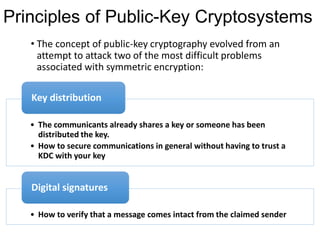
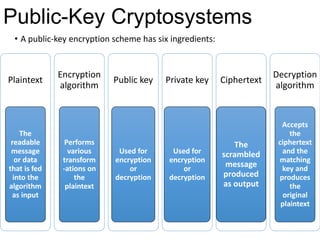
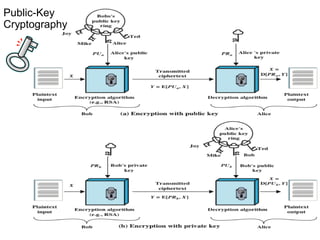
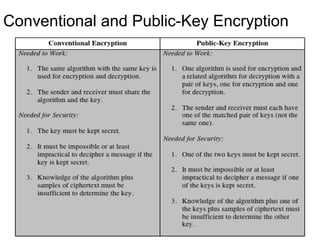
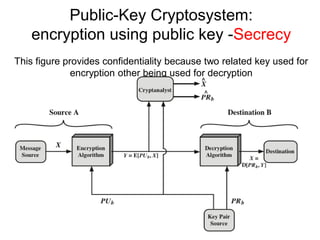
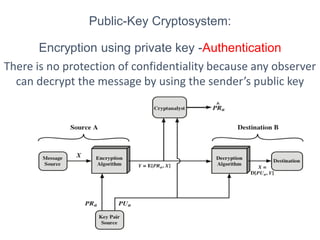
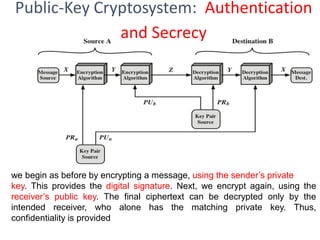
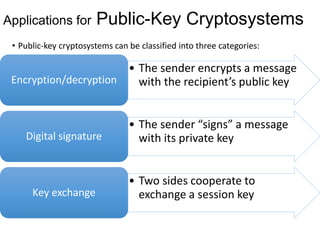
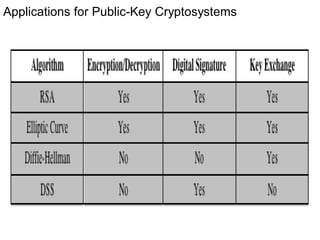
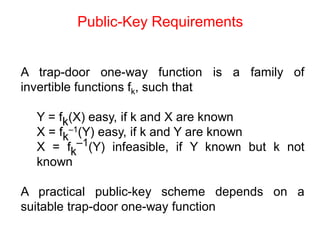
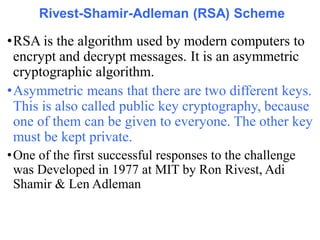
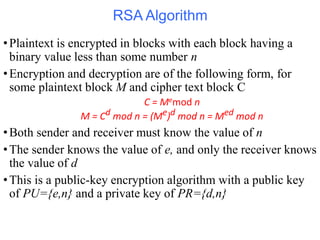
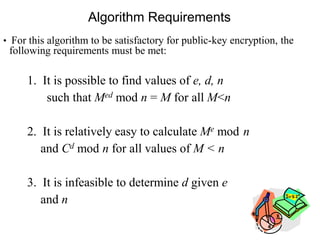
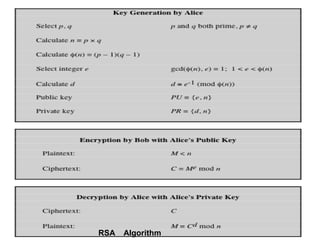
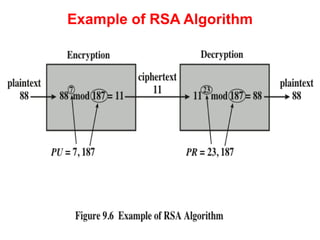
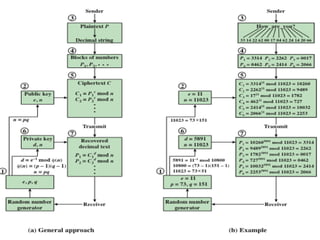
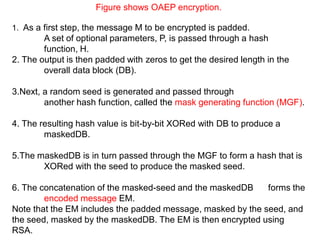
Public Key Cryptography (PKC) is an encryption method utilizing a pair of public and private keys for secure communications. The document explains the principles, requirements, and applications of PKC, including the RSA algorithm, which is widely used for encrypting messages and protecting confidentiality. Additionally, it covers various types of attacks on RSA and the use of Optimal Asymmetric Encryption Padding (OAEP) for enhanced security.