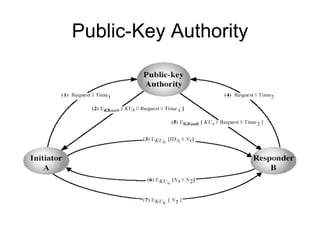
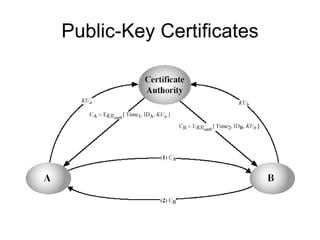
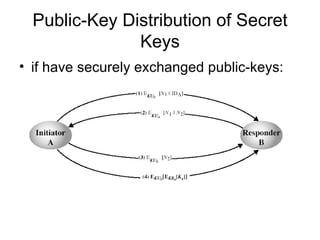
1. Public key distribution methods include public announcement, publicly available directories, public key authorities, and public key certificates.
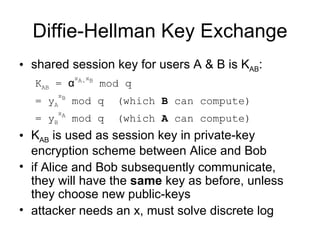
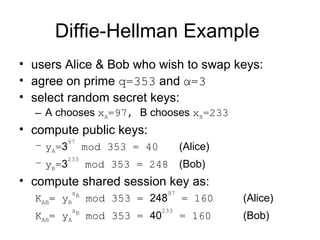
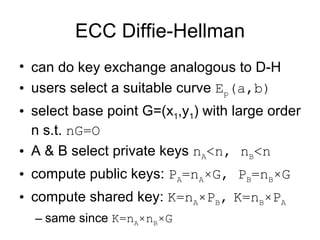
2. Diffie-Hellman key exchange allows two parties to jointly establish a shared secret key over an insecure channel without any prior secrets.
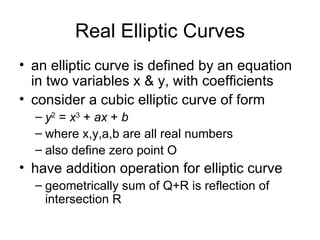
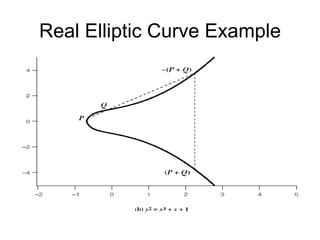
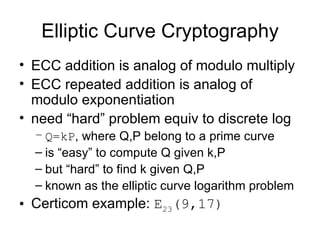
3. Elliptic curve cryptography provides the same level of security as other public key systems like RSA but with smaller key sizes, reducing computational overhead.