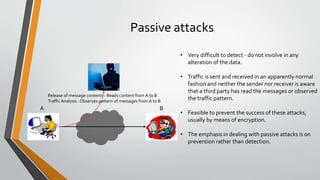
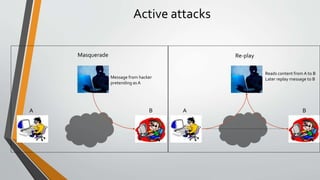
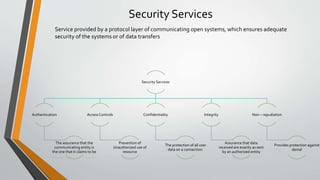
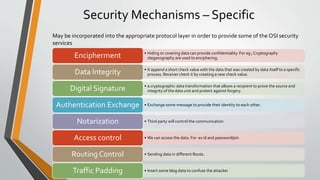
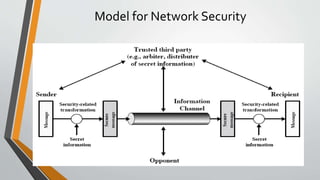
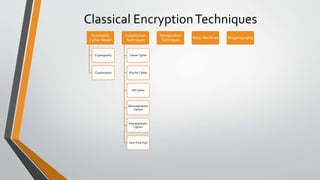
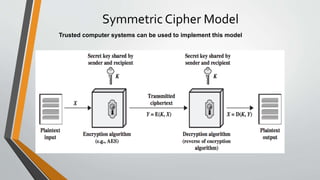
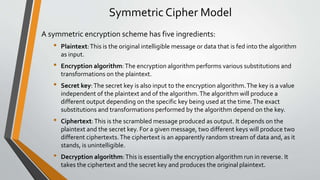
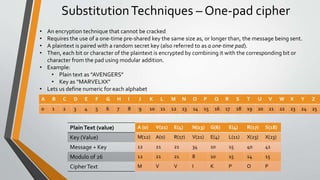
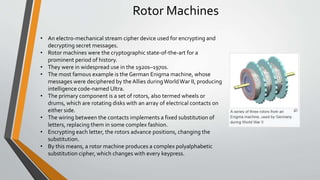
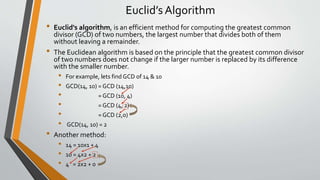
Cryptography is the study and practice of techniques for secure communication in the presence of third parties. It deals with developing and analysing protocols which prevents malicious third parties from retrieving information being shared between two entities. Some key principles of cryptography include confidentiality, data integrity, authentication, and non-repudiation. Cryptography is widely applied in computer security, network security, and internet security. Common techniques include symmetric encryption algorithms, cryptanalysis methods, and the use of substitution and transposition ciphers.

























![Modular arithmetic
• Modular arithmetic is a system of arithmetic for integers, where numbers "wrap around" upon
reaching a certain value—the modulus
• A familiar use of modular arithmetic is in the 12-hour clock, in which the day is divided into two
12-hour periods.
• If the time is 7:00 now, then 8 hours later it will be 3:00 [(7 + 8) mod 12 = 3]
• Congruence
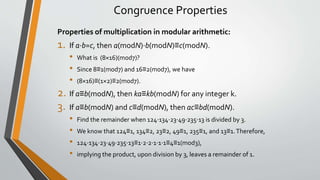
• a is congruent to b mod n can be written as a≡b (mod n).
• For a positive integer n, the integers a and b are congruent mod(n) if their remainders when divided by n are
the same.
• Another way of defining this is that integers a and b are congruent mod(n) if their difference (a - b) is an
integer multiple of n, that is, if (a-b)/n has a remainder of 0.
Example:
52≡24(mod7)
52 and 24 are congruent (mod 7) because 52(mod7)=3 and 24(mod7)=3.
Note that = is different from ≡.
Example:
36≡10(mod13)
36 and 10 are said to be congruent (mod 13) because their difference
36 - 10 = 26 is an integer multiple of n=13, that is, 26 = 2 x 13.](https://image.slidesharecdn.com/cnsnewpptunit1-230214044150-ed7a9590/85/CNS-new-ppt-unit-1-pptx-40-320.jpg)

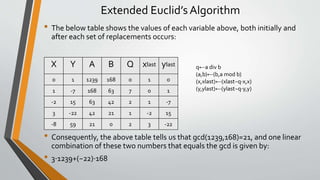
![Extended Euclid’s Algorithm
• Consider the numbers a=1239 and b=168.Their greatest common divisor (gcd) is 21. Moreover, we can
express 21 as a linear combination of a and b (i.e., as a sum of integer multiples of a and b):
• 21=3⋅1239+(−22)⋅168 [gcd(a,b) = a.x + b.y]
• The Extended EuclideanAlgorithm can be used to find the greatest common divisor (gcd) of two numbers,
and to simultaneously express the gcd as a linear combination of these numbers.Amazingly, this algorithm
finds the greatest common factor of two numbers without ever factoring the numbers! Further, it works
incredibly fast, even on extremely large numbers (with hundreds of digits).The speed at which this
algorithm works coupled with the necessary relative slowness of actually factoring very large numbers lies
at the heart of how modern cryptographic methods work (the same methods that keep your credit card
information safe when you are surfing the internet).
• The algorithm is best explained by example.To find the gcd and an associated linear combination for
a=1239 and b=168 , we do the following:
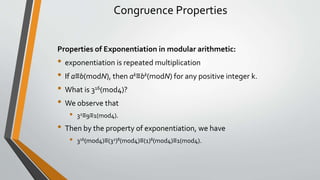
• First, we initialize some additional variables with the following values: q=0, x=0, y=1, xlast=1, and ylast=0
• Then, while b is not zero, we make the following replacements (in order):
• q←a div b
• (a,b)←(b,a mod b)
• (x,xlast)←(xlast−q⋅x,x)
• (y,ylast)←(ylast−q⋅y,y)
• When we are done, it should be the case that
• gcd(x,y)=xlast⋅1239+ylast⋅168](https://image.slidesharecdn.com/cnsnewpptunit1-230214044150-ed7a9590/85/CNS-new-ppt-unit-1-pptx-45-320.jpg)