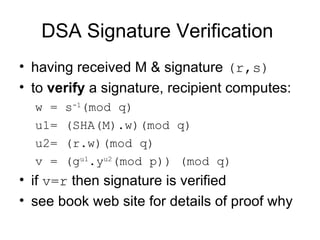
The document discusses digital signatures and authentication protocols. It covers the properties of digital signatures, including how they can verify authorship and authenticate message contents. Direct digital signatures involve the sender signing a message with their private key, while arbitrated signatures involve a third party. Authentication protocols are used to establish identity and exchange session keys, and must address issues like confidentiality, timeliness, and replay attacks. The document also describes common cryptographic algorithms and standards used for digital signatures, including the Digital Signature Algorithm (DSA).









![Needham-Schroeder Protocol original third-party key distribution protocol for session between A B mediated by KDC protocol overview is: 1. A -> KDC: ID A || ID B || N 1 2 . KDC -> A: E Ka [Ks || ID B || N 1 || E Kb [ Ks || ID A ] ] 3. A -> B: E Kb [ Ks || ID A ] 4. B -> A: E Ks [ N 2 ] 5. A -> B: E Ks [f( N 2 )]](https://image.slidesharecdn.com/ch13-1233858880948314-2/85/Ch13-10-320.jpg)


![Denning AS Protocol Denning 81 presented the following: 1. A -> AS: ID A || ID B 2. AS -> A: E KRas [ ID A ||KU a ||T] || E KRas [ ID B ||KU b ||T] 3. A -> B: E KRas [ ID A ||KU a ||T] || E KRas [ ID B ||KU b ||T] || E KUb [E KRas [K s ||T]] note session key is chosen by A, hence AS need not be trusted to protect it timestamps prevent replay but require synchronized clocks](https://image.slidesharecdn.com/ch13-1233858880948314-2/85/Ch13-13-320.jpg)

![Using Symmetric Encryption can refine use of KDC but can’t have final exchange of nonces, vis: 1. A -> KDC: ID A || ID B || N 1 2 . KDC -> A: E Ka [Ks || ID B || N 1 || E Kb [ Ks || ID A ] ] 3. A -> B: E Kb [ Ks || ID A ] || E Ks [M] does not protect against replays could rely on timestamp in message, though email delays make this problematic](https://image.slidesharecdn.com/ch13-1233858880948314-2/85/Ch13-15-320.jpg)
![Public-Key Approaches have seen some public-key approaches if confidentiality is major concern, can use: A -> B: E KUb [Ks] || E Ks [M] has encrypted session key, encrypted message if authentication needed use a digital signature with a digital certificate: A -> B: M || E KRa [H(M)] || E KRas [T||ID A ||KU a ] with message, signature, certificate](https://image.slidesharecdn.com/ch13-1233858880948314-2/85/Ch13-16-320.jpg)