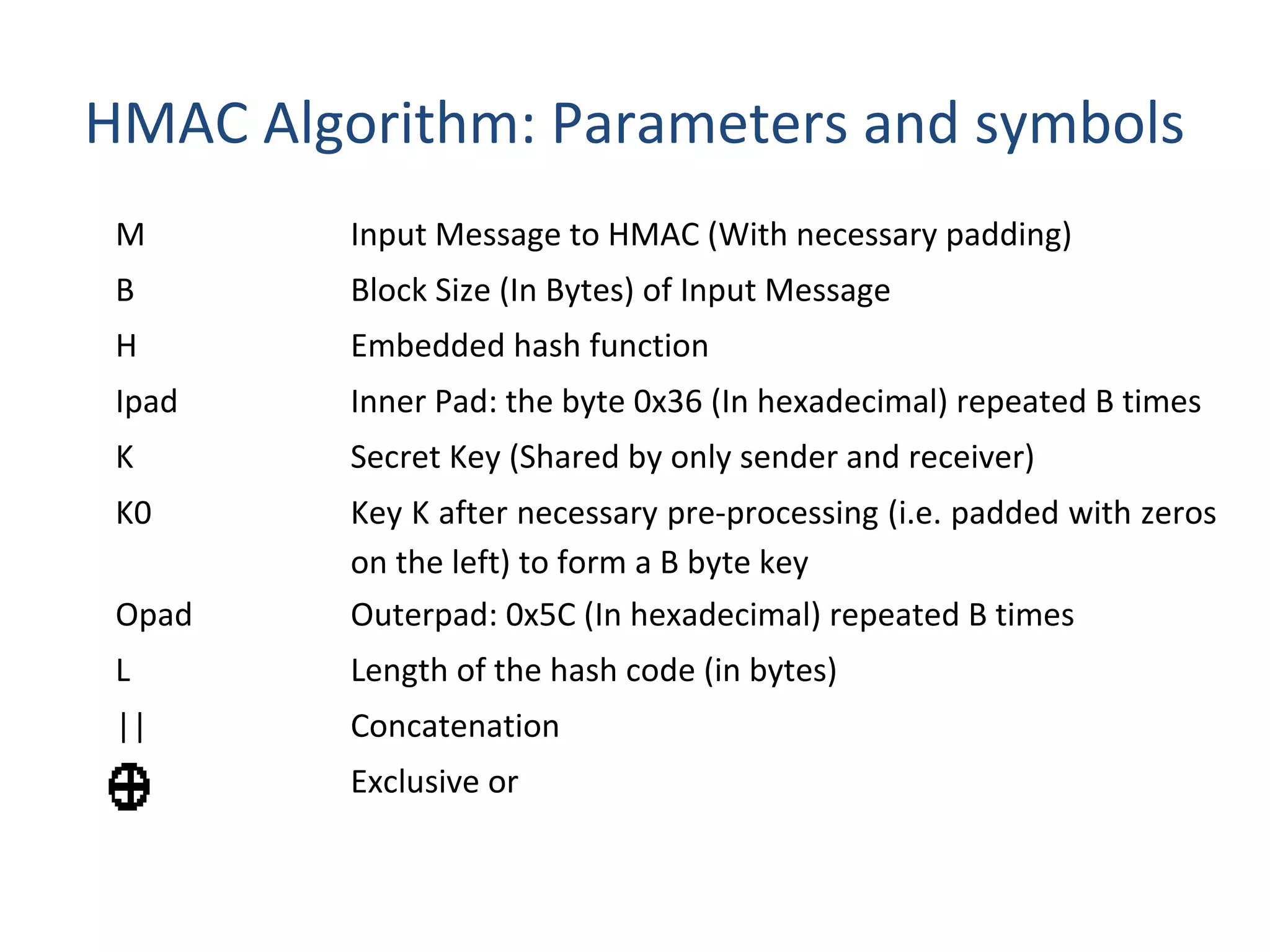
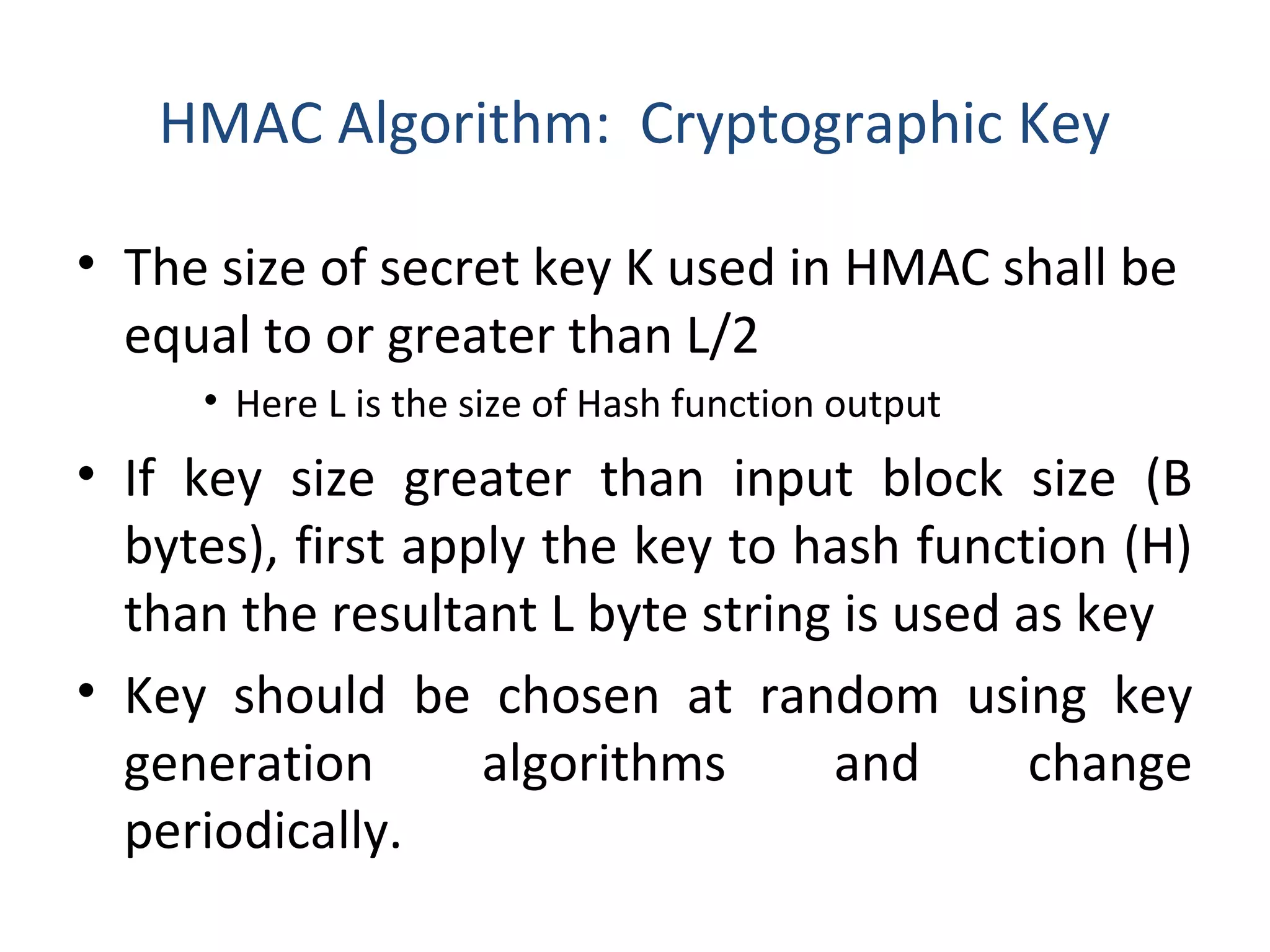
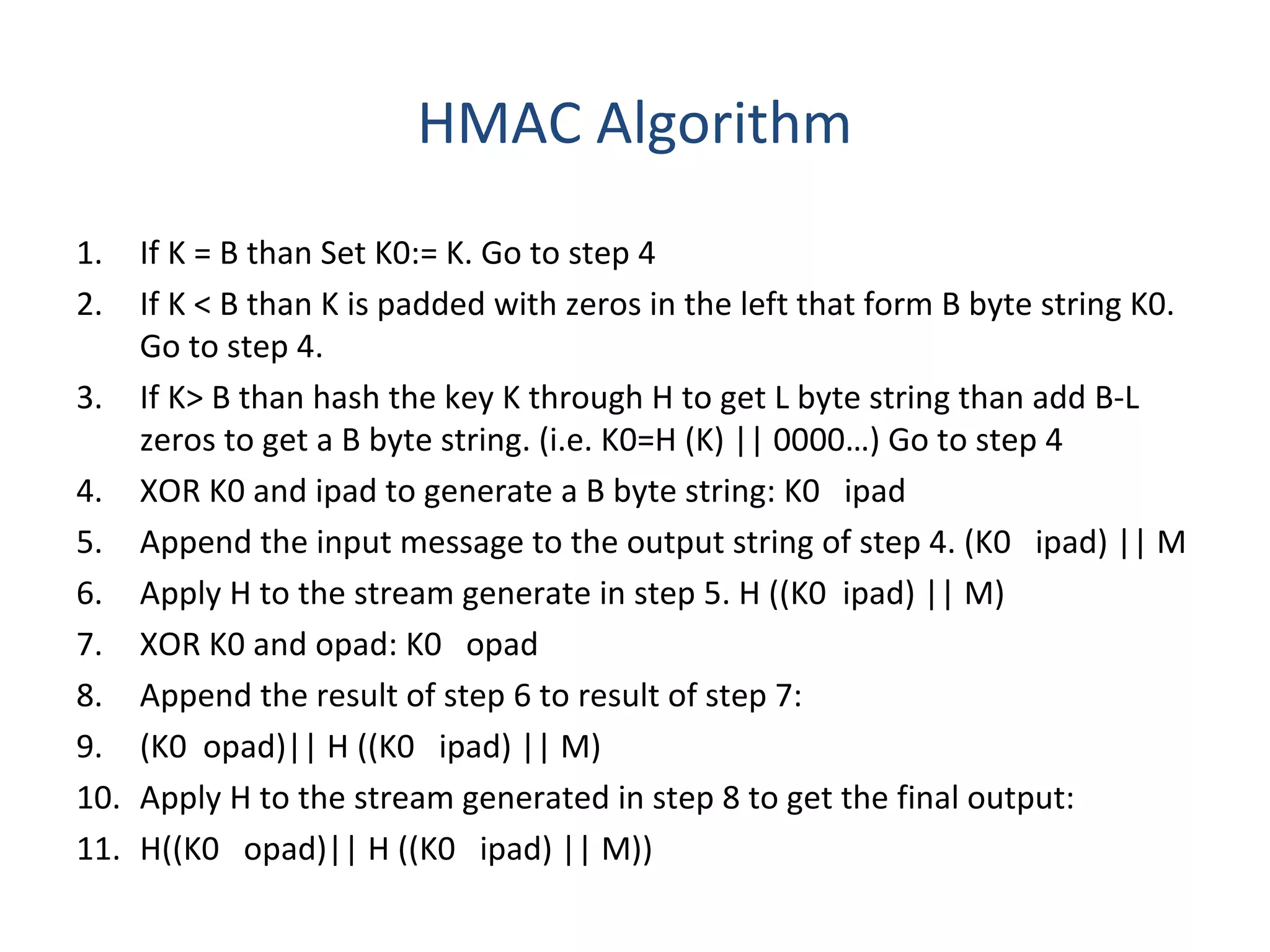
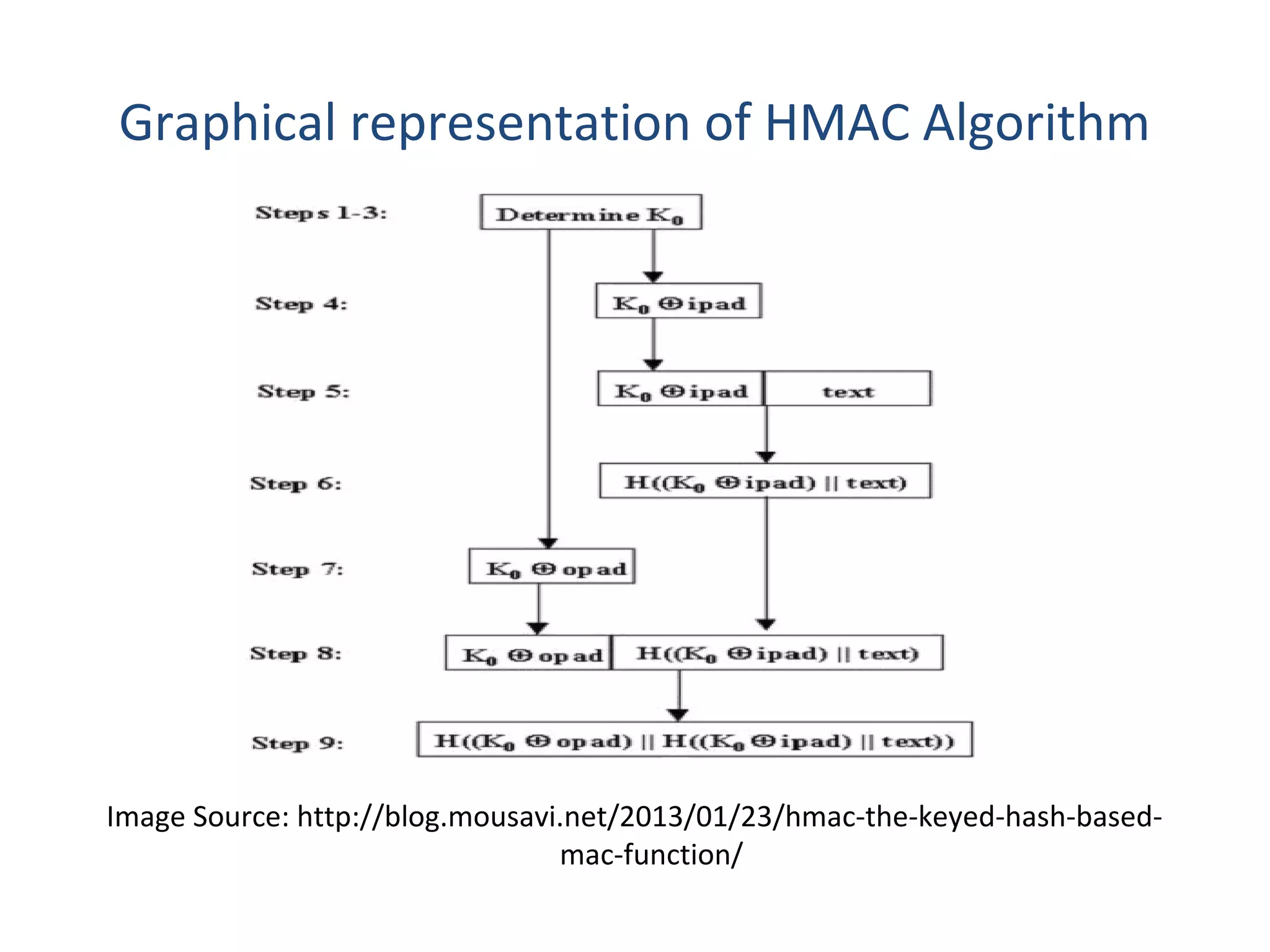
This document discusses techniques for distributing public keys and Hash-based Message Authentication Code (HMAC). It begins with an overview of public key cryptography and the need for secure key distribution. It then describes several approaches for distributing public keys, including using a public key authority, public key certificates, and a publicly available directory. The document also provides background on HMAC, describing how it uses cryptographic hash functions and a secret key to authenticate messages and ensure integrity. It includes the HMAC algorithm details, parameters, and a graphical representation of the process.