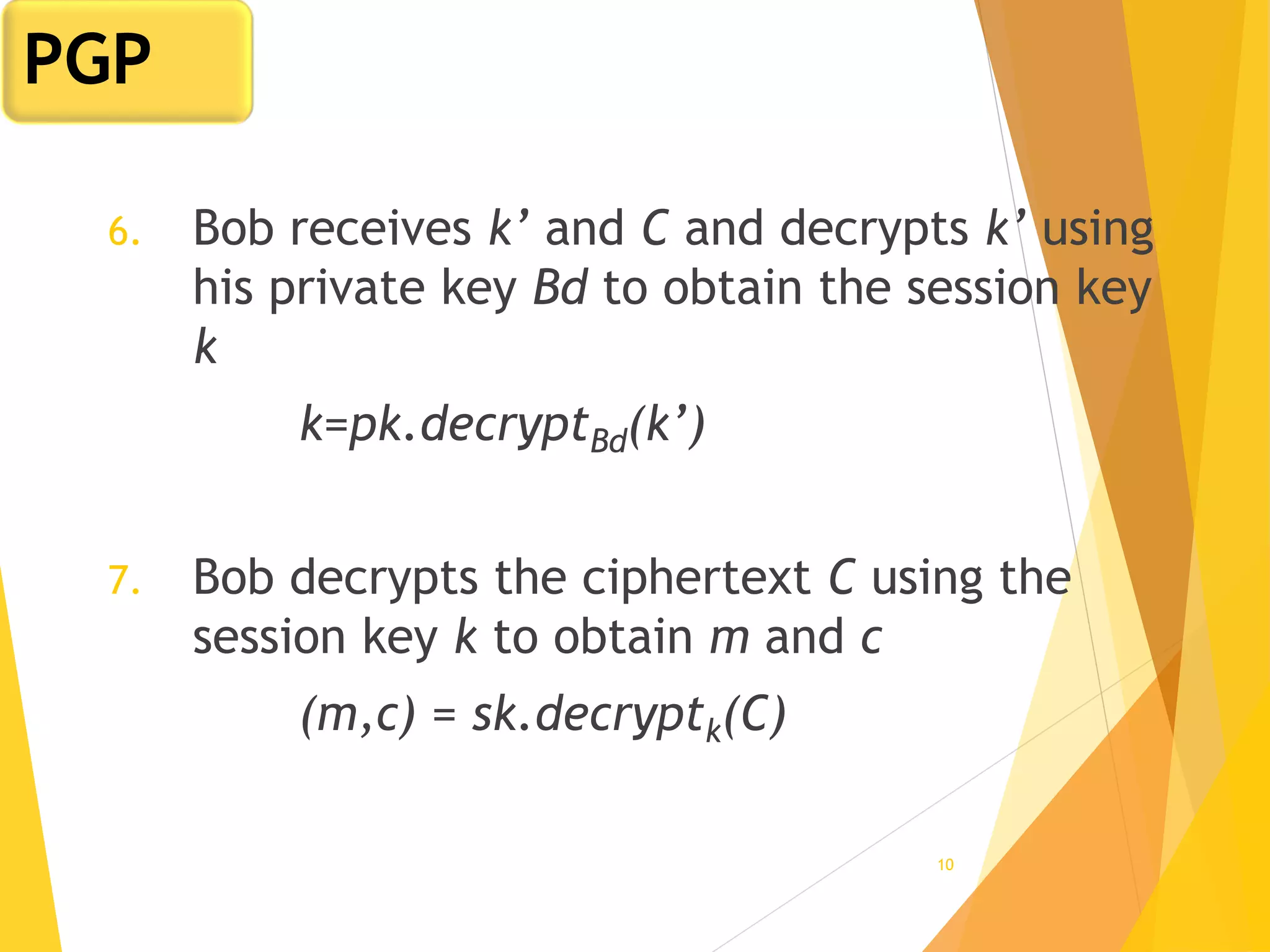
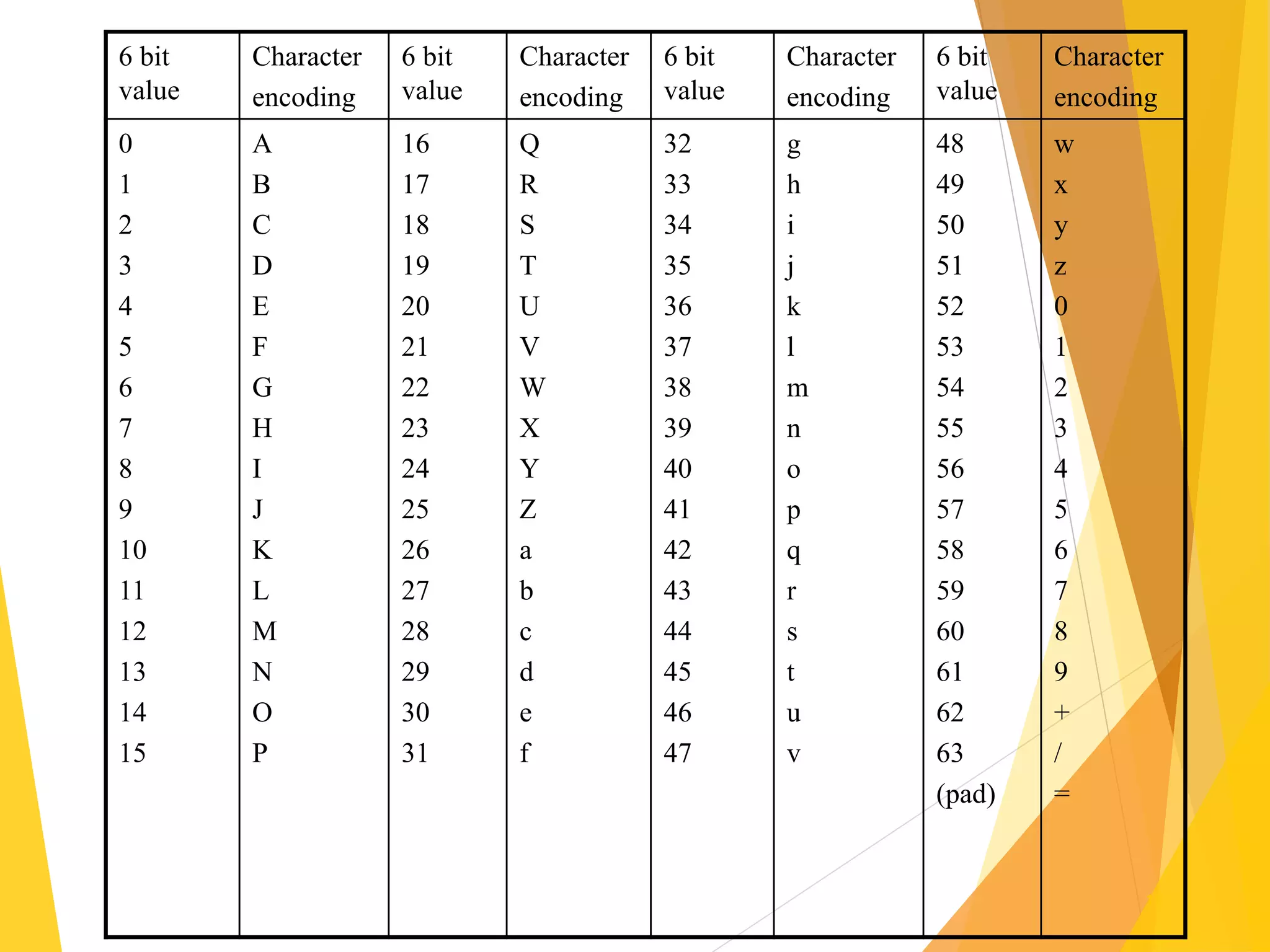
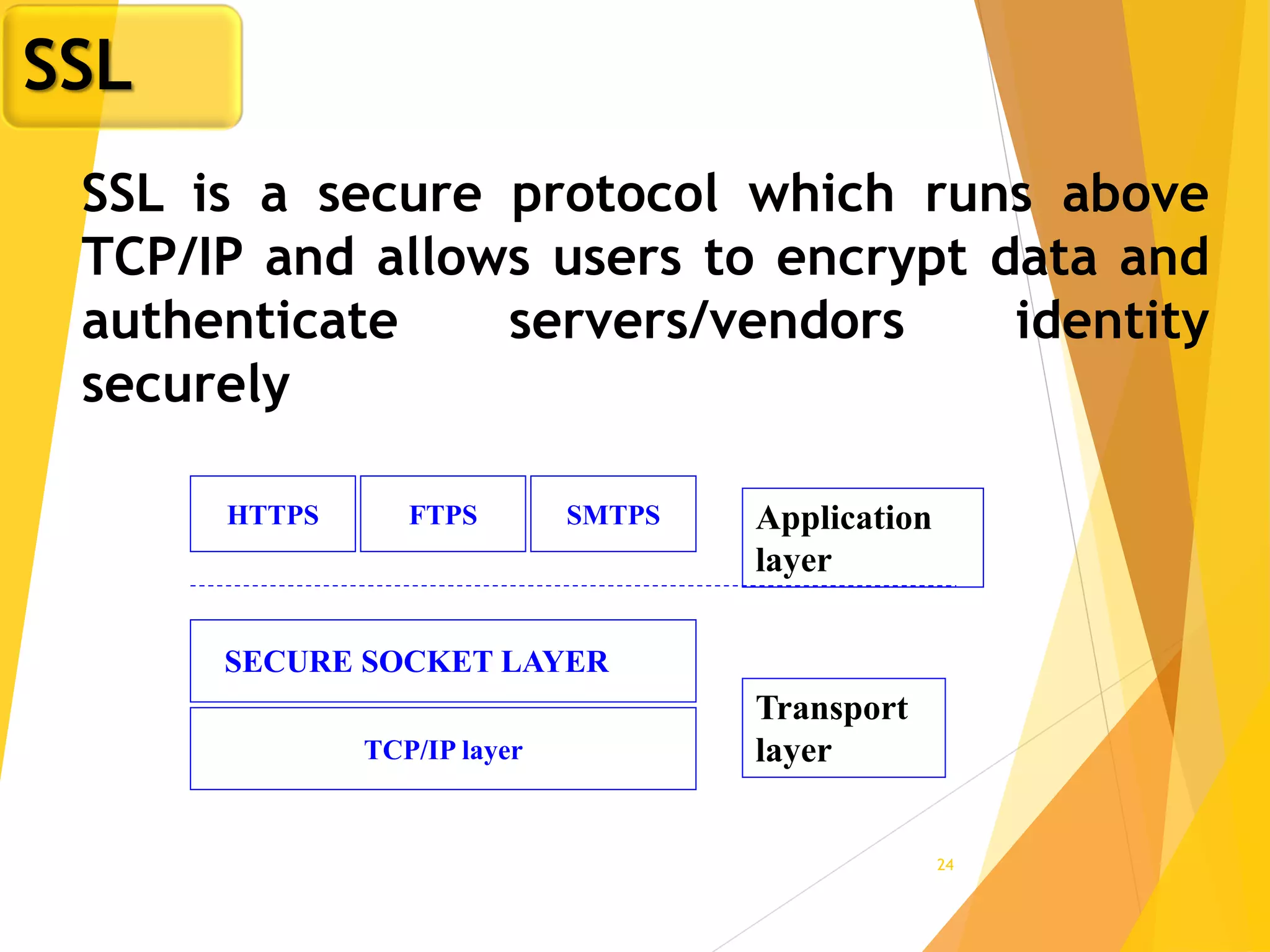
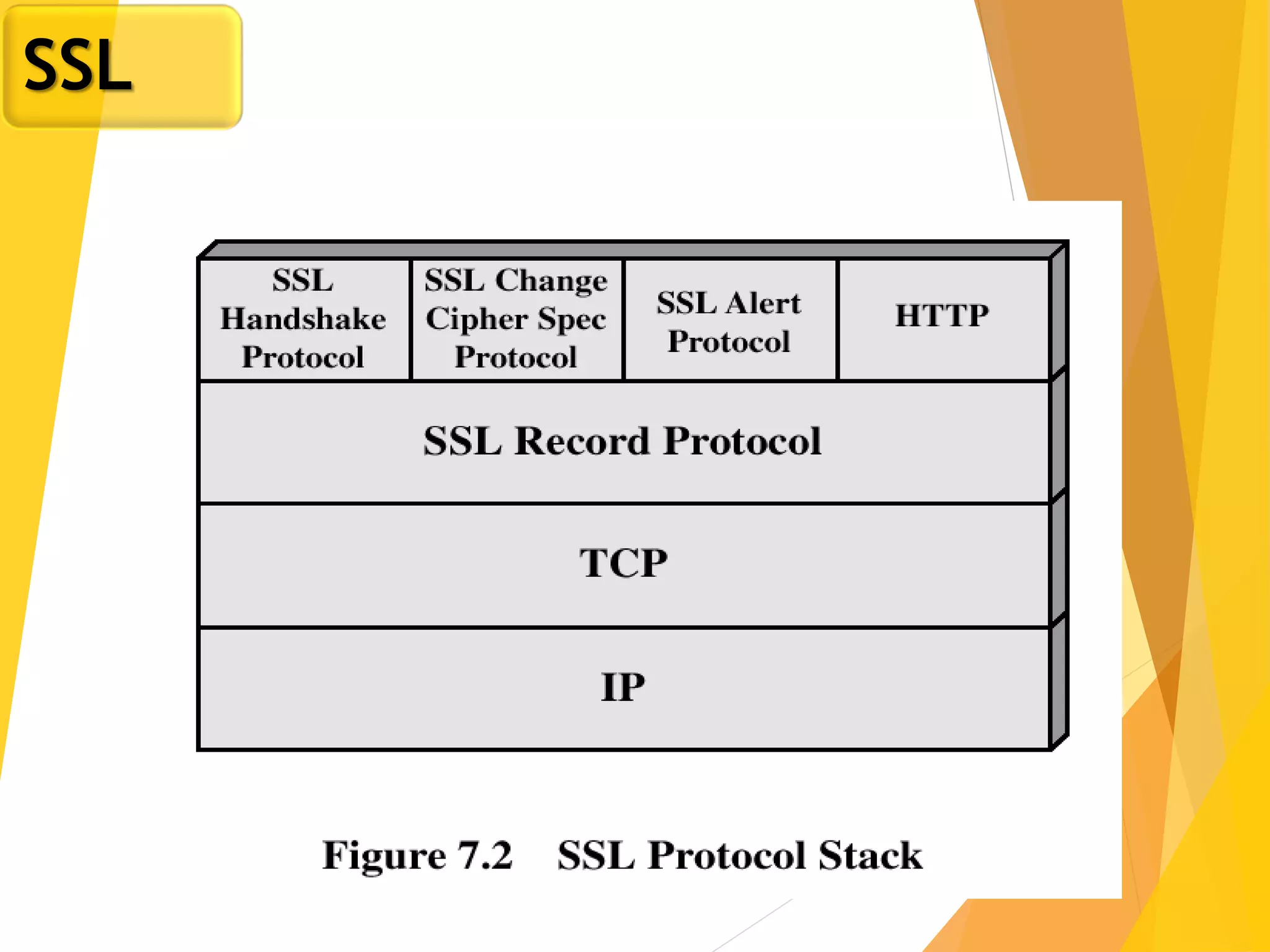
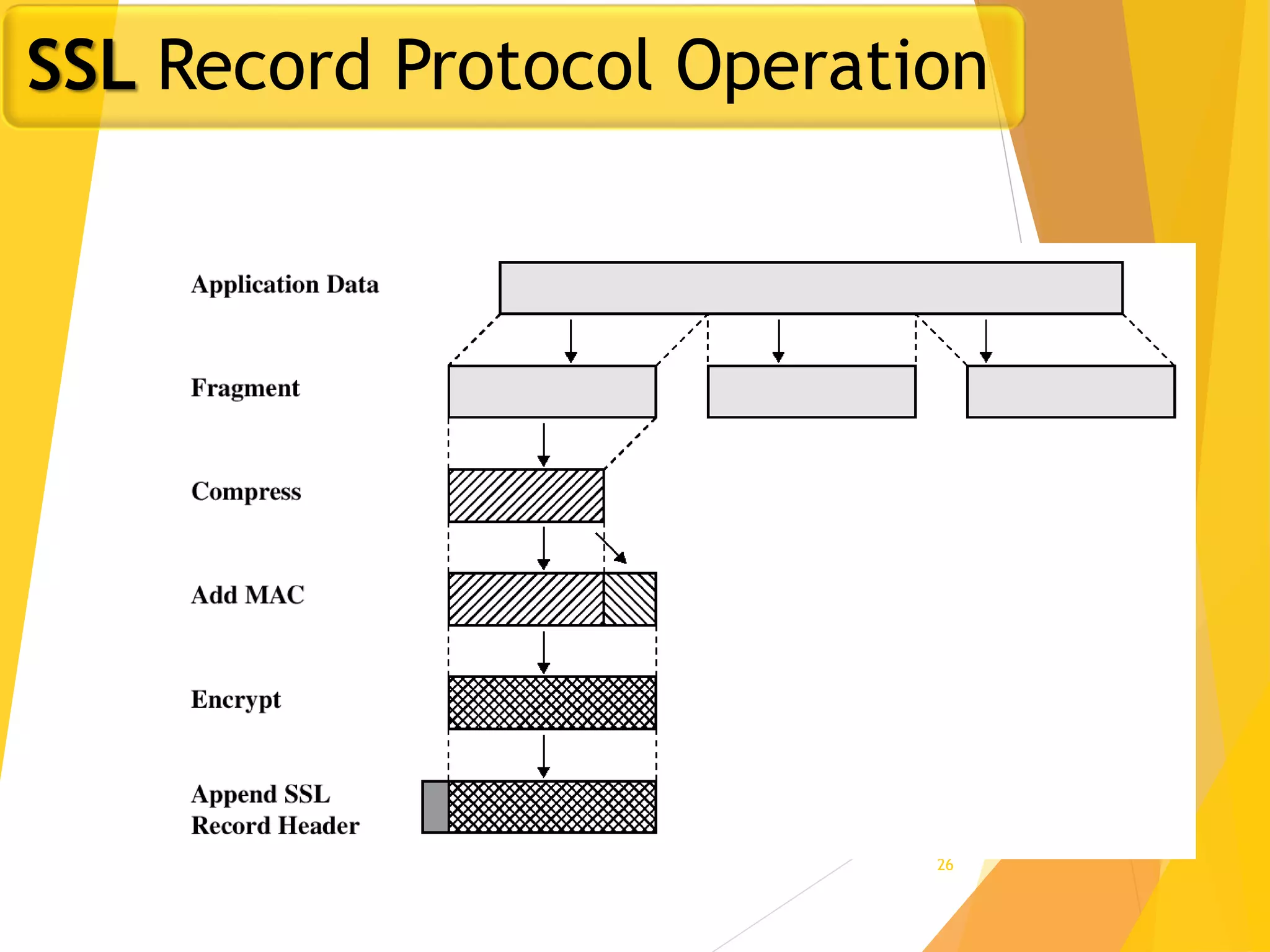
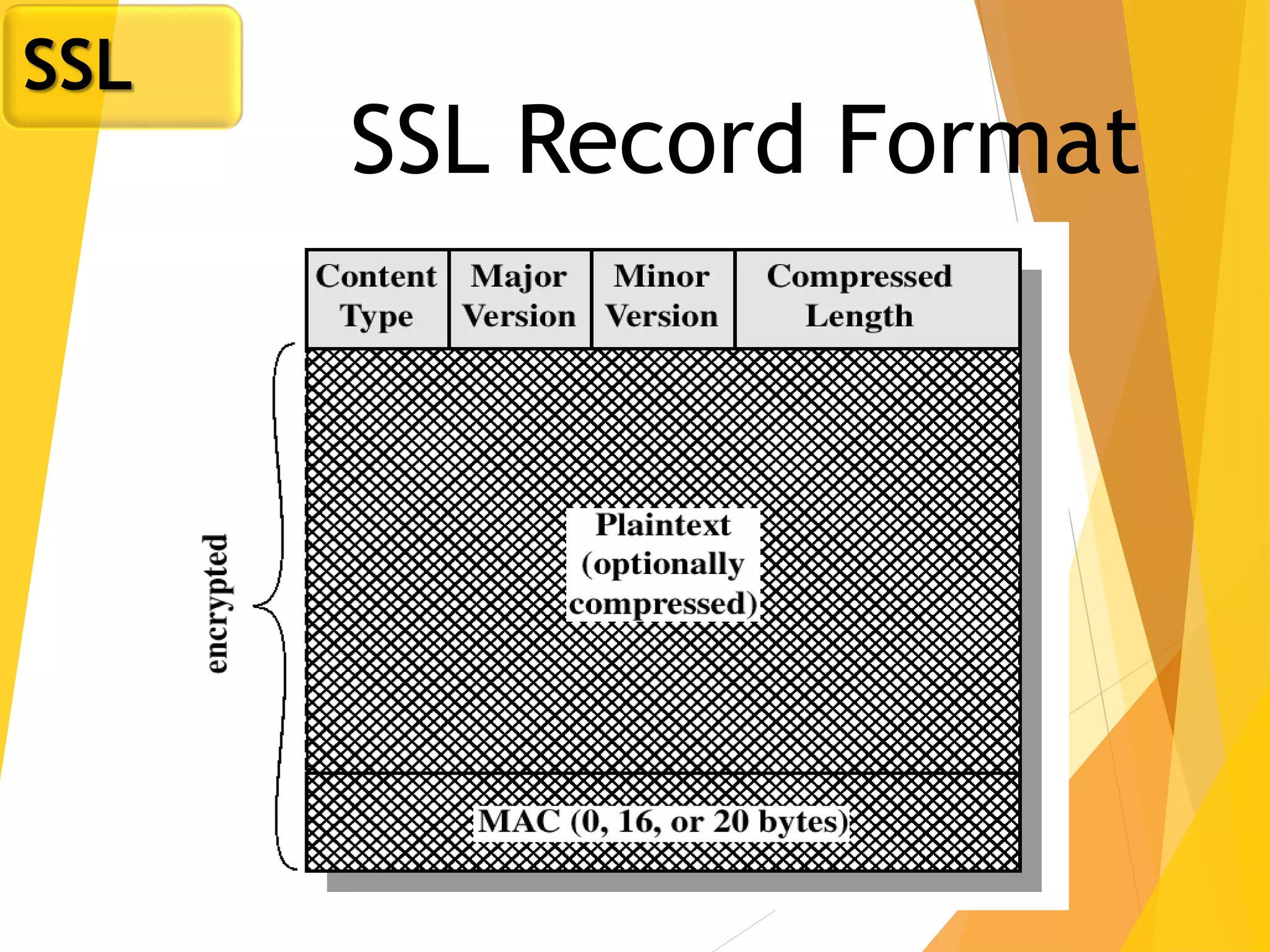
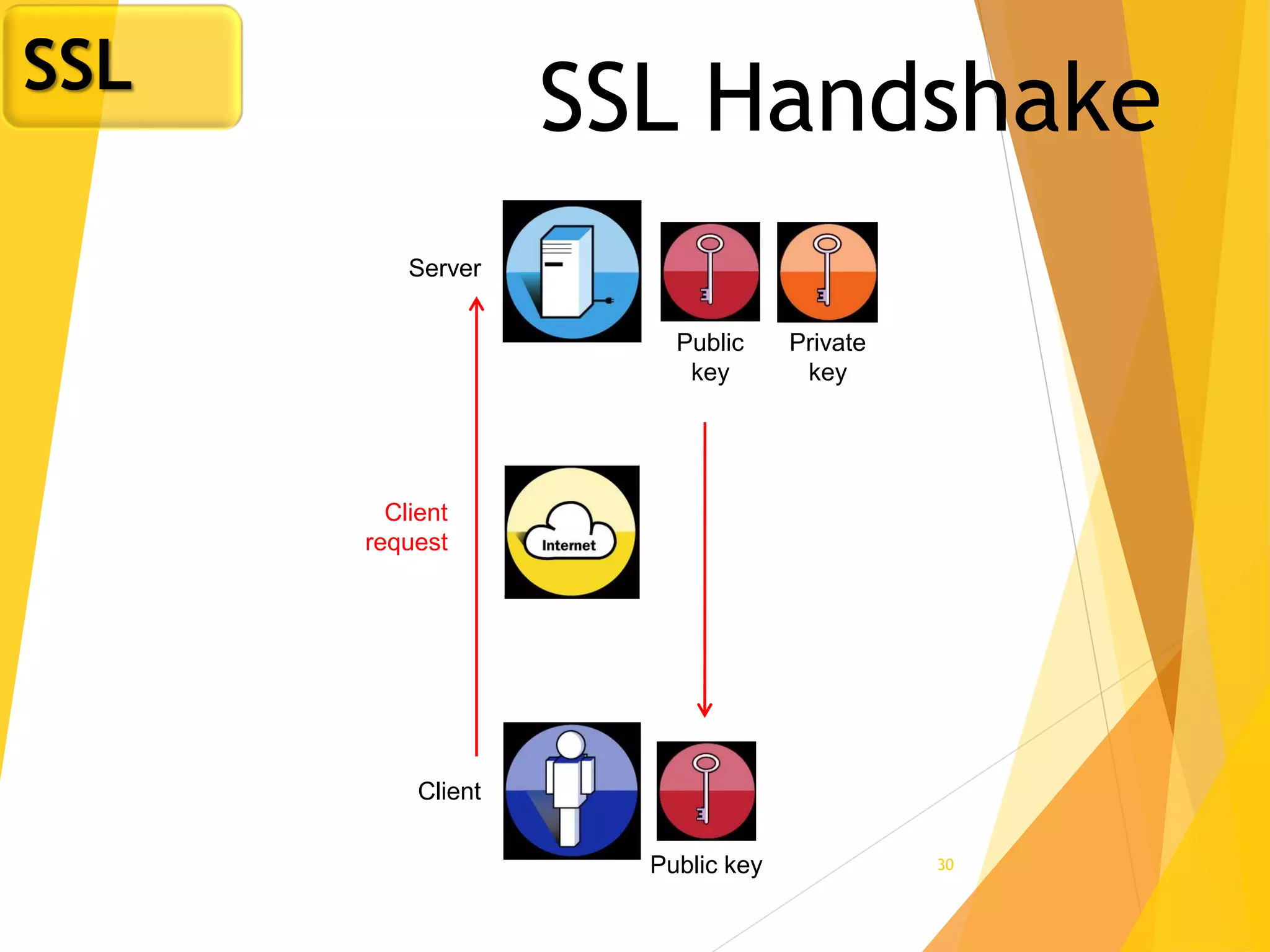
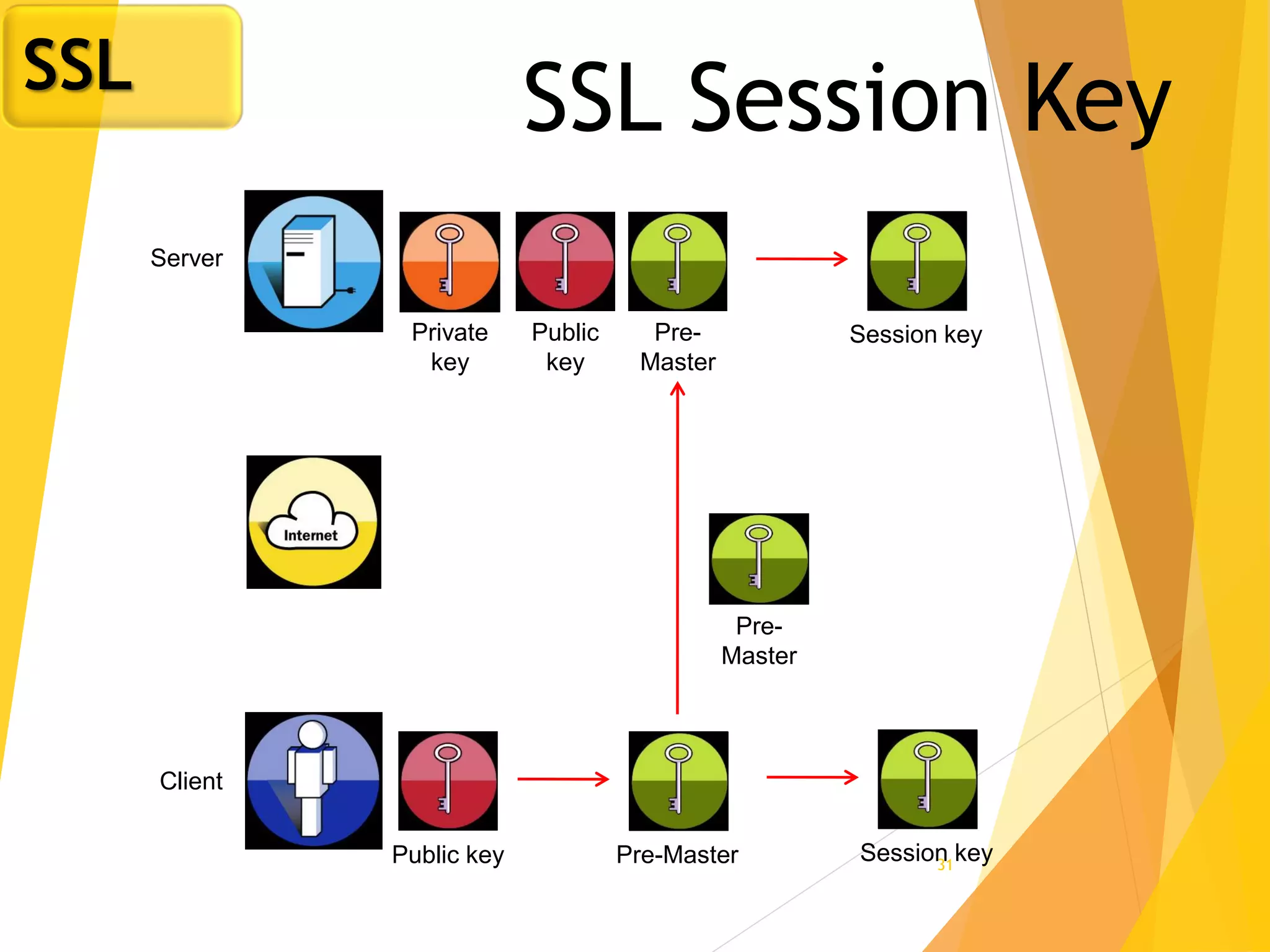
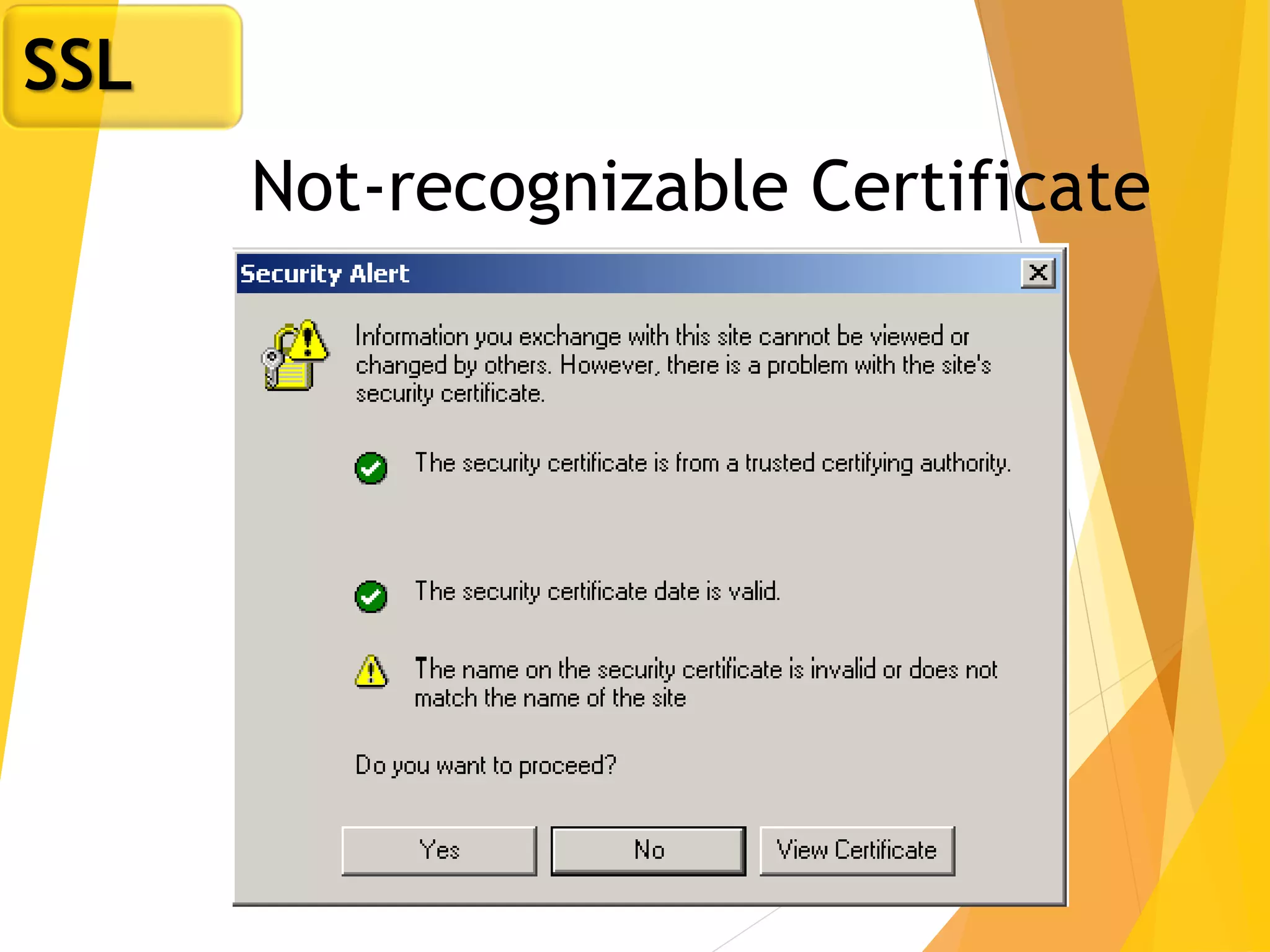
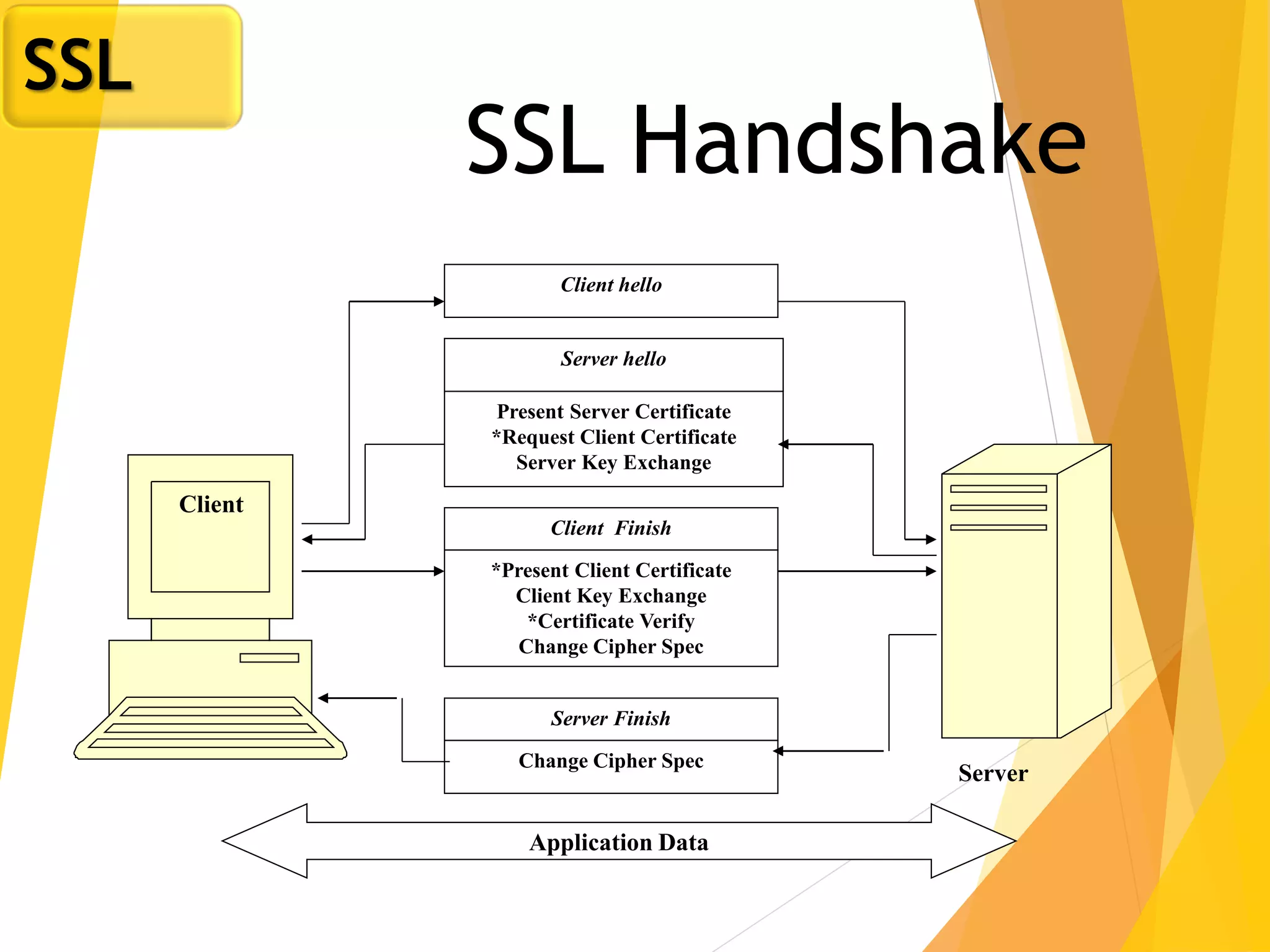
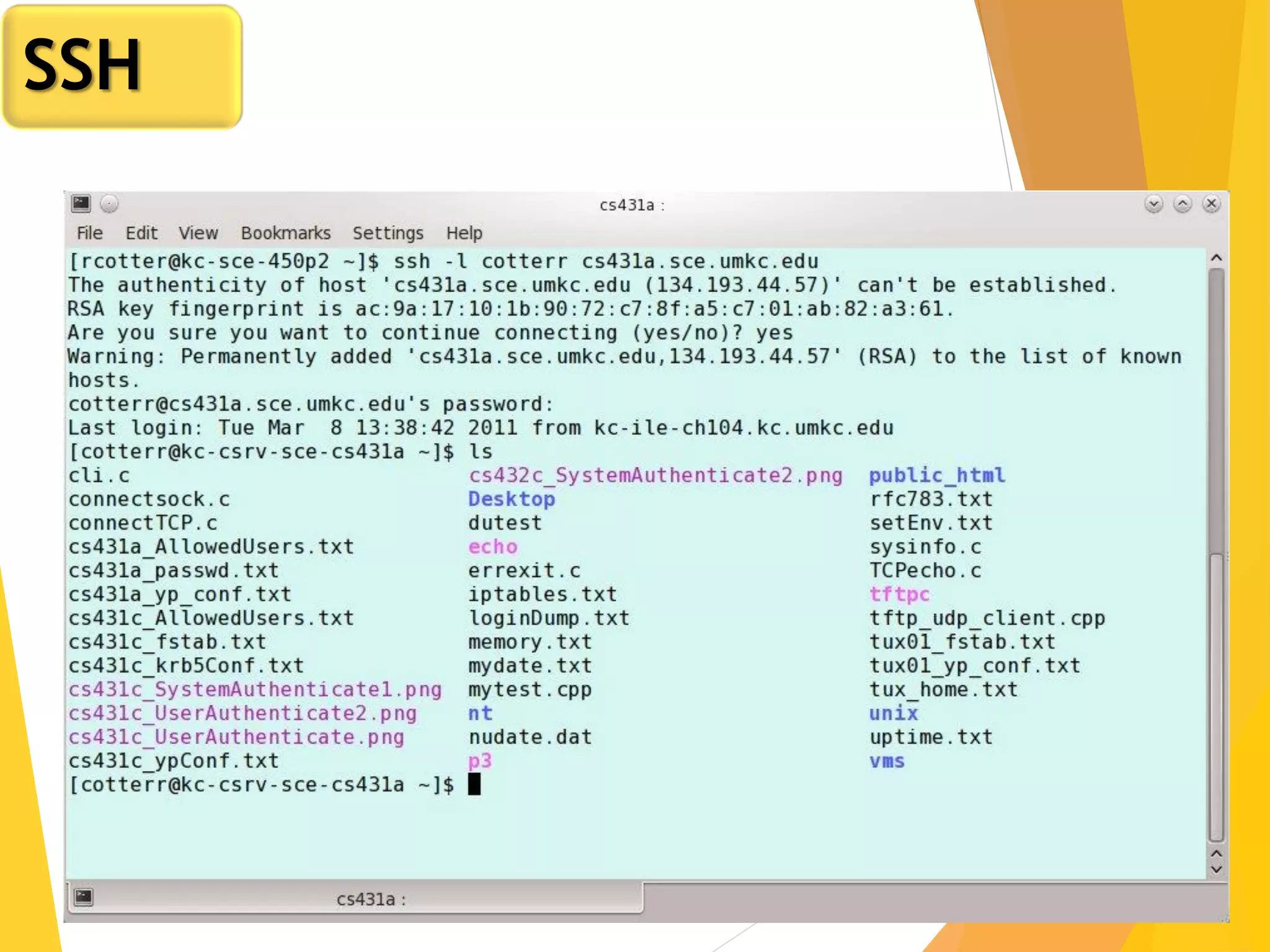
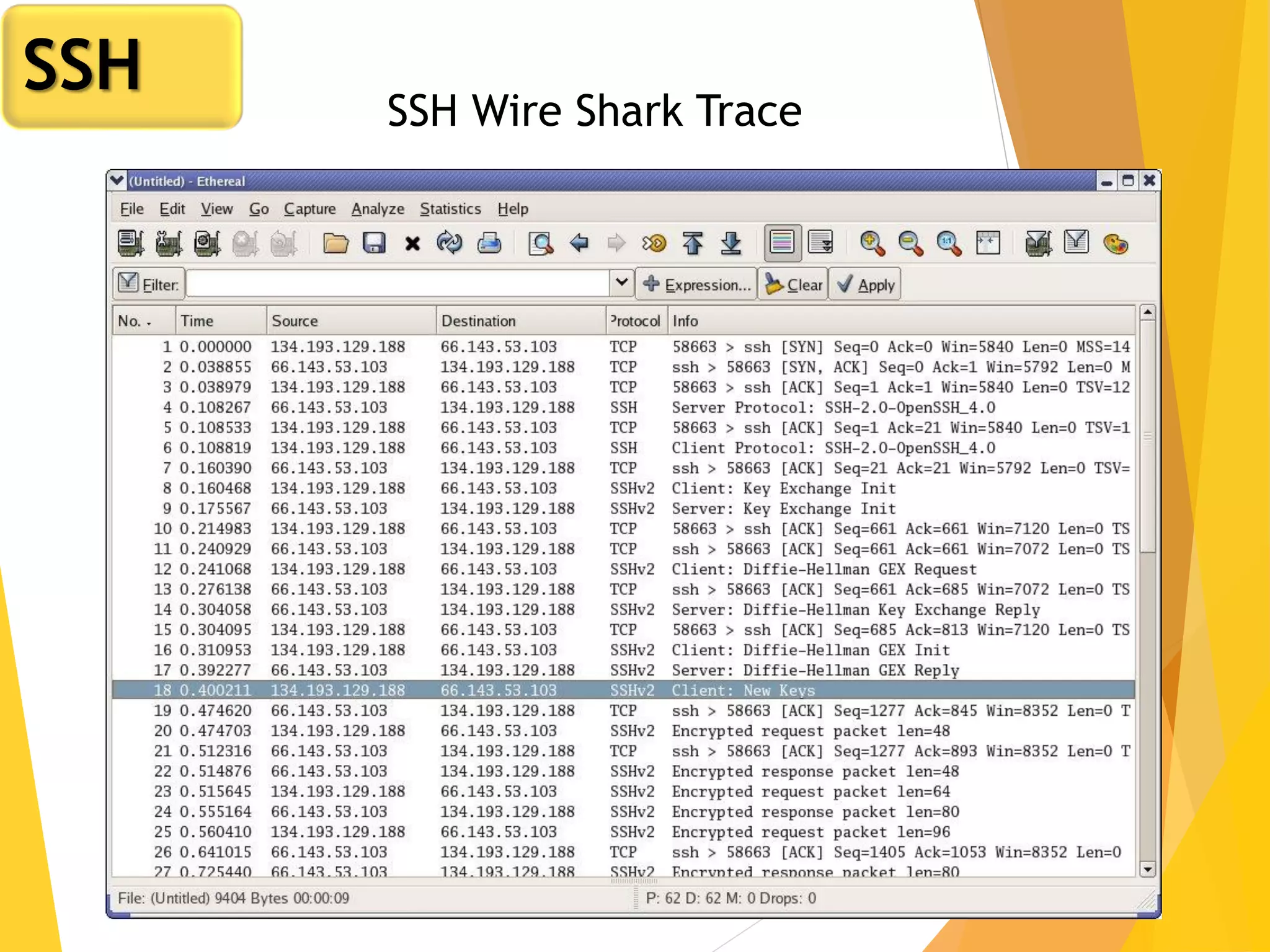
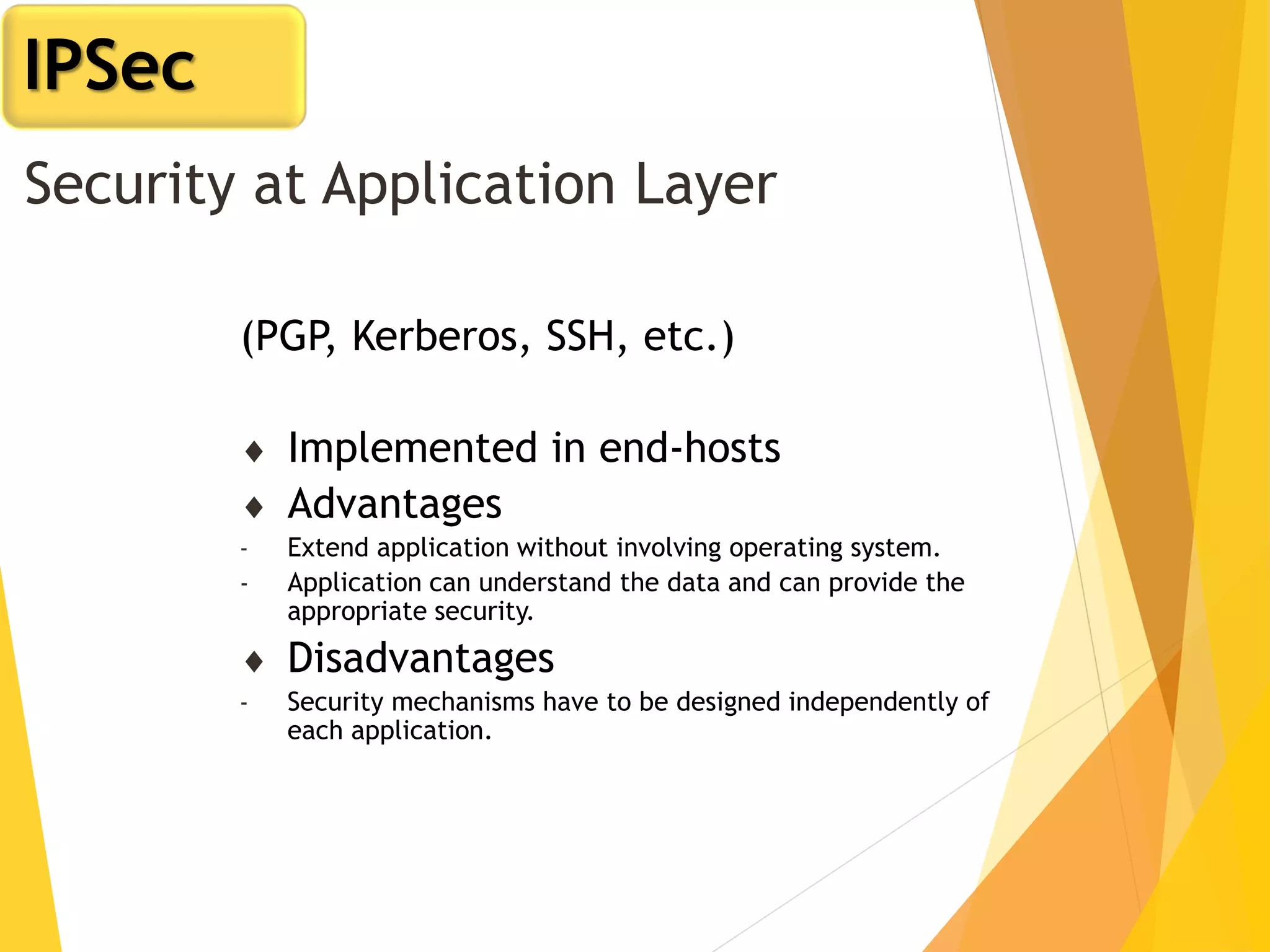
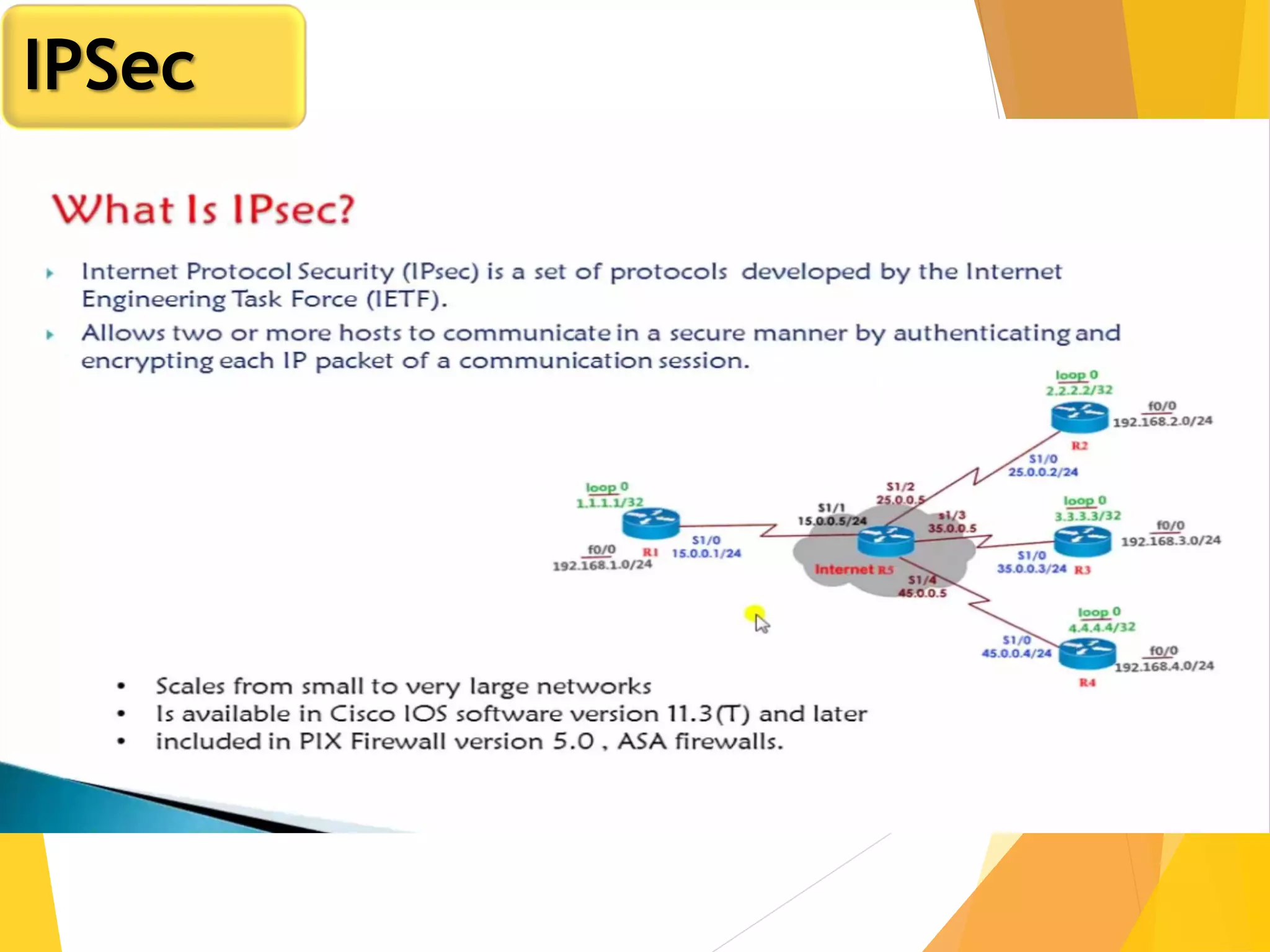
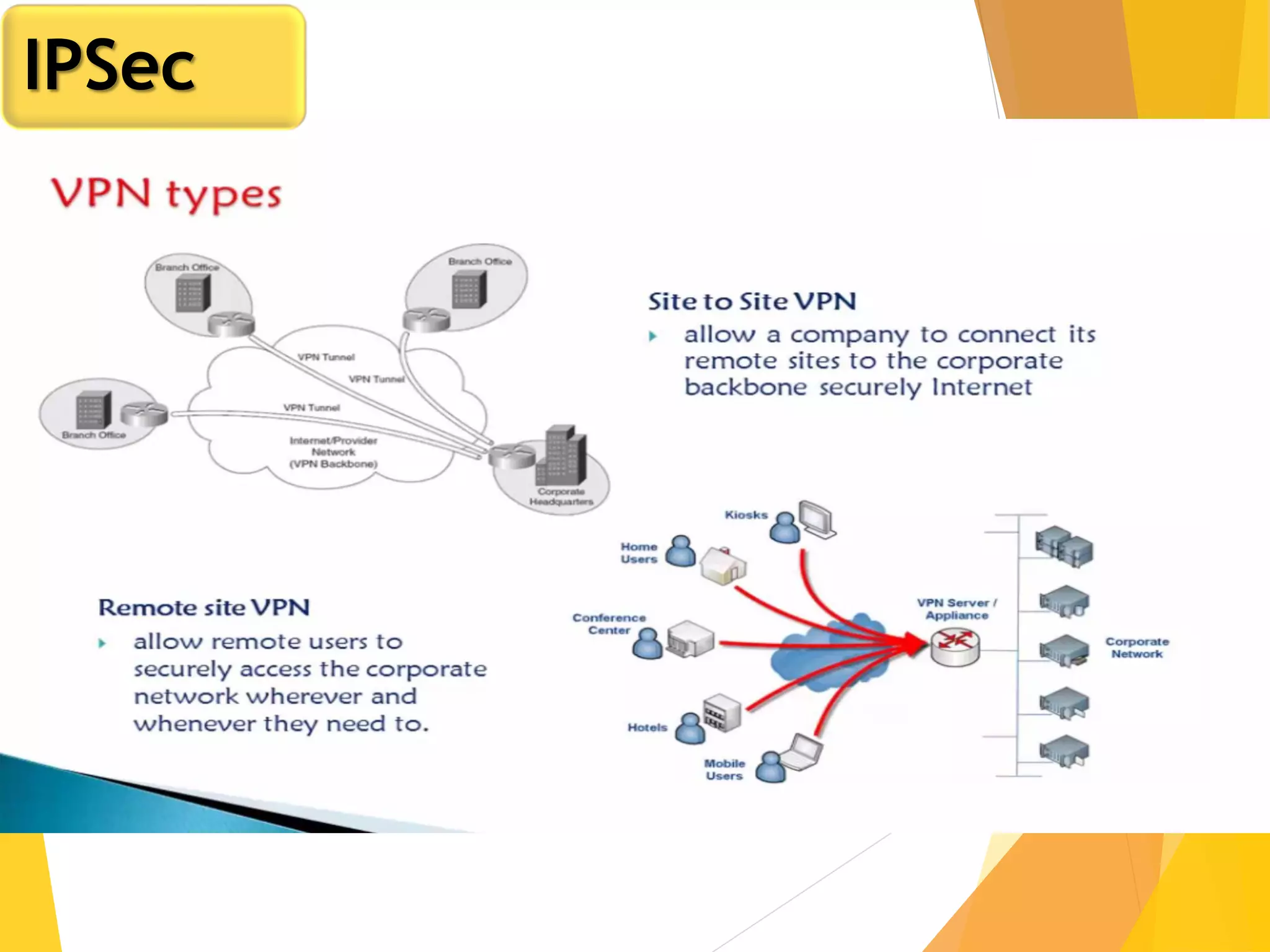
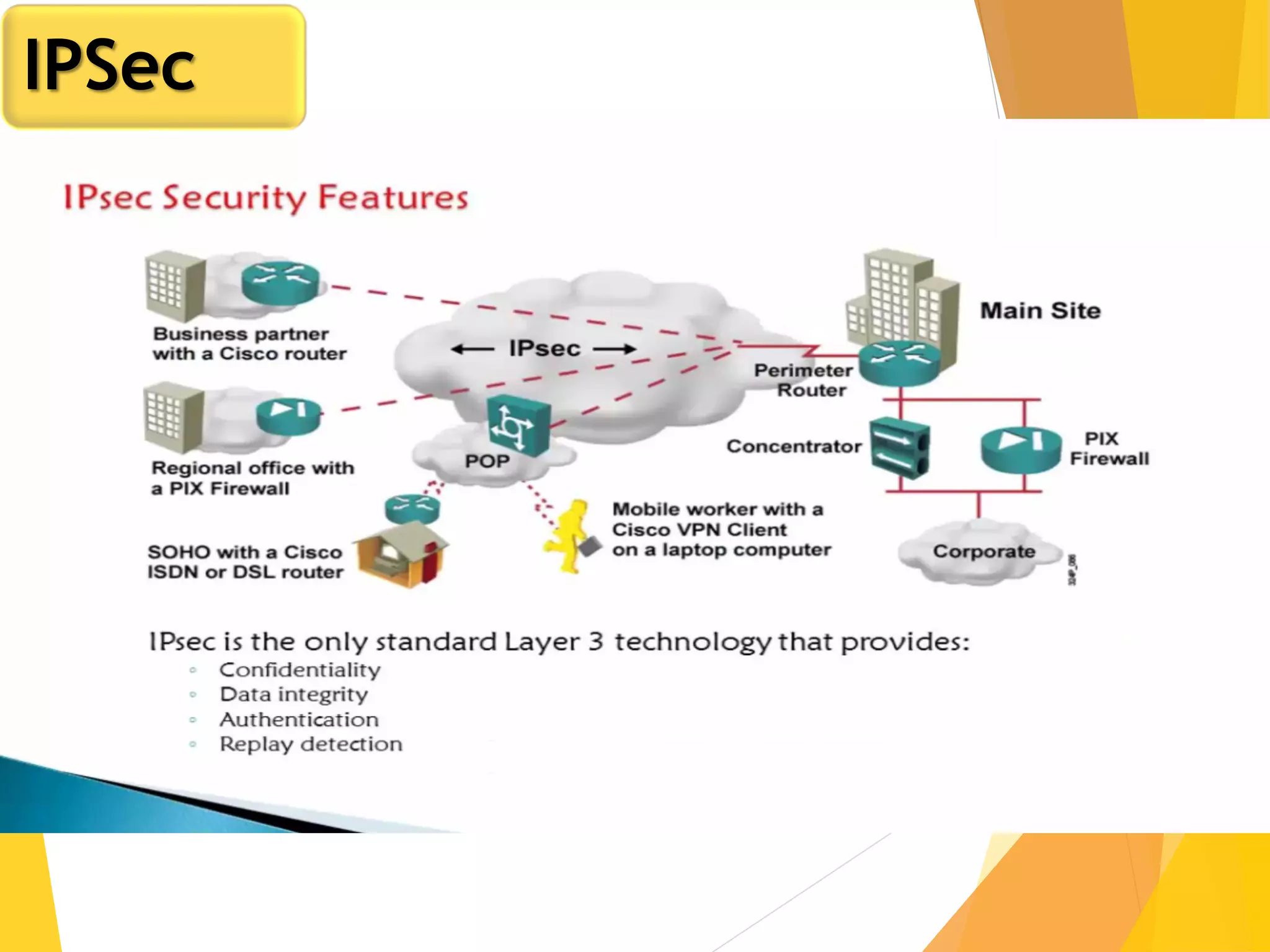
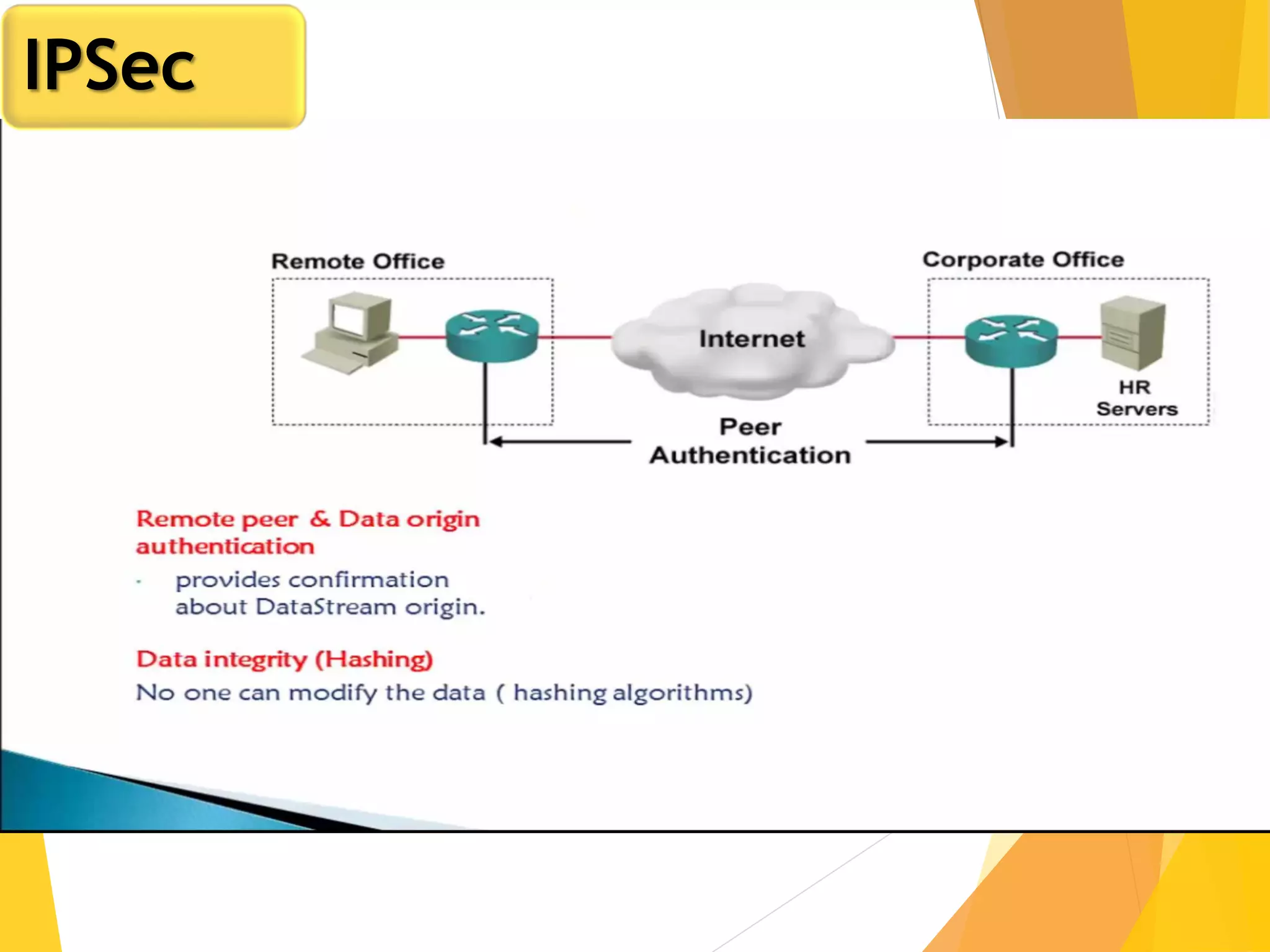
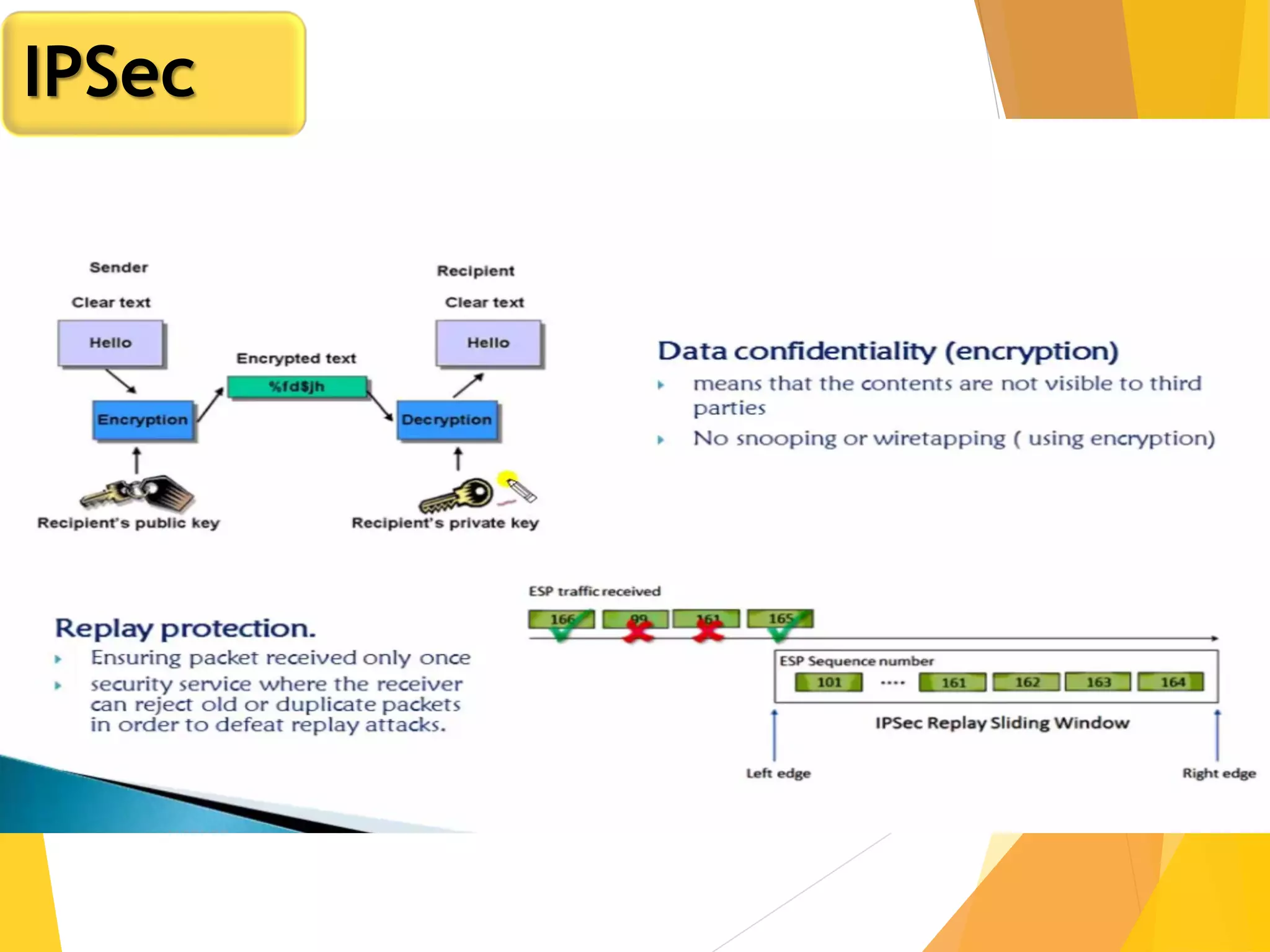
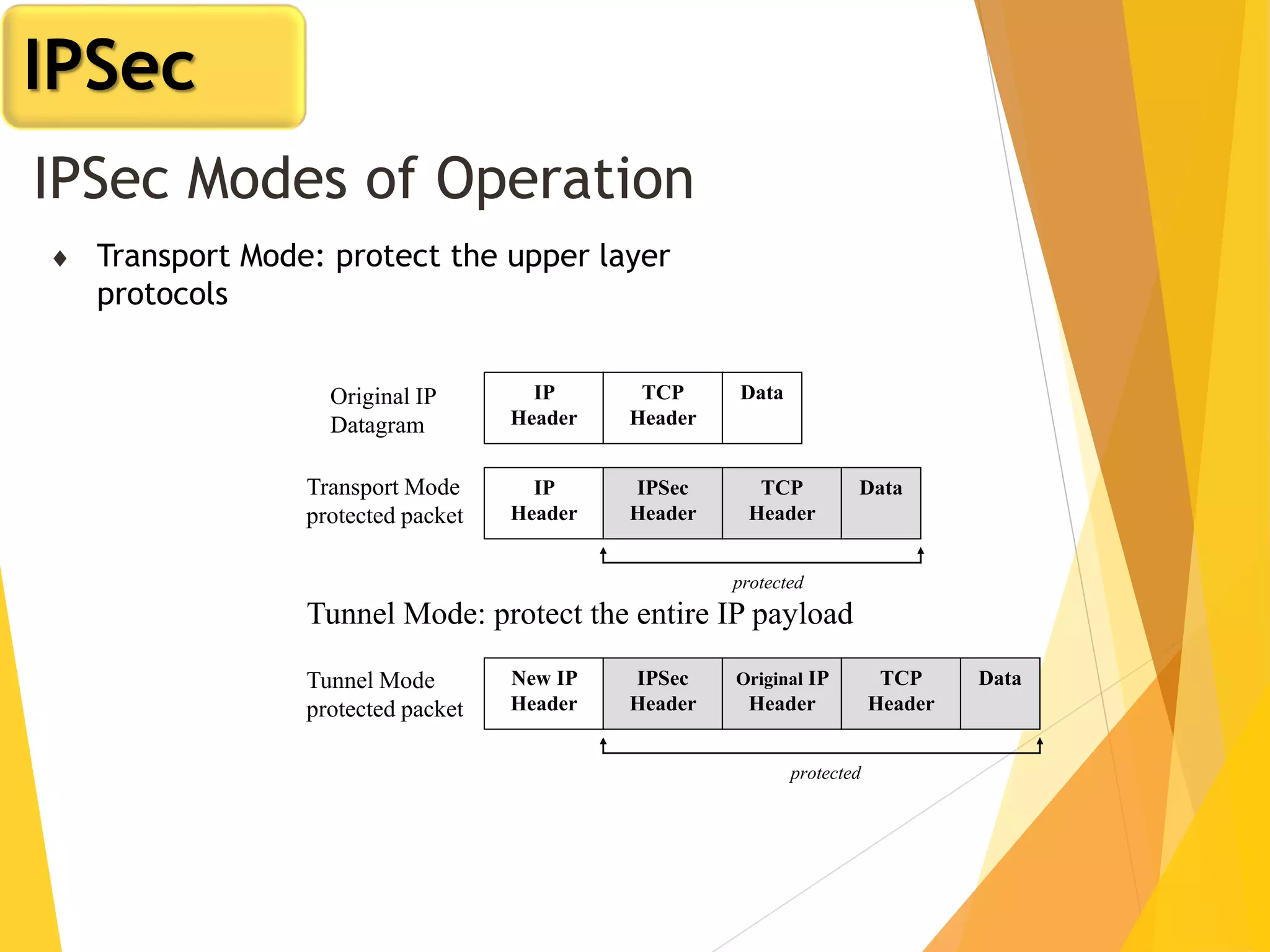
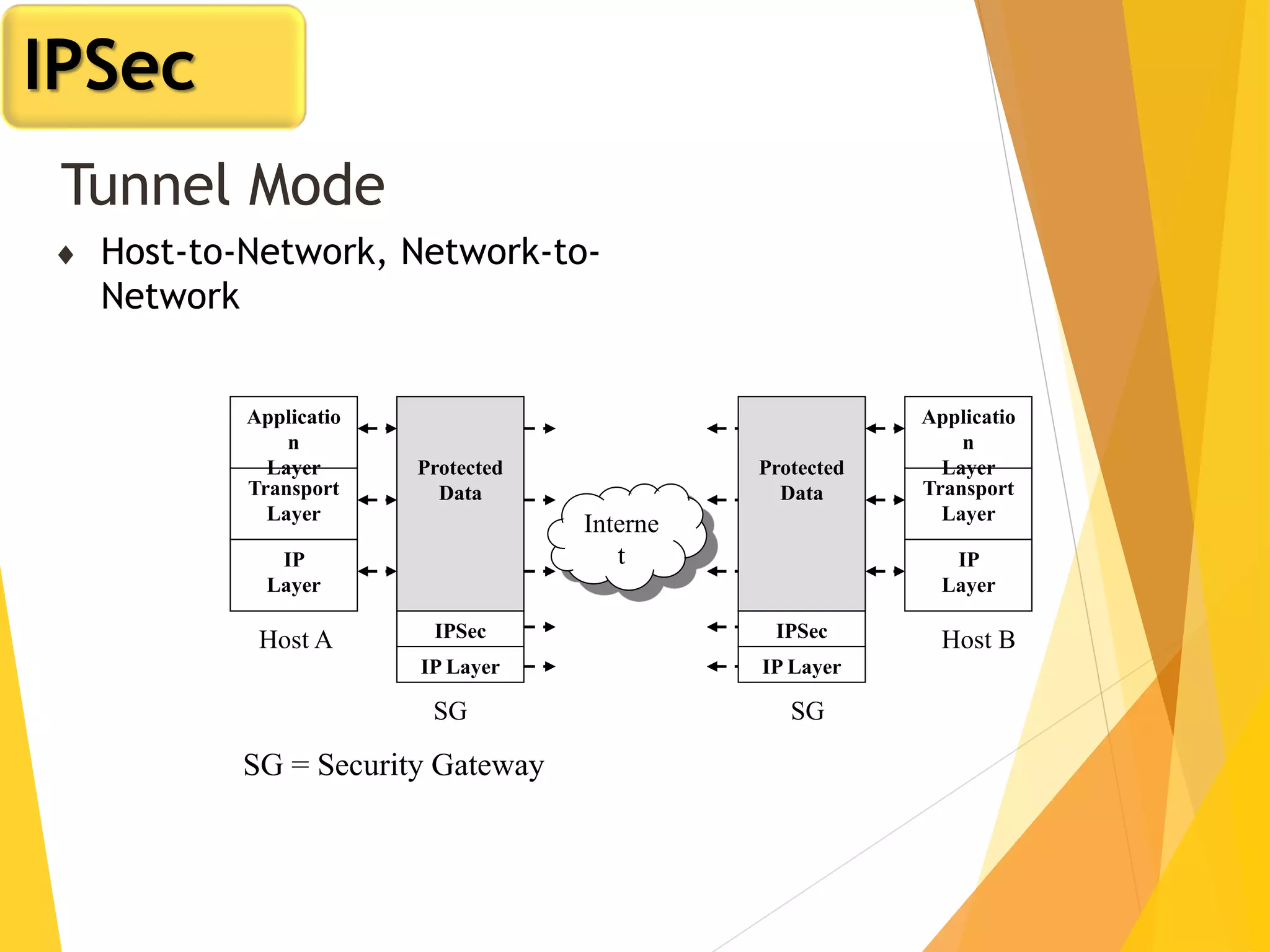
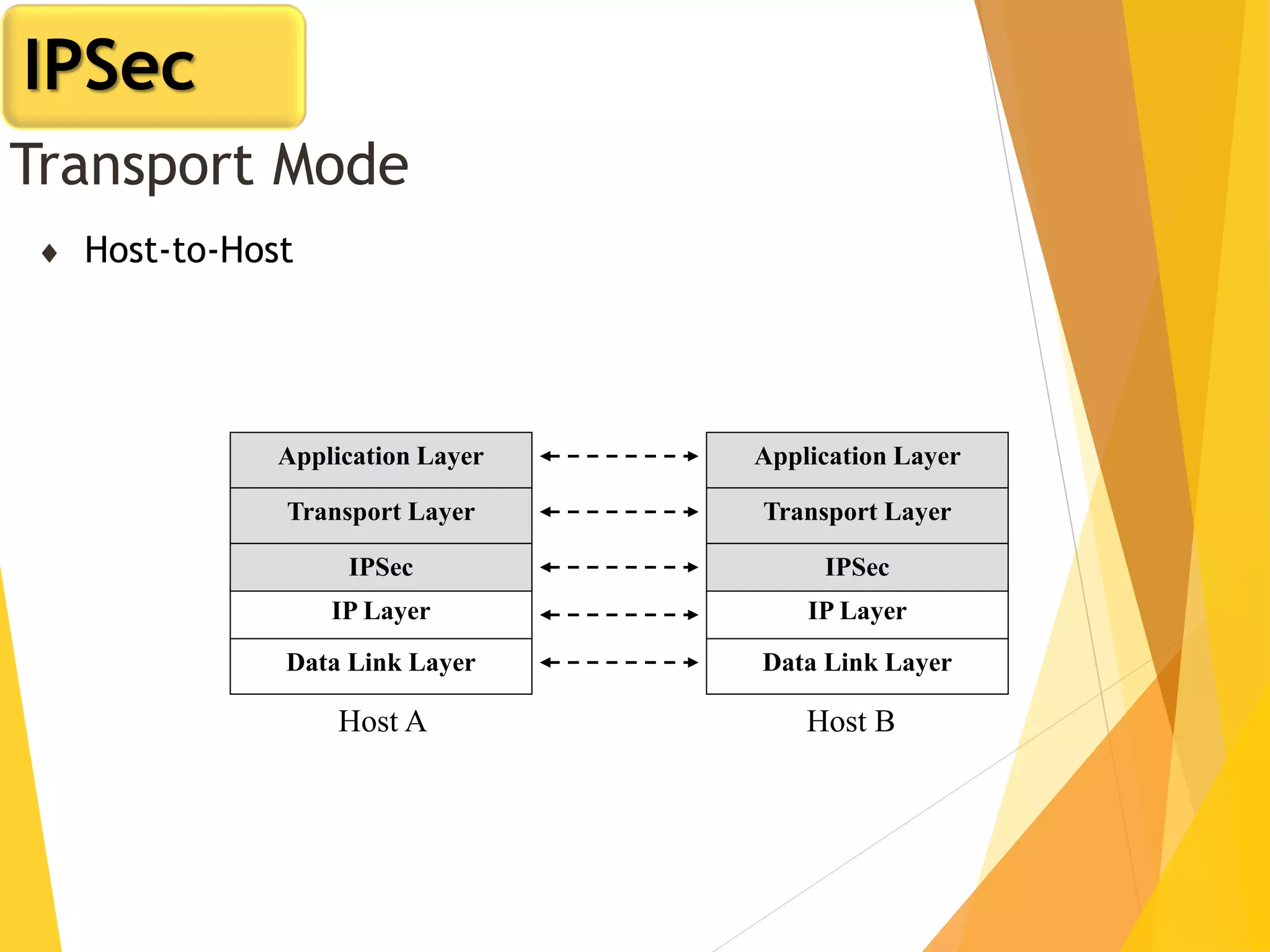
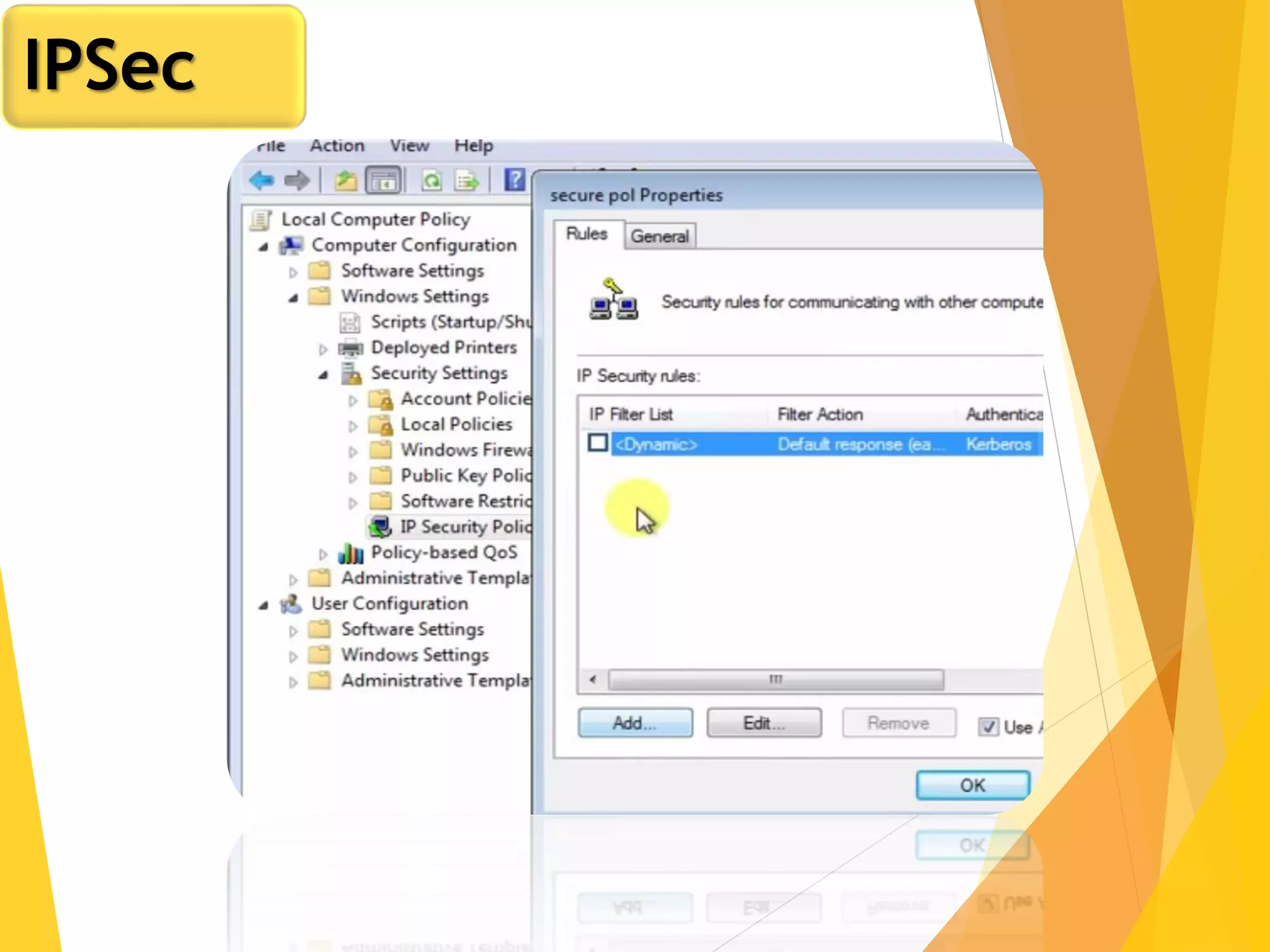
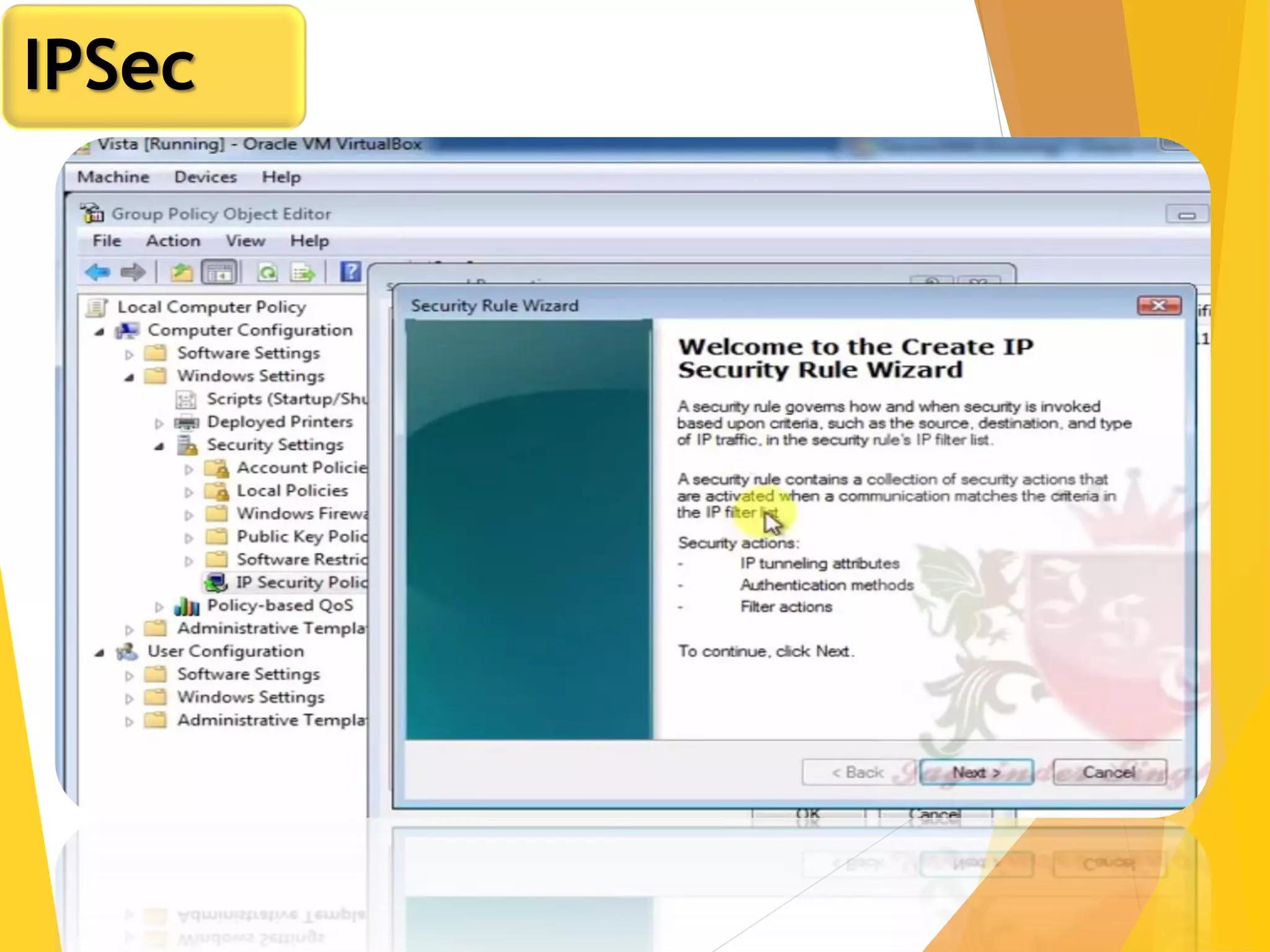
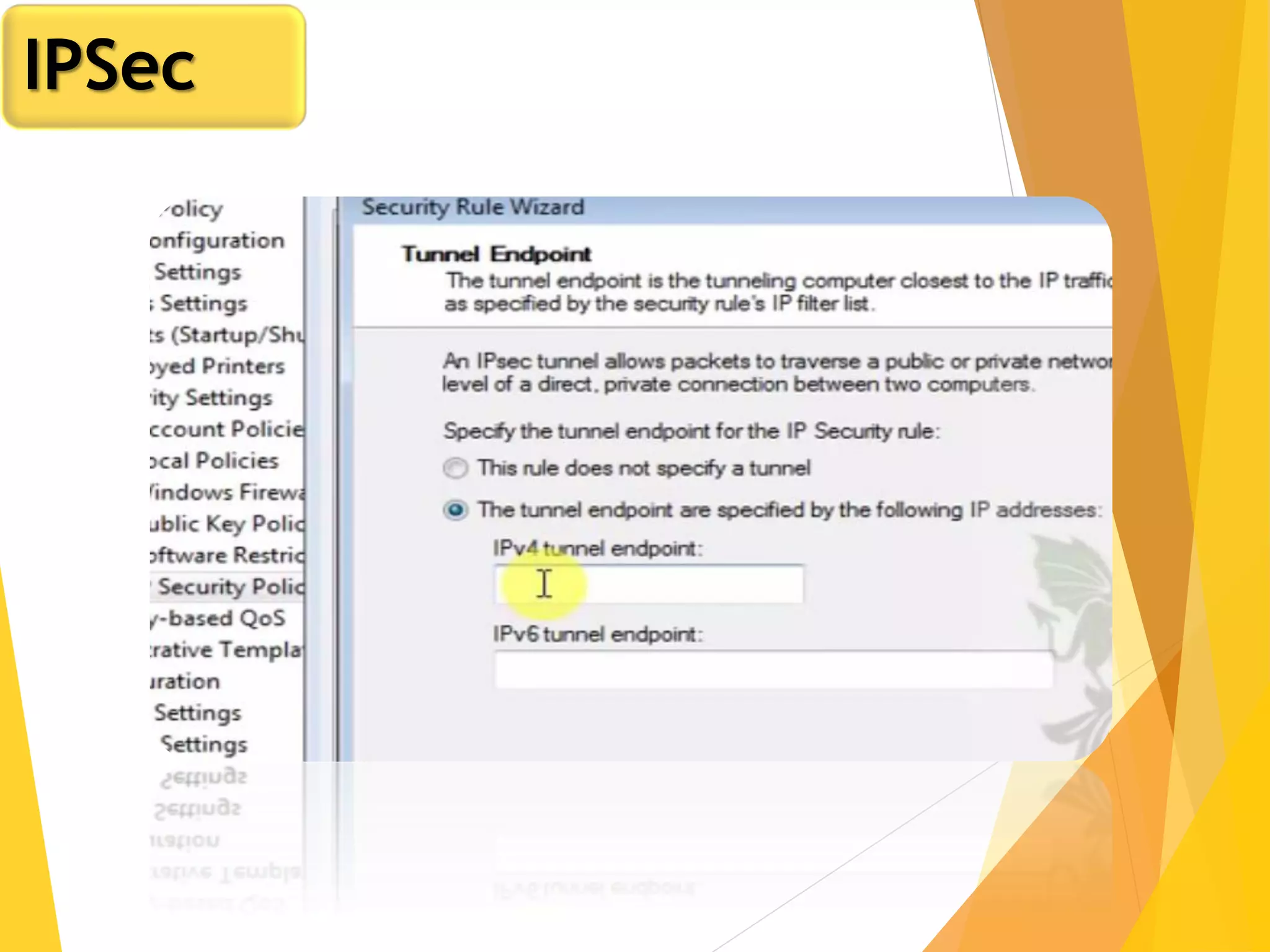
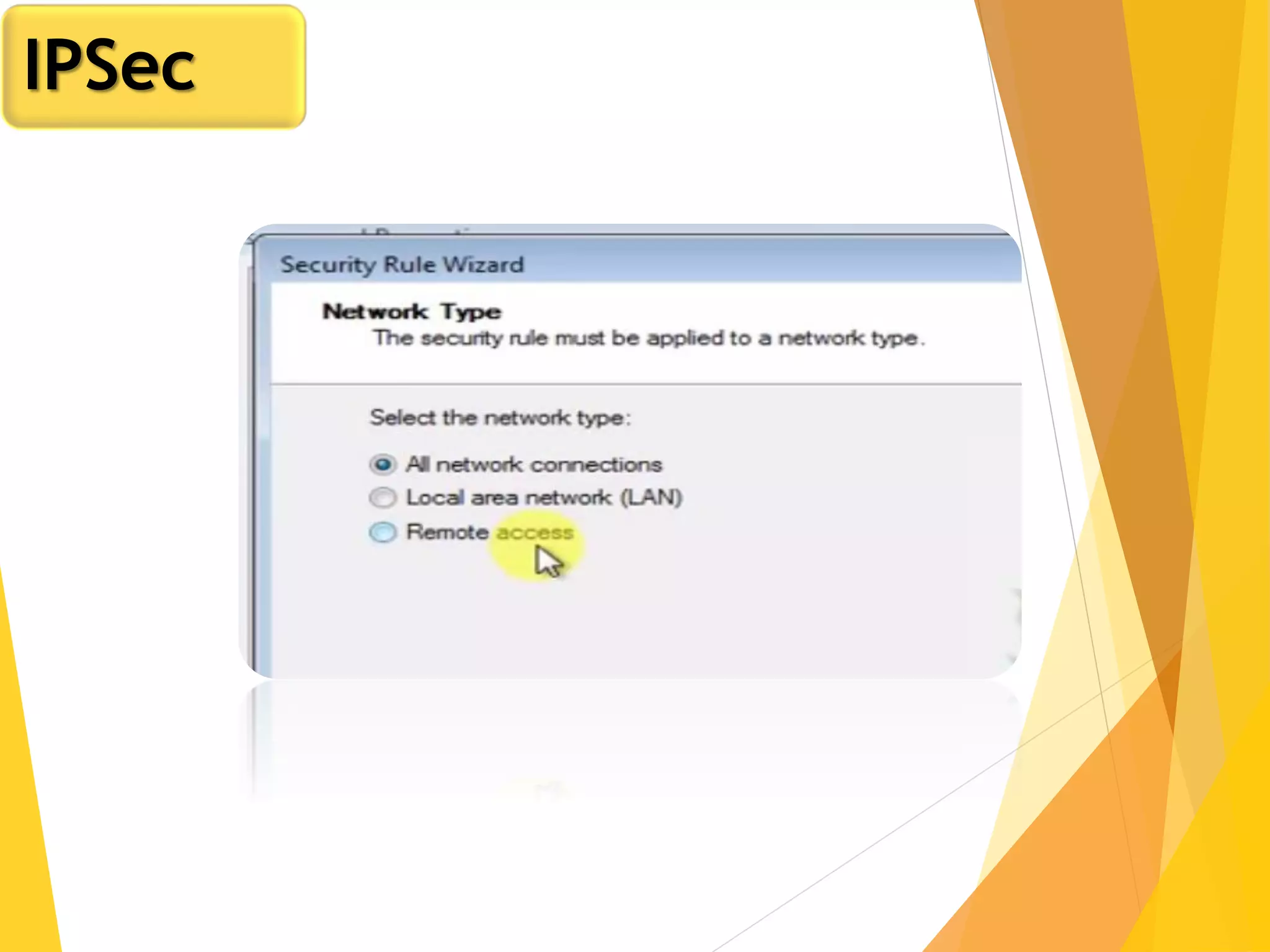
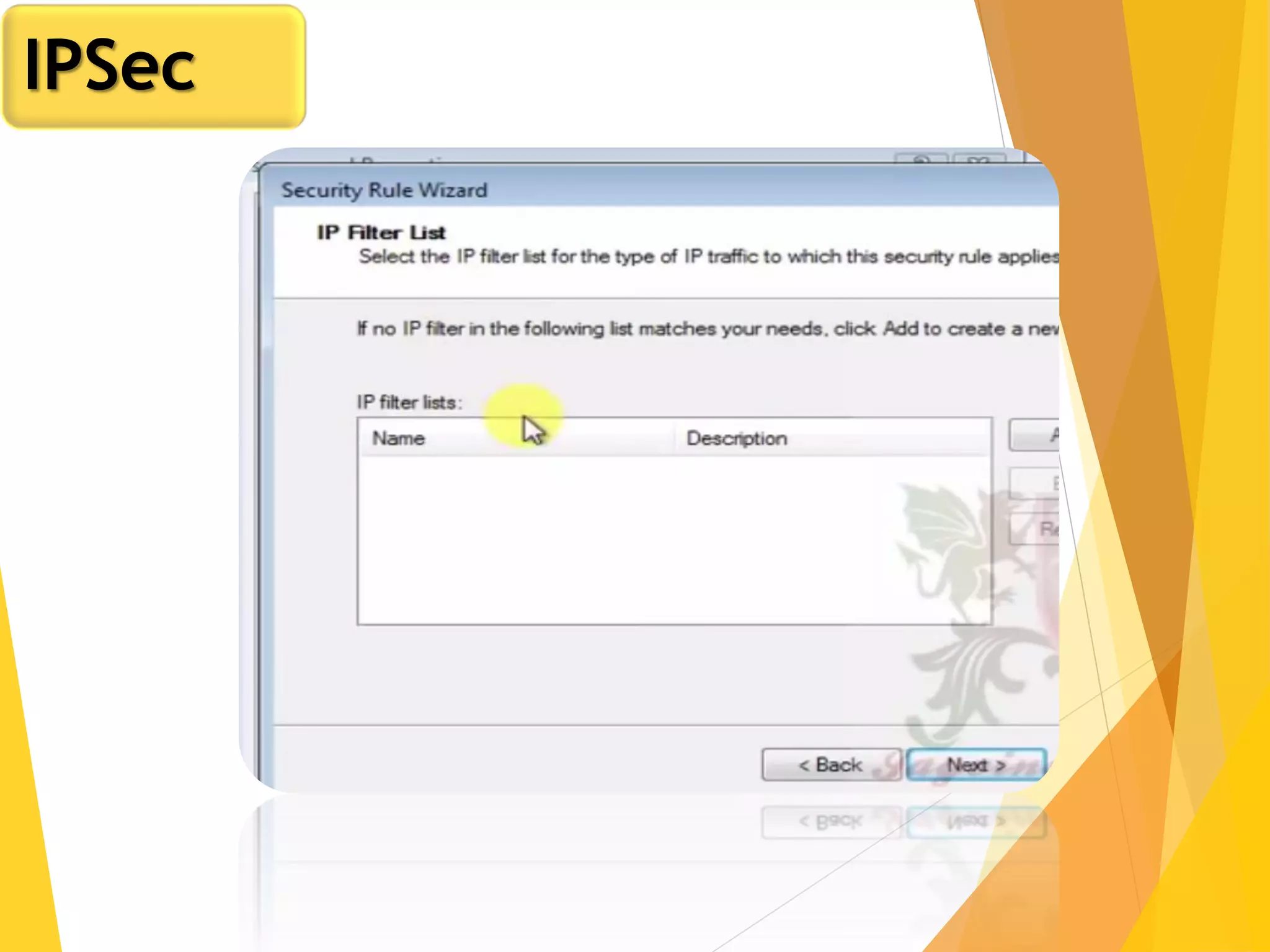
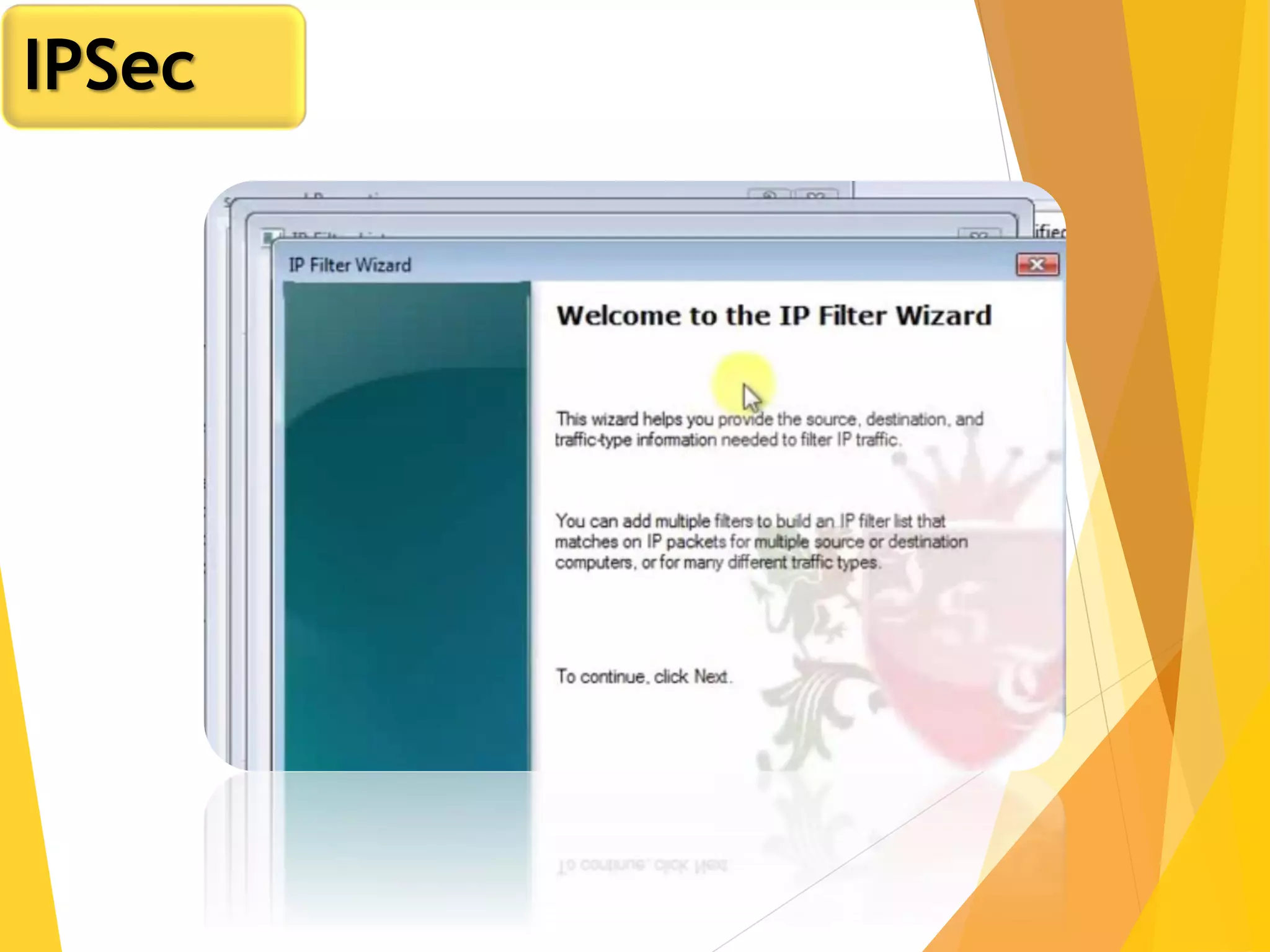
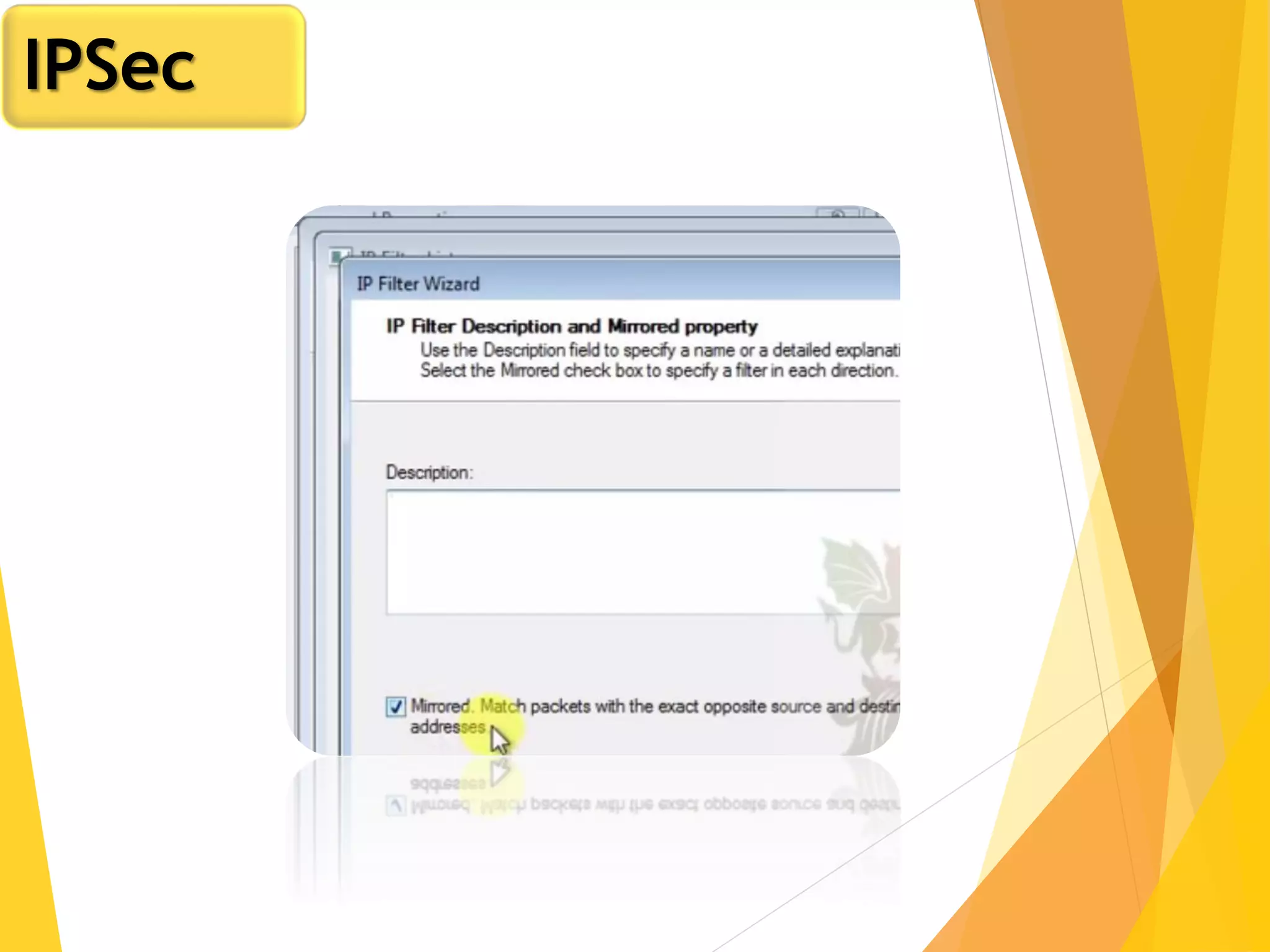
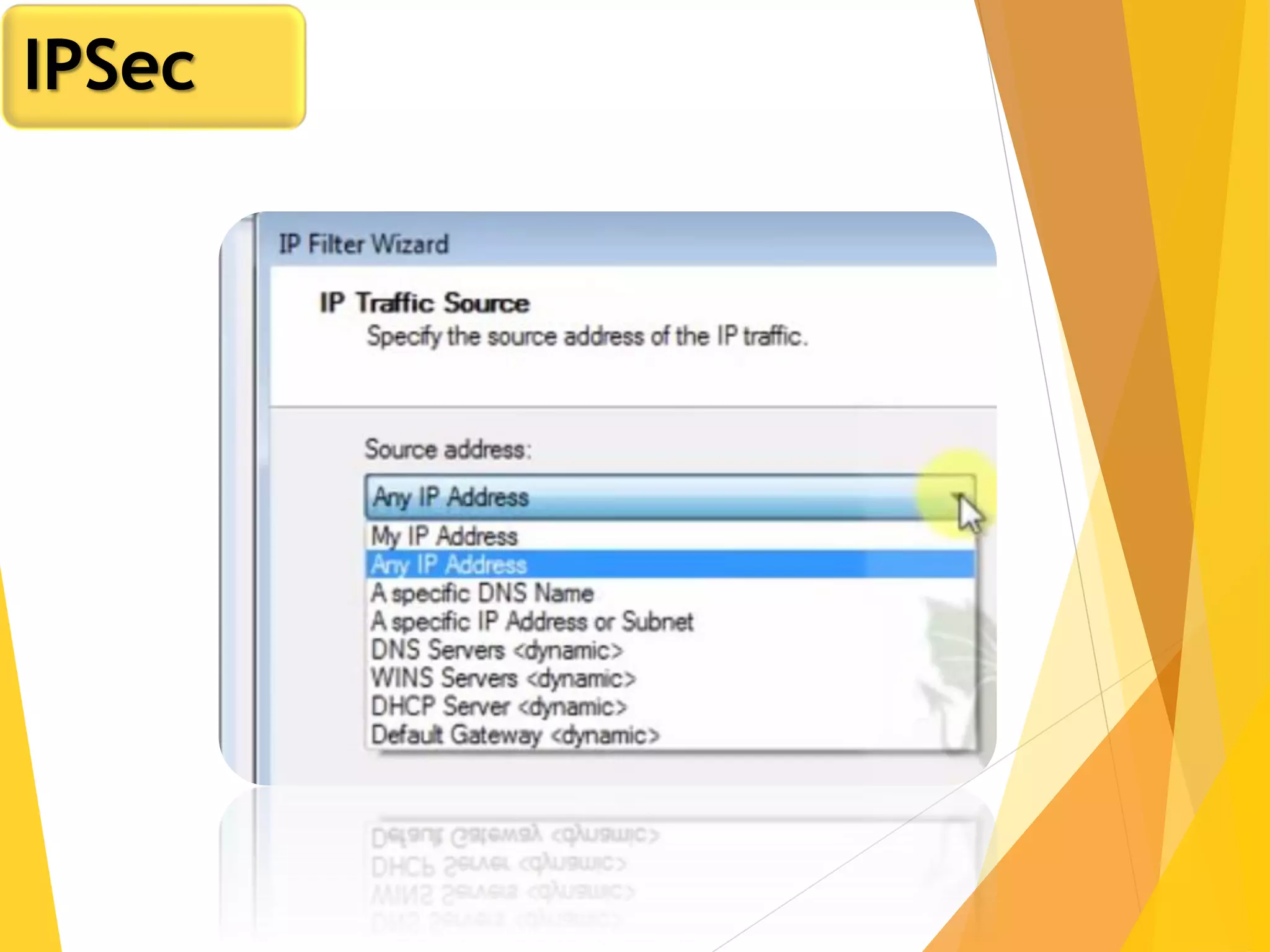
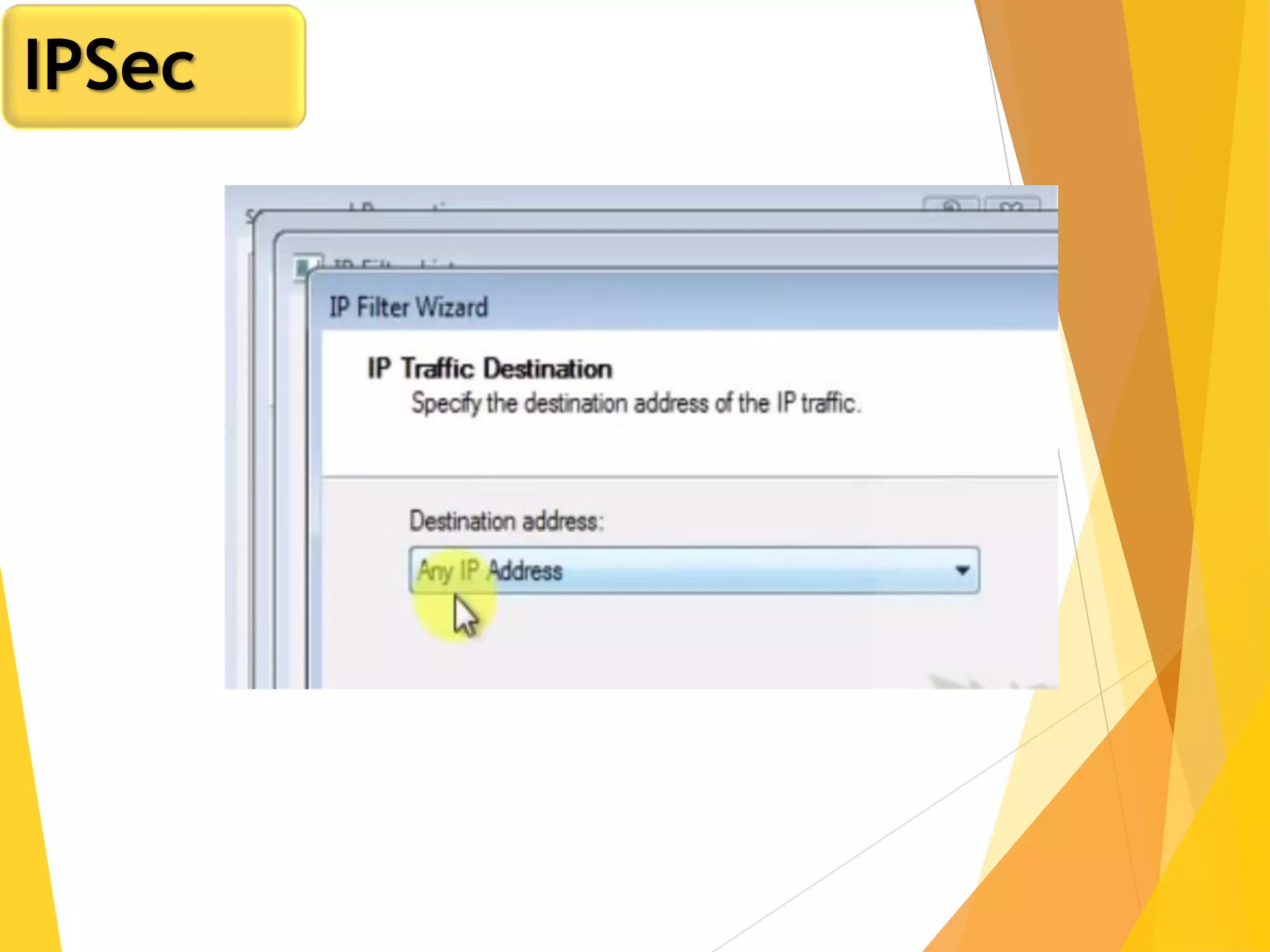
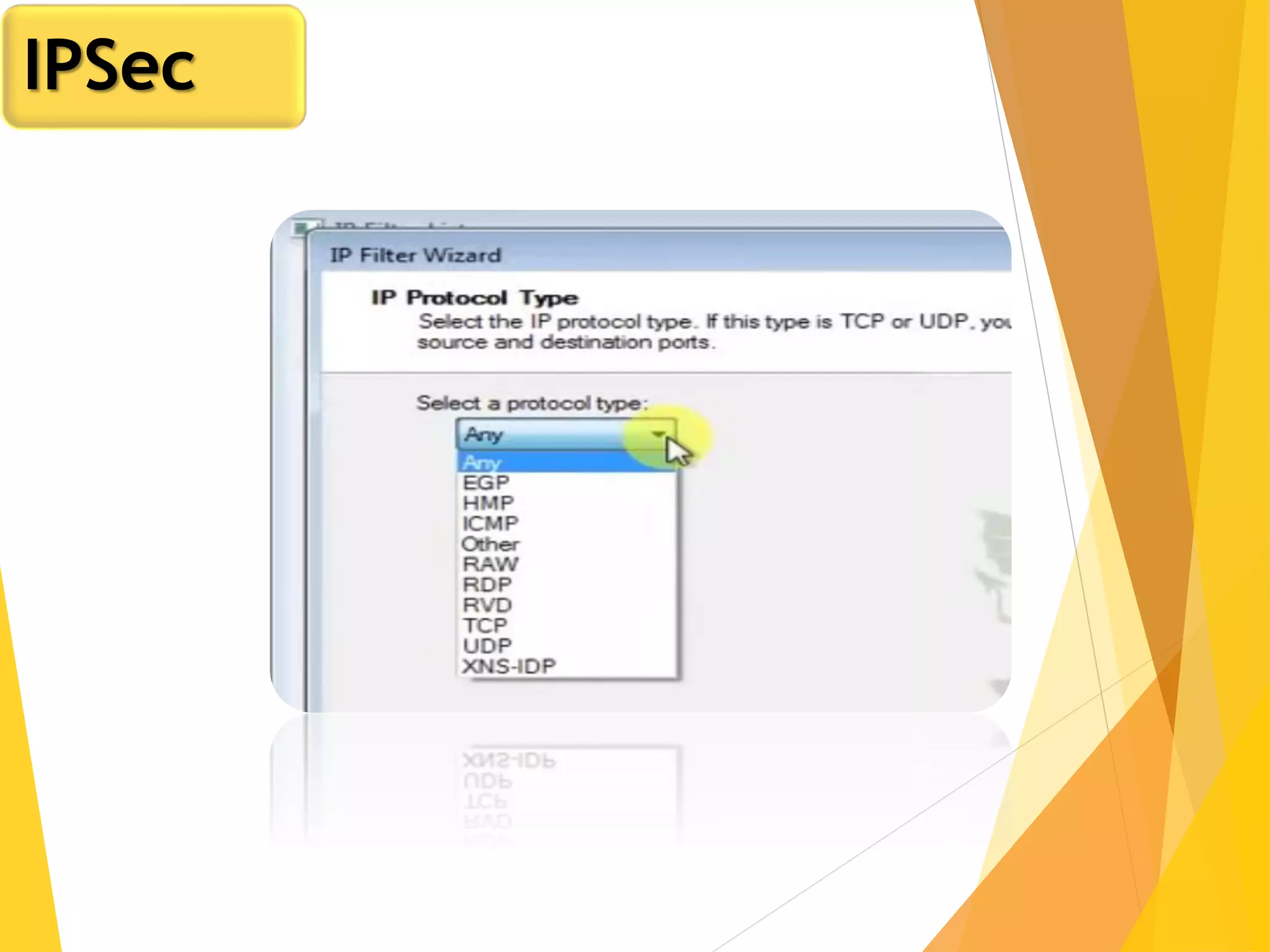
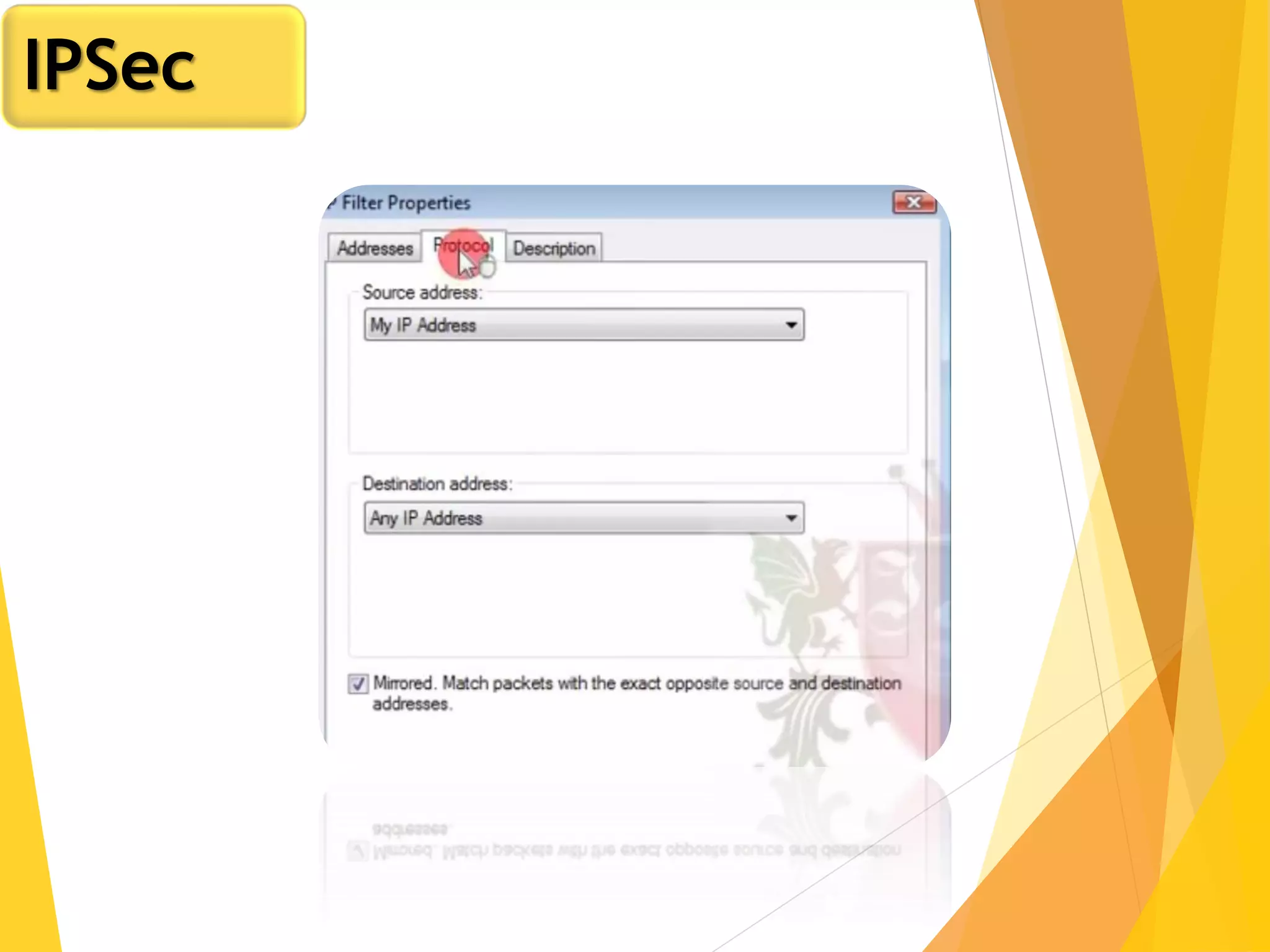
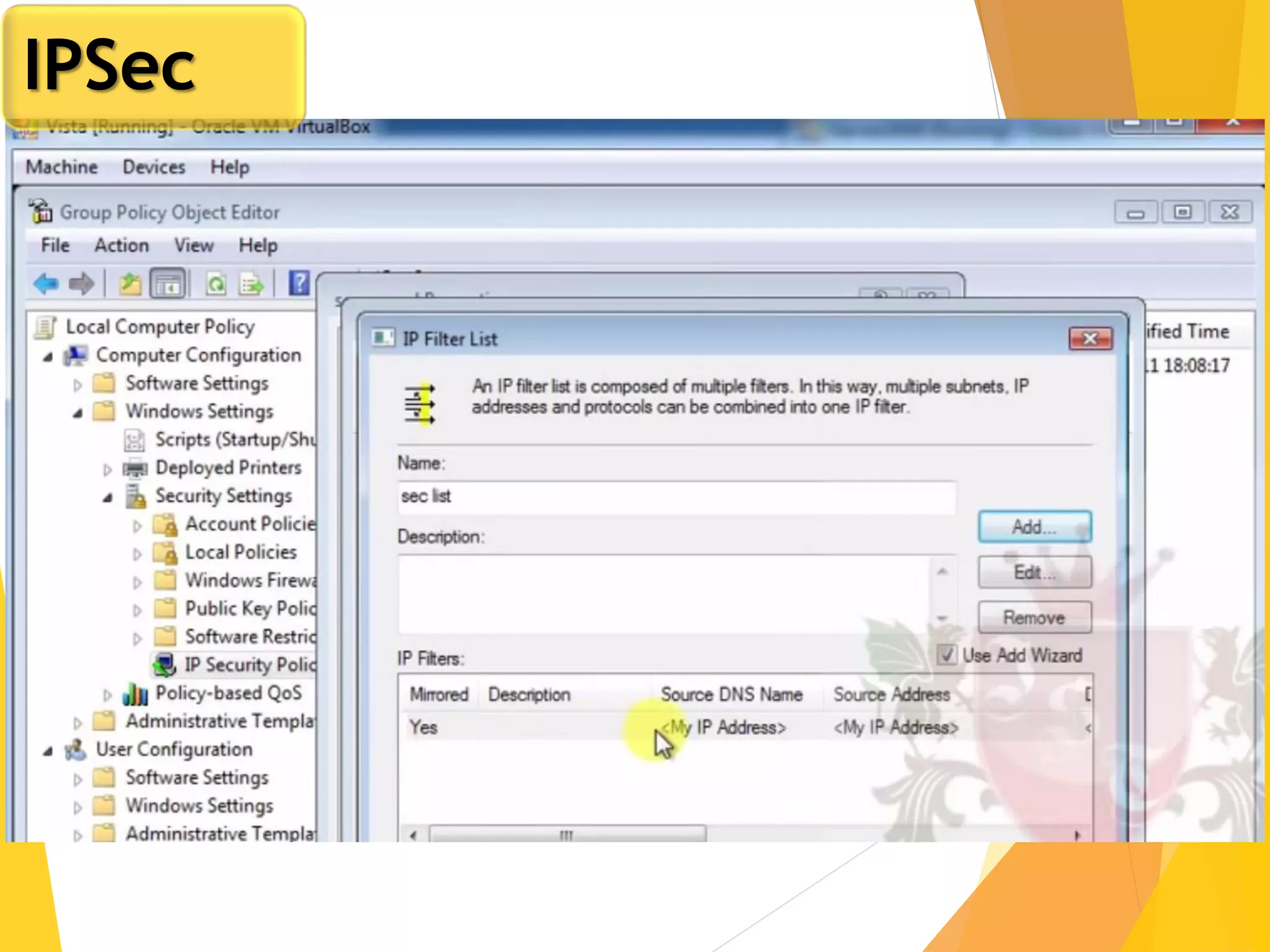
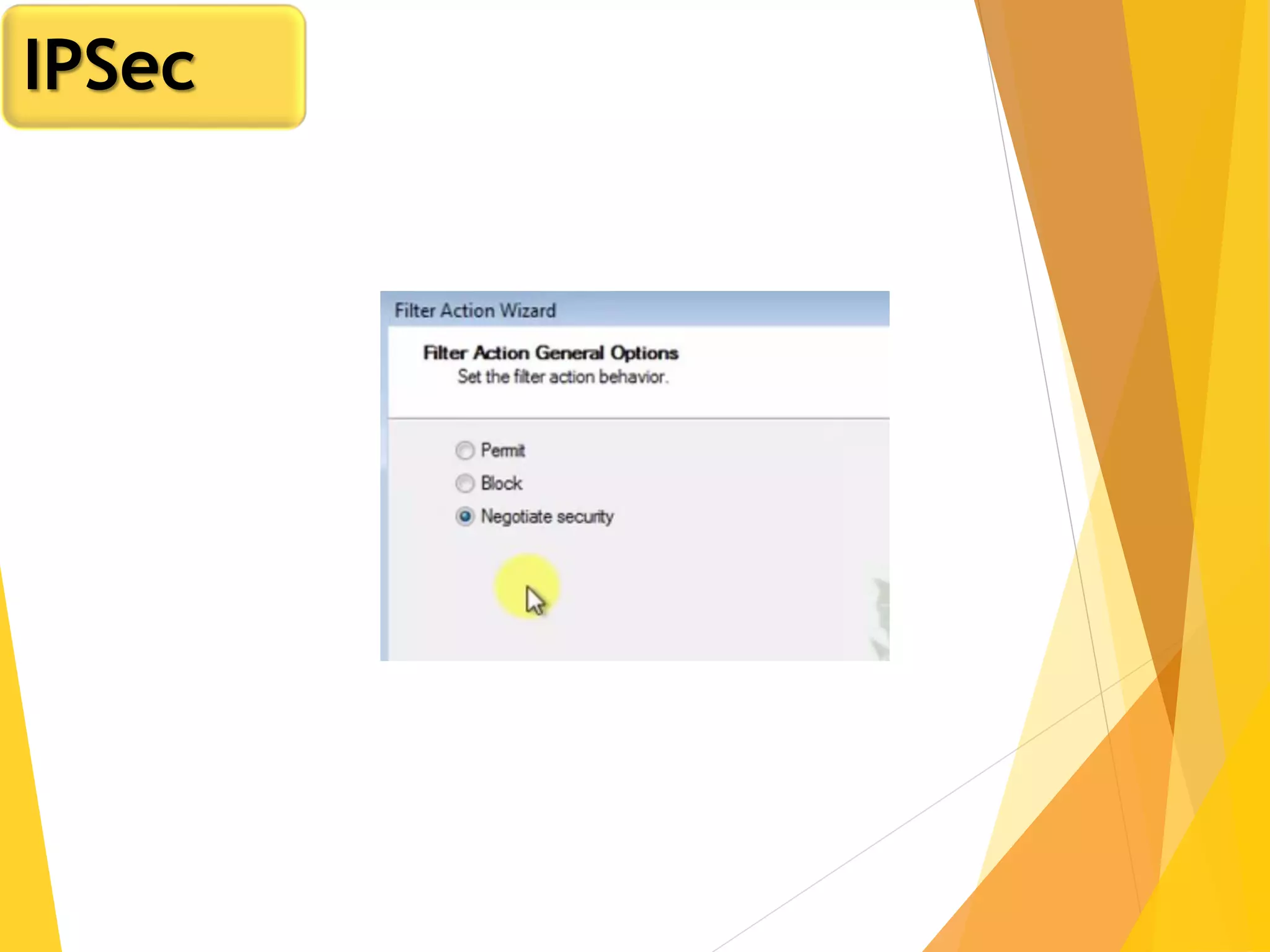
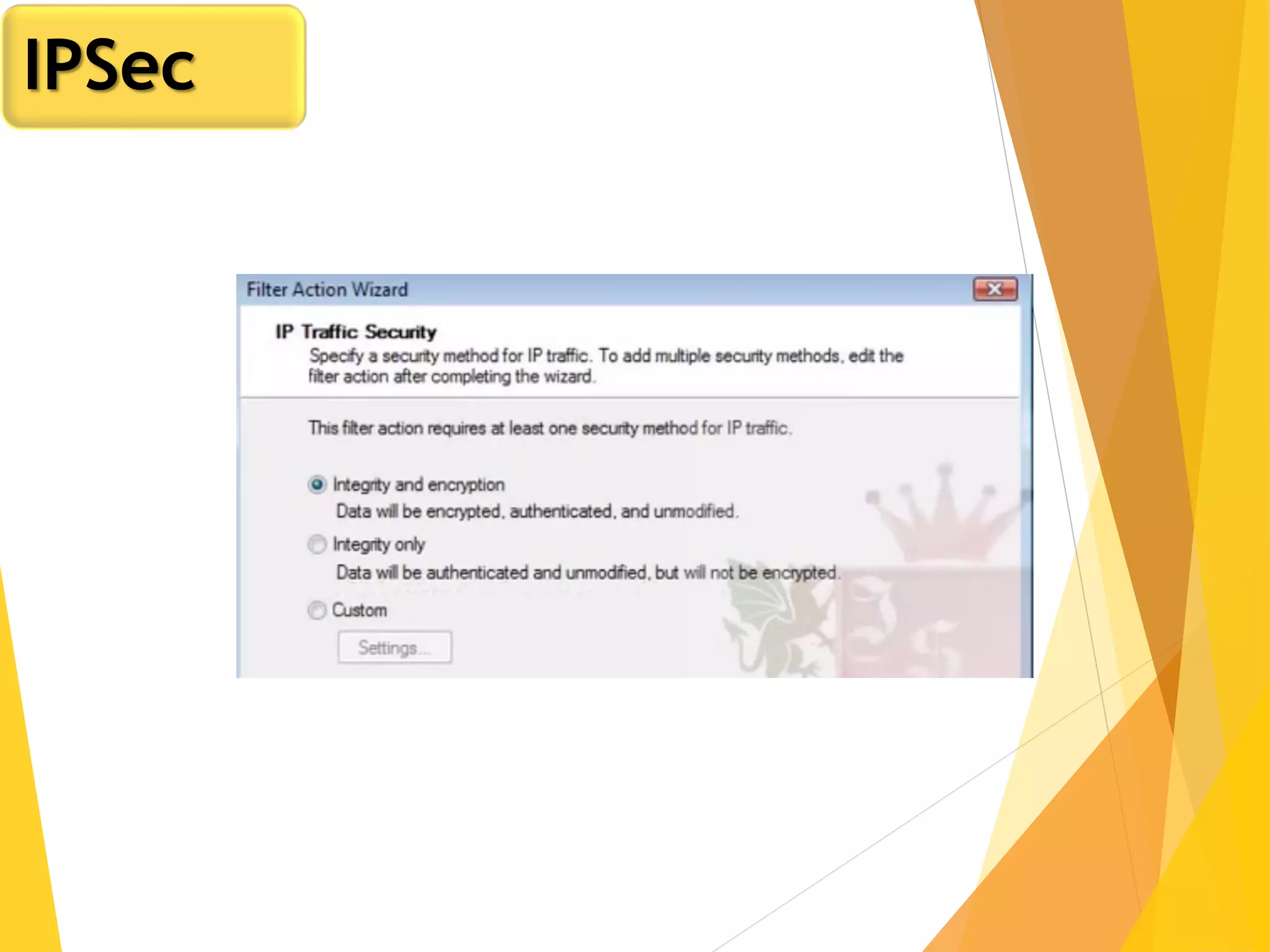
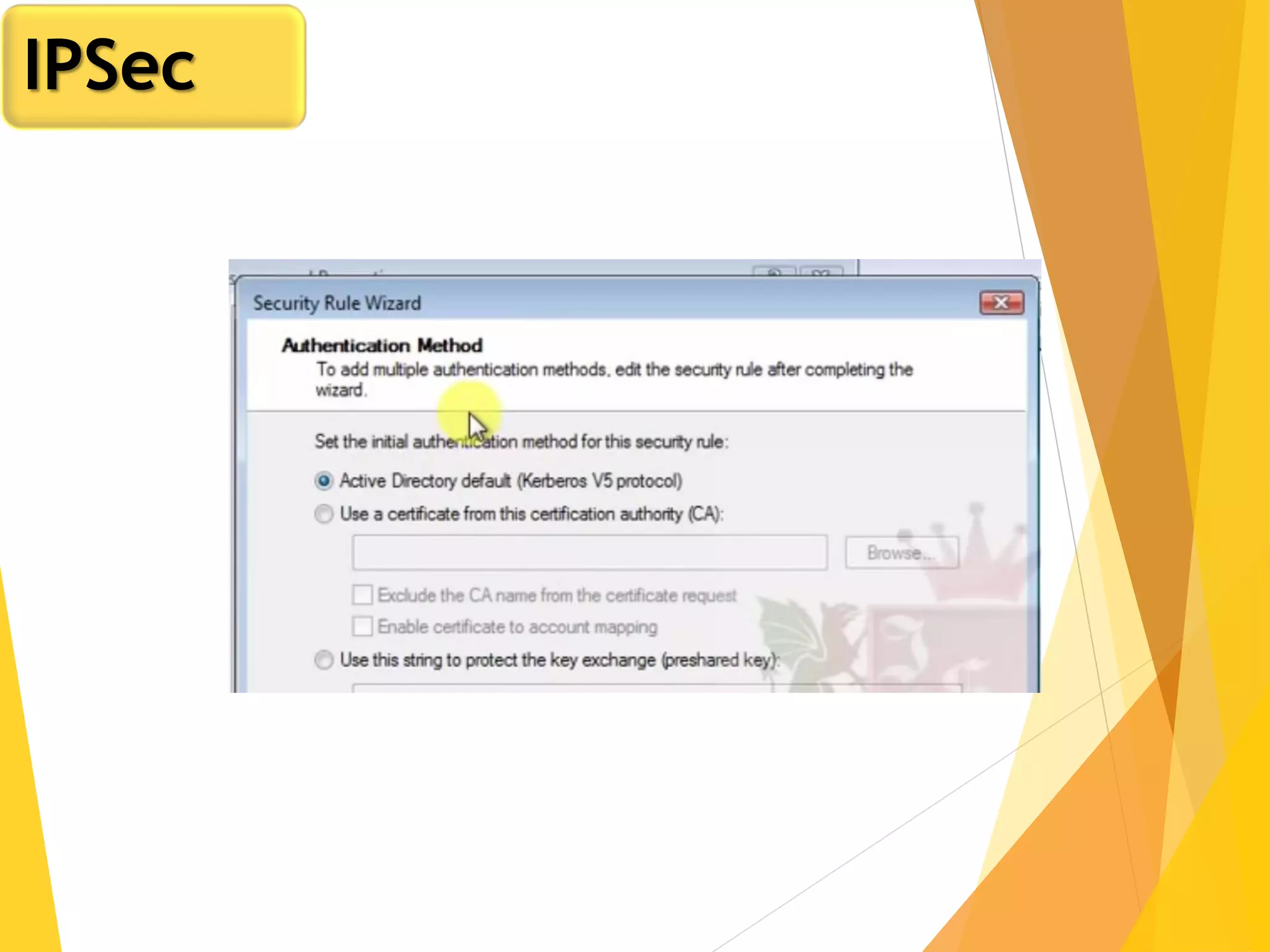
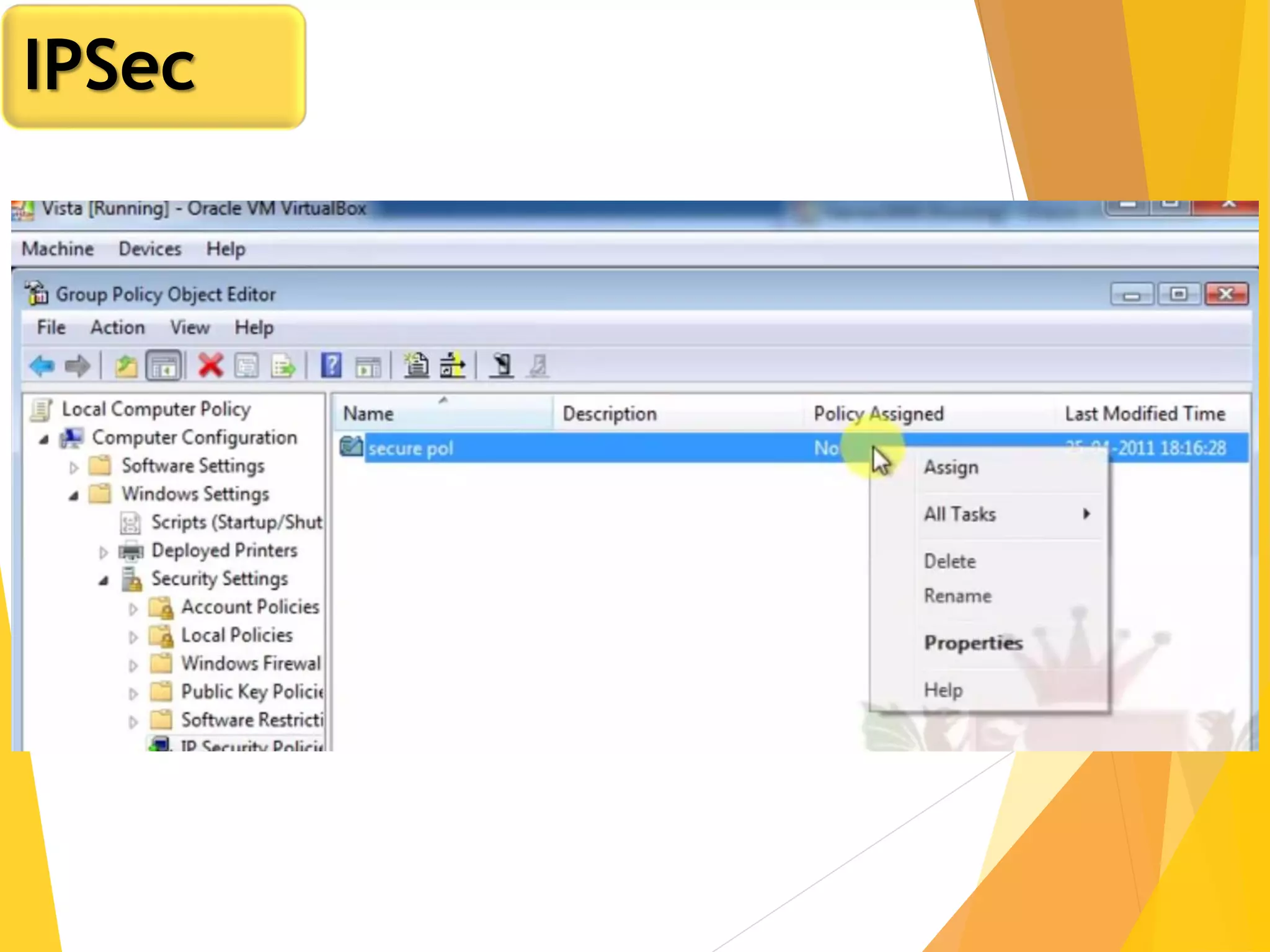
The document discusses various network security protocols, primarily focusing on PGP, SSL, and SSH. It explains how PGP provides services like authentication, confidentiality, and compression for email systems, while SSL secures data over TCP/IP connections. It also covers the implementation and advantages of IPsec in providing secure communication across different layers of a network.