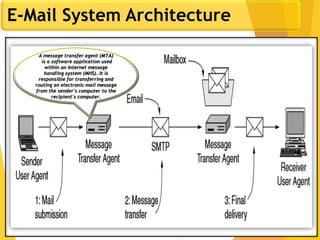
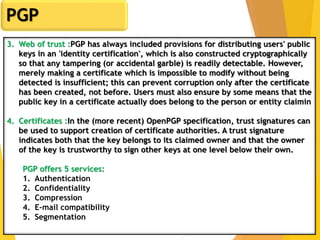
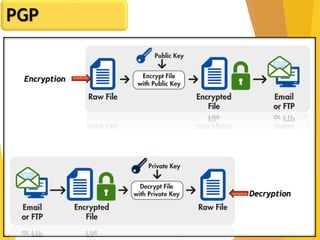
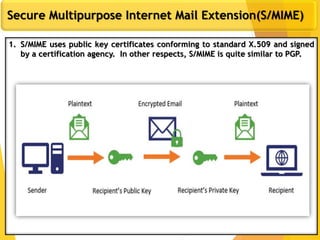
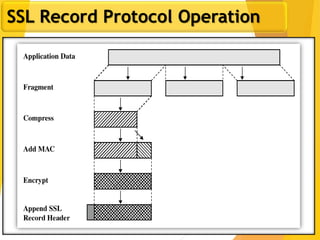
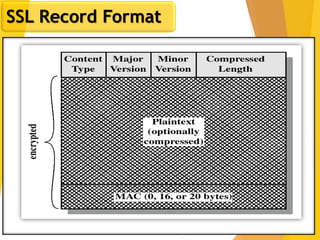
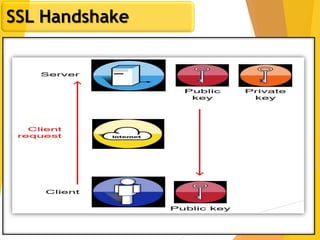
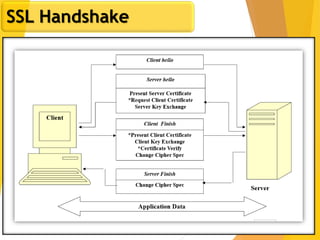
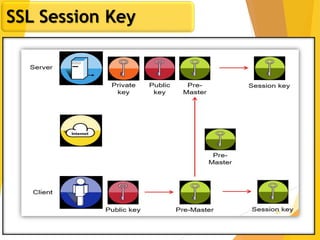
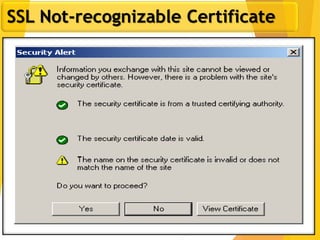
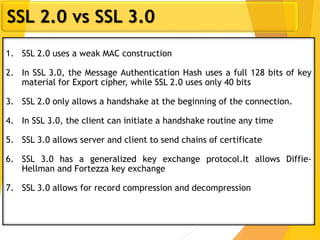
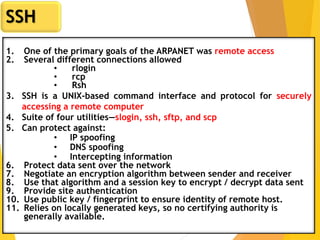
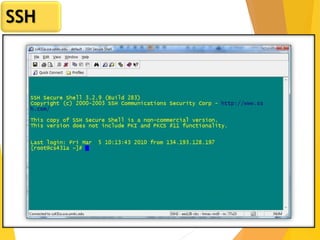
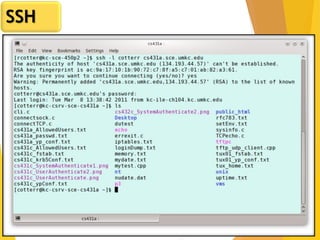
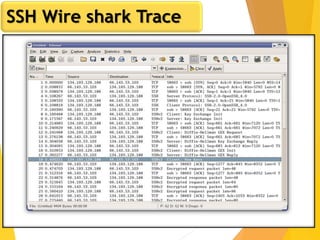
The document covers network security, focusing on application and transport layers, including secure email systems like PGP and S/MIME, and protocols such as SSL and SSH. It explains key concepts like message transfer agents, encryption methods, and digital signatures, and highlights threats to web security and their solutions. Additionally, it discusses improvements in SSL protocols and the use of SSH for secure remote access.